Dcim.exe病毒文件感染相机SD卡处理方案
症状:数码相机SD卡中的照片目录看不到了,但是右键SD卡查看占用情况时,空间占用挺大,说明文件还在盘中。
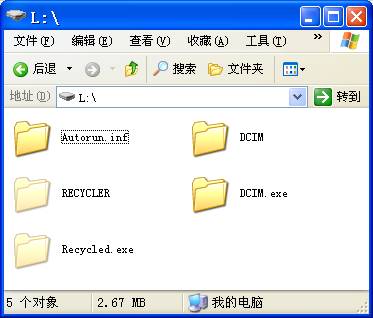
解决方案:直接在我的电脑-》工具-》文件夹选项:不勾选隐藏受保护的操作系统文件,同时隐藏文件和文件夹中点选显示所有文件和文件夹后确定即可看到照片文件目录DCIM
杀毒方案:采用symantec等杀毒软件进行清除查杀即可。
以下内容转自:http://www.uplook.cn/biancheng/115/1157968/
本文来自尚观知识库】
一个朋友还来借用已久的数码相机,正好偶家后院的一些花开得正盛,于是拍了几张PP,然后导入电脑处理。
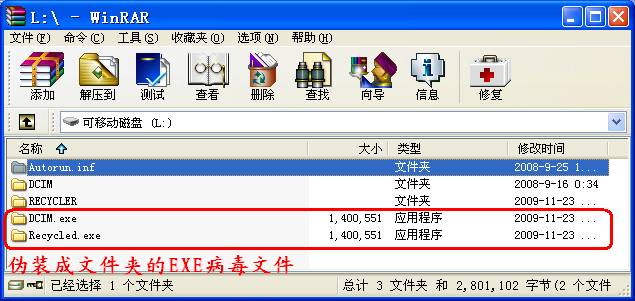
偶打开WinRAR作例行检查,打开相机记忆棒对应的L盘,不由吓出了一身冷汗,发现两个伪装成文件夹的EXE病毒文件,还多出一个名为recycled、类似回收站的文件夹,瑞星居然没有反应!
难道遇到了瑞星检测不出来的病毒?
在“资源管理器”中打开L盘,
进入 工具-》文件夹选项,取消“隐藏受保护的操作系统文件”和“隐藏已知文件类型的扩展名”前的钩,并选择“显示所有文件和文件夹”,应用,确定。
在DCIM.EXE上按右键,从快捷菜单中选择“使用瑞星杀毒”,瑞星才检测出Worm.Win32.Autorun.eyr!
用FileInfo提取病毒文件信息:
文件说明符 : L:\DCIM.exe
属性 : A---
数字签名:否
PE文件:是
获取文件版本信息大小失败!
创建时间 : 2009-11-23 10:47:43
修改时间 : 2009-11-23 10:47:48
大小 : 1400551 字节 1.343 MB
MD5 : d7435879a170e839eeeadb9587d68981
SHA1: 9A3727F6A25D14677840D6D578B4B6D1A1C3EC34
CRC32: b68180f7
上传到 http://www.virustotal.com扫描,结果如下:
文件 DCIM.exe 接收于 2009.12.15 11:28:35 (UTC)
| 反病毒引擎 | 版本 | 最后更新 | 扫描结果 |
| a-squared | 4.5.0.43 | 2009.12.15 | Trojan.Win32.FlyStudio!IK |
| AhnLab-V3 | 5.0.0.2 | 2009.12.15 | Win-Trojan/Zahl3731763.1400551 |
| AntiVir | 7.9.1.108 | 2009.12.15 | TR/Dropper.Gen |
| Antiy-AVL | 2.0.3.7 | 2009.12.15 | - |
| Authentium | 5.2.0.5 | 2009.12.02 | W32/Nuj.A.gen!Eldorado |
| Avast | 4.8.1351.0 | 2009.12.15 | Win32:Trojan-gen |
| AVG | 8.5.0.427 | 2009.12.15 | SHeur2.FZD |
| BitDefender | 7.2 | 2009.12.15 | GenPack:Trojan.Generic.1394234 |
| CAT-QuickHeal | 10.00 | 2009.12.15 | TrojanDropper.Silly.b |
| ClamAV | 0.94.1 | 2009.12.15 | - |
| Comodo | 3251 | 2009.12.15 | UnclassifiedMalware |
| DrWeb | 5.0.0.12182 | 2009.12.15 | Win32.HLLW.Autoruner.4360 |
| eSafe | 7.0.17.0 | 2009.12.14 | - |
| eTrust-Vet | 35.1.7176 | 2009.12.15 | - |
| F-Prot | 4.5.1.85 | 2009.12.14 | W32/Nuj.A.gen!Eldorado |
| F-Secure | 9.0.15370.0 | 2009.12.15 | GenPack:Trojan.Generic.1394234 |
| Fortinet | 4.0.14.0 | 2009.12.15 | PossibleThreat |
| GData | 19 | 2009.12.15 | GenPack:Trojan.Generic.1394234 |
| Ikarus | T3.1.1.74.0 | 2009.12.15 | Trojan.Win32.FlyStudio |
| K7AntiVirus | 7.10.920 | 2009.12.14 | Trojan.Win32.Malware.4 |
| Kaspersky | 7.0.0.125 | 2009.12.15 | Worm.Win32.FlyStudio.bt |
| McAfee | 5832 | 2009.12.14 | W32/Autorun.worm.ev |
| McAfee+Artemis | 5832 | 2009.12.14 | W32/Autorun.worm.ev |
| McAfee-GW-Edition | 6.8.5 | 2009.12.15 | Trojan.Dropper.Gen |
| Microsoft | 1.5302 | 2009.12.15 | Backdoor:Win32/FlyAgent.F |
| NOD32 | 4689 | 2009.12.15 | Win32/AutoRun.FlyStudio.CC |
| Norman | 6.04.03 | 2009.12.15 | W32/Lineage.BPWK |
| nProtect | 2009.1.8.0 | 2009.12.15 | Trojan/W32.Agent.1400551 |
| Panda | 10.0.2.2 | 2009.12.14 | Generic Malware |
| PCTools | 7.0.3.5 | 2009.12.15 | Net-Worm.SillyFDC |
| Prevx | 3.0 | 2009.12.15 | High Risk Worm |
| Rising | 22.26.01.01 | 2009.12.15 | Worm.Win32.Autorun.eyr |
| Sophos | 4.48.0 | 2009.12.15 | Mal/Behav-004 |
| Sunbelt | 3.2.1858.2 | 2009.12.15 | Trojan.Win32.Generic!BT |
| Symantec | 1.4.4.12 | 2009.12.15 | W32.SillyFDC |
| TheHacker | 6.5.0.2.093 | 2009.12.15 | W32/FlyStudio.bt |
| TrendMicro | 9.100.0.1001 | 2009.12.15 | TROJ_DROPPER.GEP |
| VBA32 | 3.12.12.0 | 2009.12.13 | Trojan-Dropper.Win32.Flystud.ko |
| ViRobot | 2009.12.15.2089 | 2009.12.15 | - |
| VirusBuster | 5.0.21.0 | 2009.12.14 | Backdoor.FlyAgent.ARB |
| 附加信息 |
|---|
| File size: 1400551 bytes |
| MD5...: d7435879a170e839eeeadb9587d68981 |
| SHA1..: 9a3727f6a25d14677840d6d578b4b6d1a1c3ec34 |
| SHA256: dd51f7f1837ef38987da140bcf303a0a0a064c4a6d7a11bb328fa1de64fd286b |
| ssdeep: 24576:bC7ATPZDzinZzdQq3D15pUylF83H3PFD+jIOnyCJqhQWodPjD4crbtZ0Jr hVpsdW:b8QZDzinZzV3J5e623fFD+jxy1hw/JrA |
| PEiD..: - |
| PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x1317 timedatestamp.....: 0x59bffa3 (Mon Dec 25 05:33:23 1972) machinetype.......: 0x14c (I386) ( 5 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x51ec 0x6000 7.00 4dba398236e8347fce073f48550e19c5 .rdata 0x7000 0xa4a 0x1000 3.58 367b7ce38d0c4c17f01e370dc697df5b .data 0x8000 0x1f58 0x2000 4.58 caf81b709a3fafbe71d2fc52d70be6a7 .data 0xa000 0x65000 0x65000 7.99 fcf40bcc3fc86886c00147009a3ba0ef .rsrc 0x6f000 0x3bf0 0x4000 3.40 825a8015620dc174a1747b2d60c4feb4 ( 2 imports ) > KERNEL32.dll: GetProcAddress, LoadLibraryA, CloseHandle, WriteFile, CreateDirectoryA, GetTempPathA, ReadFile, SetFilePointer, CreateFileA, GetModuleFileNameA, GetStringTypeA, LCMapStringW, LCMapStringA, HeapAlloc, HeapFree, GetModuleHandleA, GetStartupInfoA, GetCommandLineA, GetVersion, ExitProcess, HeapDestroy, HeapCreate, VirtualFree, VirtualAlloc, HeapReAlloc, TerminateProcess, GetCurrentProcess, UnhandledExceptionFilter, FreeEnvironmentStringsA, FreeEnvironmentStringsW, WideCharToMultiByte, GetEnvironmentStrings, GetEnvironmentStringsW, SetHandleCount, GetStdHandle, GetFileType, RtlUnwind, GetCPInfo, GetACP, GetOEMCP, MultiByteToWideChar, GetStringTypeW > USER32.dll: MessageBoxA, wsprintfA ( 0 exports ) |
| RDS...: NSRL Reference Data Set - |
| trid..: Win32 Executable MS Visual C++ (generic) (62.9%) Win32 Executable Generic (14.2%) Win32 Dynamic Link Library (generic) (12.6%) Clipper DOS Executable (3.3%) Generic Win/DOS Executable (3.3%) |
| pdfid.: - |
| <a href='http://info.prevx.com/aboutprogramtext.asp?PX5=88F072F6E75692145ED21559B9146E0008F29E40' target='_blank'>http://info.prevx.com/aboutprogramtext.asp?PX5=88F072F6E75692145ED21559B9146E0008F29E40</a> |
| ThreatExpert info: <a href='http://www.threatexpert.com/report.aspx?md5=d7435879a170e839eeeadb9587d68981' target='_blank'>http://www.threatexpert.com/report.aspx?md5=d7435879a170e839eeeadb9587d68981</a> |
| sigcheck: publisher....: n/a copyright....: n/a product......: n/a description..: n/a original name: n/a internal name: n/a file version.: n/a comments.....: n/a signers......: - signing date.: - verified.....: Unsigned |
| packers (Authentium): PE-Crypt.CF |
| packers (F-Prot): PE-Crypt.CF |
recycled.exe文件大小与DCIM.EXE相同,应该是同一病毒。
在L:\RECYCLER\S-5-3-42-2819952290-8240758988-879315005-3665中发现名为jwgkvsq.vmx的文件,
用FileInfo提取病毒文件信息:
文件说明符 : L:\RECYCLER\S-5-3-42-2819952290-8240758988-879315005-3665\jwgkvsq.vmx
属性 : -SHR
数字签名:否
PE文件:是
获取文件版本信息大小失败!
创建时间 : 2008-7-13 15:15:11
修改时间 : 2008-4-15 2:0:0
大小 : 160864 字节 157.96 KB
MD5 : 6b54e187a3a6971ffe03e9aea5afcacc
SHA1: 4809E42763DD2488DF993D752295941C0028085E
CRC32: 1997b4ea
上传到 http://www.virustotal.com扫描,结果如下:
| 反病毒引擎 | 版本 | 最后更新 | 扫描结果 |
| a-squared | 4.5.0.43 | 2009.12.15 | Net-Worm.Win32.Kido!IK |
| AhnLab-V3 | 5.0.0.2 | 2009.12.15 | Win32/Conficker.worm.Gen |
| AntiVir | 7.9.1.108 | 2009.12.15 | TR/Crypt.ZPACK.Gen |
| Antiy-AVL | 2.0.3.7 | 2009.12.15 | Worm/Win32.Kido.gen |
| Authentium | 5.2.0.5 | 2009.12.02 | W32/Conficker!Generic |
| Avast | 4.8.1351.0 | 2009.12.15 | Win32:Confi |
| AVG | 8.5.0.427 | 2009.12.15 | I-Worm/Generic.CMN |
| BitDefender | 7.2 | 2009.12.15 | Win32.Worm.Downadup.Gen |
| CAT-QuickHeal | 10.00 | 2009.12.15 | Worm.Conficker.b |
| ClamAV | 0.94.1 | 2009.12.15 | Worm.Downadup-85 |
| Comodo | 3251 | 2009.12.15 | NetWorm.Win32.Kido.ih |
| DrWeb | 5.0.0.12182 | 2009.12.15 | Win32.HLLW.Autoruner.5555 |
| eSafe | 7.0.17.0 | 2009.12.14 | Win32.Banker |
| eTrust-Vet | 35.1.7176 | 2009.12.15 | Win32/Conficker |
| F-Prot | 4.5.1.85 | 2009.12.14 | W32/Conficker!Generic |
| F-Secure | 9.0.15370.0 | 2009.12.15 | Worm:W32/Downadup.gen!A |
| Fortinet | 4.0.14.0 | 2009.12.15 | W32/Conficker.B!worm |
| GData | 19 | 2009.12.15 | Win32.Worm.Downadup.Gen |
| Ikarus | T3.1.1.74.0 | 2009.12.15 | Net-Worm.Win32.Kido |
| Jiangmin | 13.0.900 | 2009.12.15 | Worm/Kido.fi |
| K7AntiVirus | 7.10.920 | 2009.12.14 | Net-Worm.Win32.Kido |
| Kaspersky | 7.0.0.125 | 2009.12.15 | Net-Worm.Win32.Kido.ih |
| McAfee | 5832 | 2009.12.14 | W32/Conficker.worm.gen.b |
| McAfee+Artemis | 5832 | 2009.12.14 | W32/Conficker.worm.gen.b |
| McAfee-GW-Edition | 6.8.5 | 2009.12.15 | Trojan.Crypt.ZPACK.Gen |
| Microsoft | 1.5302 | 2009.12.15 | Worm:Win32/Conficker.C |
| NOD32 | 4689 | 2009.12.15 | a variant of Win32/Conficker.X |
| Norman | 6.04.03 | 2009.12.15 | W32/Conficker.JA |
| nProtect | 2009.1.8.0 | 2009.12.15 | Worm/W32.Kido.160864 |
| Panda | 10.0.2.2 | 2009.12.14 | W32/Conficker.C.worm |
| PCTools | 7.0.3.5 | 2009.12.15 | Net-Worm.Kido!sd6 |
| Prevx | 3.0 | 2009.12.15 | High Risk Worm |
| Rising | 22.26.01.01 | 2009.12.15 | Hack.Exploit.Win32.MS08-067.hm |
| Sophos | 4.48.0 | 2009.12.15 | Mal/Conficker-A |
| Sunbelt | 3.2.1858.2 | 2009.12.15 | Trojan.Malware |
| Symantec | 1.4.4.12 | 2009.12.15 | W32.Downadup.B |
| TheHacker | 6.5.0.2.093 | 2009.12.15 | W32/Kido.ih |
| TrendMicro | 9.100.0.1001 | 2009.12.15 | WORM_DOWNAD.AD |
| VBA32 | 3.12.12.0 | 2009.12.15 | Worm.Win32.kido.92 |
| ViRobot | 2009.12.15.2089 | 2009.12.15 | Worm.Win32.Conficker.160864 |
| VirusBuster | 5.0.21.0 | 2009.12.14 | Worm.Kido.LA |
| 附加信息 |
|---|
| File size: 160864 bytes |
| MD5...: 6b54e187a3a6971ffe03e9aea5afcacc |
| SHA1..: 4809e42763dd2488df993d752295941c0028085e |
| SHA256: 11fc18dbe7d497003d44beb4114a5c939bc3d95fc7ee05abbffb38af96f9d1a2 |
| ssdeep: 3072:RpovBKzUrgi1FDHDmTl8jAqJDdUMSk/+0zNQoiOuAhoIOM6+1u5lTTZuLEl :R+MwrguHDmTl8E2+q2MQoiza6os |
| PEiD..: - |
| PEInfo: PE Structure information ( base data ) entrypointaddress.: 0x43eb timedatestamp.....: 0x3be8e4db (Wed Nov 07 07:38:03 2001) machinetype.......: 0x14c (I386) ( 4 sections ) name viradd virsiz rawdsiz ntrpy md5 .text 0x1000 0x3494 0x3600 6.28 da6b6d517febce744574317d6cd01268 .rdata 0x5000 0x74a 0x800 4.66 7ba7d50f2f5e74b4273df1570aa7022a .data 0x6000 0xfc18 0xf600 7.98 32c3b469093c428939e2d700e8026b1e .reloc 0x16000 0x9f6 0xa00 6.35 6be06ddaa058c48c14eb94c47e317bbe ( 7 imports ) > KERNEL32.dll: IsDBCSLeadByte, LoadLibraryA, InterlockedDecrement, InterlockedExchangeAdd, GetModuleFileNameA, GetProcAddress, Sleep, MulDiv, GetLocalTime, VirtualAlloc, VirtualProtect, DosDateTimeToFileTime, QueryPerformanceFrequency, IsDebuggerPresent, GetLastError, IsBadWritePtr, GetComputerNameA, GetUserDefaultLCID, IsBadReadPtr > USER32.dll: IsIconic, GetAncestor, GetCursor, IsWindowUnicode, GetMenuContextHelpId, IsCharUpperA, GetWindowDC, IsClipboardFormatAvailable, GetForegroundWindow, GetGUIThreadInfo, GetParent, GetWindowPlacement, IsMenu, InSendMessage, CopyIcon, GetIconInfo, GetDlgItem > ADVAPI32.dll: GetUserNameA > MSVCRT.dll: _CIsinh, ldiv, _CIfmod, _adjust_fdiv, malloc, _initterm, free, memmove, _memccpy, _ultoa, time, ceil, ldexp, _pctype, _isctype, modf, __mb_cur_max, localeconv, div, _itoa, _CItanh, srand > GDI32.dll: GetPixel, GdiFlush, GetBitmapDimensionEx, GetStretchBltMode > ole32.dll: CoFileTimeNow, CoDosDateTimeToFileTime, CoRevertToSelf > SHELL32.dll: DuplicateIcon, - ( 0 exports ) |
| RDS...: NSRL Reference Data Set - |
| pdfid.: - |
| trid..: Win32 Executable Generic (38.4%) Win32 Dynamic Link Library (generic) (34.2%) Clipper DOS Executable (9.1%) Generic Win/DOS Executable (9.0%) DOS Executable Generic (9.0%) |
| <a href='http://info.prevx.com/aboutprogramtext.asp?PX5=D93EFFDB60D8DC83746002923A6753008F44CED1' target='_blank'>http://info.prevx.com/aboutprogramtext.asp?PX5=D93EFFDB60D8DC83746002923A6753008F44CED1</a> |
| ThreatExpert info: <a href='http://www.threatexpert.com/report.aspx?md5=6b54e187a3a6971ffe03e9aea5afcacc' target='_blank'>http://www.threatexpert.com/report.aspx?md5=6b54e187a3a6971ffe03e9aea5afcacc</a> |
| sigcheck: publisher....: n/a copyright....: n/a product......: n/a description..: n/a original name: n/a internal name: n/a file version.: n/a comments.....: n/a signers......: - signing date.: - verified.....: Unsigned |
| packers (Antiy-AVL): CrypToCrackPeProtector0.93 |
用WinRAR将病毒文件打包加密压缩后删除。