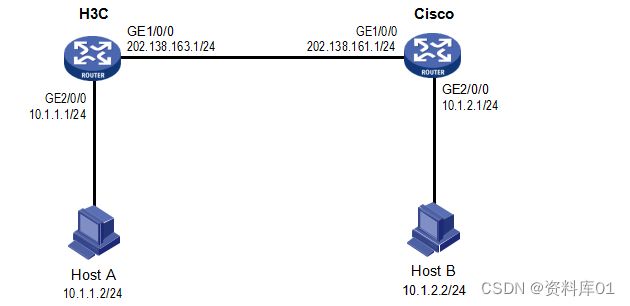
H3C路由器与Cisco路由器IPSEC对接
- IKE 主模式及预共享密钥认证配置举例
- 组网需求
在 H3C 路由器和 Cisco 路由器之间建立一个 IPsec 隧道,对Host A 所在的子网(10.1.1.0/24)与
Host B 所在的子网(10.1.2.0/24)之间的数据流进行安全保护。
-
-
- H3C 路由器与 Cisco 路由器之间采用 IKE 协商方式建立 IPsec SA。
- 协商双方使用缺省的 IKE 提议。
- 第一阶段协商的认证方法为预共享密钥认证。
-
-
- 配置步骤
- 配置 H3C 路由器
- 配置步骤
# 配置各接口的 IP 地址,具体略。
# 配置 IPv4 高级 ACL 3000,定义要保护由子网 10.1.1.0/24 去子网 10.1.2.0/24 的数据流。
[H3C-acl-ipv4-adv-3000] rule permit ip source 10.1.1.0 0.0.0.255 destination 10.1.2.0
0.0.0.255
[H3C-acl-ipv4-adv-3000] quit
# 创建 IPsec 安全提议 tran1。
[H3C] ipsec transform-set tran1
# 配置安全协议对 IP 报文的封装形式为隧道模式。
[H3C-ipsec-transform-set-tran1] encapsulation-mode tunnel
# 配置采用的安全协议为ESP。
[H3C-ipsec-transform-set-tran1] protocol esp
# 配置ESP 协议采用的加密算法为 128 比特的 AES,认证算法为 HMAC-SHA256。
[H3C-ipsec-transform-set-tran1] esp encryption-algorithm aes-cbc-128 [H3C-ipsec-transform-set-tran1] esp authentication-algorithm sha256 [H3C-ipsec-transform-set-tran1] quit
# 创建 IKE keychain,名称为 keychain1。
[H3C] ike keychain keychain1
# 配置与 IP 地址为 202.138.161.1 的对端使用的预共享密钥为明文 123456。
[H3C-ike-keychain-keychain1] pre-shared-key address 202.138.161.1 255.255.255.0 key simple 123456
[H3C-ike-keychain-keychain1] quit # 创建 IKE profile,名称为 profile1。[H3C] ike profile profile1
# 指定引用的 IKE keychain 为keychain1。
[H3C-ike-profile-profile1] keychain keychain1
# 配置本端的身份信息为 IP 地址 202.138.163.1。
[H3C-ike-profile-profile1] local-identity address 202.138.163.1
# 配置匹配对端身份的规则为 IP 地址 202.138.161.1。
[H3C-ike-profile-profile1] match remote identity address 202.138.161.1 [H3C-ike-profile-profile1] quit
# 创建一条 IKE 协商方式的 IPsec 安全策略,名称为 map1,顺序号为 10。
[H3C] ipsec policy map1 10 isakmp
# 配置 IPsec 隧道的对端 IP 地址为 202.138.161.1。
[H3C-ipsec-policy-isakmp-map1-10] remote-address 202.138.161.1
# 指定引用ACL 3000。
[H3C-ipsec-policy-isakmp-map1-10] security acl 3000
# 指定引用的安全提议为 tran1。
[H3C-ipsec-policy-isakmp-map1-10] transform-set tran1
# 指定引用的 IKE profile 为 profile1。
[H3C-ipsec-policy-isakmp-map1-10] ike-profile profile1 [H3C-ipsec-policy-isakmp-map1-10] quit
# 在接口 GigabitEthernet1/0/0 上应用 IPsec 安全策略 map1。
[H3C] interface gigabitethernet 1/0/0
[H3C-GigabitEthernet1/0/0] ipsec apply policy map1 [H3C-GigabitEthernet1/0/0] quit
# 配置到Host B 所在子网的静态路由。202.138.163.2 为本例中的直连下一跳地址,实际使用中请
以具体组网情况为准。
[H3C] ip route-static 10.1.2.0 255.255.255.0 202.138.163.2
-
-
- 配置 Cisco 路由器
-
Cisco# configure terminal Cisco(config)# crypto isakmp policy 1
Cisco(config-isakmp)# authentication pre-share Cisco(config-isakmp)# exit
Cisco(config)# crypto isakmp key 123456 address 202.138.163.1 255.255.255.0 //配置预共享密
钥为 123456
Cisco(config)# crypto isakmp peer address 202.138.163.1 //指定 IKE 协商时本端 ID 类型为 IP 形式
Cisco(config-isakmp-peer)# exit
Cisco(config)# crypto ipsec transform-set p1 esp-sha256-hmac esp-aes 128 //配置IPsec 采用的安全算法
Cisco(cfg-crypto-trans)# exit
Cisco(config)# crypto map p1 1 ipsec-isakmp //配置 IPsec 安全策略Cisco(config-crypto-map)# set peer 202.138.163.1 //采用IP 地址方式标识对等体Cisco(config-crypto-map)# set transform-set p1
Cisco(config-crypto-map)# match address 102 Cisco(config-crypto-map)# exit
Cisco(config)# interface GigabitEthernet1/0/0 Cisco(config-if)# ip address 202.138.161.1 255.255.255.0
Cisco(config-if)# duplex auto Cisco(config-if)# speed auto
Cisco(config-if)# crypto map p1 //在接口上应用安全策略
Cisco(config-if)# exit
Cisco(config)# interface GigabitEthernet2/0/0 Cisco(config-if)# ip address 10.1.2.1 255.255.255.0 Cisco(config-if)# duplex auto
Cisco(config-if)# speed auto Cisco(config-if)# exit
Cisco(config)# ip route 0.0.0.0 0.0.0.0 202.138.161.2 //配置静态路由,保证两端路由可达
Cisco(config)# access-list 102 permit ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255 //指定被保护的数据流
Cisco(config)# end
-
- 验证配置
以上配置完成后,H3C 路由器和 Cisco 路由器之间如果有子网 10.1.1.0/24 与子网 10.1.2.0/24 之间的报文通过,将触发 IKE 协商。
# 在 H3C 路由器上执行 display ike sa 命令,可以查看到 H3C 路由器上 IKE 第一阶段协商成功后生成的 IKE SA。
| [H3C] display ike Connection-ID |
sa |
Remote |
Flag |
DOI |
| 1 |
202.138.161.1/500 |
RD |
IPsec |
Flags:
RD--READY RL--REPLACED FD-FADING RK-REKEY
# 在 H3C 路由器上执行 display ipsec sa 命令,可以查看到 H3C 路由器上 IKE 第二阶段协商生成的
IPsec SA。
[H3C] display ipsec sa
Interface: GigabitEthernet1/0/0
- IPsec policy: map1
Sequence number: 10 Mode: ISAKMP
-
Tunnel id: 0
Encapsulation mode: tunnel Perfect Forward Secrecy:
Inside VPN:
Extended Sequence Numbers enable: N Traffic Flow Confidentiality enable: N Transmitting entity: Initiator
Path MTU: 1456
Tunnel:
local address/port: 202.138.163.1/500 remote address/port: 202.138.161.1/500
Flow:
sour addr: 10.1.1.0/255.255.255.0 port: 0 protocol: ip dest addr: 10.1.2.0/255.255.255.0 port: 0 protocol: ip
[Inbound ESP SAs]
SPI: 3264152513 (0xc28f03c1)
Connection ID: 90194313219
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA256
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3484 Max received sequence-number:
Anti-replay check enable: Y Anti-replay window size: 64
UDP encapsulation used for NAT traversal: N Status: Active
[Outbound ESP SAs]
SPI: 738451674 (0x2c03e0da)
Connection ID: 64424509441
Transform set: ESP-ENCRYPT-AES-CBC-128 ESP-AUTH-SHA256
SA duration (kilobytes/sec): 1843200/3600
SA remaining duration (kilobytes/sec): 1843200/3484 Max sent sequence-number:
UDP encapsulation used for NAT traversal: N Status: Active
#在Cisco 路由器上也会产生相应的 IKE SA 和 IPsec SA,查看方式为执行 show crypto isakmp sa
和 show crypto ipsec sa 命令,此处略。
-
- 配置文件
- H3C:
- 配置文件
#
sysname H3C
#
interface GigabitEthernet1/0/0 port link-mode route
ip address 202.138.163.1 255.255.255.0
ipsec apply policy map1
#
interface GigabitEthernet2/0/0 port link-mode route
ip address 10.1.1.1 255.255.255.0
#
ipsec transform-set tran1
esp encryption-algorithm aes-cbc-128 esp authentication-algorithm sha256
#
ipsec policy map1 10 isakmp transform-set tran1 security acl 3000
remote-address 202.138.161.1 ike-profile profile1
#
ike profile profile1 keychain keychain1
match remote identity address 202.138.161.1
#
ke keychain keychain1
pre-shared-key address 202.138.161.1 255.255.255.0 key simple 123456
#
Return
-
-
- Cisco:
-
!
crypto isakmp policy 1 authentication pre-share
crypto isakmp key 123456 address 202.138.163.1 255.255.255.0
!
crypto isakmp peer address 202.138.163.1
!
crypto ipsec transform-set p1 esp-sha256-hmac esp-aes 128
!
crypto map p1 1 ipsec-isakmp set peer 202.138.163.1
set transform-set p1 match address 102
!
!
interface GigabitEthernet1/0/0 ip address 202.138.161.1 255.255.255.0 duplex auto
speed auto crypto map p1
!
interface GigabitEthernet2/0/0 ip address 10.1.2.1 255.255.255.0 duplex auto
speed auto
!
!
ip route 0.0.0.0 0.0.0.0 202.138.161.2
!
access-list 102 permit ip 10.1.2.0 0.0.0.255 10.1.1.0 0.0.0.255
!
end