ASA5585-S20测试方案
Technorati 标签: ASA5585, 测试, failover, asdm
1, ASA5585概况
1.1, ASA5585性能指标

1.2, 本测试文档目标
① 掌握关键部署技术,并搭建ASA5580最佳部署实践;
② 熟练ASA5580运维技能;
③ 线下设计模拟部署线上环境。
1.3, 关键测试点
① HA routed方式部署;
② Global policy;
③ Redundancy interface;
④ Sla track;
⑤ Interface distribute across io-bridge:特指asa5580硬件架构设计,适当部署ASA5580可以提高其性能,而ASA5585没有这个限制;
⑥ Two link down;
⑦ Configure virtual mac address to avoid the interruption of network traffic;
⑧ Upgrade software online。
1.4, 几个重要命令
① Writer memory;
② Writer standby;
③ No failover active in active unit,failover active in standby unit;
④ asp load-balance per-packet;
⑤ show cpu usage detailed;
⑥ failover key;
⑦ failover reset;
ASA配置案例集锦:
http://www.cisco.com/en/US/products/ps6120/prod_configuration_examples_list.html
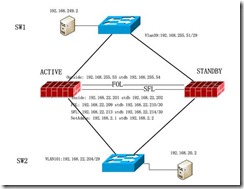
2, 测试拓扑
2.1, 设备准备和模拟拓扑
ASA5585-20 2台;
L3层交换机 2台,通过vlan隔离来模拟图中的6台交换机;
网线若干;
|
2.2, Redundant interface测试
|
Redundant interface概念:在ASA上启用一个逻辑接口redundant interface,绑定多个物理接口,其中一个接口作为active,而另一个为backup。即traffic走在active接口上。当active失效后,backup interface马上转为active,接管流量。配置如下:
|
|
SW1#
interface Vlan38
ip address 192.168.255.34 255.255.255.248
end
interface GigabitEthernet1/1
switchport access vlan 38
switchport mode access
spanning-tree portfast
interface GigabitEthernet1/2
switchport access vlan 38
switchport mode access
spanning-tree portfast
end
|
|
ASA5585-A-D01#
interface Redundant1
member-interface GigabitEthernet0/0
member-interface GigabitEthernet0/1
nameif Outside2C7609
security-level 0
ip address 192.168.255.35 255.255.255.248
!
interface GigabitEthernet0/0
no nameif
no security-level
no ip address
interface GigabitEthernet0/1
no nameif
no security-level
no ip address
|
|
ASA5585-A-D01# ping 192.168.255.34 repeat 10000
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
/Success rate is 99 percent (9999/10000), round-trip min/avg/max = 1/1/30 ms
|
|
验证结果:
1,互联交换机上的两个互联端口不配置port-channel:
① 当active interface fail后,ping包丢一个;
② 当failed interface become normal后,其不会抢占active mode,且不丢包。
2,互联交换机上的两个互联端口配置port-channel:
③ 当active interface fail后,ping包丢一个;
④ 当failed interface become normal后,数据包全部丢弃。
因此,上联交换机不能配置portchannel。
而交换机和FW都配置portchannel后,测试结果:
⑤ 当active interface fail后,ping包丢一个;
⑥ 当failed interface become normal后,其不会抢占active mode,且不丢包。
------------------------------------------------
为什么存在redundant接口:由于在8.3之前的ASA版本上不支持portchannel,因此设计了redundant接口技术,但是明显portchannel的实现优势更大。
|
2.3, Upgrade software
|
ciscoasa# sh disk0:
--#-- --length-- -----date/time------ path
13 32768 Apr 01 2011 10:56:16 coredumpinfo
14 43 Apr 01 2011 10:56:16 coredumpinfo/coredump.cfg
122 17676288 Apr 01 2011 10:57:20 asa824-smp-k8.bin
123 14812604 Apr 01 2011 10:57:56 asdm-635.bin
3 32768 Apr 01 2011 11:02:02 log
12 32768 Apr 01 2011 11:02:20 crypto_archive
125 12105313 Apr 01 2011 11:02:30 csd_3.5.841-k9.pkg
126 32768 Apr 01 2011 11:02:30 sdesktop
132 1462 Apr 01 2011 11:02:30 sdesktop/data.xml
127 2857568 Apr 01 2011 11:02:30 anyconnect-wince-ARMv4I-2.4.1012-k9.pkg
128 3203909 Apr 01 2011 11:02:32 anyconnect-win-2.4.1012-k9.pkg
129 4832344 Apr 01 2011 11:02:32 anyconnect-macosx-i386-2.4.1012-k9.pkg
130 5209423 Apr 01 2011 11:02:32 anyconnect-linux-2.4.1012-k9.pkg
2049605632 bytes total (1985347584 bytes free)
|
|
ciscoasa# copy tftp: disk0:
Address or name of remote host []? 192.168.1.2
Source filename []? asa841-smp-k8.bin
Destination filename [asa841-smp-k8.bin]?
Accessing tftp://192.168.1.2/asa841-smp-k8.bin...!!!!!!!!!!!!!!!
---------------------------------------------------------------------------
ciscoasa# copy tftp: disk0:
Address or name of remote host [192.168.1.2]?
Source filename [asa841-smp-k8.bin]? asdm-641.bin
Destination filename [asdm-641.bin]?
Accessing tftp://192.168.1.2/asdm-641.bin...!!!!!!!!!!!!!!!
|
|
ciscoasa(config)# sh disk0:
--#-- --length-- -----date/time------ path
13 32768 Apr 01 2011 10:56:16 coredumpinfo
14 43 Apr 01 2011 10:56:16 coredumpinfo/coredump.cfg
122 17676288 Apr 01 2011 10:57:20 asa824-smp-k8.bin
123 14812604 Apr 01 2011 10:57:56 asdm-635.bin
133 30726144 Apr 27 2011 19:21:18 asa841-smp-k8.bin
3 32768 Apr 01 2011 11:02:02 log
12 32768 Apr 01 2011 11:02:20 crypto_archive
134 15841428 Apr 27 2011 19:23:37 asdm-641.bin
125 12105313 Apr 01 2011 11:02:30 csd_3.5.841-k9.pkg
126 32768 Apr 01 2011 11:02:30 sdesktop
132 1462 Apr 01 2011 11:02:30 sdesktop/data.xml
127 2857568 Apr 01 2011 11:02:30 anyconnect-wince-ARMv4I-2.4.1012-k9.pkg
128 3203909 Apr 01 2011 11:02:32 anyconnect-win-2.4.1012-k9.pkg
129 4832344 Apr 01 2011 11:02:32 anyconnect-macosx-i386-2.4.1012-k9.pkg
130 5209423 Apr 01 2011 11:02:32 anyconnect-linux-2.4.1012-k9.pkg
2049605632 bytes total (1938751488 bytes free)
|
|
ciscoasa(config)# boot system disk0:/asa841-smp-k8.bin
ciscoasa(config)# asdm image disk0:/asdm-641.bin
ciscoasa(config)# wr
Building configuration...
Cryptochecksum: 23e278df 5d9abf13 31493b4e def0294e
3110 bytes copied in 2.40 secs (1555 bytes/sec)
[OK]
ciscoasa(config)# reload
Proceed with reload? [confirm]
ciscoasa(config)#
重启完成大概需要3分钟左右。
|
|
在线版本升级:
ciscoasa(config)# boot system disk0:/asa841-smp-k8.bin
ciscoasa(config)# asdm image disk0:/asdm-641.bin
ciscoasa(config)# wr
ciscoasa(config)#failover reload-standby //在active上重启standby设备;
…………
ciscoasa(config)#no failover active //进行ha切换;
ciscoasa(config)# reload
测试结果:
在没有进行ha切换的情况下直接reload,测试丢包4个。
|
2.4, Configure ssh admin
|
prompt hostname state //会在提示符前显示当前FW的
act/stdb状态;
interface Management0/0
nameif management
security-level 100
ip address 192.168.2.1 255.255.255.0
management-only
!
crypto key generate rsa modulus 1024
ssh 192.168.2.0 255.255.255.0 management
ssh timeout 30
ssh version 2
username asaAdmin password xxxxxx privilege 15
enable password xxxxxx
password xxxxxx
|
|
Ssh client登陆:
To gain access to the ASA CLI using SSH, enter the username
asa and the login password set by the password command. Then enter the username and password defined by the AAA server or local database.
Standby设备同样可以通过ssh进行管理。
|
2.5, Configure ASDM admin
|
http server enable 444 //端口默认为443
http 192.168.2.0 255.255.255.0 management
Standby设备同样可以通过ASDM进行管理。
|
2.6, Using global access rules

这里是否表明了我们可以直接使用global access rules,而不需配置interface-specific access rules了?
Answer:可以不用interface-specific access rules了,没有其他影响。
2.7, Implicit permits

2.8, Configure active/standby mode
|
Configure primary unit
:
-------------------------------------------------
failover lan unit primary
failover lan interface folink g0/2 //注意g0/2必须为初始化配置;
failover interface ip folink 192.168.22.209 255.255.255.252 standby 192.168.22.210 //注意不能为255.255.255.254的掩码;
int g0/2
no shutdown
failover link stlink GigabitEthernet0/3
failover interface ip stlink 192.168.22.213 255.255.255.252 standby 192.168.22.214
int g0/3
no shutdown
failover key ***** //配置同步认证;
failover //此命令会将ActiveUnit的配置推送给standby设备;
writer memory //本地保存,同时推送配置到standby并保存。
在active设备变更配置,会自动同步到standby设备上。
|
|
Configure secondary unit:
failover lan unit secondary //默认即为配置,可以不用配置;
failover lan interface folink g0/2 //注意g0/2必须为初始化配置;
failover interface ip folink 192.168.22.209 255.255.255.252 standby 192.168.22.210 //注意不能为255.255.255.254的掩码;
int g0/2
no shutdown
failover key *****
faileover //会从active设备同步配置到running-config,需要wr。
Write memory
-------------------------------------------------------
注意:standby上配置只需要上述即可,不需要额外配置,其他都可以从active上同步过来。
|
|
① 在unit上no failover,设备的A/S状态保持不变;
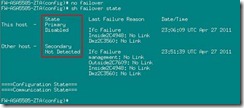
FW-ASA5585-ZTA(config)# no failover
INFO: This unit is currently in standby state. By disabling failover, this unit will remain in standby state.
② 接着使用failover命令,通过show failover state命令可以看到状态变化为:
Secondary:Sync Config à Bulk Sync à Failed 。因为有monitor的端口no link。
|
|
Virtual mac address可以任意定义,只需要与上下联交换机不冲突即可。同时正常情况下,不需要配置virtual mac address。
|
|
Monitor-interface
:
You can monitor up to 250 interfaces on a unit. By default, monitoring physical interfaces is enabled and monitoring subinterfaces is disabled.这里所说的interface是指逻辑接口,即nameif口。
配置如下:
no monitor-interface management
failover interface-policy 2 //两个逻辑口fail就发生切换,默认为1。
|
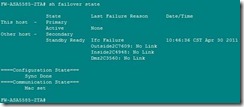
2.9, HA fail场景模拟
检测:从outside ftp到inside server进行数据传输是否中断?
初始化状态:
|
① 人为failover:failover active;
测试结果:
立即发生切换,ping丢3个包,有时候不丢包,且ftp数据传输无影响;
ftp没有影响;
② 批量下发策略;
测试结果:
无影响。
③ Outside fail;
测试结果:
5s左右显示切换提示,丢2个包;
ftp停顿5s内;
④ Failover link fail;
测试结果:
CLI上会提示:no switchover
不发生切换;但是若此时端口down掉,则发生不了HA切换。
⑤ Status link fail;
测试结果:
无HA和丢包等影响,但没有状态同步了。
⑥ http replication; //同步http状态,其他状态默认同步:
问题收集:
1, ASDM上acl的表头没有办法设置归类等;
2, inter地址是否可以不需要standby?
Answer:由于standby是可管理的,因此都需要standby地址。
3, nat不需要的话,没有特殊的配置?no nat-control?
8.3后默认为no nat-control,且不会产生xlate表项,同时可以在线添加nat策略。
no nat-control表示全局数据传输不需要做nat即可互通,当另外添加nat后,该nat局部起作用。而FWSM上即使使用no nat-control也会有xlate条目。
4, Log检索过滤,以及指定为哪条acl匹配?
5, 删除acl并apply后对当前的session(包括有状态和无状态)没有效果。
6, Show snmp-s oid:可以查看所有相关oid。