apache中ssl配置的那些事
最近负责完成一个内部系统的证书认证,关于ssl本身的配置其实并不难,主要是有很多细节的地方需要注意一下,ssl原理就不再赘述了,查询相关资料即可,主要讲一下ssl在apache中的相关配置以及企业应用中的一些注意事项。
设置证书认证流程为:(CA生成;服务器证书签发;WEB SERVER(APACHE)配置;客户端证书创建;吊销列表生成测试)
1、准备证书相关文件
[root@localhost CA]# wget http://www.openssl.org/contrib/ssl.ca-0.1.tar.gz
[root@localhost CA]# tar -zxf ssl.ca-0.1.tar.gz
[root@localhost CA]# cd ssl.ca-0.1
1.1)生成根证书
[root@localhost ssl.ca-0.1]# ./new-root-ca.sh
No Root CA key round. Generating one
Generating RSA private key, 1024 bit long modulus
........++++++
.........++++++
e is 65537 (0x10001)
Enter pass phrase for ca.key: //输入密码
Verifying - Enter pass phrase for ca.key: //确认密码
Self-sign the root CA... //签署根证书
Enter pass phrase for ca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
----- //信息输入
Country Name (2 letter code) [MY]:CN
State or Province Name (full name) [Perak]:zhejiang
Locality Name (eg, city) [Sitiawan]:hangzhou
Organization Name (eg, company) [My Directory Sdn Bhd]:ccssl
Organizational Unit Name (eg, section) [Certification Services Division]:ccdw
Common Name (eg, MD Root CA) []:intranet
Email Address []:summersun_ym@126.com
[root@localhost ssl.ca-0.1]#
1.2) 服务器生成证书
[root@localhost ssl.ca-0.1]# ./new-server-cert.sh server //证书名称
No server.key round. Generating one
Generating RSA private key, 1024 bit long modulus
...................................................++++++
....++++++
e is 65537 (0x10001)
Fill in certificate data
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
----- //输入相关信息
Country Name (2 letter code) [MY]:CN
State or Province Name (full name) [Perak]:zhejiang
Locality Name (eg, city) [Sitiawan]:hangzhou
Organization Name (eg, company) [My Directory Sdn Bhd]:ccssl
Organizational Unit Name (eg, section) [Secure Web Server]:ccdw
Common Name (eg, www.domain.com) []:localhost //服务器的ip或者域名
Email Address []:summersun_ym@126.com
You may now run ./sign-server-cert.sh to get it signed
[root@localhost ssl.ca-0.1]#
1.3)签发服务器证书
[root@localhost ssl.ca-0.1]# ./sign-server-cert.sh server //为server服务器签发证书
CA signing: server.csr -> server.crt:
Using configuration from ca.config
Enter pass phrase for ./ca.key: //输入之前设置的密码
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName:PRINTABLE:'CN'
stateOrProvinceName:PRINTABLE:'zhejiang'
localityName:PRINTABLE:'hangzhou'
organizationName:PRINTABLE:'ccssl'
organizationalUnitName:PRINTABLE:'ccdw'
commonName:PRINTABLE:'localhost'
emailAddress:IA5STRING:'summersun_ym@126.com'
Certificate is to be certified until Aug 12 05:49:48 2011 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
CA verifying: server.crt <-> CA cert
server.crt: OK
[root@localhost ssl.ca-0.1]#
2、WEB SERVER(APACHE)配置
设置以下选项,启用SSL连接,同时客户端访问需要提供有效证书。相关值具体路径根据实际情况进行调整:
修改/usr/local/apache2/conf/httpd.conf,启动httpd-ssl.conf选项
# Secure (SSL/TLS) connections
#Include conf/extra/httpd-ssl.conf
修改/usr/local/apache2/conf/extra/httpd-ssl.conf ,启动SSL相关选项
# Certificate Authority (CA):
#SSLCACertificatePath "/usr/local/apache2/conf"
SSLCACertificateFile "/usr/local/apache2/conf/ca.crt"
# Server Certificate:
SSLCertificateFile "/usr/local/apache2/conf/server.crt"
# Server Private Key:
SSLCertificateKeyFile "/usr/local/apache2/conf/server.key"
# Client Authentication (Type): //客户端认证类型
SSLVerifyClient optional
SSLVerifyDepth 10
将证书按照APACHE配置文件设置放置到指定目录;
[root@localhost ssl.ca-0.1]# cp server.crt server.key ca.crt /usr/local/apache2/conf/
3、生成客户端证书测试
[root@localhost ssl.ca-0.1]# ./new-user-cert.sh client //创建客户端证书
No client.key round. Generating one
Generating RSA private key, 1024 bit long modulus
................................++++++
..++++++
e is 65537 (0x10001)
Fill in certificate data
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg, John Doe) []:CN
Email Address []:summersun_ym@126.com
You may now run ./sign-user-cert.sh to get it signed
[root@localhost ssl.ca-0.1]# ll
[root@localhost ssl.ca-0.1]# ./sign-user-cert.sh client //签发客户端证书
CA signing: client.csr -> client.crt:
Using configuration from ca.config
Enter pass phrase for ./ca.key: //输入密码
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName RINTABLE:'CN'
RINTABLE:'CN'
emailAddress :IA5STRING:'summersun_ym@126.com'
Certificate is to be certified until Aug 12 07:13:06 2011 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
CA verifying: client.crt <-> CA cert
client.crt: OK
[root@localhost ssl.ca-0.1]#
将客户端证书转换为pkcs12格式,用于客户端安装使用:
[root@localhost ssl.ca-0.1]# openssl pkcs12 -export -clcerts -in client.crt -inkey client.key -out client.pfx
Enter Export Password: //该密码为客户端安装时会用到
Verifying - Enter Export Password:
[root@localhost ssl.ca-0.1]#
客户端直接双击该cc.pfx,会提示证书安装向导。将其导入,直接IE访问 https://localhost/ 时,会提示客户端证书
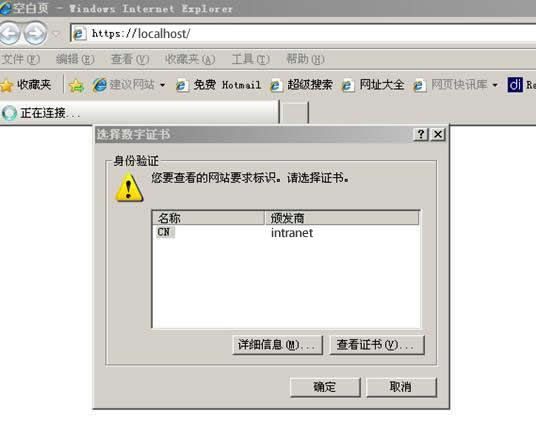
设置证书认证流程为:(CA生成;服务器证书签发;WEB SERVER(APACHE)配置;客户端证书创建;吊销列表生成测试)
1、准备证书相关文件
[root@localhost CA]# wget http://www.openssl.org/contrib/ssl.ca-0.1.tar.gz
[root@localhost CA]# tar -zxf ssl.ca-0.1.tar.gz
[root@localhost CA]# cd ssl.ca-0.1
1.1)生成根证书
[root@localhost ssl.ca-0.1]# ./new-root-ca.sh
No Root CA key round. Generating one
Generating RSA private key, 1024 bit long modulus
........++++++
.........++++++
e is 65537 (0x10001)
Enter pass phrase for ca.key: //输入密码
Verifying - Enter pass phrase for ca.key: //确认密码
Self-sign the root CA... //签署根证书
Enter pass phrase for ca.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
----- //信息输入
Country Name (2 letter code) [MY]:CN
State or Province Name (full name) [Perak]:zhejiang
Locality Name (eg, city) [Sitiawan]:hangzhou
Organization Name (eg, company) [My Directory Sdn Bhd]:ccssl
Organizational Unit Name (eg, section) [Certification Services Division]:ccdw
Common Name (eg, MD Root CA) []:intranet
Email Address []:summersun_ym@126.com
[root@localhost ssl.ca-0.1]#
1.2) 服务器生成证书
[root@localhost ssl.ca-0.1]# ./new-server-cert.sh server //证书名称
No server.key round. Generating one
Generating RSA private key, 1024 bit long modulus
...................................................++++++
....++++++
e is 65537 (0x10001)
Fill in certificate data
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
----- //输入相关信息
Country Name (2 letter code) [MY]:CN
State or Province Name (full name) [Perak]:zhejiang
Locality Name (eg, city) [Sitiawan]:hangzhou
Organization Name (eg, company) [My Directory Sdn Bhd]:ccssl
Organizational Unit Name (eg, section) [Secure Web Server]:ccdw
Common Name (eg, www.domain.com) []:localhost //服务器的ip或者域名
Email Address []:summersun_ym@126.com
You may now run ./sign-server-cert.sh to get it signed
[root@localhost ssl.ca-0.1]#
1.3)签发服务器证书
[root@localhost ssl.ca-0.1]# ./sign-server-cert.sh server //为server服务器签发证书
CA signing: server.csr -> server.crt:
Using configuration from ca.config
Enter pass phrase for ./ca.key: //输入之前设置的密码
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName:PRINTABLE:'CN'
stateOrProvinceName:PRINTABLE:'zhejiang'
localityName:PRINTABLE:'hangzhou'
organizationName:PRINTABLE:'ccssl'
organizationalUnitName:PRINTABLE:'ccdw'
commonName:PRINTABLE:'localhost'
emailAddress:IA5STRING:'summersun_ym@126.com'
Certificate is to be certified until Aug 12 05:49:48 2011 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
CA verifying: server.crt <-> CA cert
server.crt: OK
[root@localhost ssl.ca-0.1]#
2、WEB SERVER(APACHE)配置
设置以下选项,启用SSL连接,同时客户端访问需要提供有效证书。相关值具体路径根据实际情况进行调整:
修改/usr/local/apache2/conf/httpd.conf,启动httpd-ssl.conf选项
# Secure (SSL/TLS) connections
#Include conf/extra/httpd-ssl.conf
修改/usr/local/apache2/conf/extra/httpd-ssl.conf ,启动SSL相关选项
# Certificate Authority (CA):
#SSLCACertificatePath "/usr/local/apache2/conf"
SSLCACertificateFile "/usr/local/apache2/conf/ca.crt"
# Server Certificate:
SSLCertificateFile "/usr/local/apache2/conf/server.crt"
# Server Private Key:
SSLCertificateKeyFile "/usr/local/apache2/conf/server.key"
# Client Authentication (Type): //客户端认证类型
SSLVerifyClient optional
SSLVerifyDepth 10
将证书按照APACHE配置文件设置放置到指定目录;
[root@localhost ssl.ca-0.1]# cp server.crt server.key ca.crt /usr/local/apache2/conf/
3、生成客户端证书测试
[root@localhost ssl.ca-0.1]# ./new-user-cert.sh client //创建客户端证书
No client.key round. Generating one
Generating RSA private key, 1024 bit long modulus
................................++++++
..++++++
e is 65537 (0x10001)
Fill in certificate data
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Common Name (eg, John Doe) []:CN
Email Address []:summersun_ym@126.com
You may now run ./sign-user-cert.sh to get it signed
[root@localhost ssl.ca-0.1]# ll
[root@localhost ssl.ca-0.1]# ./sign-user-cert.sh client //签发客户端证书
CA signing: client.csr -> client.crt:
Using configuration from ca.config
Enter pass phrase for ./ca.key: //输入密码
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
commonName
emailAddress :IA5STRING:'summersun_ym@126.com'
Certificate is to be certified until Aug 12 07:13:06 2011 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
CA verifying: client.crt <-> CA cert
client.crt: OK
[root@localhost ssl.ca-0.1]#
将客户端证书转换为pkcs12格式,用于客户端安装使用:
[root@localhost ssl.ca-0.1]# openssl pkcs12 -export -clcerts -in client.crt -inkey client.key -out client.pfx
Enter Export Password: //该密码为客户端安装时会用到
Verifying - Enter Export Password:
[root@localhost ssl.ca-0.1]#
客户端直接双击该cc.pfx,会提示证书安装向导。将其导入,直接IE访问 https://localhost/ 时,会提示客户端证书
