思科多nat顺序
思科nat与h3c的nat过程不一样的:思科是在全局配置命令下做nat配置的,而H3c则是直接在接口上配置nat(哪条nat条目被应用于此接口,直接在此条目上过滤)。思科的这种配置法会使分组数据在路由到出口后,需要按照nat的排序(可通过show run查看排序)来进行匹配,从而满足条件后做NAT。所以配置思科nat时,请注意nat的先后顺序。这个结论是经过无数次的实验而得出的。
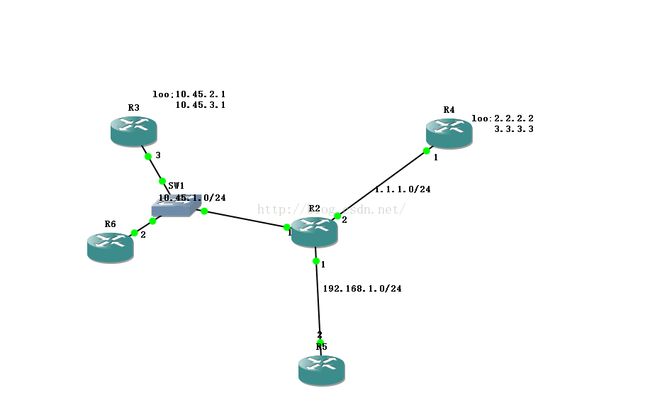
实验拓扑
附:R2中10.45.1.0及1.1.1.0网段的接口为outside;192.168.1.0接口为inside。
R2配置:
R2(config)#do sh run
Building configuration...
Current configuration : 1436 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R2
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
no ip icmp rate-limit unreachable
!
!
ip cef
no ip domain lookup
!
!
ip auth-proxy max-nodata-conns 3
ip admission max-nodata-conns 3
!
!
ip tcp synwait-time 5
!
interface Ethernet0/0
ip address 1.1.1.2 255.255.255.0
ip nat outside
ip virtual-reassembly
half-duplex
!
interface Ethernet0/1
ip address 10.45.1.1 255.255.255.0
ip nat outside
ip virtual-reassembly
half-duplex
!
interface Ethernet0/2
no ip address
shutdown
half-duplex
!
interface Ethernet0/3
ip address 192.168.1.1 255.255.255.0
ip nat inside
ip virtual-reassembly
half-duplex
!
no ip http server
no ip http secure-server
!
no ip classless
ip forward-protocol nd
ip route 0.0.0.0 0.0.0.0 1.1.1.1
ip route 10.0.0.0 255.0.0.0 10.45.1.3
!
ip nat inside source list wan interface Ethernet0/0 overload
ip nat inside source list wan2 interface Ethernet0/1 overload \\这是nat的顺序
!
!
ip access-list extended wan
permit ip any any
ip access-list extended wan2
permit ip 192.168.1.0 0.0.0.255 10.0.0.0 0.255.255.255
!
control-plane
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
exec-timeout 0 0
privilege level 15
logging synchronous
line vty 0 4
login
!
!
end
R2(config)#
我们知道inside到outside时 :分组数据先路由(选好路由的出口后,分组肯定要从这个出口路由出去,不会因为nat等原因而从另外不是最长匹配的路由出口出去),之后再nat。然而思科这里的nat并不是与接口绑定的,分组数据被nat时是有顺序的。如下
从R5上ping结果
R5#ping 10.45.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.45.3.1, timeout is 2 seconds:
.....
Success rate is 0 percent (0/5)
R5#ping 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 28/42/64 ms
R5#
在R2上查看nat过程及转换表
R2#debug ip nat detailed
IP NAT detailed debugging is on
R2#
*Mar 1 00:08:32.303: NAT: [0] Allocated Port for 192.168.1.2 -> 1.1.1.2: wanted 5 got 5 \\表明R5上ping 10.45.3.1时,R2上使用的是ip nat inside source list wan interface Ethernet0/0 overload这条。
*Mar 1 00:08:32.307: NAT*: i: icmp (192.168.1.2, 5) -> (10.45.3.1, 5) [25]
*Mar 1 00:08:32.307: NAT*: i: icmp (192.168.1.2, 5) -> (10.45.3.1, 5) [25]
*Mar 1 00:08:32.311: NAT*: s=192.168.1.2->1.1.1.2, d=10.45.3.1 [25]
R2#
*Mar 1 00:08:34.311: NAT*: i: icmp (192.168.1.2, 5) -> (10.45.3.1, 5) [26]
*Mar 1 00:08:34.315: NAT*: s=192.168.1.2->1.1.1.2, d=10.45.3.1 [26]
R2#
*Mar 1 00:08:36.303: NAT*: i: icmp (192.168.1.2, 5) -> (10.45.3.1, 5) [27]
*Mar 1 00:08:36.307: NAT*: s=192.168.1.2->1.1.1.2, d=10.45.3.1 [27]
R2#
*Mar 1 00:08:38.259: NAT*: i: icmp (192.168.1.2, 5) -> (10.45.3.1, 5) [28]
*Mar 1 00:08:38.259: NAT*: s=192.168.1.2->1.1.1.2, d=10.45.3.1 [28]
R2#
*Mar 1 00:08:40.275: NAT*: i: icmp (192.168.1.2, 5) -> (10.45.3.1, 5) [29]
*Mar 1 00:08:40.275: NAT*: s=192.168.1.2->1.1.1.2, d=10.45.3.1 [29]
R2#sh ip nat tr
Pro Inside global Inside local Outside local Outside global
icmp 1.1.1.2:5 192.168.1.2:5 10.45.3.1:5 10.45.3.1:5 \\表明R5上ping 10.45.3.1时,R2上使用的是ip nat inside source list wan interface Ethernet0/0 overload这条。
导致无法ping通10.45.3.1的原因是由于当分组数据被路由到10网段的出口时候,发现出口上配置有ip nat outside,所以分组数据被整个nat列表(所有nat条目,按先后排序)过滤,当分组数据被第一条nat过滤时就已经匹配,所以10.45.3.1的源地址192.168.1.2就被替换为1.1.1.2了,不会再进行第二条nat过滤。
这里可能大家还有个疑问:可能是由于分组数据在选择路由时,使用的是默认路由呢?为了证实这一点,在R4上添加了一个环回地址:10.45.3.1,结果R5上还是没能ping通10.45.3.1,所以这个疑问是不成立的。所以证明路由已经选择10网段出口了,出错是在nat顺序上。
解决方法1:
在R2的ip access-list extended wan中首先添加一条deny目标为10的网段,
ip access-list extended wan
deny ip any 10.0.0.0 0.255.255.255
permit ip any any
结果R5成功ping通10.45.3.1(略)
解决方法2:
在R2上调整nat条目的顺序,删除ip access-list extended wan后,添加ip access-list extended wan3,从而使调用wan3后排列在wna2的后面,
ip nat inside source list wan2 interface Ethernet0/1 overload
ip nat inside source list wan3 interface Ethernet0/0 overload
!
!
ip access-list extended wan2
permit ip 192.168.1.0 0.0.0.255 10.0.0.0 0.255.255.255
ip access-list extended wan3
permit ip any any
!
结果在R5上分别ping 10.45.3.1及2.2.2.2都通
R5#ping 10.45.3.1
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 10.45.3.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 24/42/60 ms
R5#ping 2.2.2.2
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 2.2.2.2, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 36/43/52 ms
R5#
在R2上显示nat的正常数据过程
R2(config)#
*Mar 1 00:38:27.887: NAT: [0] Allocated Port for 192.168.1.2 -> 10.45.1.1: wanted 9 got 9
*Mar 1 00:38:27.891: NAT*: i: icmp (192.168.1.2, 9) -> (10.45.3.1, 9) [45]
*Mar 1 00:38:27.895: NAT*: i: icmp (192.168.1.2, 9) -> (10.45.3.1, 9) [45]
*Mar 1 00:38:27.899: NAT*: s=192.168.1.2->10.45.1.1, d=10.45.3.1 [45]
*Mar 1 00:38:27.931: NAT*: o: icmp (10.45.3.1, 9) -> (10.45.1.1, 9) [45]
*Mar 1 00:38:27.931: NAT*: s=10.45.3.1, d=10.45.1.1->192.168.1.2 [45]
*Mar 1 00:38:27.959: NAT*: i: icmp (192.168.1.2, 9) -> (10.45.3.1, 9) [46]
*Mar 1 00:38:27.963: NAT*: s=192.168.1.2->10.45.1.1, d=10.45.3.1 [46]
*Mar 1 00:38:27.979: NAT*: o: icmp (10.45.3.1, 9) -> (10.45.1.1, 9) [46]
*Mar 1 00:38:27.983: NAT*: s=10.45.3.1, d=10.45.1.1->192.168.1.2 [46]
*Mar 1 00:38:28.007: NAT*: i: icmp (192.168.1.2, 9) -> (10.45.3.1, 9) [47]
*Mar 1 00:38:28.007: NAT*: s=192.168.1.2->10.45.1.1, d=10.45.3.1 [47]
*Mar 1 00:38:28.023: NAT*: o: icmp (10.45.3.1, 9) -> (10.45.1.1, 9) [47]
*Mar 1 00:38:28.027: NAT*: s=10.45.3.1, d=10.45.1.1->192.168.1.2 [47]
*Mar 1 00:38:28.043: NAT*: i: icmp (192.168.1.2, 9) -> (10.45.3.1, 9) [48]
*Mar 1 00:38:28.047: NAT*: s=192.168.1.2->10.45.1.1, d=10.45.3.1 [48]
*Mar 1 00:38:28.071: NAT*: o: icmp (10.45.3.1, 9) -> (10.45.1.1, 9) [48]
*Mar 1 00:38:28.071: NAT*: s=10.45.3.1, d=10.45.1.1->192.168.1.2 [48]
*Mar 1 00:38:28.091: NAT*: i: icmp (192.168.1.2, 9) -> (10.45.3.1, 9) [49]
*Mar 1 00:38:28.091: NAT*: s=192.168.1.2->10.45.1.1, d=10.45.3.1 [49]
*Mar 1 00:38:28.111: NAT*: o: icmp (10.45.3.1, 9) -> (10.45.1.1, 9) [49]
*Mar 1 00:38:28.111: NAT*: s=10.45.3.1, d=10.45.1.1->192.168.1.2 [49]
R2(config)#
R2(config)#
*Mar 1 00:38:30.595: NAT: [0] Allocated Port for 192.168.1.2 -> 1.1.1.2: wanted 10 got 10
*Mar 1 00:38:30.599: NAT*: i: icmp (192.168.1.2, 10) -> (2.2.2.2, 10) [50]
*Mar 1 00:38:30.599: NAT*: i: icmp (192.168.1.2, 10) -> (2.2.2.2, 10) [50]
*Mar 1 00:38:30.603: NAT*: s=192.168.1.2->1.1.1.2, d=2.2.2.2 [50]
*Mar 1 00:38:30.619: NAT*: o: icmp (2.2.2.2, 10) -> (1.1.1.2, 10) [50]
*Mar 1 00:38:30.619: NAT*: s=2.2.2.2, d=1.1.1.2->192.168.1.2 [50]
*Mar 1 00:38:30.651: NAT*: i: icmp (192.168.1.2, 10) -> (2.2.2.2, 10) [51]
*Mar 1 00:38:30.651: NAT*: s=192.168.1.2->1.1.1.2, d=2.2.2.2 [51]
*Mar 1 00:38:30.683: NAT*: o: icmp (2.2.2.2, 10) -> (1.1.1.2, 10) [51]
*Mar 1 00:38:30.683: NAT*: s=2.2.2.2, d=1.1.1.2->192.168.1.2 [51]
*Mar 1 00:38:30.703: NAT*: i: icmp (192.168.1.2, 10) -> (2.2.2.2, 10) [52]
*Mar 1 00:38:30.703: NAT*: s=192.168.1.2->1.1.1.2, d=2.2.2.2 [52]
*Mar 1 00:38:30.723: NAT*: o: icmp (2.2.2.2, 10) -> (1.1.1.2, 10) [52]
*Mar 1 00:38:30.723: NAT*: s=2.2.2.2, d=1.1.1.2->192.168.1.2 [52]
*Mar 1 00:38:30.743: NAT*: i: icmp (192.168.1.2, 10) -> (2.2.2.2, 10) [53]
*Mar 1 00:38:30.743: NAT*: s=192.168.1.2->1.1.1.2, d=2.2.2.2 [53]
*Mar 1 00:38:30.767: NAT*: o: icmp (2.2.2.2, 10) -> (1.1.1.2, 10) [53]
*Mar 1 00:38:30.767: NAT*: s=2.2.2.2, d=1.1.1.2->192.168.1.2 [53]
*Mar 1 00:38:30.787: NAT*: i: icmp (192.168.1.2, 10) -> (2.2.2.2, 10) [54]
*Mar 1 00:38:30.787: NAT*: s=192.168.1.2->1.1.1.2, d=2.2.2.2 [54]
*Mar 1 00:38:30.807: NAT*: o: icmp (2.2.2.2, 10) -> (1.1.1.2, 10) [54]
*Mar 1 00:38:30.811: NAT*: s=2.2.2.2, d=1.1.1.2->192.168.1.2 [54]
R2(config)#
总结:
1、思科配置中,不仅访问控制列表acl有顺序,NAT列表也有顺序(需要做nat时都经过整个nat列表的过滤)。
2、本文的技术皆为自己实验感悟,目前已在packet tracer 以及gns3实验过。
3、由于多nat技术在各大论坛上少有介绍,借鉴于本论文的伙伴们,请多多查阅其他文章及多做实验是否支持本文技术,如有偏差请各位指导纠正。