[SHCTF-校外赛道]61名
REVERSE
[WEEK1]ez_asm
enc = "nhuo[M`7mc7uhc$7midgbTf`7`$7%#ubf7 ci5Y"
for i in range(len(enc)):
print(chr((ord(enc[i]) + 0xa) ^ 0x1e), end='')
[WEEK1]easy_re
enc = [0x66, 0xC6, 0x16, 0x76, 0xB7, 0x45, 0x27, 0x97, 0xF5, 0x47,
0x03, 0xF5, 0x37, 0x03, 0xC6, 0x67, 0x33, 0xF5, 0x47, 0x86,
0x56, 0xF5, 0x26, 0x96, 0xE6, 0x16, 0x27, 0x97, 0xF5, 0x07,
0x27, 0x03, 0x26, 0xC6, 0x33, 0xD6, 0xD7, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00, 0x00,
0x00, 0x00, 0x00, 0x00]
for i in range(len(enc)):
temp = (bin(enc[i])[2:].zfill(8))
flag = temp[4:] + temp[:4]
print(chr(int(flag, 2)), end='')
[WEEK1]seed
#include[WEEK1]signin
import re
# 定义需要处理的汇编指令
s = """
mov [rbp+var_20], 66h ; 'f'
mov [rbp+var_1F], 6Ch ; 'l'
mov [rbp+var_1E], 61h ; 'a'
mov [rbp+var_1D], 67h ; 'g'
mov [rbp+var_1C], 7Bh ; '{'
mov [rbp+var_1B], 66h ; 'f'
mov [rbp+var_1A], 6Ch ; 'l'
mov [rbp+var_19], 61h ; 'a'
mov [rbp+var_18], 67h ; 'g'
mov [rbp+var_17], 31h ; '1'
mov [rbp+var_16], 73h ; 's'
mov [rbp+var_15], 69h ; 'i'
mov [rbp+var_14], 6Eh ; 'n'
mov [rbp+var_13], 61h ; 'a'
mov [rbp+var_12], 72h ; 'r'
mov [rbp+var_11], 72h ; 'r'
mov [rbp+var_10], 61h ; 'a'
mov [rbp+var_F], 79h ; 'y'
mov [rbp+var_E], 7Dh ; '}'
"""
# 使用正则表达式提取每行逗号和字符h之间的数据
pattern = r',\s*(\S+)h'
# 从字符串 s 中查找所有满足正则表达式模式 pattern 的匹配结果
# 并以列表形式返回这些匹配结果中的所有非重叠子字符串
data_list = re.findall(pattern, s)
print(data_list)
# 在每个列表元素前面加字符串0x
data_list = ['0x' + x for x in data_list]
print(data_list)
# int(j, 16) 将每个 '0x数字' 的字符串转化为整数
data_list = [int(j, 16) for j in data_list]
print(data_list)
print(''.join(chr(j) for j in data_list))
[WEEK1]easy_math
from z3 import *
l = [(Int("n[%d]" % i), 32) for i in range(6)]
s = Solver()
s.append(593 * l[0][0] + 997 * l[1][0] + 811 * l[2][0] + 258 * l[3][0] + 829 * l[4][0] + 532 * l[5][
0] == 0x5b8e0aef71d34ff43,
605 * l[0][0] + 686 * l[1][0] + 328 * l[2][0] + 602 * l[3][0] + 695 * l[4][0] + 576 * l[5][
0] == 0x551a262360964ef7f,
373 * l[0][0] + 512 * l[1][0] + 449 * l[2][0] + 756 * l[3][0] + 448 * l[4][0] + 580 * l[5][
0] == 0x49d158a5657d6931c,
560 * l[0][0] + 635 * l[1][0] + 422 * l[2][0] + 971 * l[3][0] + 855 * l[4][0] + 597 * l[5][
0] == 0x625568d5abbabf4f3,
717 * l[0][0] + 507 * l[1][0] + 388 * l[2][0] + 925 * l[3][0] + 324 * l[4][0] + 524 * l[5][
0] == 0x50ee0c025e70e3c23,
312 * l[0][0] + 368 * l[1][0] + 884 * l[2][0] + 518 * l[3][0] + 495 * l[4][0] + 414 * l[5][
0] == 0x40e735f8aa2815f65)
if s.check() == sat:
s = s.model()
print(s)
n = [0] * 6
n[2] = 13642136288051316
n[3] = 29378135513658469
n[5] = 30791965425607037
n[0] = 28829613228248624
n[4] = 32192963475959391
n[1] = 26827458353261422
s = []
for i in range(len(n)):
s.append(n[i].to_bytes(7, byteorder='big'))
print(b''.join(s))
[WEEK1]ez_apk
[WEEK2]pycode
import base64
flag = '*******************'
value = ''
output = ''
for i in range(1000):
w = 1024
x = w % 3
y = w // 9
z = x * y
w -= z
for i in range(10000):
w = 20
x = w % 6
y = w // 3
z = x * y
w += z
for i in range(1000):
w = 1024
x = w % 3
y = w // 9
z = x * y
w -= z
for i in range(10000):
w = 20
x = w % 6
y = w // 3
z = x * y
w += z
for i in range(len(flag)):
temp = ord(flag[i]) ^ 8
value += chr(temp)
for i in range(len(value)):
temp = ord(value[i]) + 3
output += chr(temp)
obfuscated_output = base64.b64encode(output.encode()).decode()[:-1]
obfuscated_output = obfuscated_output.replace("0", "t").replace("c", "4").replace("+", "-")
print(obfuscated_output)
EXP
import base64
enc = '==AeAF3M-tzO-giQ-AUQosDQ9tGK7MDPuhC47tDNB5Tb8Yn4sdW4'.replace('-', '+').replace('4', 'c').replace('t', '0')
enc = base64.b64decode(enc.encode()[::-1]).decode()
print(enc)
for i in range(len(enc)):
print(chr((ord(enc[i]) - 3) ^ 8), end='')
[WEEK2]Authur’s_box
动调,输入42位数,修改跳转,得到key
enc = [0xA8, 0xD4, 0x55, 0xAD, 0x89, 0xFA, 0xDE, 0x97, 0xCF, 0xBC,
0xE4, 0x5B, 0x48, 0xB9, 0x95, 0x13, 0x55, 0xFB, 0x93, 0xBD,
0x55, 0x96, 0x88, 0x4F, 0x34, 0x25, 0x8F, 0x8A, 0x95, 0x3C,
0x9E, 0xB5, 0x7E, 0x05, 0x92, 0x49, 0x88, 0xAC, 0x26, 0xD6,
0xB9, 0x93, ]
key = [0xCE, 0xB8, 0x34, 0xCA, 0xF2, 0xC2, 0xEB, 0xA2, 0xF9, 0xD8,
0xD3, 0x38, 0x71, 0x94, 0xF7, 0x23, 0x33, 0x9F, 0xBE, 0x89,
0x33, 0xF3, 0xB9, 0x62, 0x56, 0x14, 0xBF, 0xE9, 0xB8, 0x0C,
0xA7, 0x83, 0x48, 0x35, 0xF4, 0x2B, 0xBF, 0x99, 0x16, 0xB2,
0x8C, 0xEE, ]
print(len(enc))
for i in range(len(enc)):
print(chr(enc[i] ^ key[i]), end='')
[WEEK2]not gcc
import hashlib
import sudokum
map = [4,
0,
7,
0,
0,
3,
2,
0,
8,
5,
0,
0,
0,
2,
0,
9,
0,
0,
0,
1,
2,
9,
8,
0,
0,
0,
4,
7,
0,
9,
1,
0,
4,
8,
0,
0,
0,
6,
1,
0,
0,
0,
4,
7,
0,
0,
0,
3,
2,
7,
0,
0,
0,
6,
0,
8,
6,
3,
0,
0,
0,
4,
0,
0,
2,
0,
7,
4,
0,
6,
3,
0,
3,
0,
4,
0,
0,
2,
0,
0,
0]
puzzle = []
for i in range(9):
tmp = []
for j in range(9):
tmp.append(map[i * 9 + j])
puzzle.append(tmp)
solution = sudokum.solve(puzzle)[1]
dec = []
for i in solution:
for j in i:
dec.append(j)
flag = ''
for i in range(len(dec)):
if map[i] == dec[i]:
flag += '0'
else:
flag += str(dec[i])
print(hashlib.md5(flag.encode()).hexdigest())
[WEEK2]Run?润!
动调,将每层的迷宫打出来,然后跑脚本
1
[0, 1, 0, 0, 0, 0, 0, 0],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 0, 0, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
2
[1, 1, 1, 0, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
3
[1, 1, 1, 0, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 0, 0, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
4
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 0, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
5
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[0, 0, 0, 0, 0, 0, 0, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
6
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[0, 0, 0, 0, 0, 0, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
7
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 0, 0],
[1, 1, 1, 1, 1, 0, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
8
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 0, 0, 0],
EXP
from queue import Queue
def bfs(map, start, end):
# 1. 初始化队列
q = Queue()
q.put((start, ""))
# 2. 开始搜索
while not q.empty():
cur, path = q.get()
# 3. 判断是否到达终点
if cur == end:
return path
# 4. 判断是否越界或者是墙壁
if cur[0] < 0 or cur[0] >= len(map) or cur[1] < 0 or cur[1] >= len(map[0]) or map[cur[0]][cur[1]] == 1:
continue
# 5. 标记为已经走过
map[cur[0]][cur[1]] = 1
# 6. 向6个方向扩展
q.put(((cur[0] - 1, cur[1]), path + "w"))
q.put(((cur[0] + 1, cur[1]), path + "s"))
q.put(((cur[0], cur[1] - 1), path + "a"))
q.put(((cur[0], cur[1] + 1), path + "d"))
q.put(((cur[0] + 8, cur[1]), path + "u"))
q.put(((cur[0] - 8, cur[1]), path + "q"))
# 7. 没有找到路径
return None
map = [[0, 1, 0, 0, 0, 0, 0, 0],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 0, 0, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 0, 0, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 0, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 0, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[0, 0, 0, 0, 0, 0, 0, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[0, 0, 0, 0, 0, 0, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 1],
[0, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 0, 0],
[1, 1, 1, 1, 1, 0, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 0],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 1, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 0, 1, 1],
[1, 1, 1, 1, 1, 0, 0, 0]]
puzzle = [0] * 64 * 8
print("路径:", bfs(map, (0, 0), (63, 7)))
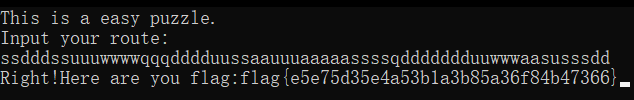
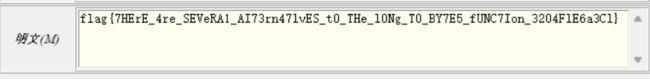
[WEEK2]签到题?
动调到ArgList未与input运算前
![[SHCTF-校外赛道]61名_第2张图片](http://img.e-com-net.com/image/info8/b75d9c63798941d4985473babf29fb5d.jpg)
提取其中的数据,有点misc的味道了
![[SHCTF-校外赛道]61名_第3张图片](http://img.e-com-net.com/image/info8/b3252e84a72d4123b2e0e82e90604d68.jpg)
EXP
import base64
enc = [0x5A, 0x6D, 0x78, 0x68, 0x5A,
0x33, 0x74, 0x68, 0x4D, 0x54,
0x42, 0x6C, 0x4E, 0x32, 0x4E,
0x6A, 0x59, 0x79, 0x31, 0x69,
0x4F, 0x44, 0x41, 0x79, 0x4C,
0x57, 0x55, 0x7A, 0x5A, 0x57,
0x49, 0x74, 0x59, 0x7A, 0x67,
0x31, 0x4F, 0x57, 0x45, 0x33,
0x4C, 0x54, 0x4D, 0x77, 0x4F,
0x54, 0x51, 0x77, 0x5A, 0x54,
0x49, 0x79, 0x4E, 0x6D, 0x52,
0x39]
tmp = ''.join(chr(i) for i in enc)
flag = base64.b64decode(tmp)
print(flag)
[WEEK3]ststst
SMC题,可以动调解密,或者自己写个idc脚本
上网找个tea解密脚本:
#include[WEEK3]java是最棒的语言吗
将Java代码copy下来,在下面两处修改一下,将密文和密钥输出
![[SHCTF-校外赛道]61名_第4张图片](http://img.e-com-net.com/image/info8/3b11782556e34ea5a066c5f14b4a30fe.jpg)
![[SHCTF-校外赛道]61名_第5张图片](http://img.e-com-net.com/image/info8/63febbeb2cb942db8735604083fbb1e5.jpg)
流程如下:
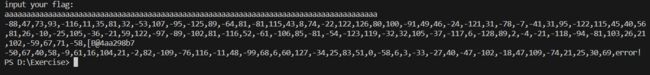
EXP:
key = [-50, 67, 40, 58, -9, 61, 16, 104, 21, -2, 82, -109, -76, 116, -11, 48, -99, 68, 6, 60, 127, -34, 25, 83, 51, 0,
-58, 6, 3, -33, -27, 40, -47, -102, -18, 47, 109, -74, 21, 25, 30, 69, ]
enc = [-88, 47, 73, 93, -116, 11, 35, 81, 32, -53, 107, -95, -125, 89, -64, 81, -81, 115, 43, 8, 74, -22, 122, 126, 80,
100, -91, 49, 46, -24, -121, 31, -78, -7, -41, 31, 95, -122, 115, 45, 40, 56, 81, 26, -10, -25, 105, -36, -21,
59, 122, -97, -89, -102, 81, -116, 52, -61, -106, 85, -81, -54, -123, 119, -32, 32, 105, -37, -117, 6, -128, 89,
2, -4, -21, -118, -94, -81, 103, 26, 21, 102, -59, 67, 71, -58]
for i in range(len(key)):
tmp = key[i] ^ enc[i]
if tmp < 0:
print(chr(-tmp), end='')
else:
print(chr(tmp), end='')
[WEEK3]crackme
# z3 can't solve problems like x%100==1(these mod value equation)
from z3 import *
s = Solver()
secret = [54, 57, 566, 532, 1014, 1, 7, 508, 10, 12, 498, 494, 6, 24, 14, 20, 489, 492, 0, 10, 490, 498, 517, 539, 21,
528, 517, 530, 543, 9, 13, 0, 4, 51, 562, 518, 14, 527, 520, 0, 517, 57, 575, 512, 1, 572, 515, 60, 18, 31, 1,
594, 117, 15]
l = len(secret)
flag = [BitVec('%d' % i, 12) for i in range(l)]
code = flag[:]
for i in range(52):
code[i] = code[i + 1] ^ code[i + 2]
code[52] = code[53] ^ code[0]
code[53] = code[0] ^ code[1]
for i in range(l):
s.add(secret[i] == code[i])
def crack(a, b):
for x in range(1, 128):
if ((x + b) % 333 + 444) % 555 - 1 == a:
return x
return ord('f')
if s.check() == sat:
m = s.model()
print(''.join([chr(crack(m[flag[i]], i + 1)) for i in range(l)]))
[WEEK3]easyre
爆破一下
import base64
import dis
import marshal
import sympy as sp
encoded_data = b'#`VVVVVVVVVVVVVVVVVVVVVSVVVVFVVVV_YZVVVVMVU|VNFV@pU|V{xUMVYvVzBSMVDSVFRVMFDSV\\VQMV@\x7fVAxPMFU{V@BPp`]vU%B_MF]eVy]VMFY|UxZUVFUbTPBSMVrSVFRVMV\x7fCVT|]N`^VVVVVVVVVVVVVVVpVVVVPVVVVF`VVV_GFVVVVsVU\'V@FUp`PSVO\'TMV].V$FUMVPSVBFVOC".U_`SqV]/UU|VQ`U/V_`RsV]/V^ZUQpVMVUtVMVR@V_\'SqV]/Vo|VqV]/UU|VVpU/Vy`RGVU/Vy`SGVUoPPFTUVU.U_\'SsVXSV_\'QqVQRVQ&pqFM/UPFSQ`U|VENVqFE/V$`TqVFMVUtVMVR@V_\'SqV]/Vo|VqV]/UU|VVpU/Vy`RGVU/Vy`SGVU/Vy`TqVFMV_`TqVZMVUtVMVR@VU|VqFs/UvVRqVM/U\'RVxFRUV_QfqVACVT|RCb|VVFVV!FVVVVSgVFVVVT|Q%pEdvOY\'%pAnN@"yMsxSuPAb%p{~rOE{NO]nNOyvUzQ`tPAbMT|^%pYeMO{vTOUdN@{bsPA#sYxUB.xUvcxUvAx\\N%{`vPAnsPA#sYxRN%\x7f\x7ftcxUv!|Vtp/VVVS!UzM&u~"`rsx[tzZ\'O%AbN$]"t_FUVVVVto`VVVVVVF`UUV^ZVDVU_V^^VFNTTVRZVEVUPpRNVEVTt\x7fRVVVUmT`VVVPA#N@&`uPAqv%A"tnxVVVSN{U!ez%M\'!&&VP ez!UZmA.\'X"g^\'/NUcvXd.TPRTTD!&UB\\`dT.R}Q{!QQUdr~UguyU&sTU"u$An^PMdN@t!rpA&sPNcXQxSr@Am@p]bu\'#gT_^EVVVVtp|VVVUvU@YxM@Ye%pA`tz{bsYxQv@"`sOCvUzAbN%.|MsxRMzo\x7fM&x]M@"}ty{`sPA|tp/VVVUnS`VVV_^GVVVVt\x7fVVVVSvTSocu%E&uPB
# xor_key = int(input('Plz input key (0
def fff(xor_key):
x = sp.symbols('x')
f = x ** 2 + x + 1
integral_value = sp.integrate(f, (x, 1, xor_key))
check_value = 13024
if integral_value * 3 == check_value:
xor_decoded_data = bytes([byte ^ xor_key for byte in encoded_data])
decoded_data = base64.b64decode(xor_decoded_data)
code_obj = marshal.loads(decoded_data)
dis.dis(code_obj)
print(xor_key)
exec(code_obj)
else:
print('Wrong!!')
for i in range(100):
fff(i)
炸出key=23,字节码:
1 0 LOAD_CONST 0 ()
2 LOAD_CONST 1 ('rc4_encrypt')
4 MAKE_FUNCTION 0
6 STORE_NAME 0 (rc4_encrypt)
21 8 LOAD_CONST 2 (b'example_key')
10 STORE_NAME 1 (key)
22 12 LOAD_CONST 3 (b'\xd8\x94\x1e\xab\x9bft\xeb]@\x1b\xba\xe6\xe8\x133W\xdd\x0e\xe6\x924\xf1\x80mh\xeb=\x08a\x02\t.\xb5\x05B\xb0\xb0/D\x8cY')
14 STORE_NAME 2 (check)
24 16 LOAD_NAME 3 (print)
18 LOAD_CONST 4 ('Plz input your flag:')
20 CALL_FUNCTION 1
22 POP_TOP
25 24 LOAD_NAME 4 (input)
26 CALL_FUNCTION 0
28 LOAD_METHOD 5 (encode)
30 LOAD_CONST 5 ('utf-8')
32 CALL_METHOD 1
34 STORE_NAME 6 (flag)
27 36 LOAD_NAME 0 (rc4_encrypt)
38 LOAD_NAME 1 (key)
40 LOAD_NAME 6 (flag)
42 CALL_FUNCTION 2
44 STORE_NAME 7 (encrypted)
29 46 LOAD_NAME 7 (encrypted)
48 LOAD_NAME 2 (check)
50 COMPARE_OP 2 (==)
52 POP_JUMP_IF_FALSE 64
30 54 LOAD_NAME 3 (print)
56 LOAD_CONST 6 ('yes')
58 CALL_FUNCTION 1
60 POP_TOP
62 JUMP_FORWARD 8 (to 72)
32 >> 64 LOAD_NAME 3 (print)
66 LOAD_CONST 7 ('no')
68 CALL_FUNCTION 1
70 POP_TOP
>> 72 LOAD_CONST 8 (None)
74 RETURN_VALUE
Disassembly of :
2 0 LOAD_GLOBAL 0 (list)
2 LOAD_GLOBAL 1 (range)
4 LOAD_CONST 1 (256)
6 CALL_FUNCTION 1
8 CALL_FUNCTION 1
10 STORE_FAST 2 (S)
3 12 LOAD_CONST 2 (0)
14 STORE_FAST 3 (j)
5 16 LOAD_GLOBAL 1 (range)
18 LOAD_CONST 1 (256)
20 CALL_FUNCTION 1
22 GET_ITER
>> 24 FOR_ITER 62 (to 88)
26 STORE_FAST 4 (i)
6 28 LOAD_FAST 3 (j)
30 LOAD_FAST 2 (S)
32 LOAD_FAST 4 (i)
34 BINARY_SUBSCR
36 BINARY_ADD
38 LOAD_FAST 0 (key)
40 LOAD_FAST 4 (i)
42 LOAD_GLOBAL 2 (len)
44 LOAD_FAST 0 (key)
46 CALL_FUNCTION 1
48 BINARY_MODULO
50 BINARY_SUBSCR
52 BINARY_ADD
54 LOAD_CONST 1 (256)
56 BINARY_MODULO
58 STORE_FAST 3 (j)
7 60 LOAD_FAST 2 (S)
62 LOAD_FAST 3 (j)
64 BINARY_SUBSCR
66 LOAD_FAST 2 (S)
68 LOAD_FAST 4 (i)
70 BINARY_SUBSCR
72 ROT_TWO
74 LOAD_FAST 2 (S)
76 LOAD_FAST 4 (i)
78 STORE_SUBSCR
80 LOAD_FAST 2 (S)
82 LOAD_FAST 3 (j)
84 STORE_SUBSCR
86 JUMP_ABSOLUTE 24
9 >> 88 LOAD_CONST 2 (0)
90 DUP_TOP
92 STORE_FAST 4 (i)
94 STORE_FAST 3 (j)
10 96 LOAD_GLOBAL 3 (bytearray)
98 CALL_FUNCTION 0
100 STORE_FAST 5 (ciphertext)
12 102 LOAD_FAST 1 (plaintext)
104 GET_ITER
>> 106 FOR_ITER 96 (to 204)
108 STORE_FAST 6 (char)
13 110 LOAD_FAST 4 (i)
112 LOAD_CONST 3 (1)
114 BINARY_ADD
116 LOAD_CONST 1 (256)
118 BINARY_MODULO
120 STORE_FAST 4 (i)
14 122 LOAD_FAST 3 (j)
124 LOAD_FAST 2 (S)
126 LOAD_FAST 4 (i)
128 BINARY_SUBSCR
130 BINARY_ADD
132 LOAD_CONST 1 (256)
134 BINARY_MODULO
136 STORE_FAST 3 (j)
15 138 LOAD_FAST 2 (S)
140 LOAD_FAST 3 (j)
142 BINARY_SUBSCR
144 LOAD_FAST 2 (S)
146 LOAD_FAST 4 (i)
148 BINARY_SUBSCR
150 ROT_TWO
152 LOAD_FAST 2 (S)
154 LOAD_FAST 4 (i)
156 STORE_SUBSCR
158 LOAD_FAST 2 (S)
160 LOAD_FAST 3 (j)
162 STORE_SUBSCR
16 164 LOAD_FAST 2 (S)
166 LOAD_FAST 2 (S)
168 LOAD_FAST 4 (i)
170 BINARY_SUBSCR
172 LOAD_FAST 2 (S)
174 LOAD_FAST 3 (j)
176 BINARY_SUBSCR
178 BINARY_ADD
180 LOAD_CONST 1 (256)
182 BINARY_MODULO
184 BINARY_SUBSCR
186 STORE_FAST 7 (k)
17 188 LOAD_FAST 5 (ciphertext)
190 LOAD_METHOD 4 (append)
192 LOAD_FAST 6 (char)
194 LOAD_FAST 7 (k)
196 BINARY_XOR
198 CALL_METHOD 1
200 POP_TOP
202 JUMP_ABSOLUTE 106
19 >> 204 LOAD_FAST 5 (ciphertext)
206 RETURN_VALUE
很明显的rc4,写个解密脚本:
from Crypto.Cipher import ARC4
key = b'example_key'
key = ARC4.new(key)
en_flag = b'\xd8\x94\x1e\xab\x9bft\xeb]@\x1b\xba\xe6\xe8\x133W\xdd\x0e\xe6\x924\xf1\x80mh\xeb=\x08a\x02\t.\xb5\x05B\xb0\xb0/D\x8cY'
flag = key.decrypt(en_flag)
print(flag)
[WEEK3]喵?喵。喵!
通过观察汇编,得知这是一个AES+base64组合加密
重点在于AES的key和iv
![[SHCTF-校外赛道]61名_第6张图片](http://img.e-com-net.com/image/info8/31868add106a418d90fbfd44f5d1be88.jpg)
接下来就是动调,判断切片的情况。
在存放输入数据的内存处打个断点,进行AES加密时会断下。
![[SHCTF-校外赛道]61名_第7张图片](http://img.e-com-net.com/image/info8/04f6b2df1d4f429bb9615d4a9838880f.jpg)
当内存变化时,可以得到key的切片
![[SHCTF-校外赛道]61名_第8张图片](http://img.e-com-net.com/image/info8/082032a05cc641bdab91cde9ba1f315f.png)
![[SHCTF-校外赛道]61名_第9张图片](http://img.e-com-net.com/image/info8/524027a727204d38883b15311aee30db.png)
EXP:
import base64
from Crypto.Cipher import AES
enc = "GMPZ5Eaw27Hyx241S0WsqXYHCyahcUyjlooFoLE1aLII8Gq/gXTu3Tplx3BOqZ3xt0yBeimgxH0uOq/OjqkMQrjKg6snFhLpMgrSTrG0mpo="
enc = base64.b64decode(enc.encode())
print(enc)
s = b"SHCTF_2023_S0_e4sy_m1ao"
key = s[7:]
print(key)
iv = s[:16]
print(iv)
aes = AES.new(key, AES.MODE_CBC, iv)
den_text = aes.decrypt(enc)
print("明文:", den_text)
Crypto
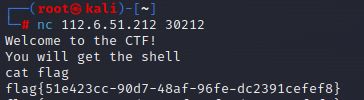
[WEEK1]really_ez_rsa
[WEEK1]what is m
[WEEK1]难言的遗憾
[WEEK1]进制
[WEEK1]okk
[WEEK1]Crypto_Checkin
[WEEK1]凯撒大帝
[WEEK1]残缺的md5
import hashlib
import itertools
def md5_encrypt(text):
md5 = hashlib.md5()
md5.update(text.encode('utf-8'))
return md5.hexdigest().upper()
# 要加密的文本
text_1 = "KCLWG"
text_2 = "K8M9O3"
text_3 = "DE"
text_4 = "84S9"
table_1 = 'abcdefghijklmnopqrstuvwxyz0123456789/'
table_2 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ_{}'
for flag in itertools.product(table_2 + table_1, repeat=3):
flag = text_1 + flag[0] + text_2 + flag[1] + text_3 + flag[2] + text_4
if md5_encrypt(flag)[:4] == "F0AF":
print(md5_encrypt(flag))
![[SHCTF-校外赛道]61名_第1张图片](http://img.e-com-net.com/image/info8/7cbb85c99a3a4e018d85aa6c75cf0fd5.jpg)
![[SHCTF-校外赛道]61名_第10张图片](http://img.e-com-net.com/image/info8/cb89ed62d2fb4d2fb74f69ebb06fa126.jpg)
![[SHCTF-校外赛道]61名_第11张图片](http://img.e-com-net.com/image/info8/ef5c26462b79457c8c658aed379153e4.jpg)
![[SHCTF-校外赛道]61名_第12张图片](http://img.e-com-net.com/image/info8/2ccfe2453bc94fcc81dda772535ccb0e.jpg)
![[SHCTF-校外赛道]61名_第13张图片](http://img.e-com-net.com/image/info8/e7e2e74e94274d1d8224667b0980f9d2.jpg)
![[SHCTF-校外赛道]61名_第14张图片](http://img.e-com-net.com/image/info8/1f53215252ba476d9a2f1a6cf65e6688.jpg)
![[SHCTF-校外赛道]61名_第15张图片](http://img.e-com-net.com/image/info8/08c48c080d1d457999e207a838517aba.jpg)
![[SHCTF-校外赛道]61名_第16张图片](http://img.e-com-net.com/image/info8/abb57edaf202463d870fd2bb3b526dd2.jpg)
![[SHCTF-校外赛道]61名_第17张图片](http://img.e-com-net.com/image/info8/ac2babaa9bf74b20b23f7415ba95f788.jpg)
![[SHCTF-校外赛道]61名_第18张图片](http://img.e-com-net.com/image/info8/ba0f466b27344817a59d30ea3c89caf2.jpg)
![[SHCTF-校外赛道]61名_第19张图片](http://img.e-com-net.com/image/info8/95dc3754d5a943c9ad8aa11d9456181b.jpg)
![[SHCTF-校外赛道]61名_第20张图片](http://img.e-com-net.com/image/info8/6c6355e6868f4723a7460ca42c40b5fb.jpg)
![[SHCTF-校外赛道]61名_第21张图片](http://img.e-com-net.com/image/info8/7c647693fcfc454caaf81f3c69627852.jpg)
![[SHCTF-校外赛道]61名_第22张图片](http://img.e-com-net.com/image/info8/06e529ae3be842dc99ead28712420479.jpg)