Android签名apk
Android requires that all apps be digitally signed with a certificate before they can be installed. Android uses this certificate to identify the author of an app, and the certificate does not need to be signed by a certificate authority. Android apps often use self-signed certificates. The app developer holds the certificate's private key.
Signing Overview
You can sign an app in debug or release mode. You sign your app in debug mode during development and in release mode when you are ready to distribute your app. The Android SDK generates a certificate to sign apps in debug mode. To sign apps in release mode, you need to generate your own certificate.
Signing in Debug Mode
In debug mode, you sign your app with a debug certificate generated by the Android SDK tools. This certificate has a private key with a known password, so you can run and debug your app without typing the password every time you make a change to your project.
Android Studio and the ADT plugin for Eclipse sign your app in debug mode automatically when you run or debug your project from the IDE.
You can run and debug an app signed in debug mode on the emulator and on devices connected to your development manchine through USB, but you cannot distribute an app signed in debug mode.
For more information about how to build and run apps in debug mode, see Building and Running.
Signing in Release Mode
In release mode, you sign your app with your own certificate:
- Create a keystore. A keystore is a binary file that contains a set of private keys. You must keep your keystore in a safe and secure place.
- Create a private key. A private key represents the entity to be identified with the app, such as a person or a company.
- Build your project. Generate an unsigned APK for your app.
- Sign your app. Use your private key to generate a signed version of your APK.
After you complete this process, you can distribute your app and publish it on Google Play.
Warning: Keep your keystore and private key in a safe and secure place, and ensure that you have secure backups of them. If you publish an app to Google Play and then lose the key with which you signed your app, you will not be able to publish any updates to your app, since you must always sign all versions of your app with the same key.
The rest of this document provides detailed instructions about how to generate a private key and sign your apps in release mode with Android Studio and with the ADT plugin for Eclipse.
Signing Android Wear Apps
When publishing Android Wear apps, you package the wearable app inside of a handheld app, because users cannot browse and install apps directly on the wearable. Both apps must be signed. For more information on packaging and signing Android Wear apps, see Packaging Wearable Apps.
Signing Your App in Android Studio
To sign your app in release mode in Android Studio, follow these steps:
- On the menu bar, click Build > Generate Signed APK.
-
On the Generate Signed APK Wizard window, click Create new to create a new keystore.
If you already have a keystore, go to step 4.
-
On the New Key Store window, provide the required information as shown in figure 1.
Your key should be valid for at least 25 years, so you can sign app updates with the same key through the lifespan of your app.

Figure 1. Create a new keystore in Android Studio.
-
On the Generate Signed APK Wizard window, select a keystore, a private key, and enter the passwords for both. Then click Next.
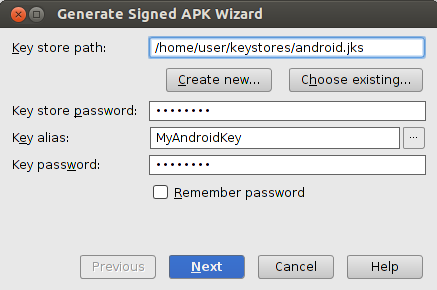
Figure 2. Select a private key in Android Studio.
-
On the next window, select a destination for the signed APK and click Finish.

Figure 3. Generate a signed APK in Android Studio.
Automatically Signing Your App
In Android Studio, you can configure your project to sign your release APK automatically during the build process:
- On the project browser, right click on your app and select Open Module Settings.
- On the Project Structure window, select your app's module under Modules.
- Click on the Signing tab.
-
Select your keystore file, enter a name for this signing configuration (as you may create more than one), and enter the required information.
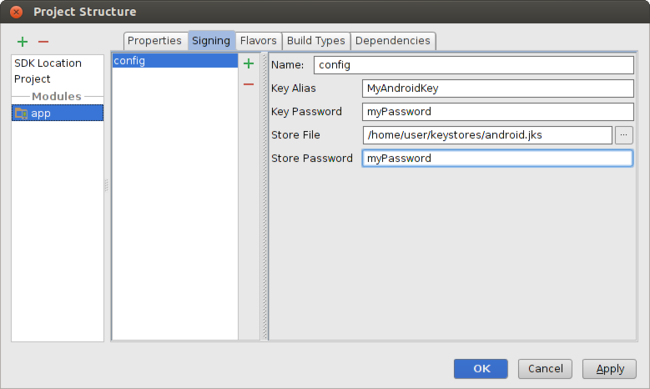
Figure 4. Create a signing configuration in Android Studio.
- Click on the Build Types tab.
- Select the release build.
-
Under Signing Config, select the signing configuration you just created.

Figure 5. Select a signing configuration in Android Studio.
- Click OK.
You can also specify your signing settings in Gradle configuration files. For more information, see Signing settings.
Signing Your App with the ADT Plugin for Eclipse
To sign your app in release mode in ADT, follow these steps:
- Select the project in the Package Explorer and select File > Export.
- On the Export window, select Export Android Application and click Next.
- On the Export Android Application window, select the project you want to sign and click Next.
-
On the next window, enter the location to create a keystore and a keystore password. If you already have a keystore, select Use existing keystore, enter your keystore's location and password, and go to step 6.
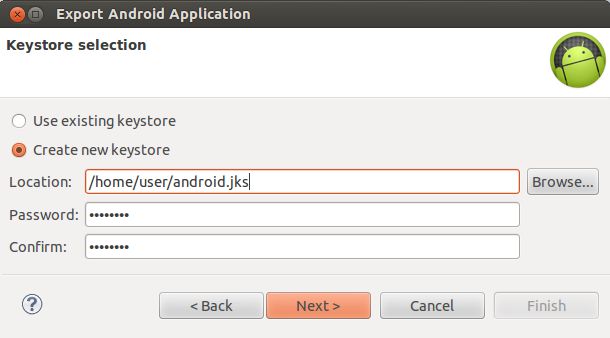
Figure 6. Select a keystore in ADT.
-
On the next window, provide the required information as shown in figure 5.
Your key should be valid for at least 25 years, so you can sign app updates with the same key through the lifespan of your app.

Figure 7. Create a private key in ADT.
-
On the next window, select the location to export the signed APK.

Figure 8. Export the signed APK in ADT.
Signing Considerations
You should sign all of your apps with the same certificate throughout the expected lifespan of your applications. There are several reasons why you should do so:
- App upgrade: When the system is installing an update to an app, it compares the certificate(s) in the new version with those in the existing version. The system allows the update if the certificates match. If you sign the new version with a different certificate, you must assign a different package name to the application—in this case, the user installs the new version as a completely new application.
- App modularity: Android allows apps signed by the same certificate to run in the same process, if the applications so requests, so that the system treats them as a single application. In this way you can deploy your app in modules, and users can update each of the modules independently.
- Code/data sharing through permissions: Android provides signature-based permissions enforcement, so that an app can expose functionality to another app that is signed with a specified certificate. By signing multiple apps with the same certificate and using signature-based permissions checks, your apps can share code and data in a secure manner.
If you plan to support upgrades for an app, ensure that your key has a validity period that exceeds the expected lifespan of that app. A validity period of 25 years or more is recommended. When your key's validity period expires, users will no longer be able to seamlessly upgrade to new versions of your application.
If you plan to publish your apps on Google Play, the key you use to sign these apps must have a validity period ending after 22 October 2033. Google Play enforces this requirement to ensure that users can seamlessly upgrade apps when new versions are available.
Securing Your Private Key
Maintaining the security of your private key is of critical importance, both to you and to the user. If you allow someone to use your key, or if you leave your keystore and passwords in an unsecured location such that a third-party could find and use them, your authoring identity and the trust of the user are compromised.
If a third party should manage to take your key without your knowledge or permission, that person could sign and distribute apps that maliciously replace your authentic apps or corrupt them. Such a person could also sign and distribute apps under your identity that attack other apps or the system itself, or corrupt or steal user data.
Your private key is required for signing all future versions of your app. If you lose or misplace your key, you will not be able to publish updates to your existing appn. You cannot regenerate a previously generated key.
Your reputation as a developer entity depends on your securing your private key properly, at all times, until the key is expired. Here are some tips for keeping your key secure:
- Select strong passwords for the keystore and key.
- Do not give or lend anyone your private key, and do not let unauthorized persons know your keystore and key passwords.
- Keep the keystore file containing your private key in a safe, secure place.
In general, if you follow common-sense precautions when generating, using, and storing your key, it will remain secure.
Expiry of the Debug Certificate
The self-signed certificate used to sign your application in debug mode has an expiration date of 365 days from its creation date. When the certificate expires, you will get a build error.
To fix this problem, simply delete the debug.keystore file. The default storage location is in ~/.android/ on OS X and Linux, in C:\Documents and Settings\<user>\.android\ on Windows XP, and in C:\Users\<user>\.android\ on Windows Vista and Windows 7.
The next time you build, the build tools will regenerate a new keystore and debug key.
Note that, if your development machine is using a non-Gregorian locale, the build tools may erroneously generate an already-expired debug certificate, so that you get an error when trying to compile your application. For workaround information, see the troubleshooting topic I can't compile my app because the build tools generated an expired debug certificate.
Signing Your App Manually
You do not need Android Studio or the ADT plugin for Eclipse to sign your app. You can sign your app from the command line using standard tools from the Android SDK and the JDK. To sign an app in release mode from the command line:
-
Generate a private key using keytool. For example:
$ keytool -genkey -v -keystore my-release-key.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
This example prompts you for passwords for the keystore and key, and to provide the Distinguished Name fields for your key. It then generates the keystore as a file called my-release-key.keystore. The keystore contains a single key, valid for 10000 days. The alias is a name that you will use later when signing your app.
-
Compile your app in release mode to obtain an unsigned APK.
-
Sign your app with your private key using jarsigner:
$ jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore my-release-key.keystore my_application.apk alias_name
This example prompts you for passwords for the keystore and key. It then modifies the APK in-place to sign it. Note that you can sign an APK multiple times with different keys.
-
Verify that your APK is signed. For example:
$ jarsigner -verify -verbose -certs my_application.apk
-
Align the final APK package using zipalign.
$ zipalign -v 4 your_project_name-unaligned.apk your_project_name.apk
zipalign ensures that all uncompressed data starts with a particular byte alignment relative to the start of the file, which reduces the amount of RAM consumed by an app.