nginx自签ssl证书
环境基于nginx1.9源码安装编博文!!!
把nginx.conf配置文件备份一下,然后进行相应的server_name更改为bbs.zxl.com方式访问
[root@nginx-web ~]# cd /usr/local/nginx/conf/ [root@nginx-web conf]# pwd /usr/local/nginx/conf [root@nginx-web conf]# cp nginx.conf nginx.conf.bak
检查nginx语法
root@nginx-web ~]# /usr/local/nginx/sbin/nginx -t nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
重新加载nginx服务
[root@nginx-web ~]# /usr/local/nginx/sbin/nginx -s reload
在linux服务器上更改hosts文件
[root@nginx-web ~]# tail -n 1 /etc/hosts 192.168.33.131bbs.zxl.com
使用curl进行访问下
[root@nginx-web ~]# curl -I http://bbs.zxl.com HTTP/1.1 200 OK Server: nginx/1.9.12 Date: Sat, 05 Mar 2016 02:35:52 GMT Content-Type: text/html Content-Length: 49 Last-Modified: Sat, 05 Mar 2016 02:34:55 GMT Connection: keep-alive ETag: "56da45cf-31" Accept-Ranges: bytes
生成自签证书
[root@nginx-web tls]# pwd /etc/pki/tls [root@nginx-web tls]# cp openssl.cnf openssl.cnf.bak//习惯修改文件之前先备份 [root@nginx-web tls]# vim openssl.cnf 42 dir = /etc/pki/CA # Where everything is kept //存放目录
生成私钥
[root@nginx-web tls]# cd /etc/pki/CA/ [root@nginx-web CA]# ls certs crl newcerts private [root@nginx-web CA]# ls private/ [root@nginx-web CA]# (umask 077; openssl genrsa 2048 > private/cakey.pem) Generating RSA private key, 2048 bit long modulus .............................+++ .......+++ e is 65537 (0x10001)
[root@nginx-web CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BJ Locality Name (eg, city) [Default City]:BJ Organization Name (eg, company) [Default Company Ltd]:ZXL Organizational Unit Name (eg, section) []:IT Common Name (eg, your name or your server's hostname) []:ca.zxl.com Email Address []:[email protected] [root@nginx-web CA]# ls cacert.pem certs crl newcerts private [root@nginx-web CA]# touch serial [root@nginx-web CA]# echo 00 > serial [root@nginx-web CA]# touch index.txt
创建存放证书目录
[root@nginx-web ~]# mkdir /usr/local/nginx/ssl [root@nginx-web ~]# cd /usr/local/nginx/ssl/ [root@nginx-web ssl]# ls [root@nginx-web ssl]# (umask 077; openssl genrsa 2048 > nginx.key) Generating RSA private key, 2048 bit long modulus ...........................................................................................................................................................+++ ............+++ e is 65537 (0x10001)
生成请求证书
[root@nginx-web ssl]# openssl req -new -key nginx.key -out nginx.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:BJ Locality Name (eg, city) [Default City]:BJ Organization Name (eg, company) [Default Company Ltd]:ZXL Organizational Unit Name (eg, section) []:IT Common Name (eg, your name or your server's hostname) []:bbs.zxl.com Email Address []:[email protected] Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:
自签证书10年
[root@nginx-web ssl]# openssl ca -in nginx.csr -out nginx.crt -days 3650 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 0 (0x0) Validity Not Before: Mar 5 02:51:37 2016 GMT Not After : Mar 3 02:51:37 2026 GMT Subject: countryName = CN stateOrProvinceName = BJ organizationName = ZXL organizationalUnitName = IT commonName = bbs.zxl.com emailAddress = [email protected] X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 74:86:87:7B:32:24:5F:2B:03:43:B8:C9:07:AF:76:33:86:21:07:04 X509v3 Authority Key Identifier: keyid:32:D4:F1:04:8E:D8:37:0C:1F:E3:74:6C:C7:76:7F:FE:8D:1C:BE:E8 Certificate is to be certified until Mar 3 02:51:37 2026 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
修改nginx配置文件中的ssl
[root@nginx-web conf]# pwd
/usr/local/nginx/conf
[root@nginx-web conf]# tail -n 22 nginx.conf
# HTTPS server
#
server {
listen 443 ssl;
server_name bbs.zxl.com;
ssl_certificate /usr/local/nginx/ssl/nginx.crt;
ssl_certificate_key /usr/local/nginx/ssl/nginx.key;
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 5m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
root html;
index index.html index.htm;
}
}
}
检查nginx语法
[root@nginx-web ~]# /usr/local/nginx/sbin/nginx -t nginx: the configuration file /usr/local/nginx/conf/nginx.conf syntax is ok nginx: configuration file /usr/local/nginx/conf/nginx.conf test is successful
加载nginx服务并查看nginx 443端口
[root@nginx-web ~]# /usr/local/nginx/sbin/nginx -s reload [root@nginx-web ~]# netstat -ntpl|grep nginx tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 14778/nginx tcp 0 0 0.0.0.0:443 0.0.0.0:* LISTEN 14778/nginx
window客户端hosts文件修改为
192.168.33.131 bbs.zxl.com
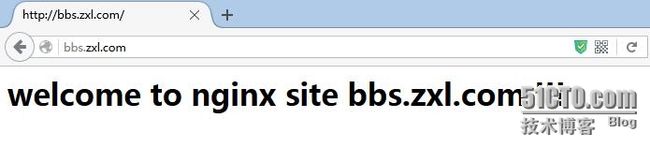
打开浏览器访问效果,在没有使用https
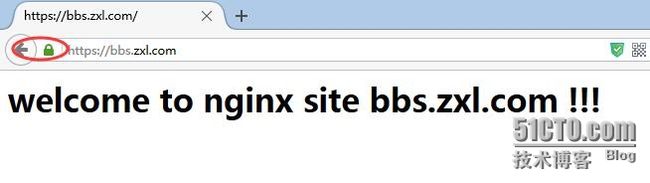
使用https访问,点击高级,添加例外
本文出自 “村里的男孩” 博客,转载请与作者联系!