k8s的“前端”——ingress
目录
Ingress 简介
Ingress 组成
Ingress 工作原理
部署 nginx-ingress-controller
ingress 暴露服务的方式
DaemonSet+HostNetwork+nodeSelecto
Deployment+NodePort模式的Service
创建虚拟主机资源
Ingress HTTPS 代理访问
Nginx 进行重写
Nginx 进行 BasicAuth
总结
Ingress 简介
service的作用体现在两个方面,对集群内部,它不断跟踪pod的变化,更新endpoint中对应pod的对象,提供了ip不断变化的pod的服务发现机制;对集群外部,他类似负载均衡器,可以在集群内外部对pod进行访问。
在Kubernetes中,Pod的IP地址和service的ClusterIP仅可以在集群网络内部使用,对于集群外的应用是不可见的。为了使外部的应用能够访问集群内的服务,Kubernetes目前提供了以下几种方案:
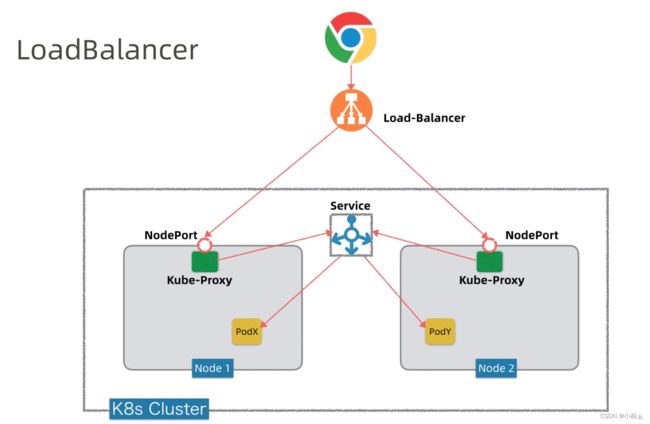
●NodePort:将service暴露在节点网络上,NodePort背后就是Kube-Proxy,Kube-Proxy是沟通service网络、Pod网络和节点网络的桥梁。 测试环境使用还行,当有几十上百的服务在集群中运行时,NodePort的端口管理就是个灾难。因为每个端口只能是一种服务,端口范围只能是 30000-32767。
●LoadBalancer:通过设置LoadBalancer映射到云服务商提供的LoadBalancer地址。这种用法仅用于在公有云服务提供商的云平台上设置 Service 的场景。受限于云平台,且通常在云平台部署LoadBalancer还需要额外的费用。 在service提交后,Kubernetes就会调用CloudProvider在公有云上为你创建一个负载均衡服务,并且把被代理的Pod的IP地址配置给负载均衡服务做后端。
externalIPs:service允许为其分配外部IP,如果外部IP路由到集群中一个或多个Node上,Service会被暴露给这些externalIPs。通过外部IP进入到集群的流量,将会被路由到Service的Endpoint上。
●Ingress:只需一个或者少量的公网IP和LB,即可同时将多个HTTP服务暴露到外网,七层反向代理。 可以简单理解为service的service,它其实就是一组基于域名和URL路径,把用户的请求转发到一个或多个service的规则。
Ingress 组成
●ingress: ingress是一个API对象,通过yaml文件来配置,ingress对象的作用是定义请求如何转发到service的规则,可以理解为配置模板。 ingress通过http或https暴露集群内部service,给service提供外部URL、负载均衡、SSL/TLS能力以及基于域名的反向代理。ingress要依靠 ingress-controller 来具体实现以上功能。
●ingress-controller: ingress-controller是具体实现反向代理及负载均衡的程序,对ingress定义的规则进行解析,根据配置的规则来实现请求转发。 ingress-controller并不是k8s自带的组件,实际上ingress-controller只是一个统称,用户可以选择不同的ingress-controller实现,目前,由k8s维护的ingress-controller只有google云的GCE与ingress-nginx两个,其他还有很多第三方维护的ingress-controller,具体可以参考官方文档。但是不管哪一种ingress-controller,实现的机制都大同小异,只是在具体配置上有差异。 一般来说,ingress-controller的形式都是一个pod,里面跑着daemon程序和反向代理程序。daemon负责不断监控集群的变化,根据 ingress对象生成配置并应用新配置到反向代理,比如ingress-nginx就是动态生成nginx配置,动态更新upstream,并在需要的时候reload程序应用新配置。为了方便,后面的例子都以k8s官方维护的ingress-nginx为例。
Ingress-Nginx github 地址:GitHub - kubernetes/ingress-nginx: NGINX Ingress Controller for Kubernetes
Ingress-Nginx 官方网站:Welcome - NGINX Ingress Controller
总结:ingress-controller才是负责具体转发的组件,通过各种方式将它暴露在集群入口,外部对集群的请求流量会先到 ingress-controller, 而ingress对象是用来告诉ingress-controller该如何转发请求,比如哪些域名、哪些URL要转发到哪些service等等。
Ingress 工作原理
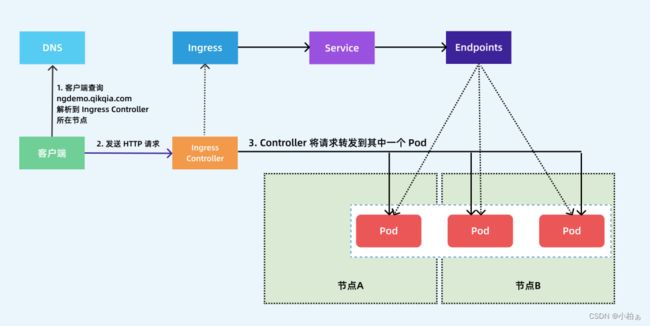
(1)ingress-controller通过和 kubernetes APIServer 交互,动态的去感知集群中ingress规则变化,
(2)然后读取它,按照自定义的规则,规则就是写明了哪个域名对应哪个service,生成一段nginx配置,
(3)再写到nginx-ingress-controller的pod里,这个ingress-controller的pod里运行着一个Nginx服务,控制器会把生成的 nginx配置写入 /etc/nginx.conf文件中,
(4)然后reload一下使配置生效。以此达到域名区分配置和动态更新的作用。
部署 nginx-ingress-controller
1、部署ingress-controller pod及相关资源
mkdir /opt/ingress
cd /opt/ingress官方下载地址: wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.25.0/deploy/static/mandatory.yaml
上面可能无法下载,可用国内的 gitee
wget https://gitee.com/mirrors/ingress-nginx/raw/nginx-0.25.0/deploy/static/mandatory.yaml
wget https://gitee.com/mirrors/ingress-nginx/raw/nginx-0.30.0/deploy/static/mandatory.yaml
#mandatory.yaml文件中包含了很多资源的创建,包括namespace、ConfigMap、role,ServiceAccount等等所有部署ingress-controller需要的资源。
ingress 暴露服务的方式
●方式一:Deployment+LoadBalancer 模式的 Service 如果要把ingress部署在公有云,那用这种方式比较合适。用Deployment部署ingress-controller,创建一个 type为 LoadBalancer 的 service 关联这组 pod。大部分公有云,都会为 LoadBalancer 的 service 自动创建一个负载均衡器,通常还绑定了公网地址。 只要把域名解析指向该地址,就实现了集群服务的对外暴露
●方式二:DaemonSet+HostNetwork+nodeSelector 用DaemonSet结合nodeselector来部署ingress-controller到特定的node上,然后使用HostNetwork直接把该pod与宿主机node的网络打通,直接使用宿主机的80/433端口就能访问服务。这时,ingress-controller所在的node机器就很类似传统架构的边缘节点,比如机房入口的nginx服务器。该方式整个请求链路最简单,性能相对NodePort模式更好。缺点是由于直接利用宿主机节点的网络和端口,一个node只能部署一个ingress-controller pod。 比较适合大并发的生产环境使用。
●方式三:Deployment+NodePort模式的Service 同样用deployment模式部署ingress-controller,并创建对应的service,但是type为NodePort。这样,ingress就会暴露在集群节点ip的特定端口上。由于nodeport暴露的端口是随机端口,一般会在前面再搭建一套负载均衡器来转发请求。该方式一般用于宿主机是相对固定的环境ip地址不变的场景。 NodePort方式暴露ingress虽然简单方便,但是NodePort多了一层NAT,在请求量级很大时可能对性能会有一定影响。
DaemonSet+HostNetwork+nodeSelecto
上传mandatory.yaml文件,并修改
[root@master01 /opt/ingress]# vim mandatory.yaml
...
#apiVersion: rbac.authorization.k8s.io/v1beta1
apiVersion: rbac.authorization.k8s.io/v1
#RBAC相关资源从1.17版本开始改用rbac.authorization.k8s.io/v1,rbac.authorization.k8s.io/v1beta1在1.22版本即将弃用
kind: ClusterRole
metadata:
name: nginx-ingress-clusterrole
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- "extensions"
- "networking.k8s.io" # (0.25版本)增加 networking.k8s.io Ingress 资源的 api
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- "extensions"
- "networking.k8s.io" # (0.25版本)增加 networking.k8s.io/v1 Ingress 资源的 api
resources:
- ingresses/status
verbs:
- update
apiVersion: apps/v1
# 修改 kind
# kind: Deployment
kind: DaemonSet
metadata:
name: nginx-ingress-controller
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
# 删除Replicas
# replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
prometheus.io/port: "10254"
prometheus.io/scrape: "true"
spec:
# 使用主机网络
hostNetwork: true
# 选择节点运行
nodeSelector:
ingress: devops
serviceAccountName: nginx-ingress-serviceaccount指定 nginx-ingress-controller 运行在 node02 节点
[root@master01 /opt/ingress]# kubectl label nodes node02 ingress=devops
node/node02 labeled
[root@master01 /opt/ingress]# kubectl get nodes --show-labels
NAME STATUS ROLES AGE VERSION LABELS
master01 Ready control-plane,master 3d21h v1.20.11 beta.kubernetes.io/arch=amd64,beta.kubernetes.io/os=linux,kubernetes.io/arch=amd64,kubernetes.io/hostname=master01,kubernetes.io/os=linux,node-role.kubernetes.io/control-plane=,node-role.kubernetes.io/master=
node01 Ready 3d21h v1.20.11 beta.kubernetes.io/arch=amd64,beta.kubernetes.io/os=linux,kubernetes.io/arch=amd64,kubernetes.io/hostname=node01,kubernetes.io/os=linux
node02 Ready 3d21h v1.20.11 beta.kubernetes.io/arch=amd64,beta.kubernetes.io/os=linux,ingress=devops,kubernetes.io/arch=amd64,kubernetes.io/hostname=node02,kubernetes.io/os=linux
在 node2 节点上传 nginx-ingress-controller 镜像压缩包 ingree.contro.tar.gz 并解压和加载镜像
[root@node02 ~]# tar -zxf ingree.contro.tar.gz
[root@node02 ~]# docker load -i ingree.contro.tar
861ac8268e83: Loading layer [==================================================>] 54MB/54MB
65108a495798: Loading layer [==================================================>] 26.45MB/26.45MB
b0f2b459d4e3: Loading layer [==================================================>] 1.931MB/1.931MB
dc166b174efb: Loading layer [==================================================>] 330.1MB/330.1MB
e3e97f070635: Loading layer [==================================================>] 728.6kB/728.6kB
b87f06926b0d: Loading layer [==================================================>] 43.05MB/43.05MB
17b3679fe89a: Loading layer [==================================================>] 8.192kB/8.192kB
2bb74ea2be4a: Loading layer [==================================================>] 2.56kB/2.56kB
f1980a0b3af3: Loading layer [==================================================>] 6.144kB/6.144kB
74e8ef22671f: Loading layer [==================================================>] 35.78MB/35.78MB
6dd0b74b8a3e: Loading layer [==================================================>] 21.37MB/21.37MB
6bcbfd84ac45: Loading layer [==================================================>] 7.168kB/7.168kB
Loaded image: quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.25.0 启动 nginx-ingress-controller
[root@master01 /opt/ingress]# kubectl apply -f mandatory.yaml
namespace/ingress-nginx created
configmap/nginx-configuration created
configmap/tcp-services created
configmap/udp-services created
serviceaccount/nginx-ingress-serviceaccount created
clusterrole.rbac.authorization.k8s.io/nginx-ingress-clusterrole created
role.rbac.authorization.k8s.io/nginx-ingress-role created
rolebinding.rbac.authorization.k8s.io/nginx-ingress-role-nisa-binding created
clusterrolebinding.rbac.authorization.k8s.io/nginx-ingress-clusterrole-nisa-binding created
daemonset.apps/nginx-ingress-controller creatednginx-ingress-controller 已经运行 node02 节点
[root@master01 /opt/ingress]# kubectl get pods -n ingress-nginx -o wide
NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES
nginx-ingress-controller-dv69n 1/1 Running 0 17m 192.168.37.105 node02 此时,查看node02的nginx服务
[root@node02 ~]# netstat -natp |grep nginx
tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 97117/nginx: master
tcp 0 0 0.0.0.0:8181 0.0.0.0:* LISTEN 97117/nginx: master
tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 97117/nginx: master
tcp 0 0 10.96.0.1:36154 10.96.0.1:443 ESTABLISHED 97071/nginx-ingress
tcp6 0 0 :::10254 :::* LISTEN 97071/nginx-ingress由于配置了 hostnetwork,nginx 已经在 node 主机本地监听 80/443/8181 端口。其中 8181 是 nginx-controller 默认配置的一个 default backend(Ingress 资源没有匹配的 rule 对象时,流量就会被导向这个 default backend)。 这样,只要访问 node 主机有公网 IP,就可以直接映射域名来对外网暴露服务了。如果要 nginx 高可用的话,可以在多个 node 上部署,并在前面再搭建一套 LVS+keepalived 做负载均衡。
创建 ingress 规则
[root@master01 /opt/ingress]# vim svc-nginx.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-app
spec:
replicas: 2
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx
imagePullPolicy: IfNotPresent
ports:
- containerPort: 80
---
apiVersion: v1
kind: Service
metadata:
name: nginx-app-svc
spec:
type: ClusterIP
ports:
- protocol: TCP
port: 80
targetPort: 80
selector:
app: nginx
[root@master01 /opt/ingress]# kubectl apply -f svc-nginx.yaml
deployment.apps/nginx-app created
service/nginx-app-svc created
[root@master01 /opt/ingress]# kubectl get pods
NAME READY STATUS RESTARTS AGE
nginx-app-845d4d9dff-b6vs5 1/1 Running 0 5s
nginx-app-845d4d9dff-phbq7 1/1 Running 0 5s
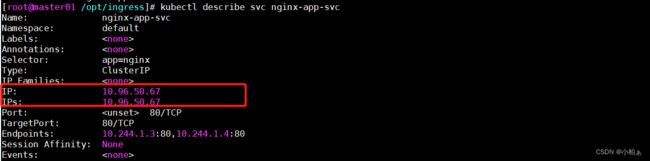
[root@master01 /opt/ingress]# kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
kubernetes ClusterIP 10.96.0.1 443/TCP 3d22h
nginx-app-svc ClusterIP 10.96.50.67 80/TCP 9s
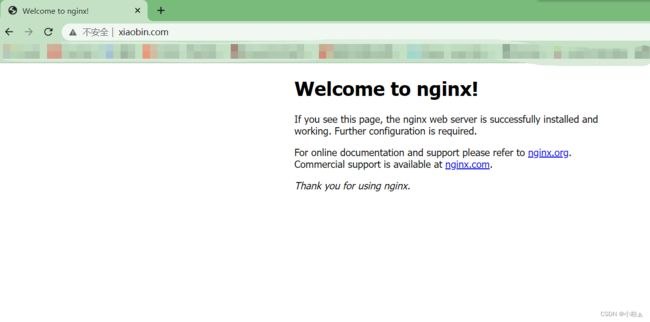
[root@master01 /opt/ingress]# curl 10.96.50.67
Welcome to nginx!
Welcome to nginx!
If you see this page, the nginx web server is successfully installed and
working. Further configuration is required.
For online documentation and support please refer to
nginx.org.
Commercial support is available at
nginx.com.
Thank you for using nginx.
为什么能访问?
创建 ingress
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-ingress
spec:
rules:
- host: www.xiaobin.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: nginx-app-svc
port:
number: 80[root@master01 /opt/ingress]# kubectl apply -f ingress-app.yaml
ingress.networking.k8s.io/nginx-ingress created
[root@master01 /opt/ingress]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
nginx-ingress www.xiaobin.com 80 6s
打开hosts文件,添加映射
192.168.37.105 www.xiaobin.com访问浏览器
也可以将两个node节点全作为标签!!!
Deployment+NodePort模式的Service
下载 nginx-ingress-controller 和 ingress-nginx 暴露端口配置文件
官方下载地址:
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/mandatory.yaml
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/provider/baremetal/service-nodeport.yaml
国内 gitee 资源地址:
wget https://gitee.com/mirrors/ingress-nginx/raw/nginx-0.30.0/deploy/static/mandatory.yaml
wget https://gitee.com/mirrors/ingress-nginx/raw/nginx-0.30.0/deploy/static/provider/baremetal/service-nodeport.yaml
[root@master01 /opt/ingress]# mkdir ingress3.0
[root@master01 /opt/ingress]# cd ingress3.0/
[root@master01 /opt/ingress/ingress3.0]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/mandatory.yaml
[root@master01 /opt/ingress/ingress3.0]# wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.30.0/deploy/static/provider/baremetal/service-nodeport.yaml为了好区分,把hostwork 的mandatory.yaml删除
[root@master01 /opt/ingress]# kubectl delete -f mandatory.yaml
namespace "ingress-nginx" deleted
configmap "nginx-configuration" deleted
configmap "tcp-services" deleted
configmap "udp-services" deleted
serviceaccount "nginx-ingress-serviceaccount" deleted
clusterrole.rbac.authorization.k8s.io "nginx-ingress-clusterrole" deleted
role.rbac.authorization.k8s.io "nginx-ingress-role" deleted
rolebinding.rbac.authorization.k8s.io "nginx-ingress-role-nisa-binding" deleted
clusterrolebinding.rbac.authorization.k8s.io "nginx-ingress-clusterrole-nisa-binding" deleted启动 nginx-ingress-controller
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f mandatory.yaml
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f service-nodeport.yaml其实此时,已经实现nodeport转发了
浏览器访问,加端口
流程:
http://www.xiaobin.com:32584/ ->ingress-nginx service资源[-> nginx-ingress-controller pod->根据主机名转发到绑定的业务service nginx-svc ->业务pod demo-nginx
创建虚拟主机资源
再重新创建两个pod,删除之前做过的所有pod和svc(也可以不删,我是出了点状况)
[root@master01 /opt/ingress/ingress3.0]# kubectl delete deployments.apps nginx-app
deployment.apps "nginx-app" deleted
[root@master01 /opt/ingress/ingress3.0]# kubectl delete svc nginx-app-svc
service "nginx-app-svc" deleted
[root@master01 /opt/ingress/ingress3.0]# kubectl get pod,svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.96.0.1 443/TCP 4d 重新创建俩个pods
[root@master01 /opt/ingress/ingress3.0]# kubectl create deployment myapp01 --image=nginx --replicas=2 --dry-run=client -o yaml > demo1.yamlvim demo1.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
creationTimestamp: null
labels:
app: myapp01
name: myapp01
spec:
replicas: 2
selector:
matchLabels:
app: myapp01
strategy: {}
template:
metadata:
creationTimestamp: null
labels:
app: myapp01
spec:
containers:
- image: nginx
name: myapp
vim demo2.yaml
apiVersion: apps/v1
kind: Deployment
metadata:
creationTimestamp: null
labels:
app: myapp02
name: myapp02
spec:
replicas: 2
selector:
matchLabels:
app: myapp02
strategy: {}
template:
metadata:
creationTimestamp: null
labels:
app: myapp02
spec:
containers:
- image: nginx
name: myapp
~
创建svc
[root@master01 /opt/ingress/ingress3.0]# kubectl expose deployment myapp01 --port=80 --target-port=80 --name=myapp01-svc --dry-run=client -o yaml >svc1.yamlapiVersion: v1
kind: Service
metadata:
labels:
app: myapp01
name: myapp01-svc
spec:
ports:
- port: 80
protocol: TCP
targetPort: 80
selector:
app: myapp01
apiVersion: v1
kind: Service
metadata:
labels:
app: myapp02
name: myapp02-svc
spec:
ports:
- port: 80
protocol: TCP
targetPort: 80
selector:
app: myapp02[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f demo1.yaml
deployment.apps/myapp01 created
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f demo2.yaml
deployment.apps/myapp02 created
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f svc1.yaml
service/myapp01-svc created
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f svc2.yaml
service/myapp02-svc created
[root@master01 /opt/ingress/ingress3.0]# kubectl get pod,svc
NAME READY STATUS RESTARTS AGE
pod/myapp01-7d6f8bbdc9-6b826 1/1 Running 0 7m40s
pod/myapp01-7d6f8bbdc9-hn2jh 1/1 Running 0 7m40s
pod/myapp02-7f546496d-d4dwh 1/1 Running 0 7m36s
pod/myapp02-7f546496d-qqvzr 1/1 Running 0 7m36s
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
service/kubernetes ClusterIP 10.96.0.1 443/TCP 4d
service/myapp01-svc ClusterIP 10.96.69.249 80/TCP 13s
service/myapp02-svc ClusterIP 10.96.218.200 80/TCP 10s
[root@master01 /opt/ingress/ingress3.0]# kubectl get endpoints
NAME ENDPOINTS AGE
kubernetes 192.168.37.100:6443 4d
myapp01-svc 10.244.1.5:80,10.244.2.4:80 8m43s
myapp02-svc 10.244.1.6:80,10.244.2.5:80 8m40s
创建ingress资源
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress1
spec:
rules:
- host: www.xiaobin1.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp01-svc
port:
number: 80
---
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress2
spec:
rules:
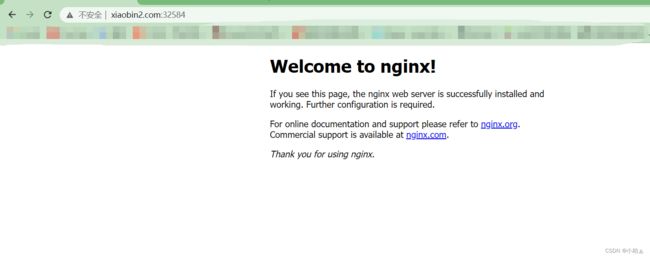
- host: www.xiaobin2.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp02-svc
port:
number: 80
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f ingress-nginx.yaml
ingress.networking.k8s.io/ingress1 created
ingress.networking.k8s.io/ingress2 created查看svc 端口
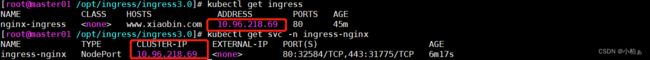
[root@master01 /opt/ingress/ingress3.0]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress1 www.xiaobin1.com 10.96.218.69 80 37s
ingress2 www.xiaobin2.com 10.96.218.69 80 37s
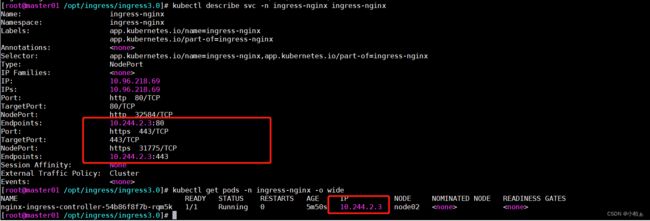
[root@master01 /opt/ingress/ingress3.0]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx NodePort 10.96.218.69 80:32584/TCP,443:31775/TCP 47m 访问测试
Ingress HTTPS 代理访问
创建ssl证书
[root@master01 /opt/ingress/ingress3.0]# mkdir ssl
[root@master01 /opt/ingress/ingress3.0]# cd ssl/
[root@master01 /opt/ingress/ingress3.0/ssl]# openssl req -x509 -sha256 -nodes -days 365 -newkey rsa:2048 -keyout tls.key -out tls.crt -subj "/CN=nginxsvc/O=nginxsvc"Generating a 2048 bit RSA private key
.........................................................+++
.....................+++
writing new private key to 'tls.key'
-----
[root@master01 /opt/ingress/ingress3.0/ssl]# ls
tls.crt tls.key
创建 secret 资源进行存储
[root@master01 /opt/ingress/ingress3.0/ssl]# kubectl create secret tls tls-secret --key tls.key --cert tls.crt
secret/tls-secret created[root@master01 /opt/ingress/ingress3.0/ssl]# kubectl get secrets
NAME TYPE DATA AGE
default-token-c47tg kubernetes.io/service-account-token 3 4d
tls-secret kubernetes.io/tls 2 34s[root@master01 /opt/ingress/ingress3.0/ssl]# kubectl describe secret tls-secret
Name: tls-secret
Namespace: default
Labels:
Annotations:
Type: kubernetes.io/tls
Data
====
tls.key: 1704 bytes
tls.crt: 1143 bytes
创建ingress资源
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: nginx-https
spec:
tls:
- hosts:
- www.xiaobin3.com
secretName: tls-secret
rules:
- host: www.xiaobin3.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp02-svc
port:
number: 80[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f ingress-https.yaml
ingress.networking.k8s.io/nginx-https created
[root@master01 /opt/ingress/ingress3.0]# kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx NodePort 10.96.218.69 80:32584/TCP,443:31775/TCP 65m 访问测试
在宿主机的 C:\Windows\System32\drivers\etc\hosts 文件中添加 192.168.37.105 www.xiaobin3.com 记录。
Nginx 进行重写
#metadata.annotations 配置说明
●nginx.ingress.kubernetes.io/rewrite-target: <字符串> #必须重定向流量的目标URI
●nginx.ingress.kubernetes.io/ssl-redirect: <布尔值> #指示位置部分是否仅可访问SSL(当Ingress包含证书时,默认为true)
●nginx.ingress.kubernetes.io/force-ssl-redirect: <布尔值> #即使Ingress未启用TLS,也强制重定向到HTTPS
●nginx.ingress.kubernetes.io/app-root: <字符串> #定义Controller必须重定向的应用程序根,如果它在'/'上下文中
●nginx.ingress.kubernetes.io/use-regex: <布尔值> #指示Ingress上定义的路径是否使用正则表达式[root@master01 /opt/ingress/ingress3.0]# vim ingress-rewrite.yaml
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-rewrite
annotations:
nginx.ingress.kubernetes.io/rewrite-target: http://www.xiaobin1.com:32584
spec:
rules:
- host: www.123.com #这个有没有无所谓,最后重写到www.xiaobin1.com中
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: test #由于re.kgc.com只是用于跳转不需要真实站点存在,因此svc资源名称可随意定义
port:
number: 80
~
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f ingress-rewrite.yaml
ingress.networking.k8s.io/ingress-rewrite created
[root@master01 /opt/ingress/ingress3.0]# kubectl get ingress
NAME CLASS HOSTS ADDRESS PORTS AGE
ingress-rewrite www.123.com 80 13s
ingress1 www.xiaobin1.com 10.96.218.69 80 35m
ingress2 www.xiaobin2.com 10.96.218.69 80 35m
nginx-https www.xiaobin3.com 10.96.218.69 80, 443 17m
nginx-ingress www.xiaobin.com 10.96.218.69 80 122m
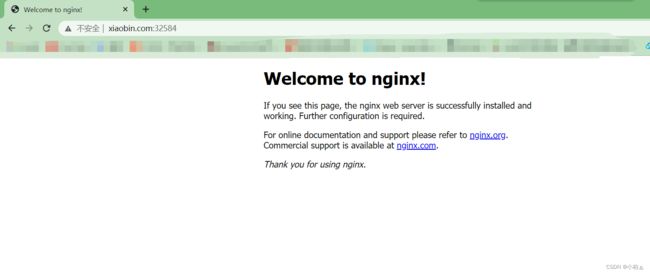
添加www.123.com映射,访问浏览器,输入http://www.123.com:32584,会跳转到http://www.xiaobin1.com:32584
Nginx 进行 BasicAuth
生成用户密码认证文件,创建 secret 资源进行存储
[root@master01 /opt/ingress/ingress3.0]# vim ingress-rewrite.yaml
[root@master01 /opt/ingress/ingress3.0]# mkdir basic-auth
[root@master01 /opt/ingress/ingress3.0]# cd basic-auth/
[root@master01 /opt/ingress/ingress3.0/basic-auth]# yum install httpd-tools.x86_64 -y[root@master01 /opt/ingress/ingress3.0/basic-auth]# htpasswd -c auth zhangsan
New password:
Re-type new password:
Adding password for user zhangsan
[root@master01 /opt/ingress/ingress3.0/basic-auth]# kubectl create secret generic basic-auth --from-file=auth
secret/basic-auth created创建 ingress 资源
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: ingress-auth
annotations: #设置认证类型basic
nginx.ingress.kubernetes.io/auth-type: basic #设置secret资源名称basic-auth
nginx.ingress.kubernetes.io/auth-secret: basic-auth #设置认证窗口提示信息
nginx.ingress.kubernetes.io/auth-realm: 'Authentication Required - zhangsan'
spec:
rules:
- host: www.bin.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: myapp01-svc
port:
number: 80
详情参考: Basic Authentication - NGINX Ingress Controller (kubernetes.github.io)
[root@master01 /opt/ingress/ingress3.0]# kubectl apply -f auth-ingress.yaml
ingress.networking.k8s.io/ingress-auth created
[root@master01 /opt/ingress/ingress3.0]# kubectl get secrets
NAME TYPE DATA AGE
basic-auth Opaque 1 7m2s
default-token-c47tg kubernetes.io/service-account-token 3 4d1h
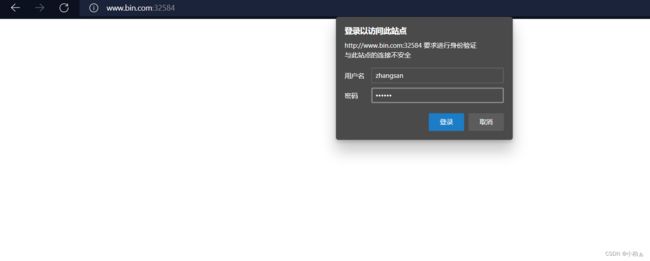
tls-secret kubernetes.io/tls 2 44m访问测试
添加映射文件,www.bin.com
访问http://www.bin.com:32584/
总结
Ingress 是对集群中服务的外部访问进行管理的 API 对象,典型的访问方式是 HTTP。
Ingress 可以提供负载均衡、SSL 终结和基于名称的虚拟托管。
ingress是k8s集群的请求入口,可以理解为对多个service的再次抽象 通常说的ingress一般包括ingress资源对象及ingress-controller两部分组成 ingress-controller有多种实现,社区原生的是ingress-nginx,根据具体需求选择 ingress自身的暴露有多种方式,需要根据基础环境及业务类型选择合适的方式