使用JDK中的 keytool【创建证书】・【查看】・【使用】
目录
■前言
1.创建证书
2.查看创建的证书内容
查看证书详细信息
查看证书指纹
3.使用
配置SpringBoot工程
application.properties
放置证书(.keystore)
可以使用的URL
访问效果
Chrome
IE
证书在IE中的显示
证书在Edge中显示
4.遇到的问题
端口被占用
浏览器不识别的SSL协议
IE 显示的情报
Google 显示的情报
查看浏览器协议支持
■其他01.消除证书中的警告
■其他02.使用CURL命令访问https的网站
curl的部分参数
===Windows
===Linux
■扩展01.JDK下,已经安装的证书查看
■扩展02.JDK添加证书的信任机构
■相关单词
■更多资料整理
■前言
HTTPS,在HTTP下加入SSL层
SSL(Secure Sockets Layer,安全套接层)
使用SSL首先需要一个证书
---
1.创建证书
keytool -genkey -alias myTomcat---
keytool -genkey -alias myTomcat -keypass tomcat -keyalg RSA -keysize 1024 -validity 365 -keystore C:\test\keystoreRSA\.keystore -storepass tomcat----
密码使用tomcat
---
---
2.查看创建的证书内容
---
查看证书详细信息
c:\test\keystoreRSA>keytool -list -v -keystore .keystore -storepass tomcat
密钥库类型: jks
密钥库提供方: SUN
您的密钥库包含 1 个条目
别名: mytomcat
创建日期: 2021-5-23
条目类型: PrivateKeyEntry
证书链长度: 1
证书[1]:
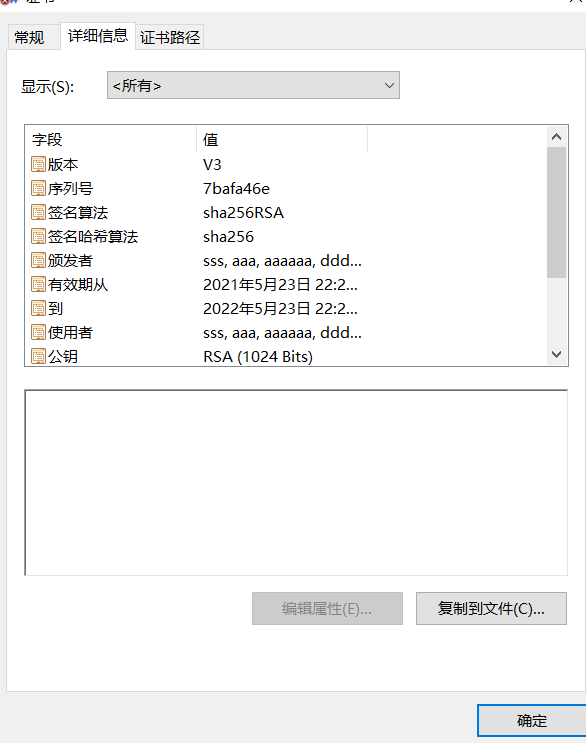
所有者: CN=sss, OU=aaa, O=aaaaaa, L=ddd, ST=dddddd, C=ccc
发布者: CN=sss, OU=aaa, O=aaaaaa, L=ddd, ST=dddddd, C=ccc
序列号: 7bafa46e
有效期为 Sun May 23 22:21:27 CST 2021 至 Mon May 23 22:21:27 CST 2022
证书指纹:
MD5: 9E:CF:A8:71:5B:ED:4C:EA:6F:69:9A:7B:9B:BF:82:40
SHA1: CE:B8:BD:B9:E7:71:0A:25:39:12:B1:3C:67:FF:F2:32:CC:05:07:7C
SHA256: C2:9E:A2:65:ED:64:42:C6:26:C9:71:D4:F1:C1:C3:76:C8:43:89:BE:C3:0B:85:03:70:62:4D:49:8F:7A:60:8F
签名算法名称: SHA256withRSA
主体公共密钥算法: 1024 位 RSA 密钥
版本: 3
扩展:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 9D D7 16 6A F7 3A 0C 02 AB C8 08 E6 E3 27 48 C0 ...j.:.......'H.
0010: 54 1C AA F4 T...
]
]
*******************************************
*******************************************
Warning:
JKS 密钥库使用专用格式。建议使用 "keytool -importkeystore -srckeystore .keystore -destkeystore .keystore -deststoretype pkcs12" 迁移到行 业标准格式 PKCS12。
c:\test\keystoreRSA>---
查看证书指纹
c:\test\keystoreRSA>keytool -list -keystore .keystore -storepass tomcat
密钥库类型: jks
密钥库提供方: SUN
您的密钥库包含 1 个条目
mytomcat, 2021-5-23, PrivateKeyEntry,
证书指纹 (SHA1): CE:B8:BD:B9:E7:71:0A:25:39:12:B1:3C:67:FF:F2:32:CC:05:07:7C
Warning:
JKS 密钥库使用专用格式。建议使用 "keytool -importkeystore -srckeystore .keystore -destkeystore .keystore -deststoretype pkcs12" 迁移到行 业标准格式 PKCS12。
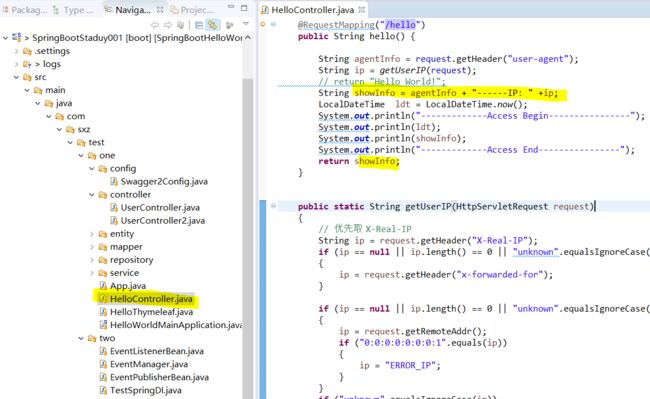
c:\test\keystoreRSA>3.使用
配置SpringBoot工程
SpringBoot之HelloWorld_sun0322的博客-CSDN博客_springboothelloword
application.properties
server.port=443
server.ssl.key-store: .keystore
server.ssl.key-store-password: tomcat
server.ssl.keyStoreType: JKS
server.ssl.keyAlias: myTomcat放置证书(.keystore)
启动log
. ____ _ __ _ _
/\\ / ___'_ __ _ _(_)_ __ __ _ \ \ \ \
( ( )\___ | '_ | '_| | '_ \/ _` | \ \ \ \
\\/ ___)| |_)| | | | | || (_| | ) ) ) )
' |____| .__|_| |_|_| |_\__, | / / / /
=========|_|==============|___/=/_/_/_/
:: Spring Boot :: (v2.1.6.RELEASE)
2021-05-23 22:34:25.101 INFO 11616 --- [ main] s.c.S.HelloWorldMainApplication : Starting HelloWorldMainApplication on PC_NAME with PID 11616 (C:\dev\SpringBootHelloWorld\target\classes started by login_UserName in C:\dev\SpringBootHelloWorld)
2021-05-23 22:34:25.105 INFO 11616 --- [ main] s.c.S.HelloWorldMainApplication : No active profile set, falling back to default profiles: default
2021-05-23 22:34:26.219 INFO 11616 --- [ main] o.s.b.w.embedded.tomcat.TomcatWebServer : Tomcat initialized with port(s): 443 (https)
2021-05-23 22:34:26.257 INFO 11616 --- [ main] o.apache.catalina.core.StandardService : Starting service [Tomcat]
2021-05-23 22:34:26.257 INFO 11616 --- [ main] org.apache.catalina.core.StandardEngine : Starting Servlet engine: [Apache Tomcat/9.0.21]
2021-05-23 22:34:26.350 INFO 11616 --- [ main] o.a.c.c.C.[Tomcat].[localhost].[/] : Initializing Spring embedded WebApplicationContext
2021-05-23 22:34:26.350 INFO 11616 --- [ main] o.s.web.context.ContextLoader : Root WebApplicationContext: initialization completed in 1208 ms
2021-05-23 22:34:26.525 INFO 11616 --- [ main] o.s.s.concurrent.ThreadPoolTaskExecutor : Initializing ExecutorService 'applicationTaskExecutor'
2021-05-23 22:34:26.608 INFO 11616 --- [ main] o.s.b.a.w.s.WelcomePageHandlerMapping : Adding welcome page: class path resource [static/index.html]
2021-05-23 22:34:27.069 INFO 11616 --- [ main] o.s.b.w.embedded.tomcat.TomcatWebServer : Tomcat started on port(s): 443 (https) with context path ''
2021-05-23 22:34:27.073 INFO 11616 --- [ main] s.c.S.HelloWorldMainApplication : Started HelloWorldMainApplication in 2.284 seconds (JVM running for 2.717)
2021-05-23 22:34:38.353 INFO 11616 --- [-nio-443-exec-7] o.a.c.c.C.[Tomcat].[localhost].[/] : Initializing Spring DispatcherServlet 'dispatcherServlet'
2021-05-23 22:34:38.353 INFO 11616 --- [-nio-443-exec-7] o.s.web.servlet.DispatcherServlet : Initializing Servlet 'dispatcherServlet'
2021-05-23 22:34:38.365 INFO 11616 --- [-nio-443-exec-7] o.s.web.servlet.DispatcherServlet : Completed initialization in 12 ms
可以使用的URL
---
https://localhost/---
https://localhost/index.html---
https://localhost/hello---
访问效果
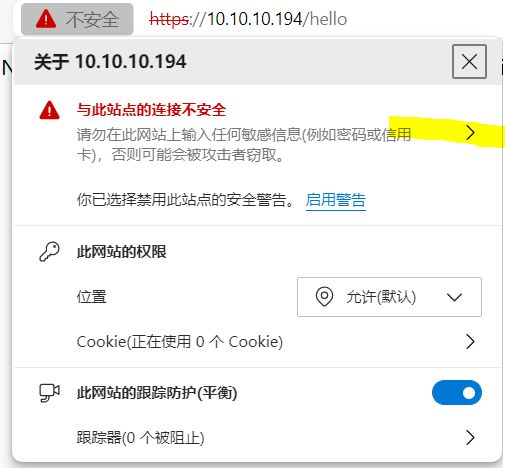
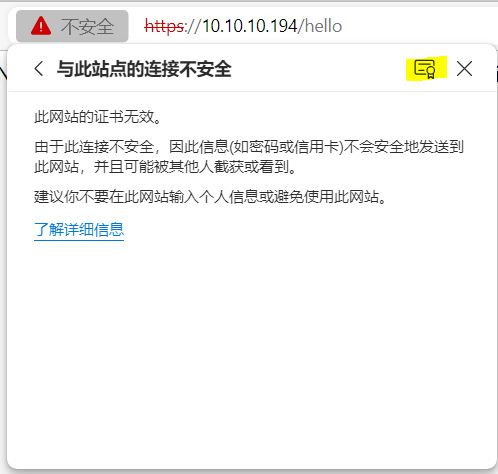
Chrome
IE
证书在IE中的显示
---
----
证书在Edge中显示
Step1
===安全时
===不安全时
===
Step2.点击上面黄色部分,再点击下面黄色部分
Step3.出现证书信息
==
==
4.遇到的问题
端口被占用
netstat -ano | find "443"
taskkill /pid 7572 /F浏览器不识别的SSL协议
---
IE 显示的情报
无法安全地连接到此页面
这可能是因为该站点使用过期的或不安全的 TLS 安全设置。如果这种情况持续发生,请与网站的所有者联系。
---
Google 显示的情报
localhost 使用了不受支持的协议。
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
---
查看浏览器协议支持
当前浏览器的SSL/TLS兼容性
---
参考解决1 NG
springboot https 报错ERR_SSL_VERSION_OR_CIPHER_MISMATCH_相交的直线的博客-CSDN博客
参考解决2 NG
SpringBoot配置ssl证书,访问提示ERR_SSL_VERSION_OR_CIPHER_MISMATCH_小净.的博客-CSDN博客
参考解决3 OK 生成证书时,指定更多信息
SpringBoot配置使用SSL,使用https(单向认证)_aiyo92的博客-CSDN博客
■其他01.消除证书中的警告
---
c:\>keytool -importkeystore -srckeystore c:\test\keystoreRSA\.keystore -destkeystore c:\test\keystoreRSA\.keystore -deststoretype pkcs12
输入源密钥库口令:
已成功导入别名 mytomcat 的条目。
已完成导入命令: 1 个条目成功导入, 0 个条目失败或取消
Warning:
已将 "c:\test\keystoreRSA\.keystore" 迁移到 Non JKS/JCEKS。将 JKS 密钥库作为 "c:\test\keystoreRSA\.keystore.old" 进行了备份。
c:\>---
---
c:\>cd c:\test\keystoreRSA
c:\test\keystoreRSA>keytool -list -v -keystore .keystore -storepass tomcat
密钥库类型: jks
密钥库提供方: SUN
您的密钥库包含 1 个条目
别名: mytomcat
创建日期: 2021-5-24
条目类型: PrivateKeyEntry
证书链长度: 1
证书[1]:
所有者: CN=sss, OU=aaa, O=aaaaaa, L=ddd, ST=dddddd, C=ccc
发布者: CN=sss, OU=aaa, O=aaaaaa, L=ddd, ST=dddddd, C=ccc
序列号: 7bafa46e
有效期为 Sun May 23 22:21:27 CST 2021 至 Mon May 23 22:21:27 CST 2022
证书指纹:
MD5: 9E:CF:A8:71:5B:ED:4C:EA:6F:69:9A:7B:9B:BF:82:40
SHA1: CE:B8:BD:B9:E7:71:0A:25:39:12:B1:3C:67:FF:F2:32:CC:05:07:7C
SHA256: C2:9E:A2:65:ED:64:42:C6:26:C9:71:D4:F1:C1:C3:76:C8:43:89:BE:C3:0B:85:03:70:62:4D:49:8F:7A:60:8F
签名算法名称: SHA256withRSA
主体公共密钥算法: 1024 位 RSA 密钥
版本: 3
扩展:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 9D D7 16 6A F7 3A 0C 02 AB C8 08 E6 E3 27 48 C0 ...j.:.......'H.
0010: 54 1C AA F4 T...
]
]
*******************************************
*******************************************
c:\test\keystoreRSA>---
c:\test\keystoreRSA>keytool -list -keystore .keystore -storepass tomcat
密钥库类型: jks
密钥库提供方: SUN
您的密钥库包含 1 个条目
mytomcat, 2021-5-24, PrivateKeyEntry,
证书指纹 (SHA1): CE:B8:BD:B9:E7:71:0A:25:39:12:B1:3C:67:FF:F2:32:CC:05:07:7C
c:\test\keystoreRSA>---
■其他02.使用CURL命令访问https的网站
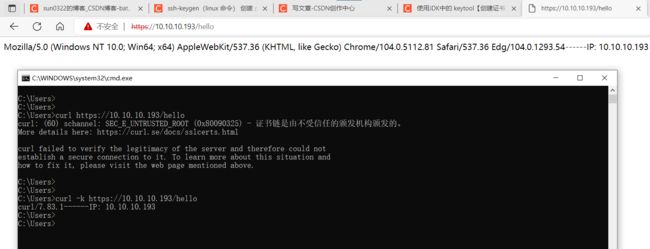
C:\Users>curl https://10.10.10.193/hello
curl: (60) schannel: SEC_E_UNTRUSTED_ROOT (0x80090325) - 证书链是由不受信任的颁发机构颁发的。
More details here: https://curl.se/docs/sslcerts.html
curl failed to verify the legitimacy of the server and therefore could not
establish a secure connection to it. To learn more about this situation and
how to fix it, please visit the web page mentioned above.curl的部分参数
===Windows
-k 忽略证明书检查
虽然帮助列表显示的命令里面,没有 -k,但是-k参数 在 windows 下面也好用
====代码
===Linux
-F
-F, --form
(HTTP SMTP IMAP) For HTTP protocol family, this lets curl emulate a filled-in form in which a user has pressed the submit
button. This causes curl to POST data using the Content-Type multipart/form-data according to RFC 2388.
For SMTP and IMAP protocols, this is the mean to compose a multipart mail message to transmit.
This enables uploading of binary files etc. To force the 'content' part to be a file, prefix the file name with an @
sign. To just get the content part from a file, prefix the file name with the symbol <. The difference between @ and < is
then that @ makes a file get attached in the post as a file upload, while the < makes a text field and just get the con乚
tents for that text field from a file.
Tell curl to read content from stdin instead of a file by using - as filename. This goes for both @ and < constructs.
When stdin is used, the contents is buffered in memory first by curl to determine its size and allow a possible resend.
Defining a part's data from a named non-regular file (such as a named pipe or similar) is unfortunately not subject to
buffering and will be effectively read at transmission time; since the full size is unknown before the transfer starts,
such data is sent as chunks by HTTP and rejected by IMAP.
Example: send an image to an HTTP server, where 'profile' is the name of the form-field to which the file portrait.jpg
will be the input:
curl -F [email protected] https://example.com/upload.cgi
Example: send a your name and shoe size in two text fields to the server:
curl -F name=John -F shoesize=11 https://example.com/
Example: send a your essay in a text field to the server. Send it as a plain text field, but get the contents for it from
a local file:
curl -F "story= -v
-v, --verbose
Makes curl verbose during the operation. Useful for debugging and seeing what's going on "under the hood". A line start乚
ing with '>' means "header data" sent by curl, '<' means "header data" received by curl that is hidden in normal cases,
and a line starting with '*' means additional info provided by curl.
If you only want HTTP headers in the output, -i, --include might be the option you're looking for.
If you think this option still doesn't give you enough details, consider using --trace or --trace-ascii instead.
Use -s, --silent to make curl really quiet.
See also -i, --include. This option overrides --trace and --trace-ascii.---
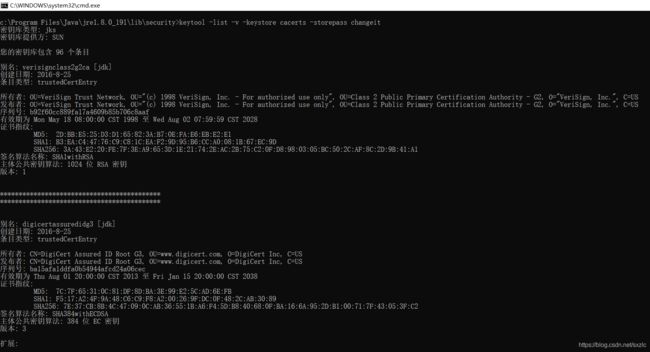
■扩展01.JDK下,已经安装的证书查看
1.cacerts文件没有被修改
cd c:\Program Files\Java\jre1.8.0_191\lib\security2.查看证书指纹
keytool -list -keystore cacerts -storepass changeit--
3.查看证书详细信息
keytool -list -v -keystore cacerts -storepass changeit ---
---
■扩展02.JDK添加证书的信任机构
加入JDK证书信任,C:\Program Files\Java\jre1.8.0_191\lib\security>目录下运行命令:
keytool -import -alias yourCacertName -keystore cacerts -file 盘:目录/证书文件.crt
keystore的默认密码“changeit”也可以写(密钥库文件:cacerts)全路径,这样就可以在任何目录下执行了
keytool -import -alias yourCacertName -keystore C:\Program Files\Java\jre1.8.0_191\lib\security\cacerts -file 盘:目录/证书文件.crt---
■相关单词
工作中使用到的单词(软件开发)_sun0322的博客-CSDN博客_https://10.59.142.4/integration
54.密钥库文件格式(.jks(Java Keystore) .ks .jce .p12 .pfx.....), 证书格式(.cer/.crt/.rsa .p7c/.p7m/.p7s .p12.....)
55.cacerts 是一个信任库。信任库用于验证对等方的身份。 // 是certified authority certificates 的缩写
56.certified 英 [ˈsɜːtɪˌfaɪd] adj. 被证明的,有保证的,具有证明文件的
57.authority 英 [ɔːˈθɒrɪtɪ] n. 权力;行政管理机构;当局;当权者;权威;权威人士
58. ( authorized [ˈɔːθəˌraɪzd] 权威认可的,经授权的 // 401 Unauthorized )
59.certificate 英 [səˈtɪfɪkɪt] n.文凭;执照;证明,证书
■更多资料整理
ssh-keygen(linux 命令) 创建 private key(私钥) , public key (公钥),实现ssh,scp,sftp命令无密码连接_sun0322的博客-CSDN博客
---