ensp综合实验:双机热备、IPSec、FTP
作业十八:综合实验
文章目录
- 作业十八:综合实验
-
- 实验要求
- 实验环境
- 实验步骤
-
- 规划并配置IP
- 划分区域
- 配置OSPF
- 配置双机热备
-
-
- 配置静态路由
- 配置VRRP
- 配置心跳接口
- 配置IPSec
- 配置安全策略
- 检查连通性
-
- 配置访问公网的Client
-
-
- NAT配置
- 配置安全策略
- 检查连通性
-
- 配置FTP
-
-
- 配置NAT
- 配置安全策略
- 配置ASPF
- 检查连通性
-
- 实验总结
实验要求
实验环境
实验步骤
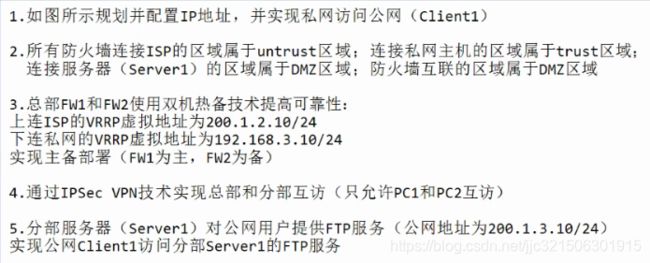
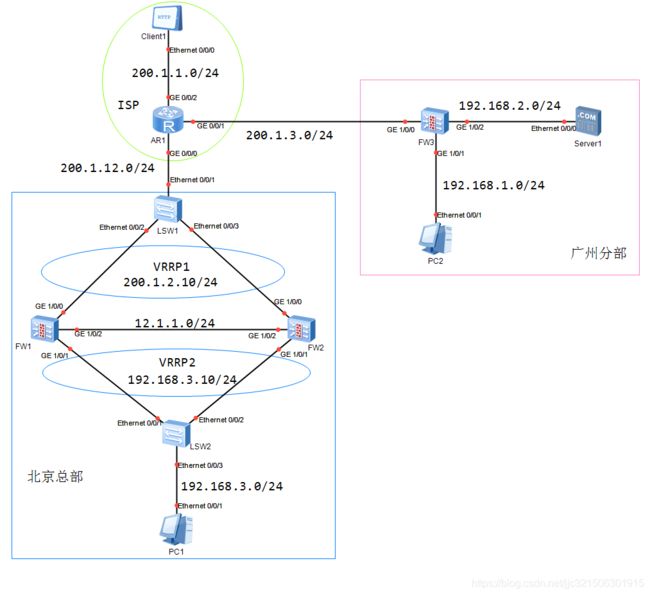
规划并配置IP
PC1:
Client1:
Server1:
R1:
[R1]int g0/0/2
[R1-GigabitEthernet0/0/2]ip add 200.1.1.254 24
[R1-GigabitEthernet0/0/2]int g0/0/1
[R1-GigabitEthernet0/0/1]ip add 200.1.3.1 24
[R1-GigabitEthernet0/0/1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip add 200.1.12.1 24
FW1:
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]ip add 192.168.4.1 24
[FW1-GigabitEthernet1/0/0]int g1/0/2
[FW1-GigabitEthernet1/0/2]ip add 12.1.1.1 24
[FW1-GigabitEthernet1/0/2]int g1/0/1
[FW1-GigabitEthernet1/0/1]ip add 192.168.3.1 24
FW2:
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]ip add 192.168.4.2 24
[FW2-GigabitEthernet1/0/0]int g1/0/2
[FW2-GigabitEthernet1/0/2]ip add 12.1.1.2 24
[FW2-GigabitEthernet1/0/2]int g1/0/1
[FW2-GigabitEthernet1/0/1]ip add 192.168.3.2 24
FW3:
[FW3]int g0/0/0
[FW3-GigabitEthernet0/0/0]ip add 200.1.3.3 24
[FW3-GigabitEthernet0/0/0]int g1/0/2
[FW3-GigabitEthernet1/0/2]ip add 192.168.2.254 24
[FW3-GigabitEthernet1/0/2]int g1/0/1
[FW3-GigabitEthernet1/0/1]ip add 192.168.1.254 24
划分区域
FW1:
[FW1]firewall zone untrust
[FW1-zone-untrust]add int g1/0/0
[FW1]firewall zone trust
[FW1-zone-trust]add int g1/0/1
[FW1]firewall zone dmz
[FW1-zone-dmz]add int g1/0/2
FW2:
[FW2]firewall zone untrust
[FW2-zone-untrust]add int g1/0/0
[FW2]firewall zone trust
[FW2-zone-trust]add int g1/0/1
[FW2]firewall zone dmz
[FW-zone-dmz]add int g1/0/2
FW3:
[FW3]firewall zone trust
[FW3-zone-trust]add int g1/0/1
[FW3]firewall zone untrust
[FW3-zone-untrust]add int g1/0/0
[FW3]firewall zone dmz
[FW3-zone-dmz]add int g1/0/2
配置OSPF
R1:
[R1]ospf
[R1-ospf-1]area 0
[R1-ospf-1-area-0.0.0.0]int g0/0/0
[R1-GigabitEthernet0/0/0]os e a 0
[R1-GigabitEthernet0/0/0]int g0/0/1
[R1-GigabitEthernet0/0/1os e a 0
[R1-GigabitEthernet0/0/1]int g0/02
[R1-GigabitEthernet0/0/2]os e a 0
FW1:
[FW1]ospf
[FW1-ospf-1]area 0
[FW1-ospf-1-area-0.0.0.0]int g1/0/0
[FW1-GigabitEthernet0/0/0]os e a 0
FW2:
[FW2]ospf
[FW2-ospf-1]area 0
[FW2-ospf-1-area-0.0.0.0]int g1/0/0
[FW2-GigabitEthernet0/0/0]os e a 0
FW3:
[FW3]ospf
[FW3-ospf-1]area 0
[FW3-ospf-1-area-0.0.0.0]int g1/0/0
[FW3-GigabitEthernet0/0/0]os e a 0
配置双机热备
配置静态路由
R1:
[R1]ip route-static 192.168.1.0 24 200.1.12.1
配置VRRP
FW1:
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 200.1.2.10 active
[FW1-GigabitEthernet1/0/0]int g1/0/1
[FW1-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 192.168.3.10 active
FW2:
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]vrrp vrid 1 virtual-ip 200.1.2.10 standby
[FW2-GigabitEthernet1/0/0]int g1/0/1
[FW2-GigabitEthernet1/0/1]vrrp vrid 1 virtual-ip 192.168.3.10 standby
配置心跳接口
FW1:
[FW1]hrp int g1/0/2 remote 12.1.1.2
[FW1]hrp enable
FW2:
[FW2]hrp int g1/0/2 remote 12.1.1.1
[FW2]hrp enable
配置IPSec
FW1:
//感兴趣流
HRP_M[FW1]acl 3000 (+B)
HRP_M[FW1-acl-adv-3000]rule permit ip source 192.168.3.0 0.0.0.255 destination 192.168.1.0 0.0.0.255 (+B)
//ike安全提议
HRP_M[FW1]ike proposal 1 (+B)
HRP_M[FW1-ike-proposal-1]di th (+B) //验证与加密算法使用默认配置如下
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
//ike对等体
HRP_M[FW1]ike peer fw3 (+B)
HRP_M[FW1-ike-peer-fw3]pre-shared-key cipher huawei (+B)
HRP_M[FW1-ike-peer-fw3]ike-proposal 1 (+B)
HRP_M[FW1-ike-peer-fw3]remote-address 200.1.3.3 (+B)
//ipsec安全提议
HRP_M[FW1]ipsec proposal 2 (+B)
HRP_M[FW1-ipsec-proposal-2]di th (+B) //验证与加密算法使用默认配置如下
#
ipsec proposal 2
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
//ipsec策略
HRP_M[FW1]ipsec policy runtime 10 isakmp (+B)
HRP_M[FW1-ipsec-policy-isakmp-runtime-10]security acl 3000 (+B)
HRP_M[FW1-ipsec-policy-isakmp-runtime-10]ike-peer fw3 (+B)
HRP_M[FW1-ipsec-policy-isakmp-runtime-10]proposal 2 (+B)
//绑定接口
HRP_M[FW1]int g1/0/0 (+B)
HRP_M[FW1-GigabitEthernet1/0/0]ipsec policy runtime (+B)
//静态配置
HRP_M[FW1]ip route-static 192.168.1.0 24 200.1.12.1 (+B)
FW3:
//感兴趣流
[FW3]acl 3000
[FW3-acl-adv-3000]rule permit ip source 192.168.1.0 0.0.0.255 destination 192.168.3.0 0.0.0.255
//ike安全提议
[FW3]ike proposal 1
[FW3-ike-proposal-1]di th //验证与加密算法使用默认配置如下
#
ike proposal 1
encryption-algorithm aes-256
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
//ike对等体
[FW3]ike peer fw1
[FW3-ike-peer-fw1]pre-shared-key cipher huawei
[FW3-ike-peer-fw1]ike-proposal 1
[FW3-ike-peer-fw1]remote-address 200.1.2.10
//ipsec安全提议
[FW3]ipsec proposal 2
[FW3-ipsec-proposal-2]di th //验证与加密算法使用默认配置如下
#
ipsec proposal 2
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
#
//ipsec策略
[FW3]ipsec policy runtime 10 isakmp
[FW3-ipsec-policy-isakmp-runtime-10]security acl 3000
[FW3-ipsec-policy-isakmp-runtime-10]ike-peer fw1
[FW3-ipsec-policy-isakmp-runtime-10]proposal 2
//绑定接口
[FW3]int g1/0/0
[FW3-GigabitEthernet1/0/0]ipsec policy runtime
//静态配置
[FW3]ip route-static 192.168.3.0 24 200.1.3.1
配置安全策略
FW1:
[FW1]security-policy (+B)
[FW1-policy-security]rule name t_u (+B)
[FW1-policy-security-rule-t_u]source-zone trust (+B)
[FW1-policy-security-rule-t_ut]destination-zone untrust (+B)
[FW1-policy-security-rule-t_u]source-address 192.168.3.0 24 (+B)
[FW1-policy-security-rule-t_u]destination-address 192.168.1.0 24 (+B)
[FW1-policy-security-rule-t_u]service icmp (+B)
[FW1-policy-security-rule-t_u]action permit (+B)
[FW1-policy-security]rule name u_t (+B)
[FW1-policy-security-rule-u_t]source-zone untrust (+B)
[FW1-policy-security-rule-u_t]destination-zone trust (+B)
[FW1-policy-security-rule-u_t]source-address 192.168.1.0 24 (+B)
[FW1-policy-security-rule-u_t]destination-address 192.168.3.0 24 (+B)
[FW1-policy-security-rule-u_t]service icmp (+B)
[FW1-policy-security-rule-u_t]action permit (+B)
[FW1-policy-security]rule name u_l (+B)
[FW1-policy-security-rule-u_l]source-zone untrust (+B)
[FW1-policy-security-rule-u_l]destination-zone local (+B)
[FW1-policy-security-rule-u_l]source-address 200.1.3.3 32 (+B)
[FW1-policy-security-rule-u_l]destination-address 200.1.2.10 32 (+B)
[FW1-policy-security-rule-u_l]service esp (+B)
[FW1-policy-security-rule-u_l]action permit (+B)
[FW1]ip service-set isakmp type object 16 (+B)
[FW1-object-service-set-isakmp]service protocol udp source-port 500 (+B)
[FW1]security-policy (+B)
[FW1-policy-security]rule name isakmp (+B)
[FW1-policy-security-rule-isakmp]source-zone untrust (+B)
[FW1-policy-security-rule-isakmp]source-zone local (+B)
[FW1-policy-security-rule-isakmp]destination-zone local (+B)
[FW1-policy-security-rule-isakmp]destination-zone untrust (+B)
[FW1-policy-security-rule-isakmp]source-address 200.1.3.3 32 (+B)
[FW1-policy-security-rule-isakmp]destination-address 200.1.2.10 32 (+B)
[FW1-policy-security-rule-isakmp]source-address 200.1.2.10 32 (+B)
[FW1-policy-security-rule-isakmp]destination-address 200.1.3.3 32 (+B)
[FW1-policy-security-rule-isakmp]service isakmp (+B)
[FW1-policy-security-rule-isakmp]action permit (+B)
FW3:
[FW3]security-policy
[FW3-policy-security]rule name t_u
[FW3-policy-security-rule-t_u]source-zone trust
[FW3-policy-security-rule-t_u]destination-zone untrust
[FW3-policy-security-rule-t_u]source-address 192.168.3.0 24
[FW3-policy-security-rule-t_u]destination-address 192.168.1.0 24
[FW3-policy-security-rule-t_u]service icmp
[FW3-policy-security-rule-t_u]action permit
[FW3-policy-security]rule name u_t
[FW3-policy-security-rule-u_t]source-zone untrust
[FW3-policy-security-rule-u_t]destination-zone trust
[FW3-policy-security-rule-u_t]source-address 192.168.1.0 24
[FW3-policy-security-rule-u_t]destination-address 192.168.3.0 24
[FW3-policy-security-rule-u_t]service icmp
[FW3-policy-security-rule-u_t]action permit
[FW3-policy-security]rule name u_l
[FW3-policy-security-rule-u_l]source-zone untrust
[FW3-policy-security-rule-u_l]destination-zone local
[FW3-policy-security-rule-u_l]source-address 200.1.2.10 32
[FW3-policy-security-rule-u_l]destination-address 200.1.3.3 32
[FW3-policy-security-rule-u_l]service esp
[FW3-policy-security-rule-u_l]action permit
[FW1]ip service-set isakmp type object 16
[FW3-object-service-set-isakmp]service protocol udp source-port 500
[FW3-policy-security]security-policy
[FW3-policy-security-rule-isakmp]rule name isakmp
[FW3-policy-security-rule-isakmp]source-zone untrust
[FW3-policy-security-rule-isakmp]source-zone local
[FW3-policy-security-rule-isakmp]destination-zone local
[FW3-policy-security-rule-isakmp]destination-zone untrust
[FW3-policy-security-rule-isakmp]source-address 200.1.3.3 32
[FW3-policy-security-rule-isakmp]destination-address 200.1.2.10 32
[FW3-policy-security-rule-isakmp]source-address 200.1.2.10 32
[FW3-policy-security-rule-isakmp]destination-address 200.1.3.3 32
[FW3-policy-security-rule-isakmp]service isakmp
[FW3-policy-security-rule-isakmp]action permit
检查连通性
PC1 ping PC2:
PC>ping 192.168.1.1
Ping 192.168.1.1: 32 data bytes, Press Ctrl_C to break
From 192.168.1.1: bytes=32 seq=1 ttl=254 time=172 ms
From 192.168.1.1: bytes=32 seq=2 ttl=254 time=63 ms
From 192.168.1.1: bytes=32 seq=3 ttl=254 time=62 ms
From 192.168.1.1: bytes=32 seq=4 ttl=254 time=62 ms
From 192.168.1.1: bytes=32 seq=5 ttl=254 time=46 ms
--- 192.168.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 46/81/172 ms
PC2 ping PC1:
PC>ping 192.168.3.1
Ping 192.168.3.1: 32 data bytes, Press Ctrl_C to break
Request timeout!
From 192.168.3.1: bytes=32 seq=2 ttl=126 time=15 ms
From 192.168.3.1: bytes=32 seq=3 ttl=126 time=15 ms
From 192.168.3.1: bytes=32 seq=4 ttl=126 time=15 ms
From 192.168.3.1: bytes=32 seq=5 ttl=126 time=15 ms
--- 172.16.1.1 ping statistics ---
5 packet(s) transmitted
4 packet(s) received
20.00% packet loss
round-trip min/avg/max = 0/15/15 ms
配置访问公网的Client
NAT配置
FW3:
//配置地址池
[FW1]nat address-group 1
[FW1-address-group-1]section 200.1.12.10 200.1.12.10
//配置NAT策略
[FW1]nat-policy
[FW1-policy-nat]rule name no_nat
[FW1-policy-nat-rule-no_nat]source-zone trust
[FW1-policy-nat-rule-no_nat]destination-zone untrust
[FW1-policy-nat-rule-no_nat]source-address 192.168.3.0 24
[FW1-policy-nat-rule-no_nat]destination-address 192.168.1.0 24
[FW1-policy-nat-rule-no_nat]action no-nat
[FW1]nat-policy
[FW1-policy-nat]rule name t_u
[FW1-policy-nat-rule-t_u]source-zone trust
[FW1-policy-nat-rule-t_u]destination-zone untrust
[FW1-policy-nat-rule-t_u]source-address 192.168.3.0 24
[FW1-policy-nat-rule-t_u]action source-nat address-group 1
配置安全策略
FW3:
//配置安全策略
[FW1]security-policy
[FW1-policy-security]rule name nat
[FW1-policy-security-rule-nat]source-zone trust
[FW1-policy-security-rule-nat]destination-zone untrust
[FW1-policy-security-rule-nat]source-address 192.168.3.0 24
[FW1-policy-security-rule-nat]service icmp
[FW1-policy-security-rule-nat]action permit
//配置静态路由
[FW1]ip route-static 0.0.0.0 0 200.1.12.1
检查连通性
PC1 ping Client1:
PC>ping 200.1.1.1
Ping 200.1.1.1: 32 data bytes, Press Ctrl_C to break
From 200.1.1.1: bytes=32 seq=1 ttl=254 time=78 ms
From 200.1.1.1: bytes=32 seq=2 ttl=254 time=46 ms
From 200.1.1.1: bytes=32 seq=3 ttl=254 time=62 ms
From 200.1.1.1: bytes=32 seq=4 ttl=254 time=62 ms
From 200.1.1.1: bytes=32 seq=5 ttl=254 time=47 ms
--- 200.1.1.1 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 46/59/78 ms
配置FTP
配置NAT
FW3:
[FW3]nat address-group 2
[FW3-address-group-1]section 200.1.3.10 200.1.3.10
[FW3-address-group-1]q
[FW3]nat-policy
[FW3-policy-nat]rule name u_t
[FW3-policy-nat-rule-t_u]source-zone untrust
[FW3-policy-nat-rule-t_u]destination-zone trust
[FW3-policy-nat-rule-t_u]source-address 200.1.1.0 24
[FW3-policy-nat-rule-t_u]action source-nat address-group 2
配置安全策略
FW3:
[FW3]security-policy
[FW3-policy-security]rule name ftp
[FW3-policy-security-rule-ftp]source-zone untrust
[FW3-policy-security-rule-ftp]destination-zone trust
[FW3-policy-security-rule-ftp]source-address 200.1.1.0 24
[FW3-policy-security-rule-ftp]destination-address 192.168.2.0 24
[FW3-policy-security-rule-ftp]service ftp
[FW3-policy-security-rule-ftp]action permit
配置ASPF
FW3:
[FW3]firewall detect ftp
检查连通性
实验总结
通过本次实验我学会了如何灵活地运用双机热备和IPSec配置。实验比较复杂,需要先想清楚要实现的功能对应的大概配置和要用到的协议,然后再一部分一部分地去完善实验。同时也要考虑配置的顺序问题,此处实验中将双机热备先配置明显较为省事。同时也要注意安全策略的配置顺序,防止需要的策略先被匹配而无法实行。