关于unsuccessful login attempts和account_locked
系统安全加固中,我们经常要在WIN和UNIX中经常要失败登录尝试次数,当达到指定的次数后,系统禁止该用户登录;如果是WIN平台,由于失败登录而被锁定的账户过一段时间后会自动解锁(由相关参数设定);而AIX平台似乎没有自动解锁这一特性(或许有,只是我不了解?)。
而暂时不再使用的用户,管理员往往会人工把它锁定。
在AIX中,要实现以上管理,分别修改unsuccessful login attempts和account_locked。
值得注意的是,由于失败登录而导致的账户被锁定和手工锁定账户的结果及解决办法是不一样的。
一、unsuccessful login attempts
1.设定unsuccessful login attempts值
方法一
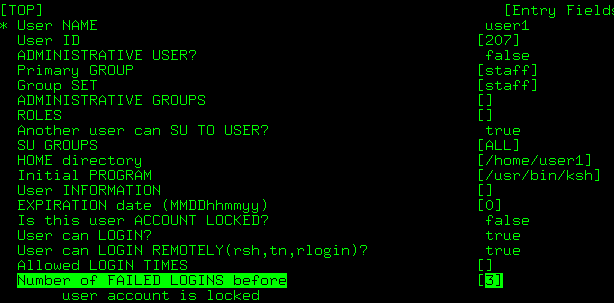
用Smitty users把user1属性
Number of FAILED LOGINS before user account is locked设定为3
方法二
也可以用命令行来实现
#chuser loginretries=3 user1
检查该用户属性
#lsuser -f user1
user1:
id=207
pgrp=staff
groups=staff
home=/home/user1
shell=/usr/bin/ksh
login=true
su=true
rlogin=true
daemon=true
admin=false
sugroups=ALL
admgroups=
tpath=nosak
ttys=ALL
expires=0
auth1=SYSTEM
auth2=NONE
umask=22
registry=files
SYSTEM=compat
logintimes=
loginretries=3
pwdwarntime=0
account_locked=false
minage=0
maxage=0
maxexpired=-1
minalpha=0
minother=0
mindiff=0
maxrepeats=8
minlen=8
histexpire=0
histsize=0
pwdchecks=
dictionlist=
fsize=-1
cpu=-1
data=262144
stack=65536
core=2097151
rss=65536
nofiles=2000
time_last_login=1262968379
time_last_unsuccessful_login=1262968719
tty_last_login=/dev/pts/4
tty_last_unsuccessful_login=/dev/pts/4
host_last_login=192.168.1.2
host_last_unsuccessful_login=192.168.1.2
unsuccessful_login_count=0
roles=
2.尝试使用错误密码登录
尝试用错误密码登录3次后提示失败登录尝试达到限定的阈值,禁止登录
AIX Version 5
(C) Copyrights by IBM and by others 1982, 2005.
login: user1
user1's Password:
3004-007 You entered an invalid login name or password.
login: user1
user1's Password:
3004-007 You entered an invalid login name or password.
login: user1
user1's Password:
3004-007 You entered an invalid login name or password.
AIX Version 5
(C) Copyrights by IBM and by others 1982, 2005.
login: user1
user1's Password:
3004-303 There have been too many unsuccessful login attempts; please see
the system administrator.
login:
3.检查失败登录次数
检查失败登录次数可以用lsuser查看
unsuccessful_login_count已经达到4次;而account_locked属性依然没有改变,仍然为false
-bash-3.00# lsuser -f user1
user1:
id=207
pgrp=staff
groups=staff
home=/home/user1
shell=/usr/bin/ksh
login=true
su=true
rlogin=true
daemon=true
admin=false
sugroups=ALL
admgroups=
tpath=nosak
ttys=ALL
expires=0
auth1=SYSTEM
auth2=NONE
umask=22
registry=files
SYSTEM=compat
logintimes=
loginretries=3
pwdwarntime=0
account_locked=false
minage=0
maxage=0
maxexpired=-1
minalpha=0
minother=0
mindiff=0
maxrepeats=8
minlen=8
histexpire=0
histsize=0
pwdchecks=
dictionlist=
fsize=-1
cpu=-1
data=262144
stack=65536
core=2097151
rss=65536
nofiles=2000
time_last_login=1262968379
time_last_unsuccessful_login=1262969926
tty_last_login=/dev/pts/4
tty_last_unsuccessful_login=/dev/pts/5
host_last_login=192.168.1.2
host_last_unsuccessful_login=192.168.1.2
unsuccessful_login_count=4
roles=
或者直接浏览/etc/security/lastlog
# cat /etc/security/lastlog
root:
time_last_login = 1262969648
tty_last_login = /dev/pts/4
host_last_login = 192.168.1.2
unsuccessful_login_count = 0
time_last_unsuccessful_login = 1264252052
tty_last_unsuccessful_login = /dev/pts/6
host_last_unsuccessful_login = 192.168.1.77
guest:
time_last_unsuccessful_login = 1226279970
tty_last_unsuccessful_login = /dev/pts/1
host_last_unsuccessful_login = 192.168.1.217
unsuccessful_login_count = 3
user1:
time_last_login = 1262968379
tty_last_login = /dev/pts/4
host_last_login = 192.168.1.2
unsuccessful_login_count = 4
time_last_unsuccessful_login = 1262969926
tty_last_unsuccessful_login = /dev/pts/5
host_last_unsuccessful_login = 192.168.1.2
oracle:
time_last_unsuccessful_login = 1255304971
tty_last_unsuccessful_login = 192_168_1_189_0
host_last_unsuccessful_login = 192.168.1.189:0
unsuccessful_login_count = 0
time_last_login = 1255305015
tty_last_login = 192_168_1_189_0
host_last_login = 192.168.1.189:0
informix:
time_last_unsuccessful_login = 1261962628
tty_last_unsuccessful_login = /dev/pts/0
host_last_unsuccessful_login = 192.168.1.157
unsuccessful_login_count = 0
time_last_login = 1262104409
tty_last_login = /dev/pts/3
host_last_login = 192.168.1.157
user2:
time_last_unsuccessful_login = 1262968664
tty_last_unsuccessful_login = /dev/pts/4
host_last_unsuccessful_login = 192.168.1.2
unsuccessful_login_count = 1
-bash-3.00#
4.尝试通过su – 来切换到user1
成功。可见即使账户锁定,依然可以用su – 来切换到被锁定的账户
5.解锁账户
方法一
通过SMITTY USERS来解锁USER1
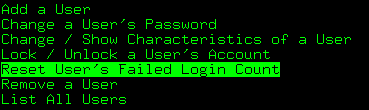
选择Reset User's Failed Login Count,在username栏输入user1
方法二
通过修改etc/security/lastlog中unsuccessful_login_count的值来进行行解锁
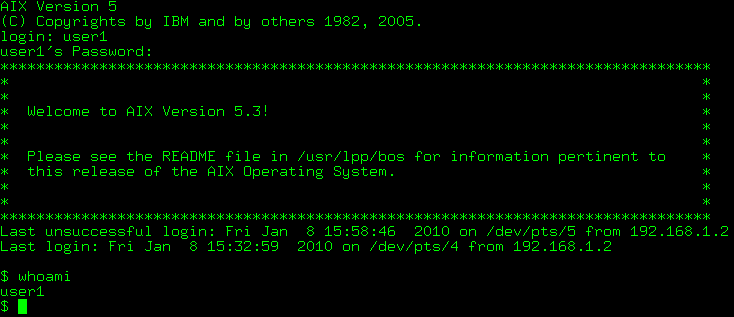
vi /etc/security/lastlog,将unsuccessful_login_count=X改为0即可
登录成功
二、account_locked
1.手工锁定用户USER1
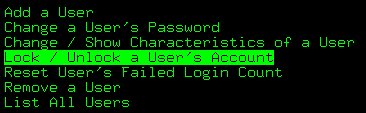
方法一
通过Smitty users来锁定user1,在user name栏输入user1;is this user account_locked栏选择true
方法二
# chuser account_locked=true user1
2.检查锁定状态
# lsuser -f user1 |grep account_locked
account_locked=true
尝试登录
login: user1
user1's Password:
3004-301 Your account has been locked; please see the system administrator.
3.尝试通过su – 来切换到user1
成功登录
4.解锁账户
方法一
用smitty users,将is this user account_locked属性改为false
方法二
# chuser account_locked=false user1
注意:从以上登录提示信息可以看出,在使用由于失败登录被锁定和手工锁定的账户来登录时,系统提示的信息是不一样的;而且账户(非ROOT)被锁定后依然可以通过ROOT账户来SU到该用户。
但是root用户失败登录次数达到设定值后被锁定,是不能通过其他用户SU到ROOT的,需要用光盘或磁带引导到维护模式下进行解锁。