ossec整合splunk
http://splunk-base.splunk.com/apps/22285/splunk-for-ossec-splunk-v4-version
This is a guest article by Dale Neufeld – canuck.eh at gmail.com
The status of the next version of the OSSEC web interface is one of the more commonly asked questions on the mailing list and is currently #2 on the community requested feature list (http://ossec.uservoice.com).
While web interfaces are nice to have, many of us suffer from information island overload by having dedicated web interfaces for each application. This is why I was stoked when the syslog ouput feature was announced last summer and officially added in version 1.6. Now I can incorporate OSSEC alerts into my SIM/SIEM or log management tool of choice, which not only eliminates the need for a dedicated OSSEC web interface but also allows for simplified incident analysis through aggregation and correlation.
In my environment, we chose Splunk based on its quick search and endless customization. Getting OSSEC alerts into Splunk is a breeze. Just grab the free license version of Splunk, install the Splunk for OSSEC app, and point the OSSEC syslog output to your Splunk server. BAM! Instant wui 0.4.
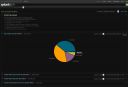
The Splunk-for-OSSEC application is a community project that was started by myself and Elazar Broad. The initial goal of this application was to provide the same set of reports that can be obtained through ossec-reportd. From there we’ve also added several other useful features:
- Top rules last 24 hrs
- Top source IP last 24 hrs
- Top user last 24 hrs
- Bruteforce top source IP last 24 hrs
- OSSEC rules for last hour
- OSSEC alert levels for last 24 hrs
- IP Geolocation lookups
- whois lookups
- rDNS lookups
- web attack and bruteforce tags.
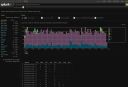
Screenshots:
OSSEC and Splunk configuration instructions
- Inside ossec.conf add a syslog_output block specifying your Splunk system IP address and the port it is listening on:
<syslog_output>
<server>172.10.2.3</server>
<port>10002</port>
</syslog_output>
- Now you need to enable the syslog_output module and restart OSSEC:
#/var/ossec/bin/ossec-control enable client-syslog
#/var/ossec/bin/ossec-control restart
- On the Splunk side, add this stanza to inputs.conf:
$SPLUNK_HOME/etc/system/local/inputs.conf
[udp://172.10.2.4:10002] #IP address of OSSEC server
disabled = false
sourcetype = ossec
By setting the sourcetype as OSSEC you’re ready to take advantage of the Splunk for OSSEC app which can be found here: http://www.splunkbase.com/apps/All/Security/app:Splunk+for+OSSEC.
- Make sure you update any local or network firewalls that this communication is traversing and then restart Splunk.
# $SPLUNK_HOME/bin/splunk restart
Splunk:
http://www.splunk.com/download
Splunk-for-OSSEC:
http://www.splunkbase.com/apps/All/Security/app:Splunk+for+OSSEC#
Feedback and feature requests are much appreciated!
If you’ve used the syslog ouput to send alerts to another SIM/SIEM or log management tool, we would love to hear from you so we can add configuration details to the wiki.