Windows安全检查脚本 bat 批处理
第二次写批处理……Windows的一键安检,最后只返回成功或失败+原因。
PS:
1、这玩意对普通人没啥用,对管理很多服务器的运维同学有用。
2、安检和加固是两码事,安检只管检,不过如果你想顺便加固,应该随便改改这个脚本就可以了,里面提供了加固的思路。
3、这个批处理依赖Sysinternals的两个小工具,以及windows自带的WMIC。
用于检测启动项的autorunsc64.exe: https://docs.microsoft.com/zh-cn/sysinternals/downloads/autoruns
用于检查文件数字签名的sigcheck64.exe: https://docs.microsoft.com/zh-cn/sysinternals/downloads/sigcheck
4、我测试下来支持2008和2012、2012R2,我的都是64位版本,32位版本不清楚……
5、执行完后,文件都拷贝到c:\tool目录,c:\tool\backup中会留下原始记录,便于后续来查看。
6、为什么不用powershell? 因为我不会。
脚本如下:
::查询用户(Administrator是否改名、是否有其他启用的Administrators组用户)
::查询启动项(是否有非系统默认的启动项)
::查询进程(是否有非白名单进程)
::查询防火墙(是否开启,是否屏蔽了某些特殊端口,仅对必要的ip开放)
::查询TCP监听(是否仅监听了必要的端口)
::密码和日志审计策略设置
::--------------------------------------------------------
::input: null
::output: Success|Failed\r\nReason
::--------------------------------------------------------
::有问题请联系http://blog.csdn.net/liv2005,谢谢!
::关闭命令回显,执行时不显示每条命令的命令行,@表示本行也不显示
@echo off
if not exist "c:\tool\backup\" (mkdir c:\tool\backup\)
del /f /q c:\tool\securitycheck.lock > nul 2>&1
ver | find "5.2" > nul
if %ERRORLEVEL% == 0 goto ver_2003
ver | find "6.1" >nul
if %ERRORLEVEL% == 0 goto ver_2008
ver | find "6.2" > nul
if %ERRORLEVEL% == 0 goto ver_2012
ver | find "6.3" > nul
if %ERRORLEVEL% == 0 goto ver_2012R2
goto warnthenexit
::--------------------------------------------------------
::-- Function section starts below here
::--------------------------------------------------------
:echofail
if not exist "c:\tool\securitycheck.lock" (
echo Failed
echo 1 > c:\tool\securitycheck.lock
)
goto:eof
:checksign
::检查文件签名
::call:checksign "c:\windows\system32\notepad.exe" buff
::return: unsigned | microsoft signed
if not exist "c:\tool\sigcheck64.exe" (copy sigcheck64.exe c:\tool\ >nul)
set "filepath=%~f1"
if not "%filepath%" EQU "" (
if exist "%filepath%" (
for /f "usebackq tokens=2,4 delims=," %%i in (`c:\tool\sigcheck64.exe /accepteula /c /nobanner "%filepath%" ^| find /i "signed"`) do (
if %%i EQU "Signed" (
if /i %%j EQU "Microsoft Corporation" (
set "%2=microsoft signed"
goto:eof
)
if /i %%j EQU "Microsoft Windows" (
set "%2=microsoft signed"
goto:eof
)
if /i %%j EQU "Microsoft" (
set "%2=microsoft signed"
goto:eof
)
) else (
set "%2=unsigned"
goto:eof
)
)
) else ( set "%2=file not exist" )
)
goto:eof
:checkuser
::查询用户(Administrator是否改名、Guest是否禁用、是否有其他启用的Administrators组用户)
setlocal enabledelayedexpansion
set flag=0
::因为wmic输出的是unicode格式,其他命令输出ASCII的,两个放一块就乱码了。
wmic useraccount list full | more >> c:\tool\backup\backup.log
for /f "tokens=1 delims= " %%i in ('wmic useraccount list status^|find "OK"') do (
set domainusername=%%i
set username=!domainusername:*\=!
::echo !username!
if /i "!username!" EQU "administrator" (
call:echofail
echo you should rename administrator
exit /b 1
)
if /i "!username!" EQU "guest" (
call:echofail
echo you should deny guest
exit /b 1
)
for /f "usebackq tokens=1 delims= " %%a in (`net user !username!^|find /i "Administrator"`) do (
if "%%a" NEQ "" (set flag=!flag!+1)
)
)
if !flag! GTR 1 (
call:echofail
echo not only one admin
exit /b 1
)
setlocal disabledelayedexpansion
goto:eof
:checkstartup
::查询启动项(是否有非系统默认的启动项)
setlocal enabledelayedexpansion
set flag=0
if not exist "c:\tool\autorunsc64.exe" (copy autorunsc64.exe c:\tool\ >nul)
c:\tool\autorunsc64.exe /accepteula /m /s /nobanner | more>> c:\tool\backup\backup.log
for /f "tokens=10 delims=," %%i in ('c:\tool\autorunsc64.exe /accepteula /m /s /nobanner /c^| find /i "exe" ^| find /v "winvnc.exe" ^| find /v "rdpclip.exe"^| find /v "WinMail.exe" ^|find /v "AlternateShell"') do (
if "%%i" GTR "" (
if !flag! EQU 0 (
set /A flag=1
call:echofail
)
echo startup NOT in whitelist: %%i
)
)
if !flag! EQU 1 (
exit /b 1
)
setlocal disabledelayedexpansion
goto:eof
:ProcessWhiteList
::保存进程白名单,并且与传入的进程名进行对比,增加需要修改list[]和list_length
set list[0]=c:\SSHD\bin\cygrunsrv.exe
set list[1]=C:\SSHD\sbin\sshd.exe
set list[2]=C:\Program Files\GCloud\gcloudagent.exe
set list_length=3
set list_index=0
:loopstart
if !list_index! EQU !list_length! (
::循环匹配白名单结束,检查签名开始
set buff=
call:checksign "%~f1" buff
if "!buff!" EQU "microsoft signed" (
set buff=
goto:eof
)
::签名也不是微软的,报错吧
set buff=process NOT in whitelist: "%~f1"
set /A list_index=0
goto:eof
)
for /f "usebackq tokens=2 delims==" %%a in (`set list[!list_index!]`) do (
if /i "%~f1" == "%%~fa" (
::echo process in whitelist: "%~f1"
set buff=
set /A list_index=0
goto:eof
)
)
set /A list_index=!list_index!+1
goto:loopstart
:checkprocess
::查询进程(是否有非白名单进程)
setlocal enabledelayedexpansion
set flag=0
wmic process get ExecutablePath | more >> c:\tool\backup\backup.log
for /f "usebackq tokens=* delims= " %%i in (`wmic process get ExecutablePath^|findstr -v "ExecutablePath"`) do (
set "name=%%i"
set "name=!name:~,-1!"
if /i not "!name!" == "" (
set "name=%%~fi"
call :ProcessWhiteList "!name!"
if not "!buff!" == "" (
if !flag! EQU 0 (
set /A flag=1
call:echofail
)
echo !buff!
set buff=
)
)
)
if !flag! EQU 1 (
exit /b 1
)
setlocal disabledelayedexpansion
goto:eof
:checkfirewall
::查询防火墙(是否开启,某些端口是否做了IP限制)
setlocal enabledelayedexpansion
set flag=0
netsh advfirewall firewall show rule name=all dir=in type=dynamic status=enabled >> c:\tool\backup\backup.log
for /f "usebackq tokens=1,2 delims= " %%i in (`netsh advfirewall show currentprofile ^| findstr "状态.*启用"`) do (
::英文系统会有问题
if not "%%j"=="启用" (
set /A flag=1
)
)
for /f "usebackq tokens=1,2,3 delims= " %%i in (`netsh advfirewall firewall show rule name^=all dir^=in type^=dynamic status^=enabled ^| findstr "IP"`) do (
::批处理的坑是如果findstr没找到内容,是不执行for循环内的代码的
echo %%k | findstr "8.8.8.8 !!!这里换成你的公司出口ip!!!" >nul && set "a=yes" || set "a=no"
if "!a!" EQU "yes" (
set /A flag=2
)
)
if !flag! EQU 1 (
call:echofail
echo firewall is off
exit /b 1
)
if !flag! EQU 0 (
call:echofail
echo firewall config error
exit /b 1
)
setlocal disabledelayedexpansion
goto:eof
:PortWhiteList
set "portwhitelist=135 445 3389 47001 end"
set tmp=!portwhitelist!
:tcploop
::循环匹配白名单
for /f "tokens=1,*" %%m in ("!tmp!") do (
if "%%m" EQU "%~1" (
set buff=
goto:eof
)
set tmp=%%n
)
if not "!tmp!" EQU "end" goto tcploop
::动态或私有端口:49152to65535或1025to103X只能checksign,微软的签名就不管,不是微软签名的就报出来
set "pid=%2"
for /f "usebackq tokens=*" %%a in (`wmic process where processid^=!pid! get ExecutablePath /value`) do (
set "line=%%a"
set "line=!line:~,-1!"
if "!line!" GTR "" (
(echo !line!|findstr -i "ExecutablePath">nul)&&(set "filepath=!line:~15!")
if "!filepath!" GTR "" (
set buff=
call:checksign !filepath! buff
if "!buff!" EQU "microsoft signed" (
set buff=
goto:eof
)
)
)
)
set buff=port NOT in whitelist: %~1
goto:eof
:checktcp
::查询TCP监听(是否仅监听了必要的端口)
setlocal enabledelayedexpansion
set flag=0
netstat -ano | find "LISTEN" | find "0.0.0.0" | find /v "127.0.0.1" >> c:\tool\backup\backup.log
for /f "usebackq tokens=2,5 delims= " %%i in (`netstat -ano ^| find "LISTEN" ^| find "0.0.0.0" ^| find /v "127.0.0.1"`) do (
set "port=%%i"
set "port=!port:*:=!"
set "pid=%%j"
call :PortWhiteList !port! !pid!
if not "!buff!" == "" (
if !flag! EQU 0 (
set /A flag=1
call:echofail
)
echo !buff!
set buff=
)
)
if !flag! EQU 1 (
exit /b 1
)
setlocal disabledelayedexpansion
goto:eof
:secedit
::密码和日志审计策略设置
setlocal enabledelayedexpansion
reg add HKLM\System\CurrentControlSet\Services\Tcpip\Parameters /v MaxUserPort /t REG_DWORD /d 65534 /f >nul
if not exist "c:\tool\celue.inf" (copy celue.inf c:\tool\ >nul)
secedit /configure /db c:\tool\celue.sdb /CFG c:\tool\celue.inf >nul
setlocal disabledelayedexpansion
goto:eof
::--------------------------------------------------------
::-- System section starts below here
::--------------------------------------------------------
:ver_2012
::Run Windows Server 2012 specific commands here.
::echo 2012
set flag=0
::buff全局变量 用来接收各种函数的返回值
set buff=
call:checkuser
if %ERRORLEVEL% GTR 0 (set /A flag=%flag%+1)
call:checkstartup
if %ERRORLEVEL% GTR 0 (set /A flag=%flag%+1)
call:checkprocess
if %ERRORLEVEL% GTR 0 (set /A flag=%flag%+1)
call:checkfirewall
if %ERRORLEVEL% GTR 0 (set /A flag=%flag%+1)
call:checktcp
if %ERRORLEVEL% GTR 0 (set /A flag=%flag%+1)
call:secedit
if %ERRORLEVEL% GTR 0 (set /A flag=%flag%+1)
if %flag% GTR 0 goto exit
goto succ
:ver_2012R2
::Run Windows Server 2012 R2 specific commands here.
goto:ver_2012
echo Failed
echo Win2012R2
goto exit
:ver_2008
::Run Windows Server 2008 specific commands here.
goto:ver_2012
echo Failed
echo Win2008
goto exit
:ver_2003
::Run Windows Server 2003 specific commands here.
echo Failed
echo Win2003
goto exit
::--------------------------------------------------------
::-- Bye!
::--------------------------------------------------------
:warnthenexit
echo Failed
echo system unknown
goto exit
:succ
echo Success
goto end
:exit
del /f /q c:\tool\securitycheck.lock > nul 2>&1
goto end
:end
其中,用于加固的chelue.inf我是这么写的,仅供参考:
[version]
signature="$CHICAGO$"
[Event Audit]
AuditSystemEvents = 3
AuditLogonEvents = 3
AuditObjectAccess = 2
AuditPrivilegeUse = 2
AuditPolicyChange = 3
AuditAccountManage = 3
AuditProcessTracking = 0
AuditDSAccess = 2
AuditAccountLogon = 3
[System Access]
PasswordComplexity = 1
MinimumPasswordLength = 12
MaximumPasswordAge = 90
用法:
1、把这四个文件放到任意目录中
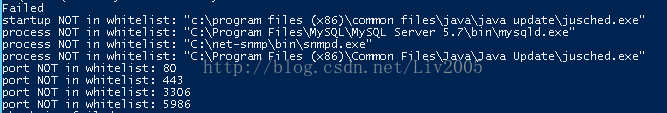
2、命令行或者远程调用s.bat,执行结果形如:
好了,发到你的若干台服务器上去,然后集中统计结果吧……
日常用用还可以,对安全有高精尖要求的还是算了.....