[From HTTP to AWS][2]Analyze TCP/IP Packets
· HTTP Analyzer
如果你想成为一个黑客,应该也是可以看看的
When I am writing a desktop client for AWS S3, and storage service of Amazon Web Services. During the development, I need to check the in/out packets, including HTTP headers, Representations, so that I can have a clearer picture of S3 and RESTful web service.
Available Tools:
CommView, Wireshark, SmartSniff, TPCMon, HTTP/HTTPS Analyzer, OmniPeek, PacketView Pro and tcpdump.
After a few hours’ trying, I chose CommView finally.
The only reason is that I just know how to use it without reading any documents and it has a 30 days free trial. However, I will look into Wireshark which is open source and has similar functionalities to CommView.
In this document, I just focus on how to use it for my work. Now let’s start the strip.
1. Download it from http://www.tamos.com/;
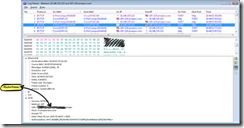
2. Install and open CommView and you can see following main frame.
Figure 1 Mainframe
In the mainframe, you see latest IP connections and add filtering rules.
3. Choose a NIC Adapter and start to record. Here is “Intel® 82566…….”
4. Choose “Rules” tab
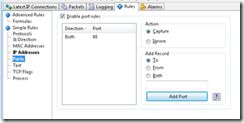
>> Add Ports Rules
Checks “Enable port rules” and add support for Port 80 in both direction.
Action = Capture
Add Record = Both
Add Port = HTTP
Figure 2 Add Ports Rules
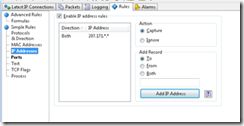
>> Add IP Addresses rules
I have already know the involved IP addresses are “207.171.*.*” during yesterday’s trying.
You can just skip these rules in the future.
Action = Capture
Add Record = Both
Add IP Addresses = 207.171.*.*
Figure 3 Add IP Addresses Rules
5. Run your AWS S3 client (CloudBerry, DragonDisk or …) and do some operations.
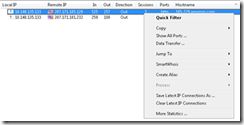
6. Open “Latest IP Connections” Tab
In “Latest IP Connections” Tab, you will see versatile information of each filtered out IP connection.
Figure 4 Latest IP Connections
To know when and who about the connection, I always concern about following data: Remote IP/Hostname, Sessions, and Last packet.
7. To know more about the connection, such as TCP/IP statistics and HTTP Headers/Presenatations, you can RMB on a connection and choose “Quick Filter” and “Log viewer” dialog will be presented.
Figure 5 Quick Filter
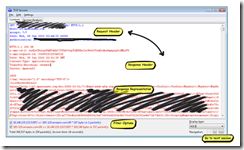
8. In Log viewer, you can see each In/Out Packets.
Figure 6 Log viewer
In this example, you can see the HTTP Header and know the request is to Get all keys under bucket .
| HTTP Header Version: HTTP/1.1 Method: GET URI: /uniquebucketname/ Host: s3.amazonaws.com Accept: */* Date: Wed, 09 Jun 2010 02:44:52 +0000 Authorization: AWS ADFGRYHVBVHTUTRURRET:NJGHJJGHJGHJYTRTsggretetet= |
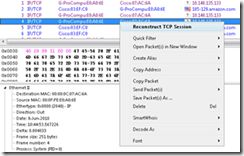
9. Another interested functionality is “Reconstruct TCP Session”
Figure 7 Reconstruct TCP Session
This tool allows you to view the TCP conversation between two hosts.
Figure 8 TCP Session dialog
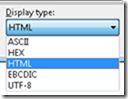
You can switch to other Display type if needed.
Figure 9 View Type
The Navigation buttons allow you to search the buffer for the next or previous TCP session.
10. Hehe. It’s the end.
I just show a simple workflow here. For more features of CommView and more information about how to monitor TCP conversion, it will be other stories.
In actual, if you are using Firefox, there are 2 addons, Live HTTP Headers and Modify header can be also used.
--------
还有网络分析和扫描工具:
>> Angry IP Scanner(开源)
Angry IP Scanner is a free open-source program that runs on Windows, Mac OS X and Linux. The scanner is capable of pinging IP addresses, resolving host names and scanning ports. The program's abilities can be extended through a variety of Java plug-ins, but they are only available for the Windows version of the program.
>>Free IP Scanner
The Free IP Scanner is a free program that works on all Windows computers. The program can display the host name, MAC address and work group as long as an IP address is supplied. The program can be run from a CD because it is a standalone application that does not require installation.
>> Advanced IP Scanner
The Advanced IP Scanner is a free program developed only for computers that use Windows. The program locates all of the computers on your local network, scans your network to find available resources and allows you to remotely wake and shut down computers.
>> Umit Tools
http://www.umitproject.org/?active=project