华为路由器 IPSec VPN 配置
需求:
通过 IPSecVPN 实现上海与成都内网互通
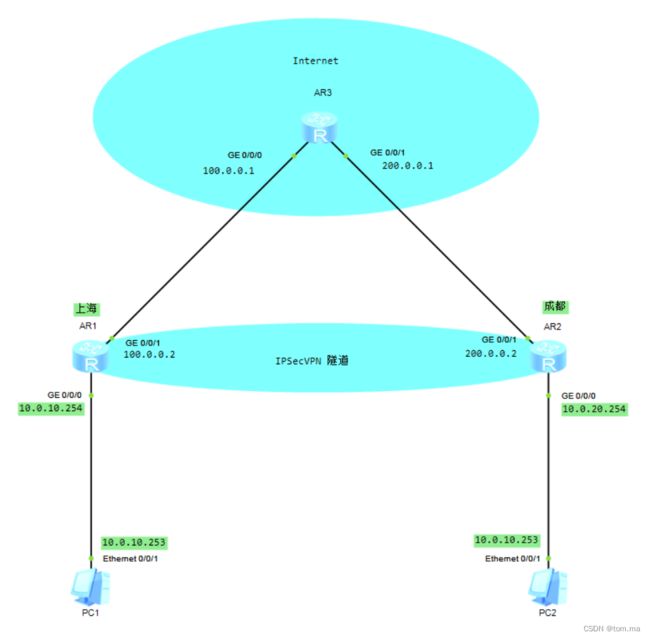
拓扑图如下:
一、首先完成网络配置
1、R1 路由器设置
sys
[Huawei]sys R1
[R1]un in en
# 开启DHCP
[R1]dhcp enable
# 设置内网接口
[R1]int g0/0/0
[R1-GigabitEthernet0/0/0]ip addr 10.0.10.254 24
[R1-GigabitEthernet0/0/0]dhcp select int
[R1-GigabitEthernet0/0/0]quit
# 设置外网接口
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ip addr 100.0.0.2 24
[R1-GigabitEthernet0/0/1]quit
# 设置 NAT
[R1]acl 3000
# 配置 NO-NAT
[R1-acl-adv-3000]rule 5 deny ip source 10.0.10.0 0.0.0.255 destination 10.0.20.0 0.0.0.255
[R1-acl-adv-3000]rule 10 permit ip source 10.0.10.0 0.0.0.255
[R1-acl-adv-3000]int g0/0/1
[R1-GigabitEthernet0/0/1]nat outbound 3000
# 设置默认路由
[R1-GigabitEthernet0/0/1]ip route-static 0.0.0.0 0 100.0.0.1
2、R2路由器设置
# 重命名并关闭提示
sys
[Huawei]sys R2
[R2]un in en
# 开启DHCP
[R2]dhcp enable
# 配置内网地址
[R2]int g0/0/0
[R2-GigabitEthernet0/0/0]ip addr 10.0.20.254 24
[R2-GigabitEthernet0/0/0]dhcp select int
[R2-GigabitEthernet0/0/0]quit
# 配置外网接口
[R2]int g0/0/1
[R2-GigabitEthernet0/0/1]ip addr 200.0.0.2 24
[R2-GigabitEthernet0/0/1]quit
# 配置 NAT
[R2]acl 3000
# 配置 NO-NAT
[R2-acl-adv-3000]rule 5 deny ip source 10.0.20.0 0.0.0.255 destination 10.0.10.0 0.0.0.255
[R2-acl-adv-3000]rule 10 permit ip source 10.0.20.0 0.0.0.255
[R2-acl-adv-3000]int g0/0/1
[R2-GigabitEthernet0/0/1]nat outbound 3000
# 配置默认路由
[R2-GigabitEthernet0/0/1]ip route-static 0.0.0.0 0 200.0.0.1 3、测试
PC1能访问 R2 的外网地址
PC1>ping 200.0.0.2
Ping 200.0.0.2: 32 data bytes, Press Ctrl_C to break
From 200.0.0.2: bytes=32 seq=1 ttl=253 time=31 ms
From 200.0.0.2: bytes=32 seq=2 ttl=253 time=31 ms
From 200.0.0.2: bytes=32 seq=3 ttl=253 time=32 ms
From 200.0.0.2: bytes=32 seq=4 ttl=253 time=15 ms
From 200.0.0.2: bytes=32 seq=5 ttl=253 time=15 ms
--- 200.0.0.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 15/24/32 msPC2能访问 R1 的外网地址
PC2>ping 100.0.0.2
Ping 100.0.0.2: 32 data bytes, Press Ctrl_C to break
From 100.0.0.2: bytes=32 seq=1 ttl=253 time=78 ms
From 100.0.0.2: bytes=32 seq=2 ttl=253 time=31 ms
From 100.0.0.2: bytes=32 seq=3 ttl=253 time=32 ms
From 100.0.0.2: bytes=32 seq=4 ttl=253 time=31 ms
From 100.0.0.2: bytes=32 seq=5 ttl=253 time=31 ms
--- 100.0.0.2 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
round-trip min/avg/max = 31/40/78 msPC1 不能访问 PC2,反之也是
PC1>ping 10.0.20.253
Ping 10.0.20.253: 32 data bytes, Press Ctrl_C to break
Request timeout!
Request timeout!
Request timeout!
Request timeout!
Request timeout!
--- 10.0.20.253 ping statistics ---
5 packet(s) transmitted
0 packet(s) received
100.00% packet loss
上面的网络情况跟生产环境基本一致。我们要在 R1 跟 R2 之间配置 IPSec VPN,实现上海与成都两地内网互通
二、配置 IPSec
1、R1 路由器设置
(1)IKE 第一阶段 建立 IKE(ISAKMP)SA
# 配置 ike 提议
[R1]ike proposal 1
[R1-ike-proposal-1]encryption-algorithm aes-cbc-256
[R1-ike-proposal-1]authentication-algorithm sha1
[R1-ike-proposal-1]authentication-method pre-share
[R1-ike-proposal-1]dh group14
[R1-ike-proposal-1]sa duration 1200
[R1-ike-proposal-1]quit
# 配置 ike 对等体,使用 v2 协议
[R1]ike peer 1 v2
# 共享密码
[R1-ike-peer-1]pre-shared-key simple 123456
# 引用 ike 提议
[R1-ike-peer-1]ike-proposal 1
# 配置远程地址
[R1-ike-peer-1]remote-address 200.0.0.2(2)IKE 第二阶段 建立 IPSec SA
# 配置兴趣流
[R1-ike-peer-1]acl 3001
[R1-acl-adv-3001]rule permit ip source 10.0.10.0 0.0.0.255 destination 10.0.20.0 0.0.0.255
[R1-acl-adv-3001]quit
# 配置 ipsec 提议
[R1]ipsec proposal 1
# 认证算法
[R1-ipsec-proposal-1]esp authentication-algorithm sha1
# 加密算法
[R1-ipsec-proposal-1]esp encryption-algorithm aes-256
# 缺省情况下,IPSec安全提议采用安全协议为ESP协议
[R1-ipsec-proposal-1]transform esp
[R1-ipsec-proposal-1]quit
# 配置 ipsec 策略
[R1]ipsec policy 1 1 isakmp
# 引用 acl
[R1-ipsec-policy-isakmp-1-1]security acl 3001
# 引用 ike 对等体
[R1-ipsec-policy-isakmp-1-1]ike-peer 1
# 引用 ipsec 提议
[R1-ipsec-policy-isakmp-1-1]proposal 1
[R1-ipsec-policy-isakmp-1-1]quit
# 接口绑定策略
[R1]int g0/0/1
[R1-GigabitEthernet0/0/1]ipsec policy 1
2、R2 路由器设置
# 配置 ike 提议
[R2]ike proposal 1
[R2-ike-proposal-1]encryption-algorithm aes-cbc-256
[R2-ike-proposal-1]authentication-algorithm sha1
[R2-ike-proposal-1]authentication-method pre-share
[R2-ike-proposal-1]dh group14
[R2-ike-proposal-1]sa duration 1200
[R2-ike-proposal-1]quit
# 配置 ike 对等体
[R2]ike peer 1 v2
[R2-ike-peer-1]pre-shared-key simple 123456
[R2-ike-peer-1]ike-proposal 1
[R2-ike-peer-1]remote-address 100.0.0.2
# 配置兴趣流
[R2-ike-peer-1]acl 3001
[R2-acl-adv-3001]rule permit ip source 10.0.20.0 0.0.0.255 destination 10.0.10.0 0.0.0.255
[R2-acl-adv-3001]quit
# 配置 ipsec 提议
[R2]ipsec proposal 1
[R2-ipsec-proposal-1]esp authentication-algorithm sha1
[R2-ipsec-proposal-1]esp encryption-algorithm aes-256
[R2-ipsec-proposal-1]transform esp
[R2-ipsec-proposal-1]quit
# 配置 ipsec 策略
[R2]ipsec policy 1 1 isakmp
[R2-ipsec-policy-isakmp-1-1]security acl 3001
[R2-ipsec-policy-isakmp-1-1]ike-peer 1
[R2-ipsec-policy-isakmp-1-1]proposal 1
[R2-ipsec-policy-isakmp-1-1]quit
# 接口绑定策略
[R2]int g0/0/1
[R2-GigabitEthernet0/0/1]ipsec policy 1
3、我们再次测试 pc1 访问 pc2,这次发现通了,说明 IPSec 通了
PC1>ping 10.0.20.253
Ping 10.0.20.253: 32 data bytes, Press Ctrl_C to break
From 10.0.20.253: bytes=32 seq=1 ttl=127 time=16 ms
From 10.0.20.253: bytes=32 seq=2 ttl=127 time=31 ms
From 10.0.20.253: bytes=32 seq=3 ttl=127 time=32 ms
From 10.0.20.253: bytes=32 seq=4 ttl=127 time=46 ms
From 10.0.20.253: bytes=32 seq=5 ttl=127 time=16 ms
--- 10.0.20.253 ping statistics ---
5 packet(s) transmitted
5 packet(s) received
0.00% packet loss
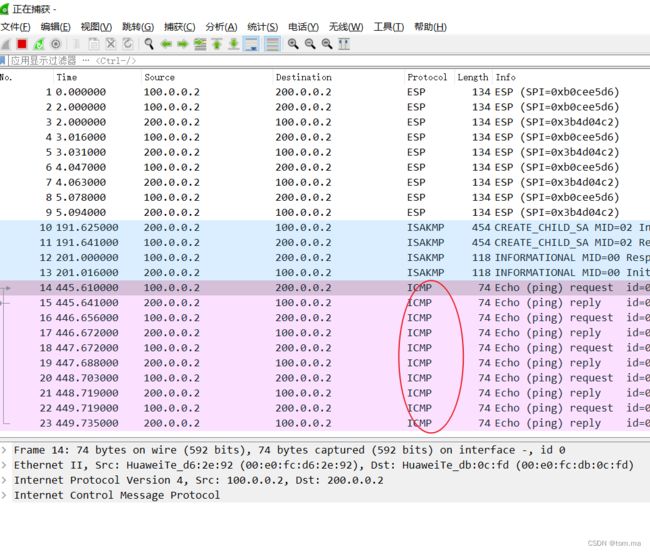
round-trip min/avg/max = 16/28/46 ms4、我们在 R1 路由器 g0/0/1 接口抓包
(1)我们在 pc1 上面 ping pc2
通过上面得出当 10.0.10.0 网段访问 10.0.20.0 网段时,的确走VPN隧道协议,并且目的地址也变成了外网地址。
(2)我们再拿 PC1 访问 成都的外网地址 200.0.0.2,然后进行抓包
通过上面得出走的就是常规的路由了,至于为什么我拿 PC1的地址去 访问 200.0.0.2,抓包显示的原地址是 100.0.0.2,是因为我们在R1上面配了 NAT,所有流量都以 100.0.0.2 出去