实训记录6——双机热备技术
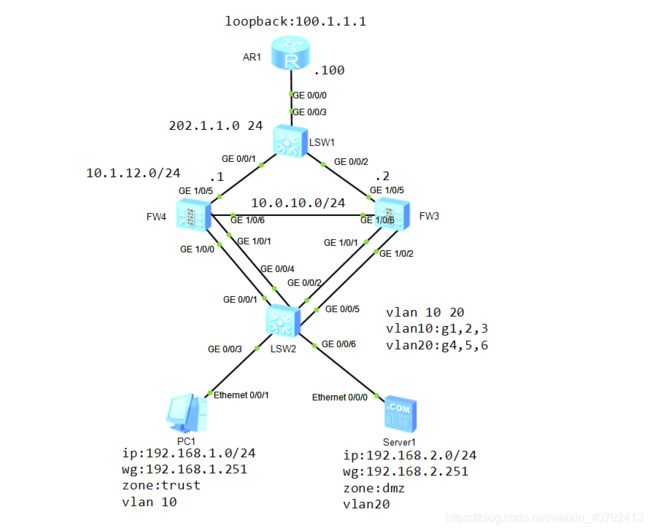
一、网络拓扑图
二、划分VLAN,配置IP,划分区域
2.1 LSW1,LSW2
LSW1关闭STP即可,不需要其他操作。
LSW2:
[sw2]
<sw2>undo t t
Info: Current terminal trapping is off.
<sw2>sy
Enter system view, return user view with Ctrl+Z.
[sw2]vlan ba
[sw2]vlan batch 10 20 //配置VLAN
Info: This operation may take a few seconds. Please wait for a moment...done.
[sw2]port-
[sw2]port-isolate
[sw2]port-mirroring
[sw2]port-group ?
STRING<1-32> Port-group name
group-member Add port to current port-group
[sw2]port-group g
[sw2]port-group group-member g
[sw2]port-group group-member GigabitEthernet 0/0/1 to
[sw2]port-group group-member GigabitEthernet 0/0/1 to g
[sw2]port-group group-member GigabitEthernet 0/0/1 to GigabitEthernet 0/0/3 //集中配置接口类型
[sw2-port-group]p l a
[sw2-GigabitEthernet0/0/1]p l a
[sw2-GigabitEthernet0/0/2]p l a
[sw2-GigabitEthernet0/0/3]p l a
[sw2-port-group]p d v 10
[sw2-GigabitEthernet0/0/1]p d v 10
[sw2-GigabitEthernet0/0/2]p d v 10
[sw2-GigabitEthernet0/0/3]p d v 10
[sw2-port-group]
[sw2-port-group]q
[sw2]port-group group-member GigabitEthernet 0/0/4 to GigabitEthernet 0/0/6
[sw2-port-group]p l a
[sw2-GigabitEthernet0/0/4]p l a
[sw2-GigabitEthernet0/0/5]p l a
[sw2-GigabitEthernet0/0/6]p l a
[sw2-port-group]p d v 20
[sw2-GigabitEthernet0/0/4]p d v 20
[sw2-GigabitEthernet0/0/5]p d v 20
[sw2-GigabitEthernet0/0/6]p d v 20
[sw2-port-group]
Jul 29 2020 16:06:13-08:00 sw2 %%01IFNET/4/IF_STATE(l)[0]:Interface Vlanif1 has
turned into DOWN state.q
[sw2]dis vlan
The total number of vlans is : 3
--------------------------------------------------------------------------------
U: Up; D: Down; TG: Tagged; UT: Untagged;
MP: Vlan-mapping; ST: Vlan-stacking;
#: ProtocolTransparent-vlan; *: Management-vlan;
--------------------------------------------------------------------------------
VID Type Ports
--------------------------------------------------------------------------------
1 common UT:GE0/0/7(D) GE0/0/8(D) GE0/0/9(D) GE0/0/10(D)
GE0/0/11(D) GE0/0/12(D) GE0/0/13(D) GE0/0/14(D)
GE0/0/15(D) GE0/0/16(D) GE0/0/17(D) GE0/0/18(D)
GE0/0/19(D) GE0/0/20(D) GE0/0/21(D) GE0/0/22(D)
GE0/0/23(D) GE0/0/24(D)
10 common UT:GE0/0/1(U) GE0/0/2(U) GE0/0/3(U)
20 common UT:GE0/0/4(U) GE0/0/5(U) GE0/0/6(U)
2.2 防火墙FW1(FW2 类似)配置IP,划分区域
<USG6000V1>undo t t
Info: Current terminal trapping is off.
<USG6000V1>sy
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sy fw1
[fw1]int g1/0/5
[fw1-GigabitEthernet1/0/5]ip ad 10.1.12.1 24
[fw1-GigabitEthernet1/0/5]
[fw1-GigabitEthernet1/0/5]int g1/0/6
[fw1-GigabitEthernet1/0/6]ip ad 10.0.10.1 24
[fw1-GigabitEthernet1/0/6]
[fw1-GigabitEthernet1/0/6]int g1/0/1
[fw1-GigabitEthernet1/0/1]ip ad 192.168.1.251 24
[fw1-GigabitEthernet1/0/1]
[fw1-GigabitEthernet1/0/1]int g1/0/0
[fw1-GigabitEthernet1/0/0]ip ad 192.168.2.251 24
[fw1-GigabitEthernet1/0/0]
[fw1-GigabitEthernet1/0/0]q
[fw1]dis ip int br
2020-07-29 08:12:10.110
*down: administratively down
^down: standby
(l): loopback
(s): spoofing
(d): Dampening Suppressed
(E): E-Trunk down
The number of interface that is UP in Physical is 6
The number of interface that is DOWN in Physical is 4
The number of interface that is UP in Protocol is 6
The number of interface that is DOWN in Protocol is 4
Interface IP Address/Mask Physical Protocol
GigabitEthernet0/0/0 192.168.0.1/24 down down
GigabitEthernet1/0/0 192.168.2.251/24 up up
GigabitEthernet1/0/1 192.168.1.251/24 up up
GigabitEthernet1/0/2 unassigned down down
GigabitEthernet1/0/3 unassigned down down
GigabitEthernet1/0/4 unassigned down down
GigabitEthernet1/0/5 10.1.12.1/24 up up
GigabitEthernet1/0/6 10.0.10.1/24 up up
NULL0 unassigned up up(s)
Virtual-if0 unassigned up up(s)
[fw1]fir
[fw1]firewall z
[fw1]firewall zone t
[fw1]firewall zone trust
[fw1-zone-trust]ad
[fw1-zone-trust]add i
[fw1-zone-trust]add interface g1/0/1
[fw1-zone-trust]q
[fw1]fi
[fw1]firewallz
[fw1]firewallzd
[fw1]firewall z
[fw1]firewall zone d
[fw1]firewall zone dmz
[fw1-zone-dmz]ad
[fw1-zone-dmz]add in
[fw1-zone-dmz]add interface g1/0/0
[fw1-zone-dmz]q
[fw1]fire
[fw1]firewall z
[fw1]firewall zone u
[fw1]firewall zone untrust
[fw1-zone-untrust]ad
[fw1-zone-untrust]add i
[fw1-zone-untrust]add interface g1/0/5
[fw1-zone-untrust]q
[fw1]fir
[fw1]firewall z
[fw1]firewall zone n
[fw1]firewall zone name hrp //自定义区域hrp(心跳区域)
[fw1-zone-hrp]set p
[fw1-zone-hrp]set priority 90 //自定义优先级为90
[fw1-zone-hrp]ad
[fw1-zone-hrp]add in
[fw1-zone-hrp]add interface g1/0/6 //添加端口g1/0/6
[fw1-zone-hrp]q
[fw1]dis zone
2020-07-29 08:15:39.270
local
priority is 100
interface of the zone is (0):
#
trust
priority is 85
interface of the zone is (2):
GigabitEthernet0/0/0
GigabitEthernet1/0/1
#
untrust
priority is 5
interface of the zone is (1):
GigabitEthernet1/0/5
#
dmz
priority is 50
interface of the zone is (1):
GigabitEthernet1/0/0
#
hrp
priority is 90
interface of the zone is (1):
GigabitEthernet1/0/6
FW2根据端口,修改IP,配置区域即可,如g1/0/1的IP为192.168.1.252 。
2.3 公网路由器配置
<Huawei>sy
Enter system view, return user view with Ctrl+Z.
[Huawei]int g0/0/0
[Huawei-GigabitEthernet0/0/0]ip ad 202.1.1.100 24
[Huawei-GigabitEthernet0/0/0]
Jul 29 2020 16:44:12-08:00 Huawei %%01IFNET/4/LINK_STATE(l)[0]:The line protocol
IP on the interface GigabitEthernet0/0/0 has entered the UP state.
[Huawei-GigabitEthernet0/0/0]q
[Huawei]int lo
[Huawei]int LoopBack 1
[Huawei-LoopBack1]ip ad 100.1.1.1
^
Error:Incomplete command found at '^' position.
[Huawei-LoopBack1]ip ad 100.1.1.1 24
[Huawei-LoopBack1]
三、防火墙配置VRRP
[fw1]int g1/0/5
[fw1-GigabitEthernet1/0/5]vrrp vi
[fw1-GigabitEthernet1/0/5]vrrp virtual-mac
[fw1-GigabitEthernet1/0/5]vrrp virtual-mac
[fw1-GigabitEthernet1/0/5]vrrp vi
[fw1-GigabitEthernet1/0/5]vrrp vr
[fw1-GigabitEthernet1/0/5]vrrp vrid 1 v
[fw1-GigabitEthernet1/0/5]vrrp vrid 1 version-3
[fw1-GigabitEthernet1/0/5]vrrp vrid 1 virtual-ip 202.1.1.1 255.255.255.0 act
[fw1-GigabitEthernet1/0/5]vrrp vrid 1 virtual-ip 202.1.1.1 255.255.255.0 active fw2中,active改为standby)
[fw1-GigabitEthernet1/0/5]vrrp vr
[fw1-GigabitEthernet1/0/5]vrrp vrid 1 vi
[fw1-GigabitEthernet1/0/5]int g1/0/1
[fw1-GigabitEthernet1/0/1]vrrp vrid 1 v
[fw1-GigabitEthernet1/0/1]vrrp vrid 1 version-3
[fw1-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 192.168.1.254 ac
[fw1-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 192.168.1.254 active fw2中,active改为standby)
[fw1-GigabitEthernet1/0/1]int g1/0/0
[fw1-GigabitEthernet1/0/0]vrrp vri
[fw1-GigabitEthernet1/0/0]vrrp vrid 1 vie
[fw1-GigabitEthernet1/0/0]vrrp vrid 1 vir
[fw1-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 192.168.2.254 act
[fw1-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 192.168.2.254 active (fw2中,active改为standby)
[fw1-GigabitEthernet1/0/0]q
[fw1]dis vrrp br
2020-07-29 08:23:51.890
Total:3 Master:0 Backup:3 Non-active:0
VRID State Interface Type Virtual IP
----------------------------------------------------------------
1 Backup GE1/0/5 Vgmp 202.1.1.1
1 Backup GE1/0/1 Vgmp 192.168.1.254
1 Backup GE1/0/0 Vgmp 192.168.2.254
四、fw1,fw2配置去公网的默认路由
两台防火墙命令相同:ip route-static 0.0.0.0 0 202.1.1.100
五、配置心跳接口g1/0/6
FW1:
[fw1]hrp enable
Info: NAT IP detect function is disabled.
HRP_S[fw1]
HRP_S[fw1]hrp int
HRP_S[fw1]hrp interface g1/0/6 re
HRP_S[fw1]hrp interface g1/0/6 remote 10.0.10.2 //配置心跳接口为1/0/6,对方IP为10.0.10.2
HRP_S[fw1]
FW2:
[fw2]hrp interface g1/0/6 remote 10.0.10.1
Info: NAT IP detect function is disabled.
[fw2]hrp standby-device //设置为备用设备
[fw2]hrp enable
HRP_S[fw2]
六、配置安全策略
//配置好心跳后,在master设备上输入的命令后面会自动带上(+B)
HRP_M[fw1]se
HRP_M[fw1]security-policy (+B)
HRP_M[fw1-policy-security]rule name
Jul 29 2020 08:33:52 fw1 %%01HRPI/2/DOWN(l)[11]:HRP link changes to down due to
send data failed.
HRP_M[fw1-policy-security]rule name 1 (+B)
HRP_M[fw1-policy-security-rule-1]se
HRP_M[fw1-policy-security-rule-1]so
HRP_M[fw1-policy-security-rule-1]source-z
HRP_M[fw1-policy-security-rule-1]source-zone t
HRP_M[fw1-policy-security-rule-1]source-zone trust (+B)
HRP_M[fw1-policy-security-rule-1]de
HRP_M[fw1-policy-security-rule-1]destination-zone un
HRP_M[fw1-policy-security-rule-1]destination-zone untrust (+B)
HRP_M[fw1-policy-security-rule-1]ac
HRP_M[fw1-policy-security-rule-1]access-authentication
HRP_M[fw1-policy-security-rule-1]action pe
HRP_M[fw1-policy-security-rule-1]action permit (+B)
HRP_M[fw1-policy-security-rule-1]sou
HRP_M[fw1-policy-security-rule-1]source-z
HRP_M[fw1-policy-security-rule-1]q
HRP_M[fw1-policy-security]rule na
HRP_M[fw1-policy-security]rule name 2 (+B)
HRP_M[fw1-policy-security-rule-2]so
HRP_M[fw1-policy-security-rule-2]source-z
HRP_M[fw1-policy-security-rule-2]source-zone un
HRP_M[fw1-policy-security-rule-2]source-zone untrust (+B)
HRP_M[fw1-policy-security-rule-2]de
HRP_M[fw1-policy-security-rule-2]destination-zone dmz (+B)
HRP_M[fw1-policy-security-rule-2]per
HRP_M[fw1-policy-security-rule-2]act
HRP_M[fw1-policy-security-rule-2]action per
HRP_M[fw1-policy-security-rule-2]action permit (+B)
HRP_M[fw1-policy-security-rule-2]q
HRP_M[fw1-policy-security]q
HRP_M[fw1]
七、配置NAT策略
HRP_M[fw1]nat-p
HRP_M[fw1]nat-policy (+B)
HRP_M[fw1-policy-nat]rule name internet (+B)
HRP_M[fw1-policy-nat-rule-internet]se
HRP_M[fw1-policy-nat-rule-internet]so
HRP_M[fw1-policy-nat-rule-internet]source-z
HRP_M[fw1-policy-nat-rule-internet]source-zone t
HRP_M[fw1-policy-nat-rule-internet]source-zone trust (+B)
HRP_M[fw1-policy-nat-rule-internet]des
HRP_M[fw1-policy-nat-rule-internet]destination-zone unt
HRP_M[fw1-policy-nat-rule-internet]destination-zone untrust (+B)
HRP_M[fw1-policy-nat-rule-internet]act
HRP_M[fw1-policy-nat-rule-internet]action s
HRP_M[fw1-policy-nat-rule-internet]action source-nat a
HRP_M[fw1-policy-nat-rule-internet]action source-nat address-group 1 (+B)
HRP_M[fw1-policy-nat-rule-internet]
八、实验效果
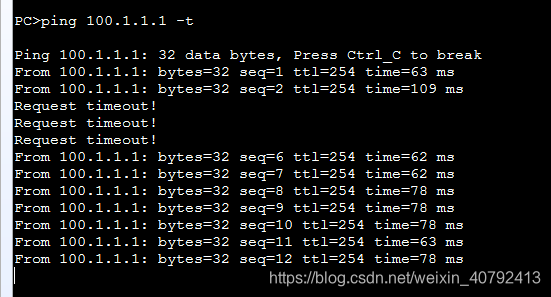
PC ping公网地址ping通,在关闭主防火墙的g1/0/1接口后,会出现短暂的timeout,然后使用备用防火墙继续工作。
HRP_S[fw1]dis firewall session table
2020-07-29 08:47:57.200
Current Total Sessions : 8
udp VPN: public --> public 10.0.10.1:49152 --> 10.0.10.2:18514
icmp VPN: public --> public 192.168.1.1:50231[202.1.1.1:2073] --> 100.1.1.1:2
048
udp VPN: public --> public 10.0.10.2:49152 --> 10.0.10.1:18514
icmp VPN: public --> public 192.168.1.1:50487[202.1.1.1:2074] --> 100.1.1.1:2
048
icmp VPN: public --> public 192.168.1.1:49719[202.1.1.1:2071] --> 100.1.1.1:2
048
icmp VPN: public --> public 192.168.1.1:49975[202.1.1.1:2072] --> 100.1.1.1:2
048
udp VPN: public --> public 10.0.10.2:16384 --> 10.0.10.1:18514
icmp VPN: public --> public 192.168.1.1:49207[202.1.1.1:2070] --> 100.1.1.1:2
048
HRP_M[fw1]
查看防火墙,可以看到已经完成地址转换。