Istio Arch-2
Istio Arch-2
https://istio.io/latest/docs/concepts/security/
Security
The Istio security features provide strong identity, powerful policy, transparent TLS encryption, and authentication, authorization and audit (AAA) tools to protect your services and data.
-
To defend against man-in-the-middle attacks, they need traffic encryption.
-
To provide flexible service access control, they need mutual TLS and fine-grained access policies.
-
To determine who did what at what time, they need auditing tools.
-
Security by default: no changes needed to application code and infrastructure
-
Defense in depth: integrate with existing security systems to provide multiple layers of defense
-
Zero-trust network: build security solutions on distrusted networks
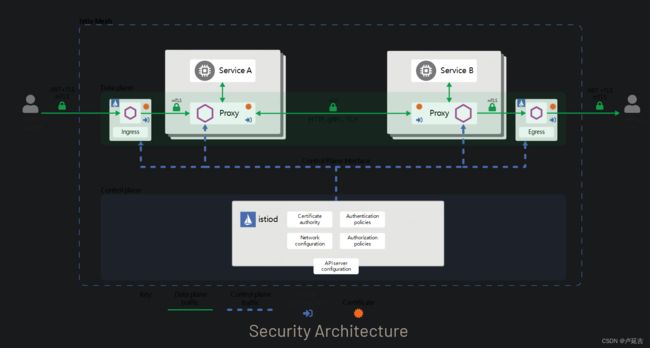
High-level architecture
- Certificate Authority for Key and Certificate Management
- Distributes to the proxies (authentication and authorization and secure naming)
Istio identity
- Identity is a fundamental concept of any security infrastructure.
- service account
Identity and certificate management
- istiod offers a gRPC service to take certificate signing requests (CSRs).
- CSR and CA and SDS(secret discovery service)
Authentication
- strong identity representing
- Secures S2S
Mutual TLS authentication
Enhancing Security for Microservices Architecture
Introduction In the world of microservices architecture, ensuring the security of services and data is paramount. ISTIO, an open-source service mesh platform, offers a comprehensive set of security features to protect services against various threats.
ISTIO Security Features ISTIO provides a range of security features to meet the diverse security requirements of microservices. Let’s dive into some of the key security features offered by ISTIO:
- Traffic Encryption: To defend against man-in-the-middle attacks, ISTIO supports transparent TLS encryption for all communication between services. This ensures that data is encrypted and secure while in transit.
- Service Access Control: ISTIO enables flexible service access control through mutual TLS authentication and fine-grained access policies. With mutual TLS authentication, services can authenticate each other to establish trust before communication. Fine-grained access policies allow administrators to set access control rules based on various criteria, such as user identity or request attributes.
- Auditing Tools: ISTIO provides auditing tools to track and monitor activities within a microservices environment. These tools enable administrators to determine who did what, and at what time. Auditing plays a crucial role in maintaining security and compliance standards.
ISTIO Security Principles: Apart from the specific features, ISTIO follows some important security principles:
- Security by Default: ISTIO ensures that security is built into the platform by default. This means that no changes are needed to application code or infrastructure to implement basic security measures. It provides a solid foundation for secure microservices communication.
- Defense in Depth: ISTIO can be seamlessly integrated with existing security systems to provide multiple layers of defense. This integration enhances the overall security posture by adding extra layers of protection to the microservices architecture.
- Zero-Trust Network: ISTIO operates on the principle of a zero-trust network, where security solutions are built on the assumption of an untrusted network. This ensures that every communication is authenticated and authorized, even within the internal network, providing robust security in distributed environments.
High-level Architecture: The security architecture of ISTIO consists of various components, such as:
- Certificate Authority for Key and Certificate Management: ISTIO leverages a Certificate Authority to manage keys and certificates for secure communication. This central authority ensures proper authentication and secure naming within the microservices environment.
- Proxy Integration: ISTIO distributes certificates, authentication, and authorization policies to the proxies, which handle the communication between services. This integration enables seamless implementation of mutual TLS authentication and secure communication channels.
Identity and Certificate Management: Identity is a fundamental concept for any security infrastructure. ISTIO uses a service account to represent the identity of a service within the system. By leveraging a distributed key management system, such as secret discovery service (SDS), ISTIO offers a scalable solution for identity and certificate management.
Authentication: ISTIO supports strong identity representation, ensuring that services can authenticate each other with confidence. This authentication mechanism secures service-to-service communication and prevents unauthorized access.
Mutual TLS Authentication: To further enhance security, ISTIO supports mutual TLS authentication. With mutual TLS, both the client and server authenticate each other before establishing a secure connection. This ensures that only trusted services can communicate within the microservices architecture.
Conclusion: Microservices architecture brings several security challenges, and ISTIO offers powerful security features to address them. From traffic encryption to fine-grained access control and auditing tools, ISTIO provides a comprehensive security framework. By following security-by-default principles, integrating with existing systems, and implementing a zero-trust network approach, ISTIO enhances security while maintaining the flexibility and scalability of a microservices architecture.
Security in Istio: Protecting Services and Data
As an Istio engineer, I would like to highlight the robust security features provided by Istio that ensure the protection of services and data. Istio offers a comprehensive set of tools, including strong identity, powerful policy enforcement, transparent TLS encryption, and authentication, authorization, and audit (AAA) capabilities.
One of the primary security concerns addressed by Istio is defending against man-in-the-middle attacks. To achieve this, Istio ensures traffic encryption, which prevents unauthorized access to sensitive data. By default, Istio enables transparent TLS encryption, providing a secure communication channel between services.
Flexible service access control is another critical aspect of Istio’s security features. It incorporates mutual TLS authentication and fine-grained access policies, allowing administrators to define and enforce access rules based on service identities. This level of control ensures that only authorized services can communicate with each other, minimizing the risk of unauthorized access.
Istio also provides auditing tools to track and monitor service activities. These tools enable administrators to determine who performed specific actions and when they occurred. This feature is crucial for maintaining accountability and detecting any potential security breaches.
One of the significant advantages of Istio’s security features is that they are implemented by default, requiring no changes to application code or infrastructure. This approach ensures that security is not an afterthought but an integral part of the system from the beginning.
To further enhance security, Istio follows a defense-in-depth strategy. It integrates seamlessly with existing security systems, allowing organizations to leverage multiple layers of defense. This integration ensures that Istio complements and enhances the security measures already in place.
Istio also embraces the zero-trust network model, building security solutions for inherently untrusted networks. By assuming that all networks are potentially compromised, Istio focuses on establishing secure communication channels and verifying the identity of services, regardless of the underlying network infrastructure.
At a high level, Istio’s security architecture includes a Certificate Authority (CA) responsible for key and certificate management. The CA distributes certificates to the proxies, facilitating authentication, authorization, and secure naming.
Identity management is a fundamental concept in Istio’s security infrastructure. Each service is assigned a unique identity, known as a service account. This identity plays a crucial role in establishing trust and enabling secure communication between services.
Istiod, the Istio control plane component, offers a gRPC service to handle certificate signing requests (CSRs). This service, along with the CA and Secret Discovery Service (SDS), forms the backbone of Istio’s identity and certificate management.
Authentication is a vital aspect of Istio’s security capabilities. It ensures that services possess strong identities, representing their authenticity. This authentication mechanism secures service-to-service (S2S) communication, preventing unauthorized services from impersonating legitimate ones.
Finally, Istio supports mutual TLS authentication, which enables services to authenticate each other during communication. This mutual authentication ensures that both the client and server verify each other’s identities, establishing a trusted connection.
In conclusion, Istio’s security features offer a comprehensive suite of tools to protect services and data. With its focus on strong identity, policy enforcement, transparent TLS encryption, and AAA capabilities, Istio enables organizations to build secure and trustworthy microservice architectures. By implementing security by default, integrating with existing systems, and embracing the zero-trust network model, Istio ensures a robust and reliable security posture for modern distributed applications.
On the one hand
Istio是一个开源的服务网格平台,它提供了许多关键概念来保护您的服务和数据的安全性。下面是其中一些关键概念的解释:
- 安全性(Security):Istio安全功能提供了强大的身份验证、强制访问控制、透明的传输层安全(TLS)加密以及身份认证、授权和审计(AAA)工具,以保护您的服务和数据。
- 为了防止中间人攻击,Istio使用流量加密来确保通信的安全性。
- 为了提供灵活的服务访问控制,Istio使用互相认证(Mutual TLS)和细粒度的访问策略。
- 为了确定是谁在什么时间做了什么,Istio提供了审计工具。
- 安全默认(Security by default):无需对应用程序代码和基础架构进行任何更改即可享受安全保护。
- 深度防御(Defense in depth):与现有安全系统集成,提供多层防御。
- 零信任网络(Zero-trust network):在不可信任的网络上构建安全解决方案。
此外,在Istio的架构中,有一些重要的组件和概念:
- 高级架构(High-level architecture):包括证书授权机构、代理分发、验证和授权、安全命名等组件。
- Istio身份(Istio identity):身份是任何安全基础架构的基本概念,Istio使用服务账户(service account)来表示服务的身份。
- 身份和证书管理(Identity and certificate management):istiod提供了一个用于处理证书签名请求的gRPC服务。通过证书签名请求(CSR)、证书授权机构(CA)和密钥发现服务(SDS),Istio实现了身份和证书的管理。
- 身份认证(Authentication):Istio提供了强大的身份认证功能,用于保证服务与服务之间的安全通信。
- 互相认证(Mutual TLS authentication):通过对双方进行互相认证,Istio确保了服务之间的安全通信。