RHEL5.4 postfix 邮件系统的安装
第一篇 邮件系统简介
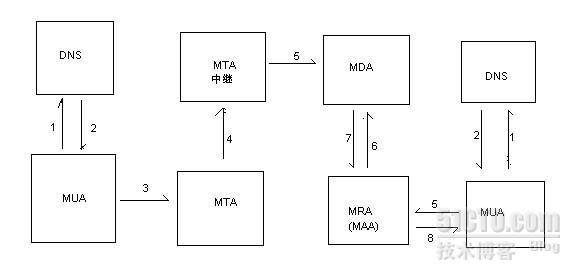
1 MUA :是Mial User Agent 的简称 ,是邮件系统的客户端程序,它提供了阅读,发送和接受电子邮件的用户接口,如:linux中的Mail ,Windowns中的Foxmail,Outlook 等
2 MSA :是Mail Submmission Agent的简称。是邮件提交代理,负责消息有MTA发送之前必须完成所有准备工作和错误检测,MSA是在MUA和MTA之间插入了一个头脑清醒的检测员,对所有的主机名,从MUA 得到的头信息等信息进行检测
3 MTA:是Mail Transfer Agent 的简称,邮件转发代理,负责邮件的存储和转发;监视用户的代理请求,根据电子邮件的目标地址找出对应的电子邮件服务器,并将信件在服务器之间传输并且将接受到的邮件进行缓冲。Linux 下有sendmail .Postfix,qmail 等
4 MDA :是Mail Ddlivery Agent 的简称。邮件投递代理,从MTA接受邮件并进行适当的本地投递,可以投递一个本地用户,一个邮件列表,一个文件或者是一个程序
5 MAA :是Mail Access Agent。邮件访问代理,用于将用户连接到系统邮件库,使用POP或者Imap协议收取邮件。Linux 下常用的MAA有,Cyrus-IMAP,COURIER-IMAP等邮件中继,当邮件的目的传输是一旦源地址和目的地址都不是本地系统,那么本地系统就是邮件中继站(即是中转站)
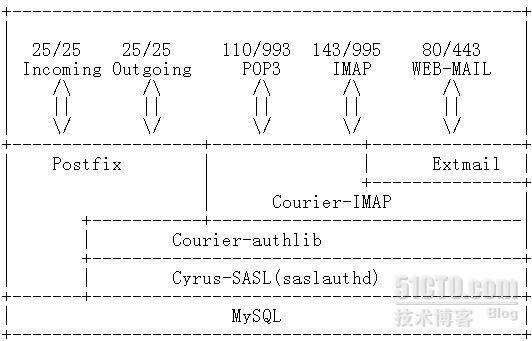
第二篇 Postfix 的安装
1 添加mysql用户
#groupadd mysql
#useradd –g mysql –s /bin/false –M mysql
#tar xvf mysql-5.5.4-m3.tar.gz
#cd mysql-5.5.4-m3
# ./configure
#/usr/local/mysql/bin/mysqladmin –uroot –p “Oldpassword” password “newpassword”
#echo “/usr/local/mysql/lib/mysql” >>/etc/ld.so.conf
注:一定要执行ldconfig –v 不然当前不会去指定的mysql的库文件中查找mysql的库文件
PATH=$PATH:/usr/local/mysql/bin
2 删除系统中的openssl 文件
# mv /usr/bin/openssl /usr/bin/openssl.OFF
# mv /usr/include/openssl /usr/include/openssl.OFF
# rm /usr/lib/libssl.so
# ln -sv /usr/local/ssl/bin/openssl /usr/bin/openssl
# ln -sv /usr/local/ssl/include/openssl /usr/include/openssl
#ln –sv /usr/local/ssl/lib/libssl.so.1.0.0 /usr/lib/libssl.so
1 安装cyrus-sasl
# ./configure --prefix=/usr/local/sasl2 (注意使用续行符)
--disable-gssapi
--disable-anon
--disable-sample
--disable-digest
--enable-plain
--enable-login
--enable-sql
--with-mysql=/usr/local/mysql
--with-mysql-includes=/usr/local/mysql/include/mysql --with-mysql-libs=/usr/local/mysql/lib/mysql --with-authdaemond=/usr/local/courier-authlib/var/spool/authdaemon/socket
#make
2 关闭系统自带的sasl
#mv /usr/lib/libsasl2.a /usr/lib/libsasl2.a.OFF
#mv /usr/lib/libsasl2.so.2.0.22 /usr/lib/libsasl2.so.2.0.22.OFF
3 重新创建新编译的sasl 库文件
Postfix2.3 以后的版本会分别在/usr/local/lib 和/usr/local/include 中搜索sasl的库文件及其头文件,因此需要将其连接至此
#ln –sv /usr/local/sasl2/lib/* /usr/local/lib
#ln –sv /usr/local/sasl2/include/sasl/* /usr/local/include
4 创建运行时需要的目录并调试启动
# mkdir -pv /var/state/saslauthd
# /usr/local/sasl2/sbin/saslauthd -a shadow pam -d
5 启动并测试
#/usr/local/sasl2/sbin/testsaslauthd –u root –p root用户密码
6 添加配之文件搜索路径
#echo “/usr/local/sasl2/lib" >> /etc/ld.so.conf
# echo "/usr/local/sasl2/lib/sasl2" >> /etc/ld.so.conf
# ldconfig –v 注:一定要执行该命令,否则不会生效,除非是重启系统
7 添加开机自动启动
#echo “/usr/local/sasl2/sbin/saslauthd -a shadow pam ” >>/etc/rc.local
# ln -sv /usr/local/BerkeleyDB/include /usr/include/db4
# ln -sv /usr/local/BerkeleyDB/include/db.h /usr/include/db.h
# ln -sv /usr/local/BerkeleyDB/include/db_cxx.h /usr/include/db_cxx.h
#./configure
--prefix=/usr/local/apache
--enable-so
--enable-ssl
--with-ssl=/usr/local/ssl
--enable-track-vars
--enable-rewrite
--with-zlib
--enable-mods-shared=most
--enable-suexec (后面extmail切换”运行时用户”时要用到)
--with-suexec-caller=daemon
#./configure --prefix=/usr/local/php
--with-apxs2=/usr/local/apache/bin/apxs
--with-mysql=/usr/local/mysql
-with-mysqli=/usr/local/mysql/bin/mysql_config
--with-libxml-dir
--with-png-dir
--with-jpeg-dir
--with-zlib
--with-freetype -dir
--with-gd-dir
--enable-mbstring=all
#cp php.ini-dist /usr/local/php/lib/php.ini
#cd /usr/local/apache/conf
AddType application/x-httpd-php .php
AddType application/x-httpd-php-source .phps
#vim Test.php
8 将网站根目录指定到/var/www:
找到DocumentRoot “/usr/local/apache/htdocs”
修改为:DocumentRoot “/var/www”(后文中我们还会注释掉此行,以启用虚拟主机)
找到<Directory “/usr/local/apache/htdocs”>
修改为:<Directory “/var/www”>
1 创建postfix 和postdrop 用户
#useradd –g postdrop –u 2526 –s /bin/false –M postdrop
2 安装postfix-2.7.1
#cd postfix-2.7.1
#make makefiles 'CCARGS=-DHAS_MYSQL -I/usr/local/mysql/include/mysql -DUSE_SASL_AUTH -DUSE_CYRUS_SASL -I/usr/local/sasl2/include/sasl -I/usr/local/BerkeleyDB/include -DUSE_TLS -I/usr/local/ssl/include/openssl ' 'AUXLIBS=-L/usr/local/mysql/lib/mysql -lmysqlclient -lz -lm -L/usr/local/sasl2/lib -lsasl2 -L/usr/local/BerkeleyDB/lib -L/usr/local/ssl/lib -lssl -lcrypto'
3 生成别名二进制文件,此步能够提高postfix的效率,如果不生成二进制文 件。Postfix 的效率比较低下
4 配置postfix,并启动,测试postfix 并进行发言
#cd /etc/postfix/
mydestination = $myhostname, localhost.$mydomain, localhost, $mydomain
说明:
myorigin参数用来指明发件人所在的域名;
mydestination参数指定postfix接收邮件时收件人的域名,即您的postfix系统要接收到哪个域名的邮件;
myhostname 参数指定运行postfix邮件系统的主机的主机名,默认情况下,其值被设定为本地机器名;
mydomain参数指定您的域名,默认情况下,postfix将myhostname的第一部分删除而作为mydomain的值;
mynetworks 参数指定你所在的网络的网络地址,postfix系统根据其值来区别用户是远程的还是本地的,如果是本地网络用户则允许其访问;
inet_interfaces 参数指定postfix系统监听的网络接口;
当然在上面的myorigin=frank.net 同时也可以用$mydomain 来代替frank.net
5 启动postfix
6 连接postfix,并验证postfix是否正常启动
# telnet localhost 25
Trying 127.0.0.1...
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 mail.frank.net ESMTP Postfix
ehlo mail.frank.net
250-mail.frank.net
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
mail from:[email protected]
250 2.1.0 Ok
rcpt to:[email protected]
250 2.1.5 Ok
data
354 End data with <CR><LF>.<CR><LF>
subject:test!
test!!!
. 250 2.0.0 Ok: queued as AB94A1A561
quit
221 2.0.0 Bye
Connection closed by foreign host.
7 切换到redhat,查看是否收到email 切换到redhat用户进行收信:
# su - redhat
$ mail
Mail version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/redhat": 1 message 1 new
>N 1 [email protected] Wed Sep 8 22:40 16/566 "test!"
&
第九 为postfix 开启基于cyrus-sasl 的认证
#/usr/local/postfix/sbin/postconf –a
cyrus
############################CYRUS-SASL############################
broken_sasl_auth_clients = yes
smtpd_recipient_restrictions=permit_mynetworks,permit_sasl_authenticated,reject_invalid_hostname,reject_non_fqdn_hostname,reject_unknown_sender_domain,reject_non_fqdn_sender,reject_non_fqdn_recipient,reject_unknown_recipient_domain,reject_unauth_pipelining,reject_unauth_destination
smtpd_sasl_auth_enable = yes
smtpd_sasl_local_domain = $myhostname
smtpd_sasl_security_options = noanonymous
smtpd_sasl_application_name = smtpd
smtpd_banner = Welcome to our $myhostname ESMTP,Warning: Version not Available!
#cd /usr/local/lib/sasl2/
pwcheck_method: saslauthd
mech_list: PLAIN LOGIN
#/usr/local/postfix/sbin/postfix reload
#telnet localhost 25
Trying 127.0.0.1...
Connected to localhost.localdomain (127.0.0.1).
220 Welcome to our mail.frank.net ESMTP,Warning:Version not Available!
第十 ;配置postfix 支持虚拟域和虚拟用户
#################Virtual Mailbox Settings ######################
virtual_mailbox_base = /var/spool/mail
virtual_mailbox_maps = mysql:/etc/postfix/mysql_virtual_mailbox_maps.cf
virtual_mailbox_domains = mysql:/etc/postfix/mysql_virtual_domains_maps.cf
virtual_alias_domains =
virtual_alias_maps = mysql:/etc/postfix/mysql_virtual_alias_maps.cf
virtual_uid_maps = static:2525
virtual_gid_maps = static:2525
virtual_transport = virtual
maildrop_destination_recipient_limit = 1
maildrop_destination_concurrency_limit = 1
######################QUOTA Settings########################
message_size_limit = 14336000
virtual_mailbox_limit = 20971520
virtual_create_maildirsize = yes
virtual_mailbox_extended = yes
virtual_mailbox_limit_maps = mysql:/etc/postfix/mysql_virtual_mailbox_limit_maps.cf
virtual_mailbox_limit_override = yes
virtual_maildir_limit_message = Sorry, the user's maildir has overdrawn his diskspace quota, please Tidy your mailbox and try again later.
virtual_overquota_bounce = yes
创建/etc/postfix/mysql_virtual_alias_maps.cf ,添加如下内容:
user = extmail
password = extmail
hosts = localhost
dbname = extmail
table = alias
select_field = goto
where_field = address
创建/etc/postfix/mysql_virtual_domains_maps.cf ,添加如下内容:
user = extmail
password = extmail
hosts = localhost
dbname = extmail
table = domain
select_field = description
where_field = domain
创建/etc/postfix/mysql_virtual_mailbox_limit_maps.cf ,添加如下内容:
user = extmail
password = extmail
hosts = localhost
dbname = extmail
table = mailbox
select_field = quota
where_field = username
创建/etc/postfix/mysql_virtual_mailbox_maps.cf ,添加如下内容:
user = extmail
password = extmail
hosts = localhost
dbname = extmail
table = mailbox
select_field = maildir
where_field = username
#tar xvf courier-authlib-0.63.0.tar.bz2
#./configure
--prefix=/usr/local/courier-authlib
--sysconfdir=/etc
--without-authpam
-without-authldap
--without-authpwd
--without-authshadow
--without-authvchkpw
--without-authpgsql
--with-authmysql
--with-mysql-libs=/usr/local/mysql/lib/mysql
--with-mysql-includes=/usr/local/mysql/inculde/mysql
--with-redhat
--with-authmysqlrc=/etc/authmysqlrc
--with-authdaemonrc=/etc/authdaemonrc
CFLAGS="-march=i686 -O2 -fexpensive-optimizations"
CXXFLAGS="-march=i686 -O2 -fexpensive-optimizations"
# make
# make install
#cp /etc/authmysqlrc.dist /etc/authmysqlrc
authmodulelist="authmysql"
authmodulelistorig="authmysql"
daemons=10
MYSQL_PORT 3306 ( 指定你的 mysql 监听的端口,这里使用默认的 3306)
MYSQL_USERNAME extmail ( 这时为后文要用的数据库的所有者的用户名 )
MYSQL_PASSWORD extmail ( 密码 )
MYSQL_SOCKET /tmp/mysql.sock
MYSQL_DATABASE extmail
MYSQL_USER_TABLE mailbox
MYSQL_CRYPT_PWFIELD password
MYSQL_UID_FIELD '2525'
MYSQL_GID_FIELD '2525'
MYSQL_LOGIN_FIELD username
MYSQL_HOME_FIELD concat('/var/spool/mail/',maildir)
MYSQL_NAME_FIELD name
MYSQL_MAILDIR_FIELD concat('/var/spool/mail/',maildir)
#cp courier-authlib.sysvinit /etc/rc.d/init.d/courier-authlib
# chmod 755 /etc/rc.d/init.d/courier-authlib
# chkconfig --add courier-authlib
# chkconfig courier-authlib on
第十二安装courier-IMAP
#./configure
--prefix=/usr/local/courier-imap
--with-redhat
--enable-unicode
--disable-root-check
--with-trashquota
--without-ipv6
CPPFLAGS='-I/usr/local/ssl/include/openssl -I/usr/local/courier-authlib/include'
LDFLAGS='-L/usr/local/courier-authlib/lib/courier-authlib'
COURIERAUTHCONFIG='/usr/local/courier-authlib/bin/courierauthconfig'
# make
# make install
#cp imap.dist imapd
#vim /usr/local/courier-imap/etc/pop3d
vim /usr/local/courier-imap/etc/imapd
6 配置SMTP 认证,同样需要修改在前面创建的/usr/local/sasl2/smtpd.conf
pwcheck_method: authdaemond
log_level: 3
mech_list:PLAIN LOGIN
authdaemond_path:/usr/local/courier-authlib/var/spool/authdaemon/socket
1 安装extmail
#mv extmail-1.2 /var/www/extsuite/extamail
#cd /var/www/exstusite/extmail
2 修改主配置文件
SYS_MESSAGE_SIZE_LIMIT = 5242880
用户可以发送的最大邮件
SYS_USER_LANG = en_US
语言选项,可改作:
SYS_USER_LANG = zh_CN
SYS_MAILDIR_BASE = /home/domains
此处即为您在前文所设置的用户邮件的存放目录,可改作:
SYS_MAILDIR_BASE = /var/mail
SYS_MYSQL_USER = db_user
SYS_MYSQL_PASS = db_pass
以上两句句用来设置连接数据库服务器所使用用户名、密码和邮件服务器用到的数据库,这里修改为:
SYS_MYSQL_USER = extmail
SYS_MYSQL_PASS = extmail
SYS_MYSQL_HOST = localhost
指明数据库服务器主机名,这里默认即可
SYS_MYSQL_SOCKET = /var/lib/mysql/mysql.sock
连接数据库的sock文件位置,这里修改为:
SYS_MYSQL_SOCKET = /tmp/mysql.sock
SYS_MYSQL_TABLE = mailbox
SYS_MYSQL_ATTR_USERNAME = username
SYS_MYSQL_ATTR_DOMAIN = domain
SYS_MYSQL_ATTR_PASSWD = password
以上用来指定验正用户登录里所用到的表,以及用户名、域名和用户密码分别对应的表中列的名称;这里默认即可
SYS_AUTHLIB_SOCKET = /var/spool/authdaemon/socket
此句用来指明authdaemo socket文件的位置,这里修改为:
SYS_AUTHLIB_SOCKET = /usr/local/courier-authlib/var/spool/authdaemon/socket
3 修改apache的配置
由于extmail要进行本地邮件的投递操作,故必须将运行apache服务器用户的身份修改为您的邮件投递代理的用户;本例中打开了apache服务器的suexec功能,故使用以下方法来实现虚拟主机运行身份的指定。此例中的MDA为postfix自带,因此将指定为postfix用户:
<VirtualHost *:80>
ServerName mail.frank.net
DocumentRoot /var/www/extsuite/extmail/html/
ScriptAlias /extmail/cgi /var/www/extsuite/extmail/cgi
Alias /extmail /var/www/extsuite/extmail/html
SuexecUserGroup postfix postfix
</VirtualHost>
修改 cgi执行文件属主为apache运行身份用户:
# chown -R postfix.postfix /var/www/extsuite/extmail/cgi/
如果您没有打开apache服务器的suexec功能,也可以使用以下方法解决:
# vi /etc/httpd/httpd.conf
User postfix
Group postfix
<VirtualHost *:80>
ServerName mail.frank.net
DocumentRoot /var/www/extsuite/extmail/html/
ScriptAlias /extmail/cgi /var/www/extsuite/extmail/cgi
Alias /extmail /var/www/extsuite/extmail/html
</VirtualHost>
4 安装 Unix-Syslog ,因为extmail 会用到DBD:syslog 当然在安装其之前必须确认perl 环软件包是否安装
# make
5 安装DBD-mysql
#make
6 测试webmail
2 修改配置文件以符合本例的需要:
# vi /var/www/extsuite/extman/webman.cf
SYS_MAILDIR_BASE = /home/domains
此处即为您在前文所设置的用户邮件的存放目录,可改作:
SYS_MAILDIR_BASE = /var/spool/mail
SYS_MYSQL_SOCKET = /var/lib/mysql/mysql.sock
此处修改为:
SYS_MYSQL_SOCKET = /tmp/mysql.sock
mysql> grant all privileges on extmain.* TO webman@localhost IDENTIFIED BY 'webman';
mysql> grant all privileges on extmain.* TO [email protected] IDENTIFIED BY 'webman';
#perl Makefile.PL
SYS_MYSQL_USER = postfix
SYS_MYSQL_PASS = 123456
connect('database=extmail;host=localhost;mysql_socket=/tmp/mysql.sock','postfix',...) failed: Access denied for user 'postfix'@'localhost' (using password: YES) at
/var/www/extsuite/extmail/libs/Ext/Auth/MySQL.pm line 45
Can't chdir to /var/mailbox/frank.net/frank/Maildir/, No such file or
此处即为您在前文所设置的用户邮件的存放目录
SYS_MAILDIR_BASE = /var/www/mail
此处即为您在前文所设置的用户邮件的存放目录,可改作:
SYS_MAILDIR_BASE = /var/mail
或者设置成
SYS_MAILDIR_BASE = /var/spool/mail
Can't open /tmp/extman//sid_26da75f9aec35f2cbc6b4fa425ab525e, No such file or directory.
# sys_sess_dir, the session dir
SYS_SESS_DIR = /tmp/extman/
Chown -R postfix.postfix /var/tmp/extman
# unzip pcre-8.10.zip
第十八 安装maildrop
#ln –sv # ln -sv /usr/local/courier-authlib/bin/courierauthconfig /usr/bin
# ln -sv /usr/local/courier-authlib/include/* /usr/include
# groupadd -g 1001 vmail
# useradd -g vmail -u 1001 -M -s /sbin/nologin vmail
# ./configure
--enable-sendmail=/usr/sbin/sendmail
--enable-trusted-users='root vmail'
--enable-syslog=1 --enable-maildirquota
--enable-maildrop-uid=1001
--enable-maildrop-gid=1001
--with-trashquota --with-dirsync
# make
# make install
2 验证安装是否正常
#maildrop -v
GDBM/DB extensions enabled.
Courier Authentication Library extension enabled.
Maildir quota extension are now always enabled.
This program is distributed under the terms of the GNU General Public
License. See COPYING for additional information.
maildrop unix - n n - - pipe
flags=DRhu user=vmail argv=/usr/local/bin/maildrop -d ${recipient}
6 修改postfix的主配置文件
virtual_transport = virtual
修改为:
virtual_transport = maildrop
7 修改/etc/authmysqlrc
MYSQL_UID_FIELD '2525'
MYSQL_GID_FIELD '2525'
更改为:
MYSQL_UID_FIELD '1001'
MYSQL_GID_FIELD '1001
如果启用了suexec的功能,则将虚拟主机中指定的
SuexecUserGroup postfix postfix
修改为:
SuexecUserGroup vmail vmail
如果没有使用上面的功能,则修改User和Group指令后的用户为vmail
将前文中的如下项
User postfix
Group postfix
修改为:
User vmail
Group vmail
# chown -R vmail.vmail /var/spool/mail
ClamAV是一个unix系统平台上的开源反病毒工具,它是特地为在邮件网关上进行邮件扫描而设计的。整套软件提供了许多的实用工具,包括一个可伸缩和可升级的多线程守护进程、一个命令行扫描工具和病毒库自动升级工具。
SpamAssassin 是目前最好的、最流行的开源反垃圾邮件软件之一。它是一个邮件过滤器,使用了多种反垃圾邮件技术,如:文本分析、贝叶斯过滤、DNS黑名单和分布式协同过滤数据库等。如果邮件被 SpamAssassin 识别为垃圾邮件(Spam),病毒邮件(Virus),不规则的邮件头(Bad Header)等,都会被 Amavisd 隔离或复制一份到 /var/virusmails/ 目录,但是将邮件的去留留给管理员做决定,虽然 Amavisd 默认使用 gzip 对这些邮件进行压缩,但该目录的大小仍将与日俱增。如果整个分区的空间被该目录占满,将有可能导致系统无法正常运行,例如:假死、无法正常提供服务等。
建议先随机挑几个文件来分析一下,(主要是以 virus- 开头的邮件,因为 spam- 开头的邮件都已经发到了实际用户邮箱里,这里的只是一个拷贝。)如果您确认这些都是病毒邮件,可以设置一个 crontab 任务定时将它们删除。例如每天删除一次,或者以每星期、每月为时间周期,等等
amavisd-new是一个连接MTA和内容检测工具(诸如病毒扫描工具和SpamAssassin)的高性能接口程序,使用perl语言写成。它一般通过SMTP、ESMTP或者LMTP和MTA进行通讯,当然也可以借助于其它外部程序进行。同postfix(MTA)协同工作时表现尤佳。当它呼叫SpamAssassin进行内容过滤时,对于一封邮件只需要呼叫一次,而不管这封邮件将发往多少个收件人;同时,它亦会尽力保证实现每一位收件人的偏好设置,如接收/拒绝,检测/不检测,垃圾邮件级别等;它还会在邮件头部分插入spam相关信息。amavisd-new 是一个介于 MTA 和内容过滤软件之间的桥梁,其角色就像是两者之间的沟通者。 amavisd-new 本身也是个简单的 MTA,也可以用来架设一个独立的 Mail Gateway,提供多台 Mail Server 做邮件过滤。除此之外,amavisd -new 还可以结合十多种杀毒软件来做病毒防护。
- 负责调用 ClamAV 对邮件进行病毒扫描
- 负责调用 SpamAssassin 对邮件内容进行过滤
#LogFile /tmp/clamd.log
#PidFile /var/run/clamd.pid
LocalSocket /tmp/clamd.socket
#DatabaseDirectory /var/lib/clamav
#User clamav
修改为:
LogFile /var/log/clamav/clamd.log
PidFile /var/run/clamav/clamd.pid
LocalSocket /var/run/clamav/clamd.socket
DatabaseDirectory /usr/local/clamav/share
User amavis
启用以下选项
LogSyslog yes
LogFacility LOG_MAIL
LogVerbose yes
StreamMaxLength 20M (后面的数值应该与邮件服务器允许的最大附件值相一致)
#vim /etc/clamav/freshclam.conf
DatabaseDirectory /usr/local/clamav/share
DatabaseMirror database.clamav.net
5 建立,进程与socket 所在的目录,并让它属于clamav用户:
#touch /var/log/clamav/freshclam.log
37 * * * /usr/local/clamav/bin/freshclam
# echo “/usr/local/clamav/lib” >> /etc/ls.so.conf
# ldconfig –v
9 添加开机更新病毒库和开启启动
#echo “/usr/local/clamav/sbin/clamd –c /etc/clamav/clamd.conf” >>/etc/rc.local
1 安装SpamAssassin 依赖的perl 模块,当然您可以去cpam 官方网站去下载各个模块然后,
必须的软件包:
Digest::SHA1
HTML::Parser
Net::DNS
LWP (aka libwww-perl)
HTTP::Date
IO::Zlib
Archive::Tar
可选的软件包,其中有些后面的amavisd也有可能会用到:
MIME::Base64
DB_File
Net::SMTP
Mail::SPF
IP::Country::Fast
Net::Ident
IO::Socket::INET6
IO::Socket::SSL
Compress::Zlib
Time::HiRes
Mail::DKIM
Mail::DomainKeys
DBI *and* DBD driver/modules
Encode::Detect
Apache::Test
Razor2
当然您可以在cpam 官方网站上下载上面的所有的包,但是我在安装的的时候有还有大量依赖的软件包,需要安装不然在启动SpamAssassin 报错
#perl -MCPAN -e shell
cpan> install Digest::SHA1
#tar zxvf 软件包.tar.gz
#cd 软件包
#perl Makefile.PL
#make
#make test
#make install
说明:某些软件包安装的过程中可能需要已经列出的其它软件包的支持(可以先尝试安装Spamassassin,然后按提示补充所需软件包),请安照提示自行调整安装顺序。另外,其中有个软件包安装过程中可能要求声明环境变量LC_ALL,此时,可输入如下命令,并重新进行软件包的编译安装即可。
#export LC_ALL=C
2 安装Mail-SpamAssassin-3.3.1.
3 修改主配置文件无法
required_hits 10.0
rewrite_subject 1
required_score 5.0
rewrite_header Subject *****SPAM*****
report_safe 1
use_bayes 1
bayes_auto_learn 1
skip_rbl_checks 1
use_razor2 0
use_pyzor 0
ok_locales all
4 测试spamassassin,并查看测试结果
#spamassassin -t < sample-nonspam.txt > nonspam.out
#spamassassin -t < sample-spam.txt > spam.out
#less nonspam.out
5 检查配置文件
6 启动 ,并将其添加至开机自动启动队列中
#echo “/usr/bin/spamd –d” >>/etc/rc.local
# chown -R amavis:amavis /var/amavis
#chmod -R 750 /var/amavis
4 安装拷贝服务端至SPATH中指定的目录,推介拷贝至/usr/local/sbin
修改为如下内容
$daemon_user = 'amavis';
$daemon_group = 'amavis';
$mydomain = 'benet.org'; (此处可更改为您集体的域)
$virus_admin = "postmaster\@$mydomain";
$mailfrom_notify_admin = "postmaster\@$mydomain";
$mailfrom_notify_recip = "postmaster\@$mydomain";
$mailfrom_notify_spamadmin = "postmaster\@$mydomain";
$mailfrom_to_quarantine = '';
virus_admin_maps => ["postmaster\@$mydomain"] (指定报告病毒和垃圾邮件时发送系统邮件的用户身份)
spam_admin_maps => ["postmaster\@$mydomain"]
\&ask_daemon, ["CONTSCAN {}\n", "/var/run/clamav/clamd.socket"],
qr/^.*?: (?!Infected Archive)(.*) FOUND$/m ],
['Mail::ClamAV', \&ask_daemon, ['{}','clamav-perl:'], [0], [1], qr/^INFECTED: (.+)/m],
7 测试启动
fetch_modules: error loading optional module MIME/Decoder/BinHex.pm:
Can't locate Convert/BinHex.pm in @INC (@INC contains: /usr/lib/perl5/site_perl/5.8.8/i386-linux-thread-multi /usr/lib/perl5/site_perl/5.8.8 /usr/lib/perl5/site_perl /usr/lib/perl5/vendor_perl/5.8.8/i386-linux-thread-multi /usr/lib/perl5/vendor_perl/5.8.8 /usr/lib/perl5/vendor_perl /usr/lib/perl5/5.8.8/i386-linux-thread-multi /usr/lib/perl5/5.8.8) at /usr/lib/perl5/site_perl/5.8.8/MIME/Decoder/BinHex.pm line 43.
BEGIN failed--compilation aborted at /usr/lib/perl5/site_perl/5.8.8/MIME/Decoder/BinHex.pm line 43.
Compilation failed in require at /usr/local/sbin/amavisd line 197.
#tar xvf Convert-BinHex-1.119.tar.gz
# cd Convert-BinHex-1.119
#perl Makefile.PL
# make && make install
8 修改postfix 的配置文件,并配置其能调用amavisd,用来实现病毒及其垃圾邮件的过滤
==========================================================================
# service type private unpriv chroot wakeup maxproc command + args
# (yes) (yes) (yes) (never) (100)
# ==========================================================================
#
amavisfeed unix - - n - 2 smtp
-o smtp_data_done_timeout=1200
-o smtp_send_xforward_command=yes
-o disable_dns_lookups=yes
-o max_use=20
#
127.0.0.1:10025 inet n - n - - smtpd
-o content_filter=
-o smtpd_delay_reject=no
-o smtpd_client_restrictions=permit_mynetworks,reject
-o smtpd_helo_restrictions=
-o smtpd_sender_restrictions=
-o smtpd_recipient_restrictions=permit_mynetworks,reject
-o smtpd_data_restrictions=reject_unauth_pipelining
-o smtpd_end_of_data_restrictions=
-o smtpd_restriction_classes=
-o mynetworks=127.0.0.0/8
-o smtpd_error_sleep_time=0
-o smtpd_soft_error_limit=1001
-o smtpd_hard_error_limit=1000
-o smtpd_client_connection_count_limit=0
-o smtpd_client_connection_rate_limit=0
-o receive_override_options=no_header_body_checks,no_unknown_recipient_checks,no_milters
-o local_header_rewrite_clients=
注:注意每行的“-o”前的空格
#vi /etc/postifx/main.cf
在文末添加如下行:
content_filter=amavisfeed:[127.0.0.1]:10024
9 重新加载postfix 的主配置文件,并查看启动情况
10 查看amavisd是否在监听10024 端口,并测试服务启动的情况
#netstat –tunlp | grep 10024
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 [127.0.0.1] ESMTP amavisd-new service ready
EHLO localhost
250 XFORWARD NAME ADDR PORT PROTO HELO SOURCE
quit
221 2.0.0 [127.0.0.1] amavisd-new closing transmission channel
11 postfix 在 重新加载配置文件后将授权并激活了10025 端口,一个正常的服务连接应该类同下面所示
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 Welcome to our mail.frank.net ESMTP,Warning:Version not Available!
EHLO localhost
250-SIZE 14336000
250-AUTH PLAIN LOGIN
250-AUTH=PLAIN LOGIN
250 DSN
221 2.0.0 Bye
Connection closed by foreign host.
12 通过amavisd 测试发Email
Connected to localhost.localdomain (127.0.0.1).
Escape character is '^]'.
220 [127.0.0.1] ESMTP amavisd-new service ready
HELO localhost
250 [127.0.0.1]
MAIL FROM:<>
250 2.1.0 Sender <> OK
RCPT TO:<postmaster>
250 2.1.5 Recipient <postmaster> OK
354 End data with <CR><LF>.<CR><LF>
From:Anti-Virus tester
To:MailServer Admin
Subject:amavisd test!
amavisd test!
. 接下来使用root用户测试收信
# mail
il version 8.1 6/6/93. Type ? for help.
"/var/spool/mail/root": 22 messages 1 new 22 unread
U 21 Anti-Virus tester Tue Dec 14 23:17 22/703 "amavisd test!"
>N 22 Anti-Virus tester Tue Dec 14 23:22 21/692 "amavisd test!
& 22
Message 22:
From MAILER-DAEMON Tue Dec 14 23:22:25 2010
X-Original-To: postmaster
Delivered-To: [email protected]
X-Virus-Scanned: amavisd-new at frank.net
X-Amavis-Alert: BAD HEADER SECTION, MIME error: error: unexpected end of
From:Anti-Virus tester
To:MailServer Admin
Subject:amavisd test!
amavisd test!
13 测试使用反病毒邮件(该处没有测试,是在网转载的)
# tail -3 /var/log/clamav/clamd.log
Reading databases from /usr/local/clamav/share
Database correctly reloaded (148100 signatures)
/var/amavis/tmp/amavis-20070918T225935-28502/parts/p002: Trojan.Downloader.Delf-747 FOUN
#tail -15 /var/log/maillog
Sep 18 23:36:40 mail postfix/pickup[28925]: 8C1681A609: uid=1001 from=<[email protected]>
Sep 18 23:36:40 mail postfix/cleanup[29002]: 8C1681A609: message-id=<[email protected]>
Sep 18 23:36:40 mail postfix/qmgr[28924]: 8C1681A609: from=<[email protected]>, size=83658, nrcpt=1 (queue active)
Sep 18 23:36:43 mail clamd[28473]: /var/amavis/tmp/amavis-20070918T225935-28502/parts/p002: Trojan.Downloader.Delf-747 FOUND
Sep 18 23:36:44 mail postfix/smtpd[29011]: connect from mail[127.0.0.1]
Sep 18 23:36:44 mail postfix/cleanup[29002]: CDF9B1A602: message-id=<[email protected]>
Sep 18 23:36:44 mail postfix/smtpd[29011]: disconnect from mail[127.0.0.1]
Sep 18 23:36:44 mail postfix/qmgr[28924]: CDF9B1A602: from=<[email protected]>, size=2230, nrcpt=1 (queue active)
Sep 18 23:36:44 mail amavis[28502]: (28502-05) Blocked INFECTED (Trojan.Downloader.Delf-747), <[email protected]> -> <[email protected]>, quarantine: virus-7mnx1DHavOWC, Message-ID: <[email protected]>, mail_id: 7mnx1DHavOWC, Hits: -, size: 83658, 4203 ms
Sep 18 23:36:45 mail postfix/smtp[29006]: 8C1681A609: to=<[email protected]>, relay=127.0.0.1[127.0.0.1]:10024, delay=4.7, delays=0.42/0.05/0.12/4.1, dsn=2.7.0, status=sent (250 2.7.0 Ok, discarded, id=28502-05 - VIRUS: Trojan.Downloader.Delf-747)
Sep 18 23:36:45 mail postfix/qmgr[28924]: 8C1681A609: removed
Sep 18 23:36:45 mail postfix/local[29014]: CDF9B1A602: to=<[email protected]>, orig_to=<[email protected]>, relay=local, delay=0.28, delays=0.12/0.09/0/0.07, dsn=2.0.0, status=sent (delivered to mailbox)
If your spam filter supports it, the GTUBE provides a test by which you
can verify that the filter is installed correctly and is detecting incoming
spam. You can send yourself a test mail containing the following string of
characters (in upper case and with no white spaces and line breaks):
XJS*C4JDBQADN1.NSBN3*2IDNEN*GTUBE-STANDARD-ANTI-UBE-TEST-EMAIL*C.34X
Sep 19 00:04:11 mail spamd[29062]: rules: meta test FM_DDDD_TIMES_2 has dependency 'FH_HOST_EQ_D_D_D_D' with a zero score
Sep 19 00:04:11 mail spamd[29062]: rules: meta test FM_SEX_HOSTDDDD has dependency 'FH_HOST_EQ_D_D_D_D' with a zero score
Sep 19 00:04:11 mail spamd[29062]: rules: meta test HS_PHARMA_1 has dependency 'HS_SUBJ_ONLINE_PHARMACEUTICAL' with a zero score
Sep 19 00:04:11 mail spamd[29062]: spamd: server started on port 783/tcp (running version 3.2.3)
Sep 19 00:04:12 mail spamd[29062]: spamd: server successfully spawned child process, pid 29064
Sep 19 00:04:12 mail spamd[29062]: spamd: server successfully spawned child process, pid 29065
Sep 19 00:06:44 mail postfix/pickup[28925]: E37651A60E: uid=1001 from=<[email protected]>
Sep 19 00:06:44 mail postfix/cleanup[29073]: E37651A60E: message-id=<[email protected]>
Sep 19 00:06:45 mail postfix/qmgr[28924]: E37651A60E: from=<[email protected]>, size=1041, nrcpt=1 (queue active)
Sep 19 00:07:01 mail amavis[28502]: (28502-06) Blocked SPAM, <[email protected]> -> <[email protected]>, quarantine: spam-7ui+Zpn7-M00.gz, Message-ID: <[email protected]>, mail_id: 7ui+Zpn7-M00, Hits: 1004.576, size: 1040, 12805 ms
Sep 19 00:07:01 mail postfix/smtp[29079]: E37651A60E: to=<[email protected]>, relay=127.0.0.1[127.0.0.1]:10024, delay=18, delays=1.8/1.5/4.9/9.9, dsn=2.5.0, status=sent (250 2.5.0 Ok, id=28502-06, DISCARD(bounce.suppressed))
1) 首先确认系统上是否安装gd,如果没有安装请安装gd
2) 安装Time-HiRes
3) 安装File-Tail
4) 安装rrdtools
# cp -r /var/www/extsuite/extman/addon/mailgraph_ext /usr/local
5) 复制启动脚本,并把其加入到自动启动列队中