2021-12-12金盾杯Re Wp
Re1
flag = 'gnbc~0221gg00>4f;g221944=1>62c61=3d71~'
key = [1,2,3,4,5,6,7]
aaa = []
for i in range(0,len(flag)):
a=ord(flag[i])
aaa.append(a^key[i%7])
print(''.join(map(chr,aaa)))flag{6533dc5695d8c74686794813a5585c63}
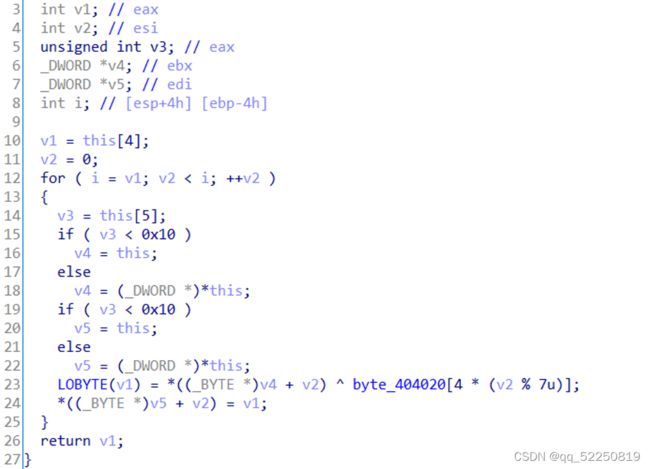
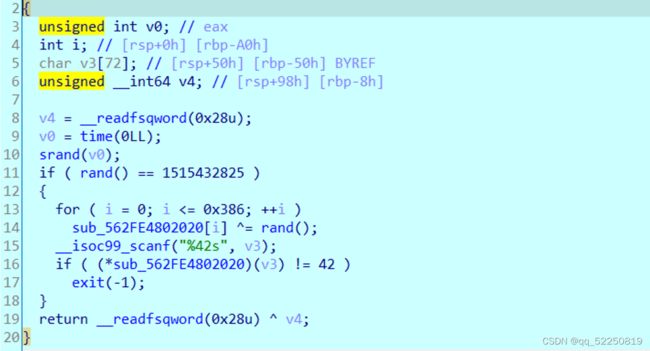
Re2
Main函数没有用,真正的要逆向的函数是main函数上面的那个
这个首先会用当前时间作为种子,取第一个随机数,且要等与1515432825
然后for循环会对地址0x562FE4802020处数据进行解密
解密后函数
对随机数进行爆破,题目给了一个时间2021.1.23 4:56:00
以此时间为基础
#include
#include
#include
int main()
{
int seed = 1611377760;
for (int k = seed; ;)
{
srand(k);
if(rand() == 1515432825)
{
printf("%d",k);
break;
}
k++;
}
return 0;
} 结果为1614027360
#include
#include
#include
int main()
{
int v3[42], v4[42];
v3[0] = 61;
v3[1] = 159;
v3[2] = 9;
v3[3] = 29;
v3[4] = 146;
v3[5] = 126;
v3[6] = 169;
v3[7] = 130;
v3[8] = 106;
v3[9] = 19;
v3[10] = 233;
v3[11] = 31;
v3[12] = 142;
v3[13] = 51;
v3[14] = 80;
v3[15] = 143;
v3[16] = 113;
v3[17] = 7;
v3[18] = 29;
v3[19] = 251;
v3[20] = 28;
v3[21] = 209;
v3[22] = 237;
v3[23] = 15;
v3[24] = 152;
v3[25] = 82;
v3[26] = 22;
v3[27] = 39;
v3[28] = 215;
v3[29] = 245;
v3[30] = 155;
v3[31] = 56;
v3[32] = 89;
v3[33] = 220;
v3[34] = 239;
v3[35] = 87;
v3[36] = 82;
v3[37] = 180;
v3[38] = 252;
v3[39] = 235;
v3[40] = 117;
v3[41] = 11;
v4[0] = 91;
v4[1] = 243;
v4[2] = 104;
v4[3] = 122;
v4[4] = 233;
v4[5] = 77;
v4[6] = 203;
v4[7] = 225;
v4[8] = 93;
v4[9] = 39;
v4[10] = 217;
v4[11] = 126;
v4[12] = 187;
v4[13] = 30;
v4[14] = 103;
v4[15] = 187;
v4[16] = 21;
v4[17] = 62;
v4[18] = 48;
v4[19] = 207;
v4[20] = 126;
v4[21] = 225;
v4[22] = 136;
v4[23] = 34;
v4[24] = 249;
v4[25] = 102;
v4[26] = 115;
v4[27] = 23;
v4[28] = 250;
v4[29] = 150;
v4[30] = 250;
v4[31] = 94;
v4[32] = 111;
v4[33] = 236;
v4[34] = 214;
v4[35] = 53;
v4[36] = 101;
v4[37] = 215;
v4[38] = 205;
v4[39] = 136;
v4[40] = 69;
v4[41] = 118;
for (int i = 0; i< 42; i++)
{
printf("%c",v3[i]^v4[i]);
}
return 0;
} flag{3bc740a5-74d9-4b0e-a4e0-caf609b7c1c0}
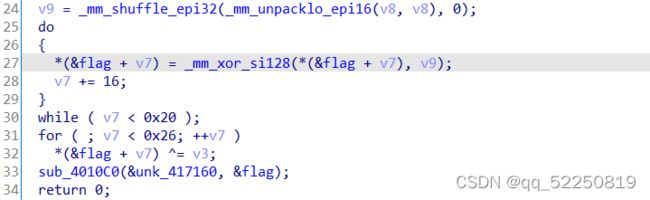
Re3
看起来很麻烦,但flag进行两次异或后就输出了
flag第一位是f,'f'^0x19=127
flag = [ 0x19, 0x13, 0x1E, 0x18, 0x04, 0x31, 0x14, 0x26, 0x4F, 0x32,
0x2B, 0x32, 0x4B, 0x31, 0x2B, 0x36, 0x4E, 0x32, 0x14, 0x36,
0x06, 0x32, 0x2A, 0x2D, 0x3B, 0x2D, 0x15, 0x2E, 0x4E, 0x30,
0x3A, 0x26, 0x4A, 0x30, 0x3A, 0x2E, 0x4F, 0x02]
for i in range(0,len(flag)):
flag[i]^=127
print(''.join(map(chr, flag)))flag{NkY0MTM4NTI1MkIyMURDRjQ1OEY5OEQ0}
Re4
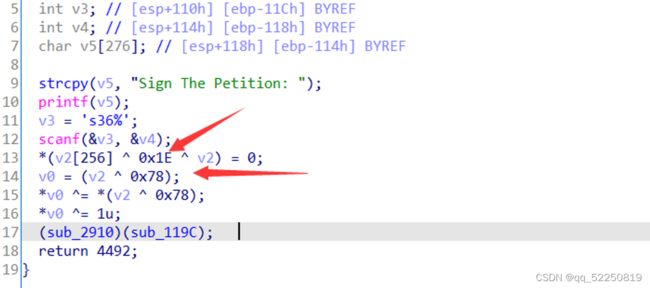
flag为42位,start函数也嵌套了42次
0x1e^0x78=f......
flag{96c69646-8184-4363-8de9-73f7398066c1}
Re5
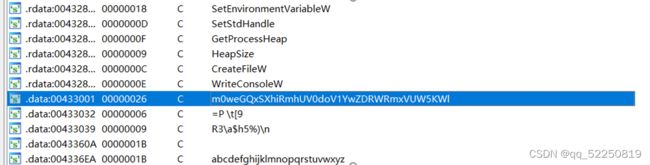
Main函数里啥也没有,在字符串窗口里中找到了一串像密文的字符串
进入调用它的函数
str = 'Vm0weGQxSXhiRmhUV0doV1YwZDRWRmxVUW5KWl'
flag = [ 0x30, 0x01, 0x51, 0x10, 0x1E, 0x1E, 0x05, 0x32, 0x04, 0x16,
0x3D, 0x50, 0x20, 0x09, 0x5B, 0x39, 0x0E, 0x52, 0x33, 0x07,
0x24, 0x68, 0x35, 0x25, 0x29, 0x0A, 0x04, 0x06, 0x2B, 0x09,
0x30, 0x18, 0x00, 0x1A, 0x63, 0x3B, 0x10, 0x11]
for i in range(0, len(str)):
flag[i]^=ord(str[i])
print(''.join(map(chr, flag)))flag{YTJWNU9rd3lXbWhrYlRsNVQydHNUMVpG}