二进制安装K8S集群-上
文章目录
-
- 一、基本环境配置
-
- 1.1 集群规划
- 1.2 网段及版本信息
- 1.3 服务器优化及升级
- 1.4 安装Runtime
- 1.5 kube-apiserver 高可用实现
- 1.6 K8S&ETCD安装包下载
- 1.7 将组件发送到其他节点
- 二、制作证书
-
- 2.1 下载生成证书工具CFSSL
- 2.2 ETCD证书
- 2.3 apiserver 证书
- 2.4 apiserver聚合证书
- 2.5 controller-manage证书
- 2.6 配置controller-manager.kubeconfig
- 2.7 scheduler证书
- 2.8 admin证书
- 2.9 ServiceAccount Key
- 2.10 发送证书至其他节点
- 三、Kubernetes系统组件配置
-
- 3.1 ETCD集群配置
一、基本环境配置
1.1 集群规划
| 主机 | IP地址 | 说明 | 需手动安装组件 |
|---|---|---|---|
| k8s-master01 | 192.168.1.10 | Master01节点 | etcd、kube-apiserver、controller manager, scheduler、kube-proxy、kubelet、keepalived+haproxy、kubectl |
| k8s-master02 | 192.168.1.11 | Master02节点 | etcd,kube-apiserver,controller manager, scheduler,kube-proxy,kubelet,keepalived+haproxy, |
| k8s-master03 | 192.168.1.12 | Master03节点 | etcd、kube-apiserver、controller manager, scheduler、kube-proxy、kubelet |
| k8s-node01 | 192.168.1.101 | Node01节点 | kube-proxy,kubelet |
1.2 网段及版本信息
K8S与Docker等的版本依赖关系
| 配置信息 | 说明 |
|---|---|
| 系统版本 | CentOS7.9 |
| 内核 | 内核-ml-4.19.12 |
| K8S版本 | 1.23.* |
| Docker 版本 | 20.10.* |
| etcd版本 | 3.5.* |
| 主机网段 | 192.168.1.0/24 |
| Pod网段 | 172.16.0.0/12 10.244.0.0/12 |
| Service网段 | 10.0.0.0/16 |
kubeadm安装方式各组件配置
| 组件 | 运行方式 | 配置所在位置 | 生效方式 |
|---|---|---|---|
| kubelet | 主机 | /etc/sysconfig/kubelet;/var/lib/kubelet/config.yaml | 重新启动kubelet进程 |
| etcd | 容器 | /etc/kubernetes/manifests | 等待自动刷新pod,或重启kubelet |
| kube-apiserver | 容器 | /etc/kubernetes/manifests | 同上 |
| kube-scheduler | 容器 | /etc/kubernetes/manifests | 同上 |
| kube-controller-manager | 容器 | /etc/kubernetes/manifests | 同上 |
| kube-proxy | 容器 | configmap | 修改configmap,重新patch |
1.3 服务器优化及升级
服务器优化及内核升级
1.4 安装Runtime
Runtime安装
1.5 kube-apiserver 高可用实现
kube-apiserver高可用实现
1.6 K8S&ETCD安装包下载
Kubernetes
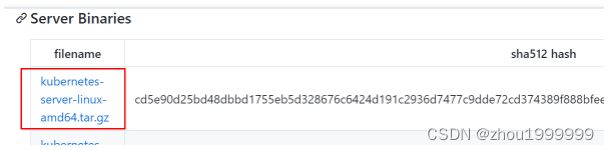
下载kubernetes安装包,选择当前最新的稳定版(v1.23.4),官方发布地址:
https://github.com/kubernetes/kubernetes/tree/master/CHANGELOG
[root@k8s-master01 ~]# wget https://dl.k8s.io/v1.23.4/kubernetes-server-linux-amd64.tar.gz # server版包括了所有组件
etcd
etcd是CoreOS团队于2013年6月发起的开源项目,它的目标是构建一个高可用的分布式键值(key-value)数据库。etcd内部采用raft协议作为一致性算法,etcd基于Go语言实现。
下载etcd安装包,选择v3.5.0,官方发布地址:
https://github.com/etcd-io/etcd/releases
[root@k8s-master01 ~]# wget https://github.com/etcd-io/etcd/releases/download/v3.5.0/etcd-v3.5.0-linux-amd64.tar.gz
分别解压
[root@k8s-master01 ~]# tar -xf kubernetes-server-linux-amd64.tar.gz --strip-components=3 -C /usr/local/bin kubernetes/server/bin/kube{let,ctl,-apiserver,-controller-manager,-scheduler,-proxy} # 解压kubernetes安装文件
[root@k8s-master01 ~]# tar -zxvf etcd-v3.5.0-linux-amd64.tar.gz --strip-components=1 -C /usr/local/bin etcd-v3.5.0-linux-amd64/etcd{,ctl} # 解压etcd安装文件
测试
[root@k8s-master01 /]# kubelet --version
Kubernetes v1.23.4
[root@k8s-master01 /]# etcdctl version
etcdctl version: 3.5.0
API version: 3.5
1.7 将组件发送到其他节点
[root@k8s-master01 ~]# MasterNodes='k8s-master02 k8s-master03'
[root@k8s-master01 ~]# WorkNodes='k8s-node01'
[root@k8s-master01 ~]# for NODE in $MasterNodes; do echo $NODE; scp /usr/local/bin/kube{let,ctl,-apiserver,-controller-manager,-scheduler,-proxy} $NODE:/usr/local/bin/; scp /usr/local/bin/etcd* $NODE:/usr/local/bin/; done
[root@k8s-master01 ~]# for NODE in $WorkNodes; do scp /usr/local/bin/kube{let,-proxy} $NODE:/usr/local/bin/; done
所有节点创建目录
[root@k8s-master01 /]# mkdir /opt/cni
[root@k8s-master01 /]# mkdir /opt/cni/bin
二、制作证书
Kubernetes 系统各组件需要使用 TLS 证书对通信进行加密。
2.1 下载生成证书工具CFSSL
语言是Flare的PKICloudGo,CF包含一个使用SSL等验证工具和SSL证书的工具和一个用于签名,捆绑TLSHTTP服务,HTTP服务,Kubernetes等组件的中会。在编写kubernetes等组件的中会。大量接触到证书的生成和使用。
[root@k8s-master01 ~]# wget "https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssl_1.6.1_linux_amd64" -O /usr/local/bin/cfssl
[root@k8s-master01 ~]# wget "https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssljson_1.6.1_linux_amd64" -O /usr/local/bin/cfssljson
#自行上传
[root@k8s-master01 ~]# mv cfssl_1.6.1_linux_amd64 /usr/local/bin/cfssl
[root@k8s-master01 ~]# mv cfssljson_1.6.1_linux_amd64 /usr/local/bin/cfssljson
[root@k8s-master01 ~]# chmod +x /usr/local/bin/cfssl /usr/local/bin/cfssljson
2.2 ETCD证书
所有master节点创建etcd证书目录
[root@k8s-master01 ~]# mkdir -p /etc/etcd/ssl
所有节点创建kubernetes相关目录,证书放在/etc/kubernetes/pki下
[root@k8s-master01 ~]# mkdir -p /etc/kubernetes/pki
创建etcd-ca-csr.json,修改年限为100年
CN(Common Name):etcd/kube-apiserver从证书中提取该字段作为请求的用户名 (User Name);浏览器使用该字段验证网站是否合法,一般写的是域名。
O(Organization):etcd/kube-apiserver 从证书中提取该字段作为请求用户所属的组 (Group);
这两个参数在后面的kubernetes启用RBAC模式中很重要,因为需要设置kubelet、admin等角色权限
C(Country): 国家
ST(State): 州,省
L(Locality):地区,城市
O: Organization Name,组织名称,公司名称
OU(Organization Unit Name): 组织单位名称,公司部门
[root@k8s-master01 ~]# cat > etcd-ca-csr.json << EOF
{
"CN": "etcd",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "etcd",
"OU": "Etcd Security"
}
],
"ca": {
"expiry": "876000h"
}
}
EOF
生成etcd的CA认证中心
[root@k8s-master01 ~]# cfssl gencert -initca etcd-ca-csr.json | cfssljson -bare /etc/etcd/ssl/etcd-ca # 初始化创建CA认证中心,将会生成 ca-key.pem(私钥) ca.pem(公钥)
# etcd-ca.csr # 根证书申请文件
# etcd-ca-key.pem # 根证书私钥
# etcd-ca.pem # 根证书公钥
[root@k8s-master01 ssl]# openssl x509 -in etcd-ca.pem -noout -text |grep ' Not ' # 查看证书时间
创建 ca-config.json
知识点:
ca-config.json:可以定义多个 profiles,分别指定不同的过期时间、使用场景等参数;后续在签名证书时使用某个 profile;此实例只有一个kubernetes模板。
signing:表示该证书可用于签名其它证书;生成的 ca.pem 证书中 CA=TRUE;
server auth:表示client可以用该CA对server提供的证书进行验证;
client auth:表示server可以用该CA对client提供的证书进行验证;
[root@k8s-master01 ~]# cat > ca-config.json << EOF
{
"signing": {
"default": {
"expiry": "876000h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "876000h"
}
}
}
}
EOF
etcd-csr.json
[root@k8s-master01 ~]# cat > etcd-csr.json << EOF
{
"CN": "etcd",
"hosts": [
"127.0.0.1",
"k8s-master01",
"k8s-master02",
"k8s-master03",
"192.168.1.10",
"192.168.1.11",
"192.168.1.12"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "etcd",
"OU": "Etcd Security"
}
]
}
EOF
签发
[root@k8s-master01 ~]# cfssl gencert \
-ca=/etc/etcd/ssl/etcd-ca.pem \
-ca-key=/etc/etcd/ssl/etcd-ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
etcd-csr.json | cfssljson -bare /etc/etcd/ssl/etcd
# 初始化CA认证中心
etcd-ca.csr
etcd-ca-key.pem
etcd-ca.pem
# 签发
etcd.csr
etcd-key.pem
etcd.pem
证书复制到其他节点
[root@k8s-master01 ~]# MasterNodes='k8s-master02 k8s-master03'
[root@k8s-master01 ~]# for NODE in $MasterNodes; do
ssh $NODE "mkdir -p /etc/etcd/ssl"
for FILE in etcd-ca-key.pem etcd-ca.pem etcd-key.pem etcd.pem; do
scp /etc/etcd/ssl/${FILE} $NODE:/etc/etcd/ssl/${FILE}
done
done
2.3 apiserver 证书
创建k8s证书目录
[root@k8s-master01 ~]# mkdir -p /etc/kubernetes/pki/
创建ca-csr.json,修改年限为100年
[root@k8s-master01 ~]# cat > ca-csr.json << EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "Kubernetes",
"OU": "Kubernetes-manual"
}
],
"ca": {
"expiry": "876000h"
}
}
EOF
生成k8s的CA认证中心
# 创建k8s的CA认证中心,将会生成 ca-key.pem(私钥) ca.pem(公钥)
[root@k8s-master01 ~]# cfssl gencert -initca ca-csr.json | cfssljson -bare /etc/kubernetes/pki/ca
# etcd-ca.csr # 根证书申请文件
# etcd-ca-key.pem # 根证书私钥
# etcd-ca.pem # 根证书公钥
创建 ca-config.json
知识点:
ca-config.json:可以定义多个 profiles,分别指定不同的过期时间、使用场景等参数;后续在签名证书时使用某个 profile;此实例只有一个kubernetes模板。
signing:表示该证书可用于签名其它证书;生成的 ca.pem 证书中 CA=TRUE;
server auth:表示client可以用该CA对server提供的证书进行验证;
client auth:表示server可以用该CA对client提供的证书进行验证;
[root@k8s-master01 ~]# cat > ca-config.json << EOF
{
"signing": {
"default": {
"expiry": "876000h"
},
"profiles": {
"kubernetes": {
"usages": [
"signing",
"key encipherment",
"server auth",
"client auth"
],
"expiry": "876000h"
}
}
}
}
EOF
apiserver-csr.json
service网段第一个IP
所有masterIP
负载均衡IP
[root@k8s-master01 ~]# cat > apiserver-csr.json << EOF
{
"CN": "kube-apiserver",
"hosts": [
"10.0.0.1",
"192.168.1.10",
"127.0.0.1",
"kubernetes",
"kubernetes.default",
"kubernetes.default.svc",
"kubernetes.default.svc.cluster",
"kubernetes.default.svc.cluster.local"
"192.168.1.11",
"192.168.1.12"
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "Kubernetes",
"OU": "Kubernetes-manual"
}
]
}
EOF
签发
[root@k8s-master01 ~]# cfssl gencert \
-ca=/etc/kubernetes/pki/ca.pem \
-ca-key=/etc/kubernetes/pki/ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
apiserver-csr.json | cfssljson -bare /etc/kubernetes/pki/apiserver
2.4 apiserver聚合证书
front-proxy-ca-csr.json
[root@k8s-master01 ~]# cat > front-proxy-ca-csr.json << EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"ca": {
"expiry": "876000h"
}
}
EOF
创建apiserver聚合证书的CA认证中心
[root@k8s-master01 ~]# cfssl gencert -initca front-proxy-ca-csr.json | cfssljson -bare /etc/kubernetes/pki/front-proxy-ca
[root@k8s-master01 ~]# cat > front-proxy-client-csr.json << EOF
{
"CN": "front-proxy-client",
"key": {
"algo": "rsa",
"size": 2048
}
}
EOF
签发
[root@k8s-master01 ~]# cfssl gencert \
-ca=/etc/kubernetes/pki/front-proxy-ca.pem \
-ca-key=/etc/kubernetes/pki/front-proxy-ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
front-proxy-client-csr.json | cfssljson -bare /etc/kubernetes/pki/front-proxy-client
2.5 controller-manage证书
[root@k8s-master01 ~]# cat > manager-csr.json << EOF
{
"CN": "system:kube-controller-manager",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "system:kube-controller-manager",
"OU": "Kubernetes-manual"
}
]
}
EOF
签发
[root@k8s-master01 ~]# cfssl gencert \
-ca=/etc/kubernetes/pki/ca.pem \
-ca-key=/etc/kubernetes/pki/ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
manager-csr.json | cfssljson -bare /etc/kubernetes/pki/controller-manager
2.6 配置controller-manager.kubeconfig
[root@k8s-master01 ~]# kubectl config set-cluster kubernetes \
--certificate-authority=/etc/kubernetes/pki/ca.pem \
--embed-certs=true \
--server=https://192.168.1.10:8443 \
--kubeconfig=/etc/kubernetes/controller-manager.kubeconfig
设置一个环境项,一个上下文
[root@k8s-master01 ~]# kubectl config set-context system:kube-controller-manager@kubernetes \
--cluster=kubernetes \
--user=system:kube-controller-manager \
--kubeconfig=/etc/kubernetes/controller-manager.kubeconfig
set-credentials 设置一个用户项
[root@k8s-master01 ~]# kubectl config set-credentials system:kube-controller-manager \
--client-certificate=/etc/kubernetes/pki/controller-manager.pem \
--client-key=/etc/kubernetes/pki/controller-manager-key.pem \
--embed-certs=true \
--kubeconfig=/etc/kubernetes/controller-manager.kubeconfig
使用某个环境当做默认环境
[root@k8s-master01 ~]# kubectl config use-context system:kube-controller-manager@kubernetes \
--kubeconfig=/etc/kubernetes/controller-manager.kubeconfig
2.7 scheduler证书
[root@k8s-master01 ~]# cat > scheduler-csr.json<< EOF
{
"CN": "system:kube-scheduler",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "system:kube-scheduler",
"OU": "Kubernetes-manual"
}
]
}
EOF
签发
[root@k8s-master01 ~]# cfssl gencert \
-ca=/etc/kubernetes/pki/ca.pem \
-ca-key=/etc/kubernetes/pki/ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
scheduler-csr.json | cfssljson -bare /etc/kubernetes/pki/scheduler
配置scheduler.kubeconfig
[root@k8s-master01 ~]# kubectl config set-cluster kubernetes \
--certificate-authority=/etc/kubernetes/pki/ca.pem \
--embed-certs=true \
--server=https://192.168.1.10:8443 \
--kubeconfig=/etc/kubernetes/scheduler.kubeconfig
[root@k8s-master01 ~]# kubectl config set-credentials system:kube-scheduler \
--client-certificate=/etc/kubernetes/pki/scheduler.pem \
--client-key=/etc/kubernetes/pki/scheduler-key.pem \
--embed-certs=true \
--kubeconfig=/etc/kubernetes/scheduler.kubeconfig
[root@k8s-master01 ~]# kubectl config set-context system:kube-scheduler@kubernetes \
--cluster=kubernetes \
--user=system:kube-scheduler \
--kubeconfig=/etc/kubernetes/scheduler.kubeconfig
[root@k8s-master01 ~]# kubectl config use-context system:kube-scheduler@kubernetes \
--kubeconfig=/etc/kubernetes/scheduler.kubeconfig
2.8 admin证书
admin-csr.json
[root@k8s-master01 ~]# cat > admin-csr.json << EOF
{
"CN": "admin",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Beijing",
"L": "Beijing",
"O": "system:masters",
"OU": "Kubernetes-manual"
}
]
}
EOF
签发
[root@k8s-master01 ~]# cfssl gencert \
-ca=/etc/kubernetes/pki/ca.pem \
-ca-key=/etc/kubernetes/pki/ca-key.pem \
-config=ca-config.json \
-profile=kubernetes \
admin-csr.json | cfssljson -bare /etc/kubernetes/pki/admin
配置
[root@k8s-master01 ~]# kubectl config set-cluster kubernetes \
--certificate-authority=/etc/kubernetes/pki/ca.pem \
--embed-certs=true \
--server=https://192.168.1.10:8443 \
--kubeconfig=/etc/kubernetes/admin.kubeconfig
[root@k8s-master01 ~]# kubectl config set-credentials kubernetes-admin \
--client-certificate=/etc/kubernetes/pki/admin.pem \
--client-key=/etc/kubernetes/pki/admin-key.pem \
--embed-certs=true \
--kubeconfig=/etc/kubernetes/admin.kubeconfig
[root@k8s-master01 ~]# kubectl config set-context kubernetes-admin@kubernetes \
--cluster=kubernetes \
--user=kubernetes-admin \
--kubeconfig=/etc/kubernetes/admin.kubeconfig
[root@k8s-master01 ~]# kubectl config use-context kubernetes-admin@kubernetes \
--kubeconfig=/etc/kubernetes/admin.kubeconfig
2.9 ServiceAccount Key
[root@k8s-master01 ~]# openssl genrsa -out /etc/kubernetes/pki/sa.key 2048
[root@k8s-master01 ~]# openssl rsa -in /etc/kubernetes/pki/sa.key -pubout -out /etc/kubernetes/pki/sa.pub
2.10 发送证书至其他节点
[root@k8s-master01 ~]# for NODE in k8s-master02 k8s-master03; do
for FILE in $(ls /etc/kubernetes/pki | grep -v etcd); do
scp /etc/kubernetes/pki/${FILE} $NODE:/etc/kubernetes/pki/${FILE};
done;
for FILE in admin.kubeconfig controller-manager.kubeconfig scheduler.kubeconfig; do
scp /etc/kubernetes/${FILE} $NODE:/etc/kubernetes/${FILE};
done;
done
查看证书数量
[root@k8s-master01 ~]# ls /etc/kubernetes/pki/ |wc -l
三、Kubernetes系统组件配置
3.1 ETCD集群配置
master01
[root@k8s-master01 ~]# vim /etc/etcd/etcd.config.yml
name: 'k8s-master01'
data-dir: /var/lib/etcd
wal-dir: /var/lib/etcd/wal
snapshot-count: 5000
heartbeat-interval: 100
election-timeout: 1000
quota-backend-bytes: 0
listen-peer-urls: 'https://192.168.1.10:2380'
listen-client-urls: 'https://192.168.1.10:2379,http://127.0.0.1:2379'
max-snapshots: 3
max-wals: 5
cors:
initial-advertise-peer-urls: 'https://192.168.1.10:2380'
advertise-client-urls: 'https://192.168.1.10:2379'
discovery:
discovery-fallback: 'proxy'
discovery-proxy:
discovery-srv:
initial-cluster: 'k8s-master01=https://192.168.1.10:2380,k8s-master02=https://192.168.1.11:2380,k8s-master03=https://192.168.1.12:2380'
initial-cluster-token: 'etcd-k8s-cluster'
initial-cluster-state: 'new'
strict-reconfig-check: false
enable-v2: true
enable-pprof: true
proxy: 'off'
proxy-failure-wait: 5000
proxy-refresh-interval: 30000
proxy-dial-timeout: 1000
proxy-write-timeout: 5000
proxy-read-timeout: 0
client-transport-security:
cert-file: '/etc/kubernetes/pki/etcd/etcd.pem'
key-file: '/etc/kubernetes/pki/etcd/etcd-key.pem'
client-cert-auth: true
trusted-ca-file: '/etc/kubernetes/pki/etcd/etcd-ca.pem'
auto-tls: true
peer-transport-security:
cert-file: '/etc/kubernetes/pki/etcd/etcd.pem'
key-file: '/etc/kubernetes/pki/etcd/etcd-key.pem'
peer-client-cert-auth: true
trusted-ca-file: '/etc/kubernetes/pki/etcd/etcd-ca.pem'
auto-tls: true
debug: false
log-package-levels:
log-outputs: [default]
force-new-cluster: false
其它master节点注意修改名称和IP即可
创建etcd service并启动
[root@k8s-master01 ~]# cat > /usr/lib/systemd/system/etcd.service << EOF
[Unit]
Description=Etcd Service
Documentation=https://coreos.com/etcd/docs/latest/
After=network.target
[Service]
Type=notify
ExecStart=/usr/local/bin/etcd --config-file=/etc/etcd/etcd.config.yml
Restart=on-failure
RestartSec=10
LimitNOFILE=65536
[Install]
WantedBy=multi-user.target
Alias=etcd3.service
EOF
所有master节点创建etcd证书目录
[root@k8s-master01 ~]# mkdir -p /etc/kubernetes/pki/etcd
[root@k8s-master01 ~]# ln -s /etc/etcd/ssl/* /etc/kubernetes/pki/etcd/
[root@k8s-master01 ~]# systemctl daemon-reload
[root@k8s-master01 ~]# systemctl enable --now etcd
查看ETCD状态
[root@k8s-master01 ~]# export ETCDCTL_API=3
[root@k8s-master01 ~]# etcdctl --endpoints="192.168.1.10:2379,192.168.1.11:2379,192.168.1.12:2379" --cacert=/etc/kubernetes/pki/etcd/etcd-ca.pem --cert=/etc/kubernetes/pki/etcd/etcd.pem --key=/etc/kubernetes/pki/etcd/etcd-key.pem endpoint status --write-out=table
+----------+----+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
| ENDPOINT | ID | VERSION | DB SIZE | IS LEADER | IS LEARNER | RAFT TERM | RAFT INDEX | RAFT APPLIED INDEX | ERRORS |
+----------+----+---------+---------+-----------+------------+-----------+------------+--------------------+--------+
| 192.168.1.10:2379 | d3bd0760893752a8 | 3.5.0 | 20 kB | true | false | 2 | 8 | 8 |
| 192.168.1.11:2379 | ace8d5b0766b3d92 | 3.5.0 | 20 kB | false | false | 2 | 8 | 8 |
| 192.168.1.12:2379 | ac7e57d44f030e8 | 3.5.0 | 20 kB | false | false | 2 | 8 | 8 |
+----------+----+---------+---------+-----------+------------+-----------+------------+--------------------+--------+