安全技术与防火墙
目录
一、安全技术
1、安全技术
2、防火墙的分类
二、netfilter
1、netfilter简述
2、防火墙工具
1.iptables工具
2.netfilter的四表五链
3.内核中数据包的传输过程
4.三种报文流向
5.实操
总结:本章主要介绍了安全技术与防火墙
一、安全技术
1、安全技术
1、入侵检测系统
特点是不阻断任何网络访问,量化、定位来自内外网络的威胁情况,主要以提供报警和事后监督为主,提供有针对性的指导措施和安全决策依据一般采用旁路部署方式
2、入侵防御系统
以透明模式工作,分析数据包的内容如:溢出攻击、拒绝服务攻击、系统漏洞等进行准确的分析判断,在判定为攻击行为后立即予以 阻断,主动而有效的保护网络的安全,一般采用在线部署方式
3、防火墙
隔离功能,工作在网络或主机边缘,对进出网络或主机的数据包基于一定的规则检查,并在匹配某规则时由规则定义的行为进行处理的一组功能的组件,基本上的实现都是默 认情况下关闭所有的通过型访问,只开放允许访问的策略
2、防火墙的分类
按保护范围划分:
主机防火墙:服务范围为当前一台主机
网络防火墙:服务范围为防火墙一侧的局域网
按实现方式划分:
硬件防火墙:在专用硬件级别实现部分功能的防火墙;另一个部分功能基于软件实现,如:华为, 山石hillstone,天融信,启明星辰,绿盟,深信服, PaloAlto , fortinet, Cisco, Checkpoint, NetScreen(Juniper2004年40亿美元收购)等
软件防火墙:运行于通用硬件平台之上的防火墙的应用软件,Windows 防火墙 ISA --> Forefront
按网络协议划分:
网络层防火墙:OSI模型下四层,又称为包过滤防火墙
应用层防火墙/代理服务器:proxy 代理网关,OSI模型七层
二、netfilter
1、netfilter简述
Linux防火墙是由Netfilter组件提供的,Netfilter工作在内核空间,集成在linux内核中
Netfilter 是Linux 2.4.x之后新一代的Linux防火墙机制,是linux内核的一个子系统。Netfilter采用模块化设计,具有良好的可扩充性,提供扩展各种网络服务的结构化底层框架。Netfilter与IP协议栈是无缝契合,并允许对数据报进行过滤、地址转换、处理等操作
2、防火墙工具
防火墙工具有:
1.iptables
2.firewalld
3.nftables
4.netfilter
1.iptables工具
iptables --version
[root@localhost ~]# iptables --version
iptables v1.4.21
[root@localhost ~]# 2.netfilter的四表五链
表中有链,链中有规则
五链(控制流量的时机)
input :进入本机的流量
output :离开本机的流量
forward :转发
prerouting :路由选择前
postrouting :路由选择后
四表(如何控制流量)
raw表 :确定是否对数据包进行状态跟踪
mangle表 :为数据包设置标记(优先级)
nat表 :修改数据包中的源,目标IP地址或端口(地址转化)
filter表 :确定是否放行该数据包(过滤流量)
3.内核中数据包的传输过程
-
当一个数据包进入网卡时,数据包首先进入PREROUTING链,内核根据数据包目的IP判断是否需要 转送出去
-
如果数据包是进入本机的,数据包就会沿着图向下移动,到达INPUT链。数据包到达INPUT链后, 任何进程都会收到它。本机上运行的程序可以发送数据包,这些数据包经过OUTPUT链,然后到达
-
如果数据包是要转发出去的,且内核允许转发,数据包就会向右移动,经过FORWARD链,然后到达POSTROUTING链输出
4.三种报文流向
流入本机:PREROUTING --> INPUT-->用户空间进程
流出本机:用户空间进程 -->OUTPUT--> POSTROUTING
转发:PREROUTING --> FORWARD --> POSTROUTING
5.实操
CentOS7默认使用firewalld防火墙,没有安装iptables,若想使用iptables防火墙。必须先关闭firewalld防火墙,再安装iptables
先准备环境:
[root@localhost ~]# systemctl stop firewalld
[root@localhost ~]# systemctl disable --now firewalld.service
[root@localhost ~]# yum install -y iptables
已加载插件:fastestmirror, langpacks
Loading mirror speeds from cached hostfile
* base: mirrors.163.com
* epel: mirrors.bfsu.edu.cn
* extras: mirrors.163.com
* updates: mirrors.ustc.edu.cn
软件包 iptables-1.4.21-35.el7.x86_64 已安装并且是最新版本
无须任何处理
[root@localhost ~]#
1.iptables语法:
iptables [-t 表名] 管理选项 [链名] [匹配条件] [-j 控制类型]
如果不用-t指定默认是filter
2.数据包的常见控制类型:
-ACCEPT:允许数据包通过
-DROP:直接丢弃数据包
-REJECT:拒绝数据包通过
-LOG:日志,添加备注,传递数据包给下一条规则
-SNAT:修改数据包的源地址
-DNAT:修改数据包的目的地址
-MASQUERADE:伪装成一个非固定公网IP地址
3.iptables的管理选项:
-A:在指定链末尾追加
-I:在指定链中插入新策略(未指定默认第一条)
-P:修改策略
-D:删除策略
-v:详细信息
-n:数字化
-L:防火墙列表
-s:指定源地址
-j:跳转
-t:指定表
-F:清空策略
-d:目的地址
4.添加与查看
[root@localhost ~]# iptables -t filter -A INPUT -p tcp -jACCEPT
[root@localhost ~]# iptables -t filter -I INPUT -p udp -jACCEPT
[root@localhost ~]# iptables -vnL
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1 76 ACCEPT udp -- * * 0.0.0.0/0 0.0.0.0/0
118 8020 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 18 packets, 1336 bytes)
pkts bytes target prot opt in out source destination
Chain VL (0 references)
pkts bytes target prot opt in out source destination5.删除和追加
追加:
pc1
[root@localhost ~]# iptables -A INPUT -s 172.16.114.20 -j DROP
遇到172.16.114.20的流量都丢弃
pc2
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
^C
--- 172.16.114.10 ping statistics ---
11 packets transmitted, 0 received, 100% packet loss, time 10004ms
[root@localhost ~]#
追加策略后,策略生效ping的包全部丢失
[root@localhost ~]# iptables -A INPUT -s 172.16.114.20 -j DROP
[root@localhost ~]# iptables -vnL
Chain INPUT (policy ACCEPT 50 packets, 3872 bytes)
pkts bytes target prot opt in out source destination
12 1000 DROP all -- * * 172.16.114.20 0.0.0.0/0
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 15 packets, 1260 bytes)
pkts bytes target prot opt in out source destination
Chain VL (0 references)
pkts bytes target prot opt in out source destination
[root@localhost ~]# iptables -D INPUT 1
[root@localhost ~]# iptables -vnL
Chain INPUT (policy ACCEPT 6 packets, 364 bytes)
pkts bytes target prot opt in out source destination
Chain FORWARD (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 4 packets, 384 bytes)
pkts bytes target prot opt in out source destination
Chain VL (0 references)
pkts bytes target prot opt in out source destination
[root@localhost ~]#
pc1删除策略后:
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
64 bytes from 172.16.114.10: icmp_seq=1 ttl=64 time=0.767 ms
64 bytes from 172.16.114.10: icmp_seq=2 ttl=64 time=1.13 ms
64 bytes from 172.16.114.10: icmp_seq=3 ttl=64 time=0.504 ms
^C
--- 172.16.114.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2003ms
rtt min/avg/max/mdev = 0.504/0.800/1.131/0.259 ms
[root@localhost ~]#
pc2可以ping通了
设置白名单:
iptables -P INPUT DROP
iptables -s 172.16.114.10 -P INPUT DROP
iptables v1.4.21: Illegal option `-s' with this command
Try `iptables -h' or 'iptables --help' for more information.
[root@localhost ~]# iptables -I INPUT 2 -i lo -j ACCEPT
[root@localhost ~]# ping 127.0.0.1
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.
64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.041 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.079 ms
64 bytes from 127.0.0.1: icmp_seq=3 ttl=64 time=0.134 ms
64 bytes from 127.0.0.1: icmp_seq=4 ttl=64 time=0.072 ms
^C
--- 127.0.0.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.041/0.081/0.134/0.034 ms
iptables -t filter -A INPUT ! -p icmp -j ACCEPT
[root@localhost ~]# iptables -F
[root@localhost ~]# iptables -P INPUT ACCEPT
[root@localhost ~]# pc1:配置只允许172.16.114.20访问
[root@localhost ~]# iptables -A INPUT -s 172.16.114.20 -j ACCEPT
[root@localhost ~]# iptables -A INPUT -i lo -j ACCEPT
[root@localhost ~]# iptables -A INPUT -j REJECTpc2:可以看见连接上了
[root@localhost ~]# ssh 172.16.114.10
The authenticity of host '172.16.114.10 (172.16.114.10)' can't be established.
ECDSA key fingerprint is SHA256:Zujj39bI5gmpNp7llhmoG7MsStyii22ClbiRDXhzdi0.
ECDSA key fingerprint is MD5:28:e5:a5:7a:6a:1f:0c:05:12:3a:bd:21:9e:ab:0d:90.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.114.10' (ECDSA) to the list of known hosts.
[email protected]'s password:
Last login: Wed Nov 29 18:29:35 2023 from 172.16.114.1
[root@localhost ~]#
pc1:可以看见连接不上了
[C:\~]$ ssh 172.16.114.10
Connecting to 172.16.114.10:22...
Could not connect to '172.16.114.10' (port 22): Connection failed.
Type `help' to learn how to use Xshell prompt.
[C:\~]$
设置黑名单:
pc1:
[root@localhost ~]# iptables -P INPUT ACCEPT
[root@localhost ~]# iptables -A INPUT -s 172.16.114.20 -j REJECT
pc2:
[root@localhost ~]# ssh 172.16.114.10
ssh: connect to host 172.16.114.10 port 22: Connection refused
[root@localhost ~]#
可以看见pc2黑名单连接不上了
6.隐含扩展:
icmp扩展模块
pc1可以ping pc2
pc2不可以ping pc1
pc1:
[root@localhost ~]# iptables -A INPUT -p icmp --icmp-type 8 -j DROP
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
64 bytes from 172.16.114.10: icmp_seq=1 ttl=64 time=0.312 ms
64 bytes from 172.16.114.10: icmp_seq=2 ttl=64 time=1.97 ms
^C
--- 172.16.114.10 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 1000ms
rtt min/avg/max/mdev = 0.312/1.145/1.978/0.833 ms
[root@localhost ~]# iptables -A INPUT -p icmp --icmp-type 0 -j ACCEPT
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
64 bytes from 172.16.114.10: icmp_seq=1 ttl=64 time=0.444 ms
64 bytes from 172.16.114.10: icmp_seq=2 ttl=64 time=0.707 ms
^C
--- 172.16.114.10 ping statistics ---
2 packets transmitted, 2 received, 0% packet loss, time 999ms
rtt min/avg/max/mdev = 0.444/0.575/0.707/0.133 ms
[root@localhost ~]# iptables -A INPUT -p icmp -j REJECT
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
64 bytes from 172.16.114.10: icmp_seq=1 ttl=64 time=0.961 ms
64 bytes from 172.16.114.10: icmp_seq=2 ttl=64 time=0.616 ms
64 bytes from 172.16.114.10: icmp_seq=3 ttl=64 time=1.01 ms
^C
--- 172.16.114.10 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2001ms
rtt min/avg/max/mdev = 0.616/0.865/1.019/0.179 ms
[root@localhost ~]#pc2:
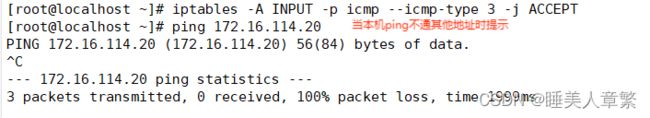
[root@localhost ~]# iptables -A INPUT -p icmp --icmp-type 3 -j ACCEPT
[root@localhost ~]# ping 172.16.114.20
PING 172.16.114.20 (172.16.114.20) 56(84) bytes of data.
^C
--- 172.16.114.20 ping statistics ---
3 packets transmitted, 0 received, 100% packet loss, time 1999ms
[root@localhost ~]#
multiport扩展模块:
pc1:
[root@localhost ~]# iptables -t filter -A INPUT -s 172.16.114.10 -p tcp -m multiport --dport 22,80 -j REJECT
[root@localhost ~]#
pc2:
[root@localhost ~]# ssh 172.16.114.20
ssh: connect to host 172.16.114.20 port 22: Connection refused
[root@localhost ~]# curl 172.16.114.20
curl: (7) Failed connect to 172.16.114.20:80; 拒绝连接
[root@localhost ~]#
可以看见这里pc2连接不上
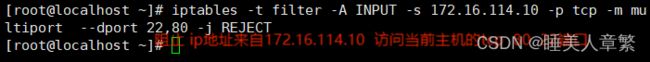
iprange扩展:
pc1
[root@localhost ~]# iptables -A INPUT -m iprange --src-range 172.16.114.20-172.16.114.21 -j REJECT
[root@localhost ~]#
设置这些地址的主机无法访问pc1
pc2
ltiport --dport 22,80 -j REJECT
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
From 172.16.114.10 icmp_seq=1 Destination Port Unreachable
From 172.16.114.10 icmp_seq=2 Destination Port Unreachable
^C
--- 172.16.114.10 ping statistics ---
2 packets transmitted, 0 received, +2 errors, 100% packet loss, time 1000ms
[root@localhost ~]#
7.时间设置
[root@localhost ~]# date
2023年 11月 29日 星期三 19:38:54 CST
[root@localhost ~]# date -u
2023年 11月 29日 星期三 11:39:02 UTC
[root@localhost ~]# iptables -A INPUT -m time --timestart 14:00 --time 16:00 -j REJECT
iptables v1.4.21: unknown option "--time"
Try `iptables -h' or 'iptables --help' for more information.
[root@localhost ~]# rpm -ql iptables|grep time
/usr/lib64/xtables/libxt_time.so
[root@localhost ~]#
state模块:
pc1:
64 bytes from 172.16.114.20: icmp_seq=133 ttl=64 time=1.09 ms
64 bytes from 172.16.114.20: icmp_seq=134 ttl=64 time=0.857 ms
64 bytes from 172.16.114.20: icmp_seq=135 ttl=64 time=0.899 ms
64 bytes from 172.16.114.20: icmp_seq=136 ttl=64 time=3.09 ms
64 bytes from 172.16.114.20: icmp_seq=137 ttl=64 time=0.250 ms
64 bytes from 172.16.114.20: icmp_seq=138 ttl=64 time=0.561 ms
64 bytes from 172.16.114.20: icmp_seq=139 ttl=64 time=0.544 ms
64 bytes from 172.16.114.20: icmp_seq=140 ttl=64 time=1.68 ms
64 bytes from 172.16.114.20: icmp_seq=141 ttl=64 time=1.25 ms
64 bytes from 172.16.114.20: icmp_seq=142 ttl=64 time=0.238 ms
64 bytes from 172.16.114.20: icmp_seq=143 ttl=64 time=0.612 ms
64 bytes from 172.16.114.20: icmp_seq=144 ttl=64 time=1.03 ms
64 bytes from 172.16.114.20: icmp_seq=145 ttl=64 time=0.711 ms
64 bytes from 172.16.114.20: icmp_seq=146 ttl=64 time=1.10 ms
64 bytes from 172.16.114.20: icmp_seq=147 ttl=64 time=1.28 ms
64 bytes from 172.16.114.20: icmp_seq=148 ttl=64 time=0.795 ms
64 bytes from 172.16.114.20: icmp_seq=149 ttl=64 time=0.601 ms
64 bytes from 172.16.114.20: icmp_seq=150 ttl=64 time=0.591 ms
64 bytes from 172.16.114.20: icmp_seq=151 ttl=64 time=0.522 ms
64 bytes from 172.16.114.20: icmp_seq=152 ttl=64 time=1.50 ms
[root@localhost ~]# iptables -A INPUT -m state --state NEW -j REJECT
[root@localhost ~]# iptables -A INPUT -m state --state ESTABLISHED -j ACCEPT
[root@localhost ~]#
pc2:
[root@localhost ~]# ping 172.16.114.10
PING 172.16.114.10 (172.16.114.10) 56(84) bytes of data.
From 172.16.114.10 icmp_seq=1 Destination Port Unreachable
From 172.16.114.10 icmp_seq=2 Destination Port Unreachable
From 172.16.114.10 icmp_seq=3 Destination Port Unreachable
^C
--- 172.16.114.10 ping statistics ---
3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2002ms
[root@localhost ~]#
这里可以看见在访问的主机正常访问,设置后其他主机访问不了了