企业常用防火墙iptables相关原理详解
防火墙的类型:
包过滤型防火墙:(IP/TCP)
简单包过滤、带状态检查包过滤(连接状态)
简单包过滤
带状态检测包过滤:连接状态
应用层网关防火墙:(对特定的应用层协议做检查)
硬件:
Netscreen、checkpoint
linux内核:
TCP/IP:网络子系统
打开linux系统转发功能:/proc/sys/net/ipv4/ip_forward
linux路由表查看:route �Cn、 netstat �Crn
ipfw ---linux kernel2.0
ipchains ---linuxkernel 2.2
iptables ---linux kernel 2.4以后
iptables:用户空间工具
编写规则:
netfilter
内核中,框架(framework)
hookfunction
规则链input、 output、 forward、prerouting 、postrouting
源地址转换:SNAT --在即将出去的网卡地址做转换
目标地址转换:DNAT --在刚刚进来的网卡地址做转换
端口地址转换:PNAT --
4.2 防火墙的功能:
filter ---过滤
nat ---转换
mangle ---修改
raw
数据包过滤匹配流程:
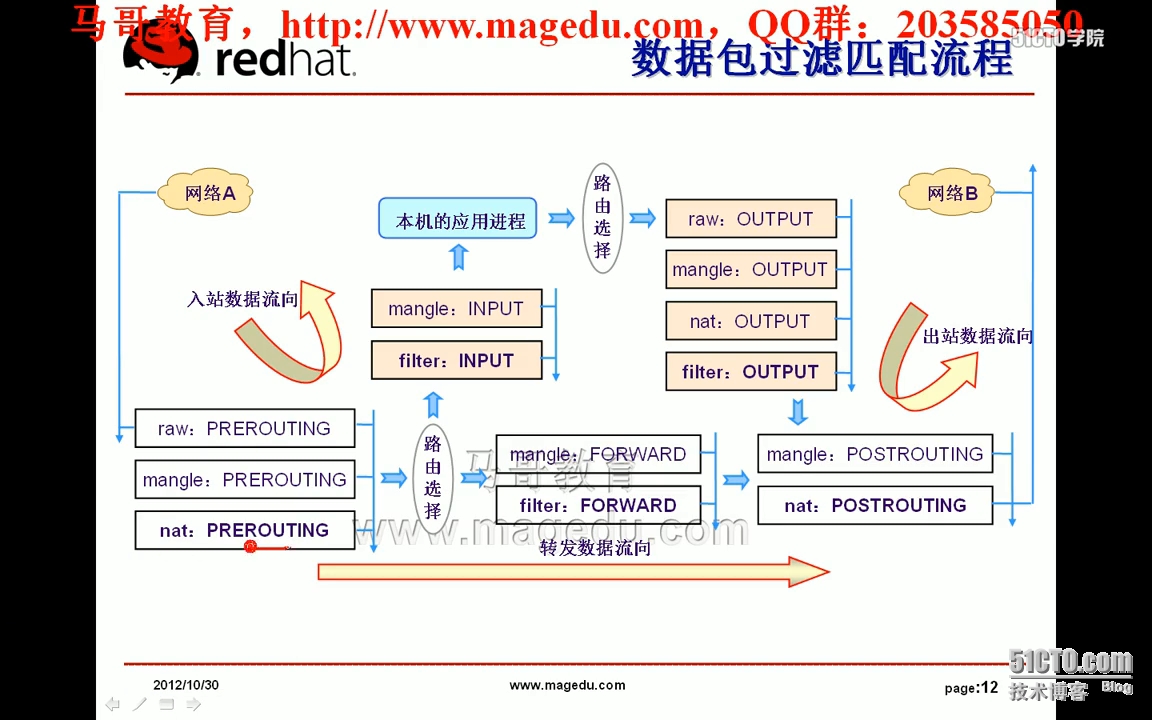
转发数据流向:
到本机
PreroutingàInput
转发
PreroutingàForwardàPostrouting
由本机发出
OutputàPostrouting
table:
raw
Prerouting、Output
mangle
Prerouting、Input 、Output 、Forward、Postrouting
nat
Prerouting、Output、Postrouting
filter
Input、Output 、Forward
Prerouting |
Input |
Forward |
Output |
Postrouting |
|
raw |
yes |
yes |
|||
mangle |
yes |
yes |
yes |
yes |
yes |
nat |
yes |
yes |
yes |
||
filter |
yes |
yes |
yes |
过滤:
匹配条件
netfilter,检查模块
拓展模块
处理动作
Accept
Drop,Reject
4.3 iptables用法
iptables [-tTABLE] COMMAND CHAIN [CRETIRIA] �CjACTION
-t 后跟的table:raw manglenat filter[默认]
COMMAND:对链或者对链中的规则进行管理操作
链中规则:
-A ---在链中最后添加一条新的规则
-I # ---插入一条规则,#表示插入为第几条
-R # ---替换第几条规则
-D # ---删除第几条规则或者�CDCRETAERIA删除链中规则
链:
-N ---新建一个自定义链
-X ---删除一个自定义的空链
-E ---重命名一条自定义链
-F ---清空指定链,如果不指定链,就会清空整个表中的链
-P ---设置链的默认策略
-Z ---置零(每条规则,包括默认策略都有两个计算器,一个是被本规则匹配到的所有数据包的个数,另一个是被本规则匹配到的所有数据包的大小之和)
-L ---查看
-v --详细
-vv --更加详细
--line-munbers ---行号
-x --显示精确值
-n --不要对地址或者名称做反解【显示数字地址】
ipatbes:
服务脚本:/ect/rc.d/init.d/iptables
脚本配置文件:/ect/sysconfig/iptables-config
规则保存位置:/etc/sysconfig/iptables
serviceiptables {status|start|stop|restart|save}
ls/ect/rc.d/init.d
… iptables …
ls/ect/sysconfig
… iptables-config …
serviceiptables status
cat/etc/sysconfig/iptables
serviceiptabes start
touch/etc/sysconfig/iptables
serviceiptabes start
iptabels�CL �Cn
iptabels �CL raw�Cn
iptabels �CL nat�Cn
iptabels �CLmanagle�Cn
iptabels �CL raw�Cn -v
匹配条件:
通用匹配:
-s --源地址
-d --目标地址
IP
NETWORK/MASK
!
-p {icmp|tcp|udp} --协议
-iIN_INTERFACE --指定流入接口
-oOUT_INTERFACE --指定流出接口
-jTARGET
ACCEPT
DROP
REJECT
REDIRECT
DNAT
SNAT
MASQUERADE
LOG
扩展匹配:
隐式扩展
-p tcp
--sportPORT[-PORT2]
--dportPORT[-PORT2]
--tcp-flagsSYN,ACK,RST,FIN SYN (=--syn )
-p udp
--sportPORT[-PORT2]
--dportPORT[-PORT2]
-p icmp
--icmp-type
0:echo-reply ---响应
8:echo-request ---请求
显示扩展
netfilter扩展模块引入的扩展,用于扩展匹配条件,通常需要额外专用选项来定义
-m state --用于实现链接的姿态检测
--state
NEW,ESTABLISHED,
RELATED[例如fdp],INVALID[无效的]
-mmultiport
--source-ports
--destination-ports
--ports
rpm�Cql iptables
……
/lib/iptables/libipt_state.so ---扩展state模块
……
/lib/iptables/libipt_mutiport --扩展mutiport模块
…….
iptabes�Ct filter �CA INPUT �Cs 172.16.0.0/16 �Cp icmp �C-icmp-type 8 �Cj DROP
---不允许172.16.0.0/16网段的用户ping本机
iptables�Ct filter �CL �Cn
……
target port opt source destination
DROP icmp -- 172.16.0.0/16 0.0.0.0/0 icmptype 8
……
iptables�Ct filter �CL �Cn -v
iptabes �Ct filter �CA INPUT �Cs 172.16.0.0/16�Cd 172.16.100.1 �Cp icmp �C-icmp-type 0 �Cj DROP
---不允许本机[172.16.100.1]ping172.16.0.0/16主机没有响应
iptables �Ct filter �CD INPUT 2
--删除filter表的第二条规则
iptables �CA INPUT �Cs !172.16.0.0/16 �Cd172.16.100.1 �Cp tcp �Cdport 80 �Cj DROP
--让除了172.16.0.0/16的主机访问172.16.100.1:80端口
iptables �CL �Cn
iptabels �Ct filter �CF INPUT
iptabels �CL �Cn
iptables �CF --清除所有的规则
iptables �Ct filter �CA INPUT �Cd 172.16.100.1�Cp tcp �Cdport 22 �Cj ACCEPT
--让所有机器的ssh访问172.16.100.1
iptables �Ct filter �CA OUTPUT �Cs172.16.100.1 �Cp tcp �Csport 22 �Cj ACCEPT
iptables �CL �Cn
iptables �Ct filter �CP INPUT DROP
iptables �Ct filter �CP OUTPUT DROP
iptables �CL �Cn �Cv
---将除了22端口都Drop掉
iptables �CA INPUT �Cd 172.16.100.1 �Cp icmp �C-icmp-type8 �Cj ACCEPT
iptables �CA OUTPUT �Cs 172.16.100.1 �Cp icmp�C-icmp-type 0 �Cj ACCEPT
---现在别人可以ping通自己
iptables �CA INPUT �Cs 172.16.100.1 �Cp icmp�C-icmp-type 8 �Cj ACCEPT
iptables �CA OUTPUT �Cd 172.16.100.1 �Cp icmp �C-icmp-type0 �Cj ACCEPT
---现在可让自己ping别人
iptables �CF
iptable �CL �Cn
iptables �Ct filter �CA INPUT �Cd 172.16.100.1�Cp tcp --dport 22 �Cm state --state NEW,ESTABLISHED �Cj ACCEPT
iptables �Ct filter �CA OUTPUT �Cs172.16.100.1 �Cp tcp --sport 22 �Cm state --state ESTABLISHED -j ACCEPT
iptables �CP INPUT DROP
iptables �CP OUTPUT DROP
iptables �CL �Cn -v
---不让本机建立任何新的ssh请求
iptables �Ct filter �CA INPUT �Cd 172.16.100.1�Cp tcp --dport 80 �Cm state --state NEW,ESTABLISHED �Cj ACCEPT
iptables �Ct filter �CA OUTPUT �Cs172.16.100.1 �Cp tcp --sport 80 �Cm state --state ESTABLISHED -j ACCEPT
---不让本机建立任何新的80端口请求
对语句进行优化[将OUTPUT请求的两条语句合并为一条]:
iptables �CA OUTPUT �Cs 172.168.100.1 �Cmstate --state ESTABLISHED �Cj ACCEPT
iptables �CD OUTPUT 1 --删除第一条规则,但是第二条会自动变成第一条
iptables �CD OUTPUT 1 --删除第一条规则,此时才算删除干净了
iptables �CL �Cn
iptables �CA INPUT �Cd 172.16.100.1 �Cp icmp--icmp-type 8 �Cj ACCEPT
iptables �CL �Cn
---让别人可以ping通自己
对80和22端口合并
iptables �CI INPUT 1 �Cd 172.16.100.1 �Cp tcp�Cm multiport �Cdestination-ports 80,22 �Cm state �Cstate NEW,ESTABLISHED �Cj ACCEPT
iptables �CD INPUT 2
iptables �CD INPUT 2
elinks �Cdump http://172.16.100.1
---不能本机连接自己
4.4 自定义链
创建:
iptables�CN NAME
删除:
iptables�CX NAME
置零:
Iptables�CZ NAME
iptables �CN come_in
iptables �CL �Cn -v
iptables �CX come_in
iptables �CL �Cn �Cv
iptables �CZ INPUT
iptables �CL �Cn �Cv
iptables �CA INPUT �Cd 172.16.100.1 �Cp tcp--dport 80 �Cj ACCEPT
iptables �CL �Cn �Cv
iptables �CZ INPUT
iptables �CL �Cn �Cv
netstat �Ctnlp
service httpd start
setenforce 0
service httpd start
iptables �CA INPUT �Ci lo �Cj ACCEPT
iptables �CA OUTPUT �Co lo �Cj ACCEPT
---让localhost对localhost本地访问ACCEPT
TCP
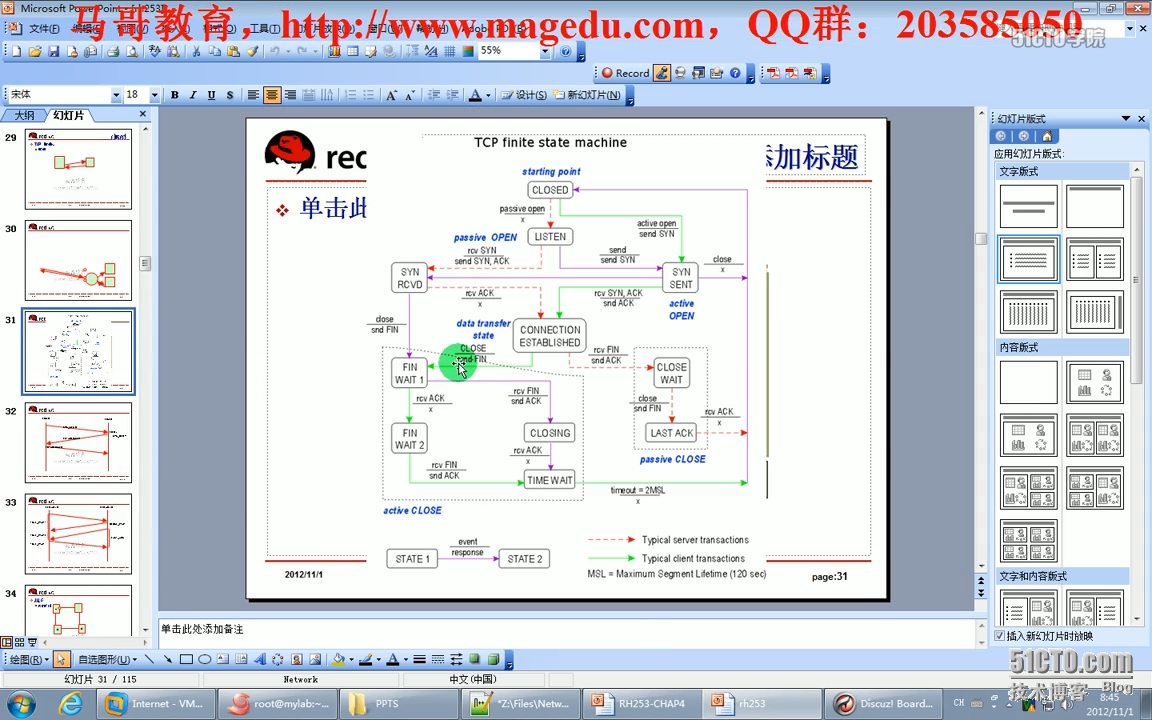
被动打开:LISTEN,SYN_RECV,ESTABLISHED
主动打开:SYN_SENT,ESTABLISHED
主动关闭:FIN_WAIT1,FIN_WAIT2,CLOSING,TIME_WAIT,CLOSED
被动关闭:CLOSE_WAIT,LAST_ACK,CLOSED,LISTEN
iptables �CN clean_in
iptables �CA clean_in �Cd 255.255.255.255 �Cpicmp �Cj DROP
iptables �CA clean_in �Cd 172.16.255.255 �Cpicmp j DROP
iptables �CA clean_in �Cp tcp ! �Csyn �Cm state�Cstate NEW �Cj DROP
iptables �CA clean_in �Cp tcp --tcp-flags ALLALL �Cj DROP
iptanles �CA clean_in �Cp tcp --tcp-flags ALLNONE �Cj DROP
iptables �CA clean_in �Cd 172.16.100.1 �CjRETURN --跳出clean_in链
iptables �CA INPUT �Cd 172.16.100.1 �Cj clean_in --跳到clean_in链上
iptables �CA INPUT �Ci lo �Cj ACCEPT
iptables �CA OUTPUT �Co lo �Cj ACCEPT
iptables �CA INPUT �Ci eth0 �Cm multiport �Cptcp --dports 53,113,135,137,139,445,-j DROP
iptables �CA INPUT �Ci eth0 �Cm multiport �Cpudp --dports 53,113,135,137,139,445,-j DROP
iptables �CA INPUT �Ci eth0 �Cp udp --dport1026 �Cj DROP
iptables �CA INPUT �Ci eth0 �Cm multiport �Cptcp --dport 1433,4899 �Cj DROP
iptables �CA INPUT �Cp icmp �Cm limit �Climit10/second �Cj ACCEPT
iptables �CA INPUT ! --syn �Cp tcp �Cm state�Cstate NEW �Cj DROP
iptables �CA INPUT �Cp tcp --tcp-flags ALLALL �Cj DROP
iptables �CA INPUT �Cp tcp --tcp-flags ALLNONE �Cj DROP
iptables �CA INPUT �Cp icmp �Cd255.255.255.255 �Cj DROP
iptables �CA INPUT �Cp icmp �Cd 172.16.255.255�Cj DROP
4.5 限定链接速率
显示扩展(续)
/lib/iptables
-mlimit
3/s,1000
--limit3/min
--limit-burst3000
iptables �CA INPUT �Ci eth0 �Cd 172.16.100.1�Cp icmp --icmp-type 8 �Cm limit --limit 5/minute --limit-burst 8 �Cj ACCEPT
iptables �CA INPUT �Ci eth0 �Cd 172.16.100.1�Cp icmp --icmp-type 8 �Cj DROP
iptables �CI INPUT 1 �Ci eth0 �Cd 172.16.100.1�Cp tcp --dport 22 �Cm state �Cstate ESTABLISHED �Cj ACCEPT
iptables �CI INPUT 2 �Ci eth0 �Cd 172.16.100.1�Cp tcp --dport 22 �Cm limit --limit 2/minute --limit-burst 2 �Cm state --stateNEW �Cj ACCEPT
这两条可以写成一条命令
iptables �CI INPUT 1 �Ci eth0 �Cd 172.16.100.1�Cp tcp --dport 22 �Cm limit --limit 2/minute --limit-burst 2 �Cm state --state NEW, ESTABLISHED �Cj ACCEPT
iptables �CI INPUT 3 �Ci eth0 �Cd 172.16.100.1�Cp tcp --dport 22 �Cj DROP
---对SSH的访问值限定
4.6 限定连接数
/lib/iptables
-mconnlimit
[!] --connlimit-above n --多于n个表示满足条件,表示应该不允许的个数
-miprage
--src-rangeip-ip
--dst-rangeip-ip
-mmac
--mac-sourceXX:XX:XX:XX:XX:XX
-mstring
--algo[kmp|bm]
--string“STRING”
iptables�CI OUTPUT 1 �Co eth0 �Cs 172.16.100.1 �Cp tcp --dport 80 �Cm string --algo kmp--string “sex” �Cj DROP
iptables�CL �Cn -v
-mrecent
利用iptables的recent模块来抵御DOS攻击
SSH:远程连接,
iptables �CI INPUT �Cp tcp --dport 22 �Cmconnlimit --connlimit-above 3 �Cj DROP
iptables �CI INPUT �Cp tcp --dport 22 �Cmstate --state NEW �Cm recent --set --name SSH
iptables �CI INPUT �Cp tcp --dport 22 �Cmstate --state NEW �Cm --update --seconds 300 --hitcount 3 --name SSH �Cj DROP
iptables �CA INPUT �Cp tcp --dport 22 �Cmstate --state NEW �Cm recent --update --name SSH--seconds 300 --hitcount 3 �CjLOG --log-prefix “SSH ATTACK”
--记录日志
4.7 网卡的源地址转发模拟
模拟图:
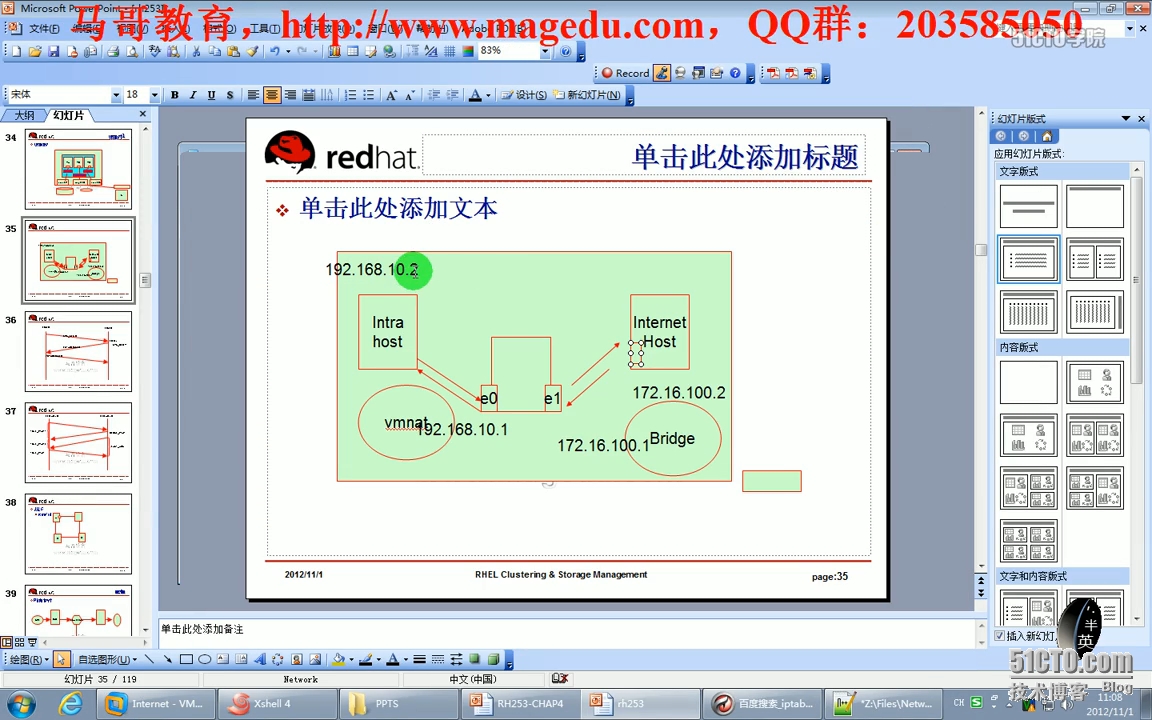
说明:
Intra Host IP:192.168.10.2模式为Vmnet1 ifconfig eth0192.168.10.2/24(ping192.168.100.1不通)
routeadd default gw 192.168.10.1(指定网关时候,还是ping192.168.100.1不通了,需要转发一次)
Iptables eth0 IP:192.168.10.1 模式为Vmnet1 ifconfig eth0 192.168.10.1/24
Serverhttpd start
打开主机的转发功能(转发)
cat /proc/sys/net/ipv4/ip_forward ---输出0
echo1 > /proc/sys/net/ipv4/ip_forward
Iptables eth1 IP:192.168.100.1模式为Bridge ifconfig eth1 192.168.100.1/16
Internet Host IP:192.168.100.2模式为Bridge ifconfig eth0 192.168.100.2/16
vi/var/www/html/index.html
thisis a test!
route add default gw 192.168.100.1
当100.1ping100.2时候抓包
tcpdump�Ci eth0 �Cnn �CX host 172.16.100.2 (100.2)
ping 192.168.100.2 (100.1)
tcpdump�Ci eth0 �Cnn �CX tcp port 80 and host 172.16.100.2 (100.2)
elinks�Cdump http://172.16.100.2(100.1)
做源地址转换
iptables�Ct nat �CA POSTROUTING �Cs 192.168.10.1/24 �Co eth1 �Cj SNAT --to-srource172.16.100.1 (Iptables)
iptables�Ct nat �CL �Cn(100.1)
elinks�Cdump http://172.16.100.2 (10.2)
iptables�Ct nat �CL �Cn (100.1)
tail/var/log/httpd/access_log(100.2)
限定只允许80,443,53端口上网
iptables �Ct nat �CA POSTROUTING �Cs192.168.0.0/24 �Cp tcp �Cm multiport --destination-port 80,443,53 �Cj SNAT--to-source 123.1.21.3
iptables �Ct nat �CA POSTROUTING �Cs192.168.0.0/24 �Cp udp �Cm multiport --destination-port 80,443,53 �Cj --to-source123.1.21.3
MASQURADE:自动选择一个合适地址作为转换后的源地址
iptables �Ct nat �CA POSTROUTING �Cs192.168.0.0/24 �Cp udp �Cm multiport --destination-port 80,443,53 �Cj MASQURADE
--此模式用于拨号上网,即外网地址动态获取!