CrackMe —— 027
160 CrackMe 是比较适合新手学习逆向破解的CrackMe的一个集合一共160个待逆向破解的程序
CrackMe:它们都是一些公开给别人尝试破解的小程序,制作 crackme 的人可能是程序员,想测试一下自己的软件保护技术,也可能是一位 cracker,想挑战一下其它 cracker 的破解实力,也可能是一些正在学习破解的人,自己编一些小程序给自己破。
CrackMe简称CM。
程序下载地址: 点击我
来源 <-点击查看
| 编号 | 作者 | 保护方式 |
| 027 | Cosh | CD-CHECK |
工具
x32dbg
开始破解之旅
ON.1
爆破方式
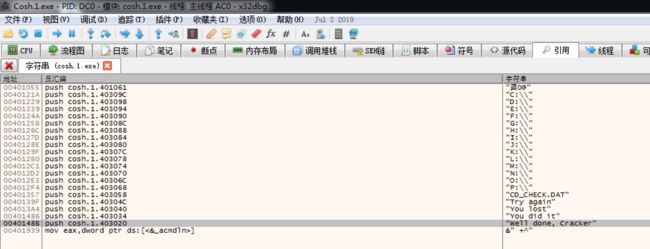
首先我们使用x32dbg打开027号程序,右键搜索字符串
这里看到了我们的正确提示字符串信息和错误提示字符串信息
进入正确字符串地址处0040148B,向上翻看
00401384 | E8 11030000 | call <JMP.&Ordinal#800> | 00401389 | 385D F3 | cmp byte ptr ss:[ebp-0xD],bl | 0040138C | 0F84 F3000000 | je cosh.1.401485 | 判断验证信息是否正确,正确则跳转到正确提示处 00401392 | FF45 EC | inc dword ptr ss:[ebp-0x14] | 00401395 | 83C7 04 | add edi,0x4 | edi:"0#@" 00401398 | 837D EC 07 | cmp dword ptr ss:[ebp-0x14],0x7 | 0040139C | 75 9F | jne cosh.1.40133D | 错误则向上跳转,循环每个盘验证注册信息 0040139E | 53 | push ebx | 0040139F | 68 4C304000 | push cosh.1.40304C | 40304C:"Try again" 004013A4 | 68 40304000 | push cosh.1.403040 | 403040:"You lost" 004013A9 | 8B4D E4 | mov ecx,dword ptr ss:[ebp-0x1C] | [ebp-1C]:"0#@" 004013AC | E8 D1020000 | call <JMP.&Ordinal#4224> | 004013B1 | 8D4D E8 | lea ecx,dword ptr ss:[ebp-0x18] | 004013B4 | C645 FC 0E | mov byte ptr ss:[ebp-0x4],0xE | 004013B8 | E8 DD020000 | call <JMP.&Ordinal#800> | 004013BD | 56 | push esi | esi:"0#@" 004013BE | 6A 01 | push 0x1 | 004013C0 | 8D45 DC | lea eax,dword ptr ss:[ebp-0x24] | 004013C3 | 6A 04 | push 0x4 | 004013C5 | 50 | push eax | 004013C6 | C645 FC 0D | mov byte ptr ss:[ebp-0x4],0xD | D:'\r' 004013CA | E8 27030000 | call cosh.1.4016F6 | 004013CF | 8D4D D8 | lea ecx,dword ptr ss:[ebp-0x28] | 004013D2 | C645 FC 0C | mov byte ptr ss:[ebp-0x4],0xC | C:'\f' 004013D6 | E8 BF020000 | call <JMP.&Ordinal#800> | 004013DB | 8D4D D4 | lea ecx,dword ptr ss:[ebp-0x2C] | 004013DE | C645 FC 0B | mov byte ptr ss:[ebp-0x4],0xB | B:'\v' 004013E2 | E8 B3020000 | call <JMP.&Ordinal#800> | 004013E7 | 8D4D D0 | lea ecx,dword ptr ss:[ebp-0x30] | 004013EA | C645 FC 0A | mov byte ptr ss:[ebp-0x4],0xA | A:'\n' 004013EE | E8 A7020000 | call <JMP.&Ordinal#800> | 004013F3 | 8D4D CC | lea ecx,dword ptr ss:[ebp-0x34] | 004013F6 | C645 FC 09 | mov byte ptr ss:[ebp-0x4],0x9 | 9:'\t' 004013FA | E8 9B020000 | call <JMP.&Ordinal#800> | 004013FF | 8D4D C8 | lea ecx,dword ptr ss:[ebp-0x38] | 00401402 | C645 FC 08 | mov byte ptr ss:[ebp-0x4],0x8 | 00401406 | E8 8F020000 | call <JMP.&Ordinal#800> | 0040140B | 8D4D C4 | lea ecx,dword ptr ss:[ebp-0x3C] | 0040140E | C645 FC 07 | mov byte ptr ss:[ebp-0x4],0x7 | 00401412 | E8 83020000 | call <JMP.&Ordinal#800> | 00401417 | 8D4D C0 | lea ecx,dword ptr ss:[ebp-0x40] | 0040141A | C645 FC 06 | mov byte ptr ss:[ebp-0x4],0x6 | 0040141E | E8 77020000 | call <JMP.&Ordinal#800> | 00401423 | 8D4D BC | lea ecx,dword ptr ss:[ebp-0x44] | 00401426 | C645 FC 05 | mov byte ptr ss:[ebp-0x4],0x5 | 0040142A | E8 6B020000 | call <JMP.&Ordinal#800> | 0040142F | 8D4D B8 | lea ecx,dword ptr ss:[ebp-0x48] | 00401432 | C645 FC 04 | mov byte ptr ss:[ebp-0x4],0x4 | 00401436 | E8 5F020000 | call <JMP.&Ordinal#800> | 0040143B | 8D4D B4 | lea ecx,dword ptr ss:[ebp-0x4C] | 0040143E | C645 FC 03 | mov byte ptr ss:[ebp-0x4],0x3 | 00401442 | E8 53020000 | call <JMP.&Ordinal#800> | 00401447 | 8D4D B0 | lea ecx,dword ptr ss:[ebp-0x50] | 0040144A | C645 FC 02 | mov byte ptr ss:[ebp-0x4],0x2 | 0040144E | E8 47020000 | call <JMP.&Ordinal#800> | 00401453 | 8D4D AC | lea ecx,dword ptr ss:[ebp-0x54] | 00401456 | C645 FC 01 | mov byte ptr ss:[ebp-0x4],0x1 | 0040145A | E8 3B020000 | call <JMP.&Ordinal#800> | 0040145F | 8D4D A8 | lea ecx,dword ptr ss:[ebp-0x58] | 00401462 | 885D FC | mov byte ptr ss:[ebp-0x4],bl | 00401465 | E8 30020000 | call <JMP.&Ordinal#800> | 0040146A | 834D FC FF | or dword ptr ss:[ebp-0x4],0xFFFFFFFF | 0040146E | 8D4D A4 | lea ecx,dword ptr ss:[ebp-0x5C] | 00401471 | E8 24020000 | call <JMP.&Ordinal#800> | 00401476 | 8B4D F4 | mov ecx,dword ptr ss:[ebp-0xC] | 00401479 | 5F | pop edi | edi:"0#@" 0040147A | 5E | pop esi | esi:"0#@" 0040147B | 5B | pop ebx | 0040147C | 64:890D 00000000 | mov dword ptr fs:[0],ecx | 00401483 | C9 | leave | 00401484 | C3 | ret | 00401485 | 53 | push ebx | 00401486 | 68 34304000 | push cosh.1.403034 | 403034:"You did it" 0040148B | 68 20304000 | push cosh.1.403020 | 403020:"Well done, Cracker" 00401490 | E9 14FFFFFF | jmp cosh.1.4013A9 | 此处向上跳转,跳转到004013A9 00401495 | 6A 00 | push 0x0 | 00401497 | FF71 20 | push dword ptr ds:[ecx+0x20] |
我们在0040138C处下断点,点击Check for CD按钮,此时程序停在了我们的断点处
将0040138C处JE修改为JMP
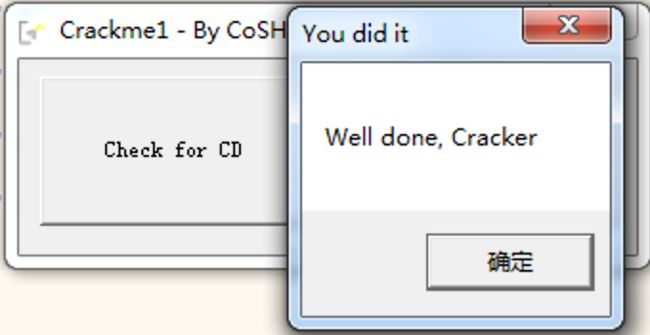
bingo ~ 破解成功
ON.2
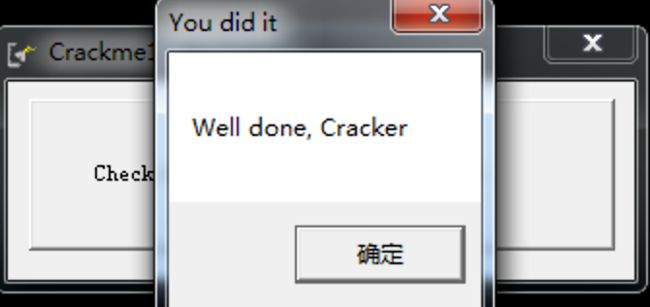
来到上一步下的断点处,向上一栋两三步可以看出来,该代码会循环读取C-P硬盘下的"CH_CHECK.DAT"文件,判断是否存在如果存在成提示正确信息,在C盘下创建该文件后点击Check for CD按钮,提示我们破解成功