Ip作业:防火墙的配置与acl相关配置
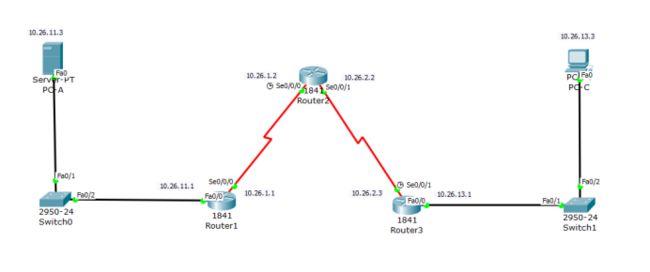
拓扑图如下(学号26):
配置静态路由:
R1(config)#int f0/0
R1(config-if)#ip address 10.26.1.1 255.255.255.0
R1(config-if)#no shutdown
R1(config)#int f0/1
R1(config-if)#ip address 14.26.2.1 255.255.255.0
R1(config-if)#no shutdown
R4(config)#ip route 10.26.1.0 255.255.255.0 14.26.2.1
R3(config)#ip route 14.26.2.0 255.255.255.0 10.26.1.1
R2(config)#ip route 14.26.2.0 255.255.255.0 10.26.1.1
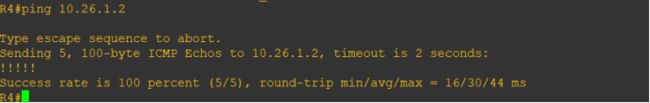
测试网络是否Ping通:
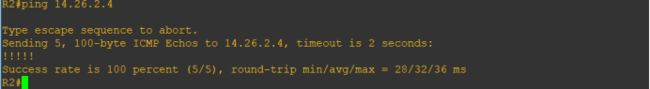
R2pingR4
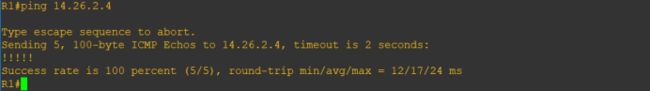
R1pingR4
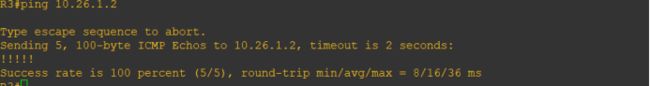
R3pingR2
R4pingR2
标准acl
R4(config)#access-list 1 deny 10.26.1.2 0.0.0.0
R4(config)#int f0/1
R4(config-if)#ip access-group 1 in
R4(config-if)#end
自反acl
R1(config)#ip access-list extended come
R1(config-ext-nacl)#permit icmp any any
R1(config-ext-nacl)#evaluate abc
R1(config)#int f0/1
R1(config-if)#ip access-group come in
R1(config)#ip access-list extended goto
R1(config-ext-nacl)#permit tcp any any eq telnet reflect abc timeout 60
R1(config-ext-nacl)#permit ip any any
R1(config)#int f0/1
R1(config-if)#ip access-group goto out
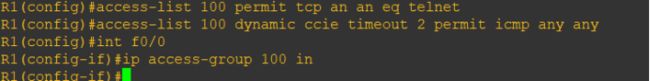
动态acl
R1(config)#access-list 100 permit tcp an an eq telnet
R1(config)#access-list 100 dynamic ccie timeout 2 permit icmp any any
R1(config)#int f0/0
R1(config-if)#ip access-group 100 in
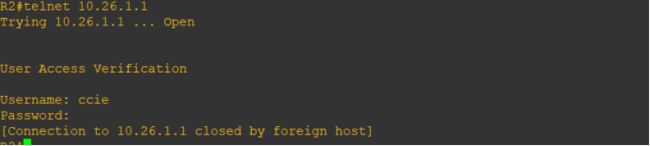
配置本地用户数据库
R1(config)#username ccie password ysx
R1(config)#line vty 0 181
R1(config-line)#login local
R1(config-line)#autocommand access-enable
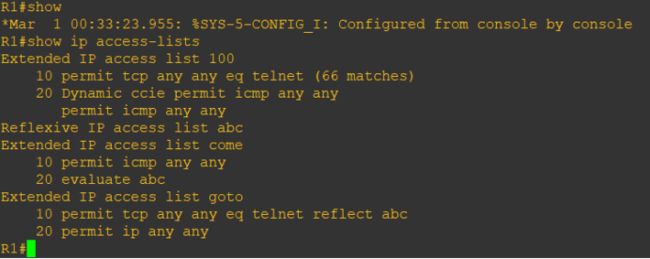
R1#show ip access-lists
Extended IP access list 100
10 permit tcp any any eq telnet (84 matches)
20 Dynamic ccie permit icmp any any
Reflexive IP access list abc
Extended IP access list come
10 permit icmp any any (35 matches)
20 evaluate abc
Extended IP access list goto
10 permit tcp any any eq telnet reflect abc (23 matches)
20 permit ip any any (15 matches)
基于时间的acl
R1(config)#time-range TELNET
R1(config-time-range)#periodic weekdays 9:00 to 14:00
R1(config)#access-list 150 deny tcp host 10.26.1.2 any eq 23 time TELNET
R1(config)#$ 150 deny tcp host 10.26.1.2 any eq 23 time-range TELNET
R1(config)#access-list 150 permit ip any any
R1(config)#int f0/0
R1(config-if)#ip access-group 150 in
查看路由器时间
![]()
测试R2向R4发起telnet会话
r2#telnet 14.26.2.4
Trying 14.26.2.4 ...
% Destination unreachable; gateway or host down
r2#
说明:可以看到,在规定的时间范围内,R2向R4发起telnet会话是被拒绝的。
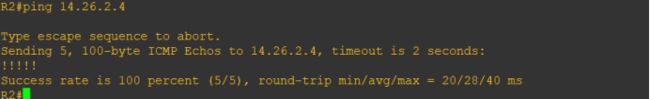
测试除telnet外的其它流量
r2#ping 14.26.2.4
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 14.26.2.4, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/2/4 ms
r2#
说明:可以看到,在规定的时间范围内,除了telnet之外,其它流量不受限制
查看当前R1的时间
r1#sh clock
测试R2向R4发起telnet会话
r2#telnet 14.26.2.4
Trying 14.26.2.4 ... Open
r4>
说明:在时间范围之外,所限制的流量被放开。
配置基于区域策略的防火墙
拓扑图
地址表
|
Device |
Interface |
IP Address |
Subnet Mask |
Default Gateway |
|
R1 |
Fa0/0 |
10.26.11.1 |
255.255.255.0 |
N/A |
| S0/0/0000 |
10.26.1.1 |
255.255.255.0 |
N/A |
|
|
R2 |
S0/0/0100 |
10.26.1.2 |
255.255.255.0 |
N/A |
| S0/0/1 |
10.26.2.2 |
255.255.255.0 |
N/A |
|
|
R3 |
Fa0/0 |
10.26.13.1 |
255.255.255.0 |
N/A |
| S0/0/1 |
10.26.2.3 |
255.255.255.0 |
N/A |
|
| PC-A |
NIC |
10.26.11.3 |
255.255.255.0 |
10.26.11.1 |
| PC-C |
NIC |
10.26.13.3 |
255.255.255.0 |
10.26.13.1 |
配置静态路由使其能ping通
Router1(config)#ip route 10.26.2.0 255.255.255.0 10.26.1.2
Router1(config)#ip route 10.26.13.0 255.255.255.0 10.26.1.2
Router2(config)#ip route 10.26.13.0 255.255.255.0 10.26.2.3
Router2(config)#ip route 10.26.11.0 255.255.255.0 10.26.1.1
Router3(config)#ip route 10.26.1.0 255.255.255.0 10.26.2.2
Router3(config)#ip route 10.26.11.0 255.255.255.0 10.26.2.2
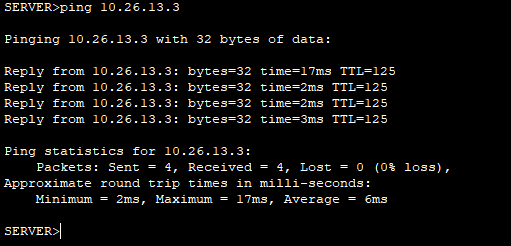
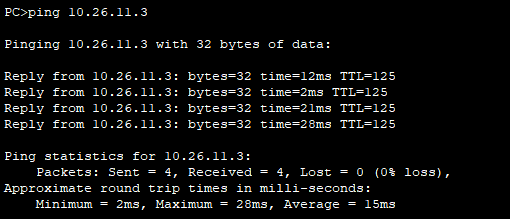
网络ping通测试
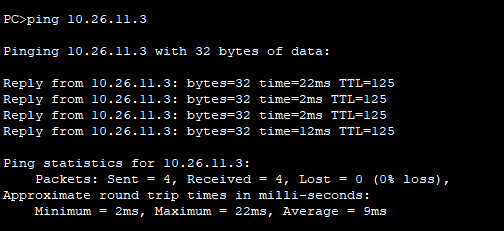
PC-A ping通PC-C。
PC-C ping 通PC-A
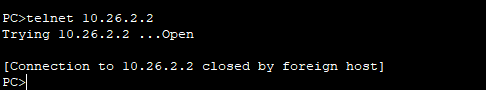
PC-C telnet到s0/0/1接口
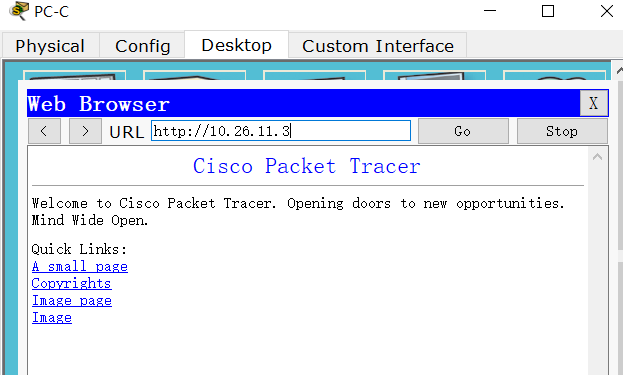
PC-C登到PC-A的网页
在R3创建区域防火墙
Router3(config)#zone security IN-ZONE
Router3(config-sec-zone)#zone security OUT-ZONE
Router3(config-sec-zone)#ex
Router3(config)#access-list 101 permit ip 10.26.13.0 0.0.0.255 any
Router3(config)#class-map type inspect match-all IN-NET-CLASS-MAP
Router3(config-cmap)#match access-group 101
Router3(config-cmap)#ex
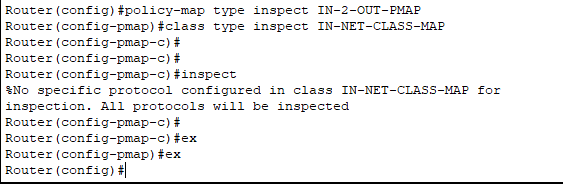
Router3(config)#policy-map type inspect IN-2-OUT-PMAP
Router3(config-pmap)#class type inspect IN-NET-CLASS-MAP
Router3(config-pmap-c)#inspect
%No specific protocol configured in class IN-NET-CLASS-MAP for inspection. All protocols will be inspected
Router3(config-pmap-c)#
Router3(config-pmap-c)#ex
Router3(config-pmap)#ex
Router3(config)#zone-pair security IN-2-OUT-ZPAIR source IN-ZONE destination OUT-ZONE
Router3(config-sec-zone-pair)#service-policy type inspect IN-2-OUT-PMAP
Router3(config-sec-zone-pair)#ex
Router3(config)#int f0/0
Router3(config-if)#zone-member security IN-ZONE
Router3(config-if)#ex
Router3(config)#int s0/0/1
Router3(config-if)#zone-member security OUT-ZONE
Router3(config-if)#ex
Router3(config)#ex
Router3#
%SYS-5-CONFIG_I: Configured from console by console
Router3#show policy-map type inspect zone-pair sessions
Zone-pair: IN-2-OUT-ZPAIR
PC-C能成功ping到PC-A
然后登陆pc-ad的网页的同时查看R3的命令
R3# show policy-map type inspect zone-pair sessions
Zone-pair: IN-ZONE-OUT-ZONE
Service-policy inspect : IN-2-OUT-PMAP
Class-map: IN-NET-CLASS-MAP (match-all)
Match: access-group 101
Inspect
Established Sessions
Session 139142400 (10.26.13.3:1027)=>(10.26.11.3:80)
http:tcp SIS_OPEN
总结:
经过这次实验我学到了很多东西,我懂得了防火墙的配置以及它的原理,也懂得了acl的设置其中我也有许多问题在咨询同学后加深了理解,比如基于时间的acl配置。希望以后有更大的进步,更加锻炼自己的实践能力以及独立思考与解决问题的能力。