Nmap渗透测试指南之防火墙/IDS逃逸、信息搜集
Nmap渗透测试指南之防火墙/IDS逃逸、信息搜集
- 一. 防火墙/IDS逃逸
-
-
- 本章知识点
- 本章选项
- 一 .关于防火墙/IDS
- 二. 报文分段
- 三. 指定偏移大小
- 四. IP欺骗
- 五. 源地址欺骗
- 六. 源端口欺骗
- 七. 指定发包长度
- 八. 目标主机随机排序
- 九. MAC地址欺骗
-
- 二. 信息收集
-
-
- 本章知识点
- 本章脚本
- 一. 信息搜集
- 二. IP信息搜集
- 三. WHOIS查询
-
-
- 介绍
- 操作步骤:
- hosts.txt文件:
- hosts.txt文件:未知
-
- 四. 搜集E-mail信息
-
-
- 参数:
- 简介:
- 操作步骤
-
- 五. IP反查
-
-
- 参数:
- 操作步骤:
- 分析
- 注意
-
- 六. DNS信息搜集
-
-
- 参数:
- 介绍:
- DNS系统中,常见的资源记录类型包括以下几种。
- 介绍
- 操作步骤
- 分析
- 七. 检索系统信息
- 参数:
- 操作步骤:
- 分析
-
- 八. 后台打印机服务漏洞
-
-
- 操作步骤
- 分析
-
- 九. 系统漏洞扫描
-
-
- 参数:
- 操作步骤
- 分析:
-
- 十. 扫描Web漏洞
-
-
- 参数:
- 操作步骤
- 分析:
-
- 十一. 通过Snmp列举Windows服务/账户
-
-
- 参数:
- 操作步骤
- 分析
-
- 十二. 枚举DNS服务器的主机名
-
-
- 参数:
- 介绍:
- 操作步骤
- 分析
-
- 十三. HTTP信息搜集
-
-
- 参数:
- HTTP版本探测
- 操作步骤
- 分析
- HTTP头信息探测
- 操作步骤
- 分析
- HTTP目录结构探测
- 操作步骤
- 分析
-
- 十四. 枚举SSL密钥
-
-
- 参数:
- 介绍:
- 操作步骤
- 分析
-
- 十五. SSH服务密钥信息探测
-
-
- 参数:
- 介绍:
- 操作步骤
- 分析
-
-
- 三. 组合 减少时间
-
-
- 1. 参数:-sV -T 4 --version-intensity 1
-
-
- 时间:24.58s
- 系统猜测:大致正确,没有系统的猜测的百分比了,直接猜测某一种系统了
-
- 2. 参数:-sV -O -T 4 --version-intensity 1
-
-
- 时间:35.28s(多了十秒)
- 系统猜测:大致正确,没有系统的猜测的百分比了,直接猜测某一种系统了
-
- 3. 参数:-O -T 4 --version-intensity 2
-
-
- 时间:114.04s(多了三分之二)
- 系统猜测:大致正确,没有系统的猜测的百分比了,直接猜测某一种系统了
-
-
一. 防火墙/IDS逃逸
本章知识点
-
关于防火墙/IDS
-
报文分段
-
指定偏移大小
-
IP欺骗
-
源地址欺骗
-
源端口欺骗
-
指定发包长度
-
目标主机随机排序
-
MAC地址欺骗
本章节将介绍的知识仅供参考,读者切勿用于非法用途,请遵守相应的道德标准。通过对该章的学习可以利用Nmap逃避防火墙/IDS的防护获取信息甚至进行攻击,本章只对实用选项进行典型例子解析,希望可以起到抛砖引玉的作用。
本章选项
下表所示为本章节所需Nmap命令表,为方便读者查阅,笔者特此整理。
本章所需选项
| 选项 | 解释 |
|---|---|
| -f | 报文分段 |
| –mtu | 指定偏移大小 |
| -D | IP欺骗 |
| -sl | 源地址欺骗 |
| –source-port | 源端口欺骗 |
| –data-length | 指定发包长度 |
| –randomize-hosts | 目标主机随机排序 |
| –spoof-mac | MAC地址欺骗 |
一 .关于防火墙/IDS
网络防火墙就是一个位于计算机和它所连接的网络之间的软件。该计算机流入流出的所有网络通信均要经过此防火墙。防火墙对流经它的网络通信进行扫描,这样能够过滤掉一些攻击,以免其在目标计算机上被执行。防火墙还可以关闭不使用的端口,而且还能禁止特定端口的流出通信,封锁特洛伊木马。最后,它可以禁止来自特殊站点的访问,从而防止来自不明入侵者的所有通信。
IDS是英文“Intrusion Detection Systems”的缩写,中文意思是“入侵检测系统”。专业上讲就是依照一定的安全策略,通过软、硬件,对网络、系统的运行状况进行监视,尽可能发现各种攻击企图、攻击行为或者攻击结果,以保证网络系统资源的机密性、完整性和可用性。作一个形象的比喻:假如防火墙是一幢大楼的门锁,那么 IDS就是这幢大楼里的监视系统。一旦小偷爬窗进入大楼,或内部人员有越界行为,只有实时监视系统才能发现情况并发出警告。
实时入侵检测在网络连接过程中进行,系统根据用户的历史行为模型、存储在计算机中的专家知识以及神经网络模型对用户当前的操作进行判断,一旦发现入侵迹象立即断开入侵者与主机的连接,并收集证据和实施数据恢复。这个检测过程是不断循环进行的。而事后入侵检测则是由具有网络安全专业知识的网络管理人员定期或不定期进行的,不具有实时性,因此防御入侵的能力不如实时入侵检测系统。
IDS系统组件之间需要通信,不同厂商的IDS系统之间也需要通信。因此,定义统一的协议,使各部分能够根据协议所制订的标准进行沟通是很有必要的。IETF目前有一个专门的小组IDWG(IntrusionDetection WorkingGroup)负责定义这种通信格式,称作IntrusionDetection ExchangeFormat。目前只有相关的草案,并未形成正式的RFC文档。尽管如此,草案为IDS各部分之间甚至不同IDS系统之间的通信提供层协议,涉及许多其他功能(如可从任意端发起连接,结合了加密、身份验证等)。
二. 报文分段
参数: -f
报文分段的选项是-f。在Nmap使用-f选项时会将TCP头分段在几个包中,使得包过滤器、IDS以及其他工具的检测更加困难。Nmap在IP头后会将包分为8个字节或更小。在使用-f选项的时候需要小心,处置不当时会出现某些错误,这是我们不愿意看到的。
一些主机会禁止相应ICMP请求,对于这种情况就可以使用报文分段的方法来逃避目标防火墙的规则。首先使用Ping扫描目标主机。
[root@localhost ~]# nmap -sX -v -F 192.168.10.1
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:20 CST
Initiating ARP Ping Scan at 12:20
Scanning 192.168.10.1 [1 port]
Completed ARP Ping Scan at 12:20, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:20
Completed Parallel DNS resolution of 1 host. at 12:20, 0.01s elapsed
Initiating XMAS Scan at 12:20
Scanning 192.168.10.1 [100 ports]
Completed XMAS Scan at 12:20, 3.04s elapsed (100 total ports)
Nmap scan report for 192.168.10.1
Host is up (0.000090s latency).
All 100 scanned ports on 192.168.10.1 are open|filtered
MAC Address: 00:50:56:C0:00:08 (VMware)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 3.11 seconds
Raw packets sent: 201 (8.028KB) | Rcvd: 15 (748B)
[root@localhost ~]# nmap -sX -v -f 192.168.10.1
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:21 CST
Initiating ARP Ping Scan at 12:21
Scanning 192.168.10.1 [1 port]
Completed ARP Ping Scan at 12:21, 0.01s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:21
Completed Parallel DNS resolution of 1 host. at 12:21, 0.01s elapsed
Initiating XMAS Scan at 12:21
Scanning 192.168.10.1 [1000 ports]
Completed XMAS Scan at 12:22, 21.17s elapsed (1000 total ports)
Nmap scan report for 192.168.10.1
Host is up (0.000074s latency).
All 1000 scanned ports on 192.168.10.1 are open|filtered
MAC Address: 00:50:56:C0:00:08 (VMware)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 21.23 seconds
Raw packets sent: 2001 (80.028KB) | Rcvd: 98 (5.188KB)
在输出的结果中无法获知目标主机的端口是否开放。此时尝试使用报文分段进行扫描。
[root@localhost ~]# nmap -f -v 192.168.10.1
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:23 CST
Initiating ARP Ping Scan at 12:23
Scanning 192.168.10.1 [1 port]
Completed ARP Ping Scan at 12:23, 0.02s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 12:23
Completed Parallel DNS resolution of 1 host. at 12:23, 0.01s elapsed
Initiating SYN Stealth Scan at 12:23
Scanning 192.168.10.1 [1000 ports]
Discovered open port 3306/tcp on 192.168.10.1
Discovered open port 6000/tcp on 192.168.10.1
Discovered open port 5357/tcp on 192.168.10.1
Discovered open port 903/tcp on 192.168.10.1
Completed SYN Stealth Scan at 12:23, 4.75s elapsed (1000 total ports)
Nmap scan report for 192.168.10.1
Host is up (0.000074s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
903/tcp open iss-console-mgr
3306/tcp open mysql
5357/tcp open wsdapi
6000/tcp open X11
MAC Address: 00:50:56:C0:00:08 (VMware)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 4.82 seconds
Raw packets sent: 1998 (87.896KB) | Rcvd: 29 (1.488KB)
尝试使用报文分段后获得了更多的数据。这说明报文分段能够有效地应对目标主机防火墙的防护规则。
三. 指定偏移大小
参数: --mtu
使用--mtu就可以用来指定偏移大小。MTU,即Maximum Transmission Unit(最大传输单元),此值设定TCP/IP协议传输数据报时的最大传输单元。使用指定的MTU可以达到逃逸防火墙/IDS`的目的,需要注意的是偏移量必须是8的倍数。
[root@localhost ~]# nmap --mtu 16 192.168.10.128
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:25 CST
Nmap scan report for 192.168.10.128
Host is up (0.0029s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:02:A3:30 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.13 seconds
四. IP欺骗
参数: -D
使用-D选项就可以达到使用诱饵进行IP欺骗的作用,在使用该选项对目标进行扫描的时候,会让目标主机误认为是在利用诱饵进行扫描,而不是一个真实的扫描,这样可以躲避防火墙和某些规则的限制,也可以达到隐藏自身的目的,这在实际的扫描中是非常有用的一个选项。
可以使用英文的逗号对每个诱饵主机进行分割,当然也要领会目标主机管理员的想法,他可能会认为该扫描使用的是诱饵主机进行扫描的,而不是真实的扫描地址,因此会忽略这次扫描,反而可以使用自己的真实IP去进行扫描,会达到欺骗目标主机管理员的目的,这样做时最好与诱饵主机交叉使用。
IP欺骗的语法如下:
Nmap-D 【decoyl,decoy2…|RND:number】【目标】
使用-D选项可以指定多个IP地址,或者使用RND随机生成几个地址,在指定的诱饵之间使用逗号进行分割,需要注意的是在进行版本检测或者TCP扫描的时候诱饵是无效的。
[root@localhost ~]# nmap -D RND:11 192.168.10.128
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:30 CST
Nmap scan report for 192.168.10.128
Host is up (0.00063s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:02:A3:30 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.23 seconds
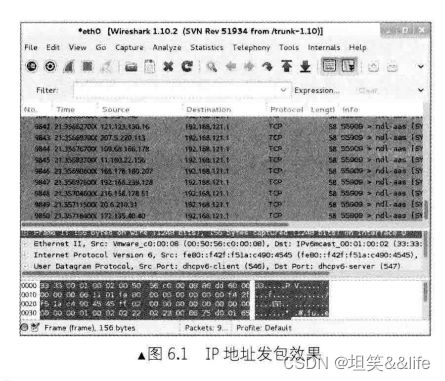
我们通过抓包的方法,看一下Nmap规避防火墙的效果。
如图6.1所示,可以看到有11个随机的、不同的IP地址向目标主机发送了SYN包,其中,192.168.239.128是真实的IP地址。
这种随机的方法或许容易被发现,接下来将指定几个IP地址对目标实施扫描来达到更好的效果。
[root@localhost ~]# nmap -D 192.168.199.1,192.168.199.2,192.168.199.254 192.168.10.1
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:32 CST
Nmap scan report for 192.168.10.1
Host is up (0.000096s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
903/tcp open iss-console-mgr
3306/tcp open mysql
5357/tcp open wsdapi
6000/tcp open X11
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.83 seconds
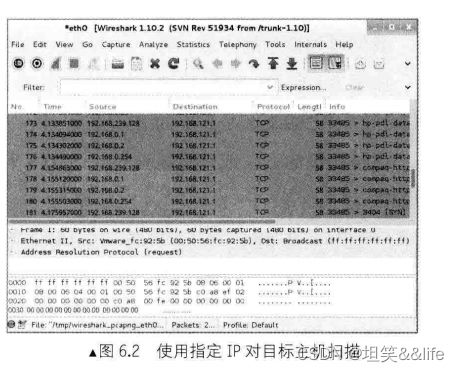
如图6.2所示,通过抓包的方法看到Nmap正在使用我们指定的IP进行对目标主机的扫描。您也可以使用ME选项指定自己的真实IP。
[root@localhost ~]# nmap -D 192.168.199.1,192.168.199.2,192.168.199.254,ME 192.168.10.1
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:35 CST
Nmap scan report for 192.168.10.1
Host is up (0.00014s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
903/tcp open iss-console-mgr
3306/tcp open mysql
5357/tcp open wsdapi
6000/tcp open X11
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 4.76 seconds
注意:
需要注意的是,诱饵主机必须处于工作状态,否则会导致目标主机的SYN洪水攻击。
五. 源地址欺骗
参数: -sI
使用-sI选项就可以进行源地址欺骗。如果Nmap无法确定你的源地址,Nmap会给出相应的提示,我们使用-sI选项指定所需要发包的接口IP地址。
root@Wing:-#nmap -sI www.Oday.co:80192.168.126.131
WARNING:Many people use -Pn w/Idlescan to prevent pings from their true IP.On the otherhand,timing info Nmap gains from pings can allow for faster,more reliable scans.
Starting Nmap 6.40(http://nmap.org)at 2014-06-1214:50 csT
Idle scan using zombie www.Oday.co(210.209.122.11:80);Class:Incremental
Nmap scan report for 192.168.126.131
Host is up(0.051s latency).
Not shown:977 closedlfiltered ports
PORT
STATE STATE SERVICE
21/tcp open ftp
22/tCP open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tep open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgreaql
5900/tcp open vnc
6000/tcp open x11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MaC Address:00:0c:29;E0;2E:76(VMware)
Nmap done:1 Ip address (1 host up)scanned in 40.30 seconds
root@Wing:~#
[root@localhost ~]# nmap -sI www.Oday.co:80 192.168.10.128
WARNING: Many people use -Pn w/Idlescan to prevent pings from their true IP. On the other hand, timing info Nmap gains from pings can allow for faster, more reliable scans.
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 12:46 CST
Could not resolve idle scan zombie host "www.Oday.co": Name or service not known
QUITTING!
-sI选项我们在之前的章节空闲扫描中提到过,但它主要是用作源地址欺骗
六. 源端口欺骗
参数: --source-port
使用--source-port选项就可以进行源端口欺骗,当然也可以使用-g选项,它们是一样的,我们只需要提供一个端口号,Nmap就可以从这些端口中发送数据,因为防火墙对服务器的设置会根据端口选择是否信任数据流,管理员可能会认为这些端口不会有攻击发生,所以可以利用这些端口去进行扫描。
[root@localhost ~]# nmap --source-port 53 192.168.10.128
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:36 CST
Nmap scan report for 192.168.10.128
Host is up (0.000037s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:02:A3:30 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.11 seconds
在这里我们指定的是53端口,一般这是被允许的,当然也可以指定其他的端口进行源端口欺骗。
七. 指定发包长度
参数: --data-length
使用--data-length选项就可以在发送报文的时候指定发包长度。通常情况下,TCP包是40个字节,ICMP Echo有28个字节,所以在原来的报文基础上附加随机数据达到规避防火墙的效果。
[root@localhost ~]# nmap --data-length 30 192.168.10.128
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:39 CST
Nmap scan report for 192.168.10.128
Host is up (0.0025s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:02:A3:30 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 0.14 seconds
以上则是对目标主机发送30个字节大小的包。
八. 目标主机随机排序
参数: --randomize-hosts
使用--randomize-hosts选项就可以对目标主机的顺序进行随机的排序,最多可达8096个主机。单方面使用这个选项对防火墙/IDS逃逸的效果不大,如果配合时间选项则会有很好的效果。
[root@localhost ~]# nmap --randomize-hosts 192.168.10.1-200
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:41 CST
Nmap scan report for 192.168.10.128
Host is up (0.0024s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
MAC Address: 00:0C:29:02:A3:30 (VMware)
Nmap scan report for 192.168.10.2
Host is up (0.00036s latency).
Not shown: 999 closed ports
PORT STATE SERVICE
53/tcp filtered domain
MAC Address: 00:50:56:FB:23:6C (VMware)
Nmap scan report for 192.168.10.1
Host is up (0.000085s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
903/tcp open iss-console-mgr
3306/tcp open mysql
5357/tcp open wsdapi
6000/tcp open X11
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.10.131
Host is up (0.0000020s latency).
Not shown: 997 closed ports
PORT STATE SERVICE
22/tcp open ssh
111/tcp open rpcbind
6000/tcp open X11
Nmap done: 200 IP addresses (4 hosts up) scanned in 6.00 seconds
九. MAC地址欺骗
使用--spoof-mac选项就可以进行MAC地址欺骗。冒失地指定一个MAC定制反而会引起管理员的怀疑,这时我们可以使用字符串“0”随机分配一个MAC地址。这里需要注意的是,此处是数字“0”而不是字母“O”,当然您可以指定一个MAC地址进行欺骗,指定的MAC地址最好是真实存在的,这样才能起到欺骗管理员的效果。使用--spoof-mac选项可以使用的参数包括0、MAC Address、Vendor Name。0表示随机生成一个MAC地址,MAC Address表示用户手动指定一个MAC地址,Vendor Name表示从指定的厂商生成一个MAC地址。
[root@localhost ~]# nmap -sT -PN --spoof-mac 0 192.168.10.128
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:45 CST
Spoofing MAC address 5D:78:C3:A8:A1:0E (No registered vendor)
Nmap scan report for 192.168.10.128
Host is up (0.83s latency).
Not shown: 977 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
23/tcp open telnet
25/tcp open smtp
53/tcp open domain
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
512/tcp open exec
513/tcp open login
514/tcp open shell
1099/tcp open rmiregistry
1524/tcp open ingreslock
2049/tcp open nfs
2121/tcp open ccproxy-ftp
3306/tcp open mysql
5432/tcp open postgresql
5900/tcp open vnc
6000/tcp open X11
6667/tcp open irc
8009/tcp open ajp13
8180/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 1.12 seconds
二. 信息收集
本章知识点
-
信息搜集
-
IP信息搜集
-
WHOIS查询
-
搜集E-mail信息
-
IP反查
-
DNS信息搜集
-
检索系统信息
-
后台打印机服务漏洞
-
系统漏洞扫描
-
扫描Web漏洞
-
通过Snmp列举Windows服务/账户
-
枚举DNS服务器的主机名
-
HTTP信息搜集
-
枚举SSL密钥
-
SSH服务密钥信息探测
本章节将介绍Nmap的NES脚本,脚本是用Lua程序创作的,目前已有好几百种。lua的易用性也让更多的用户加入脚本的创作当中来,本章节通过对Nmap信息搜集脚本的使用让大家了解Nmap的高级技法。
本章脚本
下表所示为本章节所需Nmap命令表,为方便读者查阅,笔者特此整理。
| 脚本 | 解释 |
|---|---|
| –script ip-geolocation-* | IP信息搜集 |
| whois | WHOIS查询 |
| http-email-harvest | 搜集E-mail信息 |
| hostmap-ip2hosts | IP反查 |
| dns-brute | DNS信息搜集 |
| membase-http-info | 检索系统信息 |
| smb-security-mode.nse | 后台打印机服务漏洞 |
| smb-check-vulns.nse | 系统漏洞扫描 |
| http-stored-xss.nse | 扫描Web漏洞 |
| snmp-win32-services | 通过Snmp列举Windows服务/账户 |
| dns-brute | 枚举DNS服务器的主机名 |
| http-headers/hitp-sitemap-generator | HTTP信息搜集 |
| ssl-enum-ciphers | 枚举SSL密钥 |
| ssh-hostkey | SSH服务密钥信息探测 |
一. 信息搜集
在进行渗透测试的时候,首先要做的是对目标进行尽可能全面的信息搜集,在渗透测试中必不可少的就是信息搜集,这是作为渗透思路及方法的铺垫。
信息搜集的方法很多,我们手工也可以对网站进行搜集,也可以借助一些工具对目标站点进行信息搜集,Nmap就是一个不错的选择。Nmap内置了很多插件,可供我们进行信息搜集,可不仅仅是一个端口扫描器这么简单。
二. IP信息搜集
参数:–script ip-geolocation-*
操作步骤
我们首先打开Shell终端,运行以下命令“nmap--script ip-geolocation-*目标”。
[root@localhost ~]# nmap --script ip-geolocation-* www.Oday.co
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:47 CST
Nmap scan report for www.Oday.co (157.7.189.151)
Host is up (0.017s latency).
rDNS record for 157.7.189.151: users213.vip.heteml.jp
All 1000 scanned ports on www.Oday.co (157.7.189.151) are filtered
Host script results:
| ip-geolocation-geoplugin:
| 157.7.189.151 (www.Oday.co)
| coordinates (lat,lon): 35.6897,139.6895
|_ state: , Japan
|_ip-geolocation-maxmind: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 52.26 seconds
分析:
从以上返回来的信息中,我们可以获取目标域名的IP地址,并且还可以确定该IP地址为一个香港地区IP,这个IP的开放端口有80端口、443端口。可以说我们已经初步确定了目标域名的IP及目标主机的端口情况,但需要注意的是,如果目标域名使用了CDN,那么这个方法是无效的,我们获取的只是目标域名的CDN的相关情况,并不是目标域名所对应的真正的IP地址。
注意:
Nmap很早就提供了script脚本,这些脚本包含着不同的功能,现在的脚本允许用户自定义开发。
三. WHOIS查询
参数:--script whois
介绍
WHOIS(读作“Who is”,而非缩写)是用来查询互联网中域名的IP以及所有者等信息的传输协议。早期的WHOIS查询多以命令行接口(Command Line)存在,但是现在出现了一些基于网页接口的简化在线查询工具,甚至可以一次向不同的数据库查询。网页接口的查询工具仍然依赖WHOIS协议向服务器发送查询请求,命令行接口的工具仍然被系统管理员广泛使用。
WHOIS通常使用TCP协议43端口。每个域名或IP的WHOIS信息由对应的管理机构保存,例如,以.com结尾的域名的WHOIS信息由.com域名运营商VeriSign管理,中国国家顶级域名.cn由CNNIC管理。
通常情况下,域名或IP的信息可以由公众自由查询获得,具体的查询方法是登录由管理机构提供的WHOIS服务器,输入待查询的域名进行查询。
操作步骤:
使用命令“nmap --script whois目标”即可查询目标域名whois信息。
hosts.txt文件:
210.209.122.0/24
74.125.0.0/24
59.0.0.0/24
[root@localhost ~]# nmap --script whois www.Oday.co
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:53 CST
Nmap scan report for www.Oday.co (157.7.189.151)
Host is up (0.012s latency).
rDNS record for 157.7.189.151: users213.vip.heteml.jp
Not shown: 998 filtered ports
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Host script results:
| whois: Record found at whois.apnic.net
| inetnum: 157.7.188.0 - 157.7.189.255
| netname: HETEML-JP
| descr: paperboy&co. Inc.
|_country: JP
Nmap done: 1 IP address (1 host up) scanned in 61.87 seconds
分析:
从返回的数据来看,我们可以确定目标域名的IP地址及其开放的端口,也搜集到了域名提供商的网址以及域名解析地址和E-mail地址。在使用whois查询的时候要切记whois都是小写字母。查询到的结果仅供参考,大部分的网站现在都启用了whois保护,对于域名所有者的姓名、电话等都会隐藏,我们可以查询该域名的历史whois,历史whois可能还没有启用whois保护。我们还可以启用其他的几个whois查询脚本。
[root@localhost ~]# nmap --script whois --script-args whois.whodb=nofollow www.Oday.co
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 13:57 CST
Nmap scan report for www.Oday.co (157.7.189.151)
Host is up (0.016s latency).
rDNS record for 157.7.189.151: users213.vip.heteml.jp
Not shown: 998 filtered ports
PORT STATE SERVICE
80/tcp open http
443/tcp open https
Host script results:
|_whois: ERROR: Script execution failed (use -d to debug)
Nmap done: 1 IP address (1 host up) scanned in 26.50 seconds
不同的脚本返回的结果也不尽相同。如果目标域名比较多,我们可以使用列表的方式进行查询。
[root@localhost ~]# nmap -sn --script whois -v -iL host.txt
Starting Nmap 6.40 ( http://nmap.org ) at 2023-10-17 14:03 CST
NSE: Loaded 1 scripts for scanning.
NSE: Script Pre-scanning.
Initiating Ping Scan at 14:03
Scanning 768 hosts [4 ports/host]
Completed Ping Scan at 14:03, 31.46s elapsed (768 total hosts)
Initiating Parallel DNS resolution of 768 hosts. at 14:03
Completed Parallel DNS resolution of 768 hosts. at 14:03, 0.72s elapsed
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.57s elapsed
Nmap scan report for 210.209.122.0
Host is up (0.000077s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122001.ctinets.com (210.209.122.1)
Host is up (0.043s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122002.ctinets.com (210.209.122.2)
Host is up (0.00013s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122003.ctinets.com (210.209.122.3)
Host is up (0.046s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122004.ctinets.com (210.209.122.4)
Host is up (0.000059s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122005.ctinets.com (210.209.122.5)
Host is up (0.000047s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122006.ctinets.com (210.209.122.6)
Host is up (0.000054s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122007.ctinets.com (210.209.122.7)
Host is up (0.000064s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122008.ctinets.com (210.209.122.8)
Host is up (0.050s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122009.ctinets.com (210.209.122.9)
Host is up (0.00010s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122010.ctinets.com (210.209.122.10)
Host is up (0.000070s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122011.ctinets.com (210.209.122.11)
Host is up (0.000060s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122012.ctinets.com (210.209.122.12)
Host is up (0.000048s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122013.ctinets.com (210.209.122.13)
Host is up (0.042s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122014.ctinets.com (210.209.122.14)
Host is up (0.00082s latency).
Host script results:
| whois: Record found at whois.apnic.net
| inetnum: 210.209.122.0 - 210.209.122.255
| netname: NWTCRS-HK
| descr: NWT CRS Dynamic Pool
| country: HK
| role: ABUSE HKBNESLHK
| email: esabuse@hkbnes.net
| person: internet Data Centre
|_email: idc@hkbnes.net
Nmap scan report for 210209122015.ctinets.com (210.209.122.15)
Host is up (0.045s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122016.ctinets.com (210.209.122.16)
Host is up (0.000038s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122017.ctinets.com (210.209.122.17)
Host is up (0.00084s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122018.ctinets.com (210.209.122.18)
Host is up (0.000077s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122019.ctinets.com (210.209.122.19)
Host is up (0.000071s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122020.ctinets.com (210.209.122.20)
Host is up (0.000053s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122021.ctinets.com (210.209.122.21)
Host is up (0.000031s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122022.ctinets.com (210.209.122.22)
Host is up (0.000032s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122023.ctinets.com (210.209.122.23)
Host is up (0.000090s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122024.ctinets.com (210.209.122.24)
Host is up (0.00015s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122025.ctinets.com (210.209.122.25)
Host is up (0.00016s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122026.ctinets.com (210.209.122.26)
Host is up (0.000061s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122027.ctinets.com (210.209.122.27)
Host is up (0.000080s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122028.ctinets.com (210.209.122.28)
Host is up (0.0012s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122029.ctinets.com (210.209.122.29)
Host is up (0.0012s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122030.ctinets.com (210.209.122.30)
Host is up (0.0012s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122031.ctinets.com (210.209.122.31)
Host is up (0.0012s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122032.ctinets.com (210.209.122.32)
Host is up (0.000057s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122033.ctinets.com (210.209.122.33)
Host is up (0.0011s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122034.ctinets.com (210.209.122.34)
Host is up (0.00032s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122035.ctinets.com (210.209.122.35)
Host is up (0.0011s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122036.ctinets.com (210.209.122.36)
Host is up (0.00036s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122037.ctinets.com (210.209.122.37)
Host is up (0.0011s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122038.ctinets.com (210.209.122.38)
Host is up (0.00040s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122039.ctinets.com (210.209.122.39)
Host is up (0.00038s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122040.ctinets.com (210.209.122.40)
Host is up (0.000076s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122041.ctinets.com (210.209.122.41)
Host is up (0.000061s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122042.ctinets.com (210.209.122.42)
Host is up (0.000056s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122043.ctinets.com (210.209.122.43)
Host is up (0.00044s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122044.ctinets.com (210.209.122.44)
Host is up (0.000039s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122045.ctinets.com (210.209.122.45)
Host is up (0.000031s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122046.ctinets.com (210.209.122.46)
Host is up (0.00013s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122047.ctinets.com (210.209.122.47)
Host is up (0.00029s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122048.ctinets.com (210.209.122.48)
Host is up (0.000035s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122049.ctinets.com (210.209.122.49)
Host is up (0.000039s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122050.ctinets.com (210.209.122.50)
Host is up (0.00061s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122051.ctinets.com (210.209.122.51)
Host is up (0.00021s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122052.ctinets.com (210.209.122.52)
Host is up (0.00021s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122053.ctinets.com (210.209.122.53)
Host is up (0.051s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122054.ctinets.com (210.209.122.54)
Host is up (0.000036s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122055.ctinets.com (210.209.122.55)
Host is up (0.00010s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122056.ctinets.com (210.209.122.56)
Host is up (0.000069s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122057.ctinets.com (210.209.122.57)
Host is up (0.00067s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122058.ctinets.com (210.209.122.58)
Host is up (0.00017s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122059.ctinets.com (210.209.122.59)
Host is up (0.000041s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122060.ctinets.com (210.209.122.60)
Host is up (0.00064s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122061.ctinets.com (210.209.122.61)
Host is up (0.00062s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122062.ctinets.com (210.209.122.62)
Host is up (0.044s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122063.ctinets.com (210.209.122.63)
Host is up (0.00014s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122064.ctinets.com (210.209.122.64)
Host is up (0.000033s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122065.ctinets.com (210.209.122.65)
Host is up (0.043s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122066.ctinets.com (210.209.122.66)
Host is up (0.046s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122067.ctinets.com (210.209.122.67)
Host is up (0.000030s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122068.ctinets.com (210.209.122.68)
Host is up (0.00055s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122069.ctinets.com (210.209.122.69)
Host is up (0.000033s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122070.ctinets.com (210.209.122.70)
Host is up (0.045s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122071.ctinets.com (210.209.122.71)
Host is up (0.000083s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122072.ctinets.com (210.209.122.72)
Host is up (0.000027s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122073.ctinets.com (210.209.122.73)
Host is up (0.047s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122074.ctinets.com (210.209.122.74)
Host is up (0.000051s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122075.ctinets.com (210.209.122.75)
Host is up (0.047s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122076.ctinets.com (210.209.122.76)
Host is up (0.000037s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122077.ctinets.com (210.209.122.77)
Host is up (0.00030s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122078.ctinets.com (210.209.122.78)
Host is up (0.000056s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122079.ctinets.com (210.209.122.79)
Host is up (0.043s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122080.ctinets.com (210.209.122.80)
Host is up (0.00012s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122081.ctinets.com (210.209.122.81)
Host is up (0.000026s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122082.ctinets.com (210.209.122.82)
Host is up (0.045s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122083.ctinets.com (210.209.122.83)
Host is up (0.000065s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122084.ctinets.com (210.209.122.84)
Host is up (0.00014s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122085.ctinets.com (210.209.122.85)
Host is up (0.00013s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122086.ctinets.com (210.209.122.86)
Host is up (0.000034s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122087.ctinets.com (210.209.122.87)
Host is up (0.045s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122088.ctinets.com (210.209.122.88)
Host is up (0.046s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122089.ctinets.com (210.209.122.89)
Host is up (0.000095s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122090.ctinets.com (210.209.122.90)
Host is up (0.049s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122091.ctinets.com (210.209.122.91)
Host is up (0.00019s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122092.ctinets.com (210.209.122.92)
Host is up (0.000033s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122093.ctinets.com (210.209.122.93)
Host is up (0.000065s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122094.ctinets.com (210.209.122.94)
Host is up (0.000024s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122095.ctinets.com (210.209.122.95)
Host is up (0.000027s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122096.ctinets.com (210.209.122.96)
Host is up (0.000023s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122097.ctinets.com (210.209.122.97)
Host is up (0.000025s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122098.ctinets.com (210.209.122.98)
Host is up (0.000028s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122099.ctinets.com (210.209.122.99)
Host is up (0.041s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122100.ctinets.com (210.209.122.100)
Host is up (0.000097s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122101.ctinets.com (210.209.122.101)
Host is up (0.000029s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122102.ctinets.com (210.209.122.102)
Host is up (0.000025s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122103.ctinets.com (210.209.122.103)
Host is up (0.000031s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122104.ctinets.com (210.209.122.104)
Host is up (0.000055s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122105.ctinets.com (210.209.122.105)
Host is up (0.00013s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122106.ctinets.com (210.209.122.106)
Host is up (0.000051s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122107.ctinets.com (210.209.122.107)
Host is up (0.00020s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122108.ctinets.com (210.209.122.108)
Host is up (0.00019s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122109.ctinets.com (210.209.122.109)
Host is up (0.00015s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122110.ctinets.com (210.209.122.110)
Host is up (0.045s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122111.ctinets.com (210.209.122.111)
Host is up (0.00014s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122112.ctinets.com (210.209.122.112)
Host is up (0.00011s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122113.ctinets.com (210.209.122.113)
Host is up (0.00011s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122114.ctinets.com (210.209.122.114)
Host is up (0.000079s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122115.ctinets.com (210.209.122.115)
Host is up (0.00010s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122116.ctinets.com (210.209.122.116)
Host is up (0.00012s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122117.ctinets.com (210.209.122.117)
Host is up (0.000080s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122118.ctinets.com (210.209.122.118)
Host is up (0.000042s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122119.ctinets.com (210.209.122.119)
Host is up (0.00088s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122120.ctinets.com (210.209.122.120)
Host is up (0.000091s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122121.ctinets.com (210.209.122.121)
Host is up (0.000067s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122122.ctinets.com (210.209.122.122)
Host is up (0.000049s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122123.ctinets.com (210.209.122.123)
Host is up (0.000064s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122124.ctinets.com (210.209.122.124)
Host is up (0.000044s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122125.ctinets.com (210.209.122.125)
Host is up (0.051s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122126.ctinets.com (210.209.122.126)
Host is up (0.000025s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122127.ctinets.com (210.209.122.127)
Host is up (0.000042s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122128.ctinets.com (210.209.122.128)
Host is up (0.053s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122129.ctinets.com (210.209.122.129)
Host is up (0.00022s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122130.ctinets.com (210.209.122.130)
Host is up (0.000061s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122131.ctinets.com (210.209.122.131)
Host is up (0.000032s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122132.ctinets.com (210.209.122.132)
Host is up (0.000047s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122133.ctinets.com (210.209.122.133)
Host is up (0.000056s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122134.ctinets.com (210.209.122.134)
Host is up (0.00048s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122135.ctinets.com (210.209.122.135)
Host is up (0.047s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122136.ctinets.com (210.209.122.136)
Host is up (0.00048s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122137.ctinets.com (210.209.122.137)
Host is up (0.00047s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122138.ctinets.com (210.209.122.138)
Host is up (0.048s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122139.ctinets.com (210.209.122.139)
Host is up (0.046s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122140.ctinets.com (210.209.122.140)
Host is up (0.00045s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122141.ctinets.com (210.209.122.141)
Host is up (0.046s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122142.ctinets.com (210.209.122.142)
Host is up (0.00044s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122143.ctinets.com (210.209.122.143)
Host is up (0.00042s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
NSE: Script scanning 16 hosts.
Initiating NSE at 14:03
Completed NSE at 14:03, 0.00s elapsed
Nmap scan report for 210209122144.ctinets.com (210.209.122.144)
Host is up (0.000081s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122145.ctinets.com (210.209.122.145)
Host is up (0.000084s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122146.ctinets.com (210.209.122.146)
Host is up (0.00050s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122147.ctinets.com (210.209.122.147)
Host is up (0.000041s latency).
Host script results:
|_whois: See the result for 210.209.122.14.
Nmap scan report for 210209122148.ctinets.com (210.209.122.148)
Host is up (0.000039s latency).
Host s